记录自己的常用linux软件及设置
一、tmux设置
主要实现分栏选取(不用按住shift,不再按Ctrl+Shift+C),选取内容直接进入系统剪贴板(而不是留在tmux缓存区),操作改为vi习惯,屏蔽tmux自己的右键菜单(和终端的右键菜单冲突)
unbind ^b
set -g prefix ^b
set-option -g mouse on
set -g mode-keys vi
bind-key % split-window -h -c "#{pane_current_path}"
bind-key '"' split-window -v -c "#{pane_current_path}"
bind -r k select-pane -U
bind -r j select-pane -D
bind -r h select-pane -L
bind -r l select-pane -R
#disable right mouse button menu
bind-key -T root MouseDown3Pane select-pane
#select Enter directly copy into clipboard
bind-key -T copy-mode-vi Enter send-keys -X copy-selection-and-cancel \; run-shell "tmux show-buffer | xsel --clipboard --input"
#mouse drag select directly copy into clipboard
bind-key -T copy-mode-vi MouseDragEnd1Pane send-keys -X copy-selection-and-cancel \; run-shell "tmux show-buffer | xsel --clipboard --input"二、zsh命令行提示符设置
增加自定义函数short_path(),实现比较简洁的提示符。
# 自定义函数显示路径缩写
function short_path() {
# 如果当前路径在用户目录下,用 ~ 替换主目录部分,并缩写后续路径
if [[ "$PWD" == $HOME* ]]; then
# 主目录部分替换为 ~,仅缩写后续路径
print -P "~"$(print -P "${PWD/#$HOME}" | awk -F'/' '{for(i=1; i<=NF; i++) printf substr($i, 1, 1) (i==NF ? "" : "/")}')
else
# 对非用户目录,直接缩写每个文件夹的首字母
print -P "%~" | awk -F'/' '{for(i=1; i<=NF; i++) printf substr($i, 1, 1) (i==NF ? "" : "/")}'
fi
}
configure_prompt() {
prompt_symbol=㉿
# Skull emoji for root terminal
#[ "$EUID" -eq 0 ] && prompt_symbol=💀
case "$PROMPT_ALTERNATIVE" in
twoline)
PROMPT=$'%F{%(#.blue.green)}┌──${debian_chroot:+($debian_chroot)─}${VIRTUAL_ENV:+($(basename $VIRTUAL_ENV))─}(%B%F{%(#.red.blue)}%n'$prompt_symbol$'%m%b%F{%(#.blue.green)})-[%B%F{reset}%(6~.%-1~/…/%4~.%5~)%b%F{%(#.blue.green)}]\n└─%B%(#.%F{red}#.%F{blue}$)%b%F{reset} '
# Right-side prompt with exit codes and background processes
#RPROMPT=$'%(?.. %? %F{red}%B⨯%b%F{reset})%(1j. %j %F{yellow}%B⚙%b%F{reset}.)'
;;
oneline)
PROMPT=$'${debian_chroot:+($debian_chroot)}${VIRTUAL_ENV:+($(basename $VIRTUAL_ENV))}%B%F{%(#.red.blue)}%n@%m%b%F{reset}:%B%F{%(#.blue.green)}%~%b%F{reset}%(#.#.$) '
RPROMPT=
;;
backtrack)
#PROMPT=$'${debian_chroot:+($debian_chroot)}${VIRTUAL_ENV:+($(basename $VIRTUAL_ENV))}%B%F{red}%n@%m%b%F{reset}:%B%F{blue}%~%b%F{reset}%(#.#.$) '
PROMPT=$'%B%F{blue}%~%b%F{reset}%(#.#.$) '
RPROMPT=
;;
kali)
PROMPT='$(short_path)%F{blue} $%f'
RPROMPT=
;;
esac
unset prompt_symbol
}效果如下:
/u/s/s/P $pwd
/usr/share/seclists/Passwords
~/./b $pwd
/home/kali/.local/bin(一)将常用命令保存在一个文件中。
~ $cat /opt/dmenu_commands.txt
sudo arp-scan --interface eth1 192.168.56.0/24
sudo arp-scan --interface eth2 192.168.69.0/24
netexec smb $IP
netexec smb $IP -u 'anonymous' -p '' --rid-brute
netexec winrm $IP
netexec ldap $IP -u 'appolonia' -p '5umm3r@' --bloodhound --collection All --dns-server $IP
smbclient -NL $IP
smbmap -H $IP
crackmapexec smb $IP -u 'null' -p '' --shares
nmap -sV -sC -Pn -p- -oN port.log $IP
nmap --script smb-vuln* -p139,445 -T4 -Pn $IP
sudo nmap -sU -sV --version-intensity 0 -n -F -T4 -oN port_udp.log $IP
ldapsearch -x -H ldap://$IP -s base
rpcclient -N -U "" $IP -c "enumdomusers"
rpcclient -N -U "" $IP -c "querydispinfo"
rpcclient -U "$USER%$PASS" $IP -c "enumdomusers"
rpcclient -U "$USER%$PASS" $IP -c "querydispinfo"
python3 -c 'import pty;pty.spawn("/bin/bash")'
rlwrap nc -nlvp 1234
sudo php -S 0.0.0.0:80
sudo php -S 0.0.0.0:80 -t ~
find / -perm -u=s 2>/dev/null
find / -type f -perm -ug=rwx 2>/dev/null
find / -writable -not -path "/proc*" 2>/dev/null
enum4linux -a $IP
getcap -r / 2>/dev/null
ss -tulnp
IP="$(ip -4 addr show | grep 'inet 192.168.56' | sed 's/.*inet \\([^/]*\\).*/\\1/')"
ssh-keygen -f "/home/kali/.ssh/known_hosts" -R $IP
echo -n "请输入win端口号" && read PORT && gobuster dir -u http://$IP:$PORT -t 20 -H 'User-Agent:Mozilla' -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.asp,.aspx,.txt -b 401,403,404,500 -o $PORT.log
echo -n "请输入win端口号" && read PORT && echo -n "请输入子目录" && read SUBDIR && gobuster dir -u http://$IP:$PORT/$SUBDIR -t 20 -H 'User-Agent:Mozilla' -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.asp,.aspx,.txt -b 401,403,404,500 -o $PORT_$SUBDIR.log
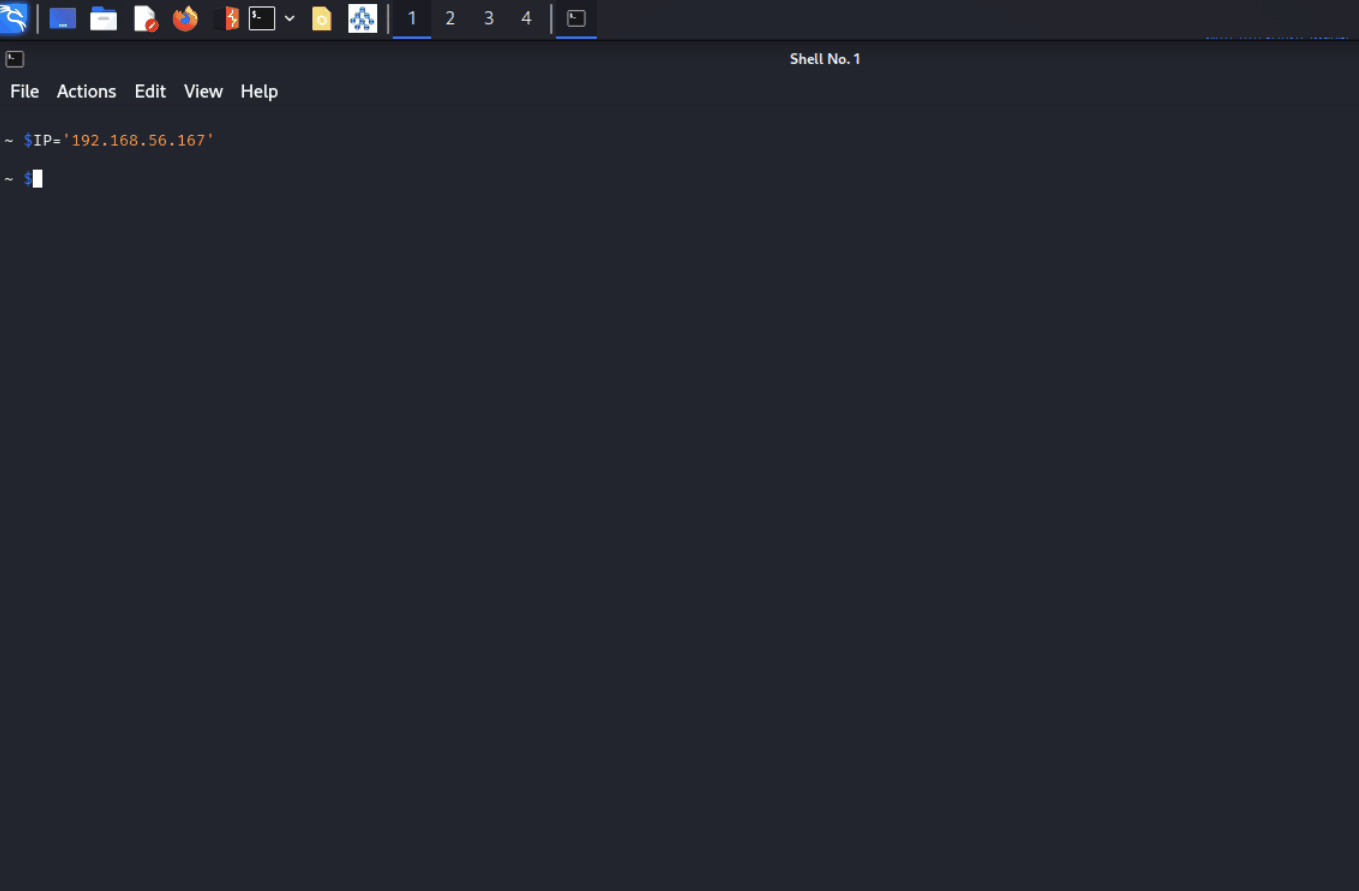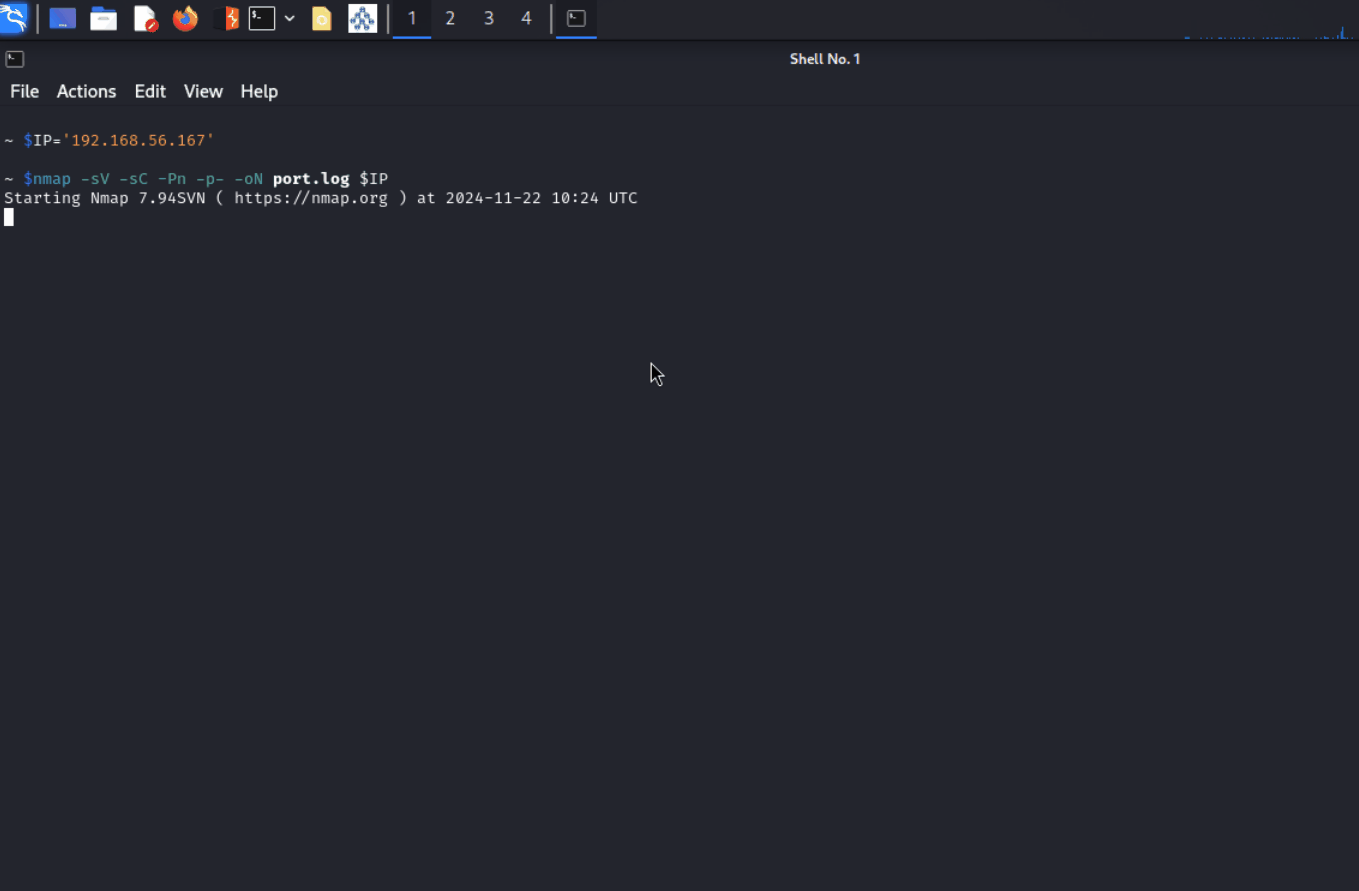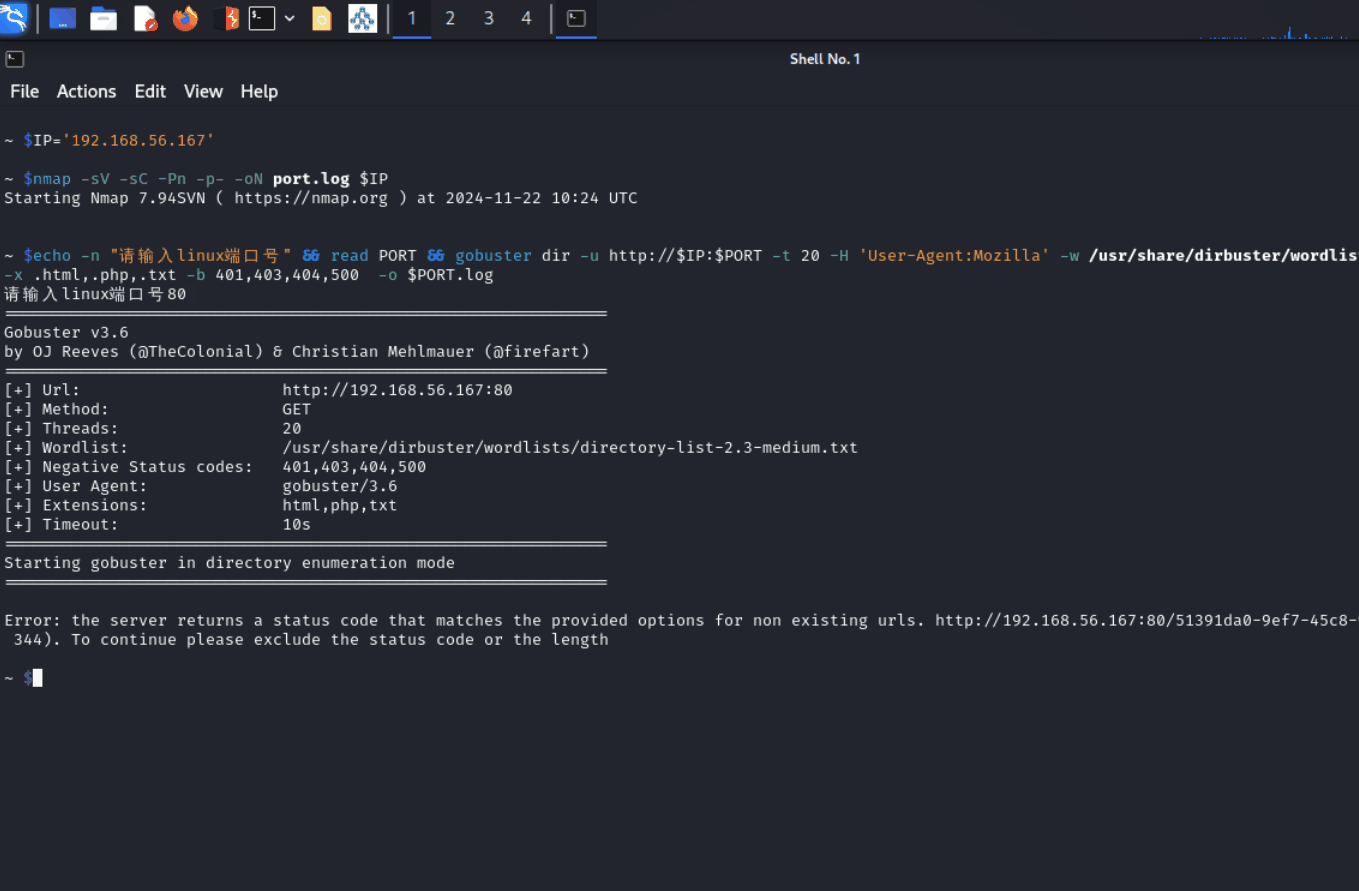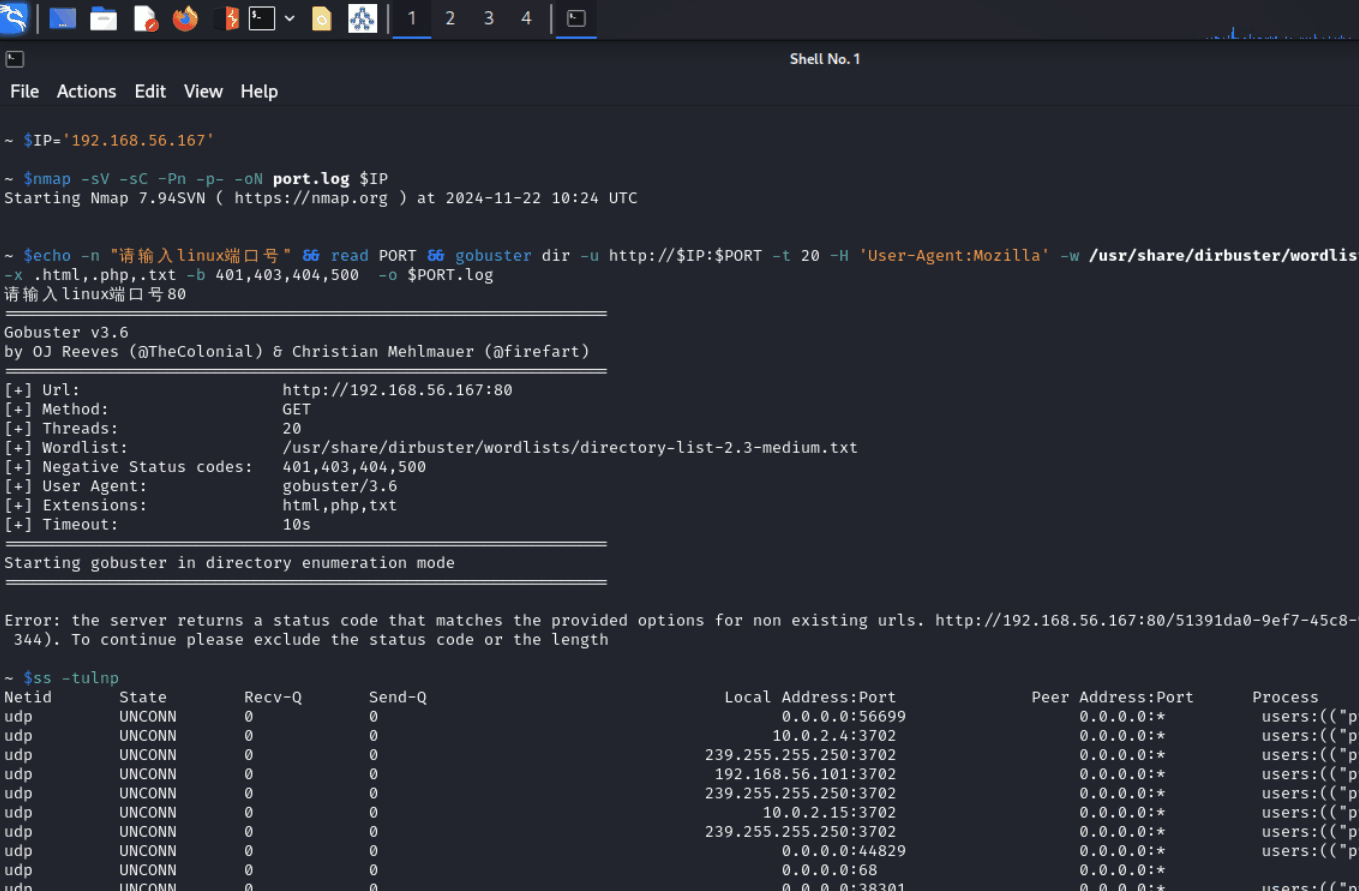
echo -n "请输入linux端口号" && read PORT && gobuster dir -u http://$IP:$PORT -t 20 -H 'User-Agent:Mozilla' -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.txt -b 401,403,404,500 -o $PORT.log
echo -n "请输入linux端口号" && read PORT && echo -n "请输入子目录" && read SUBDIR && gobuster dir -u http://$IP:$PORT/$SUBDIR -t 20 -H 'User-Agent:Mozilla' -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.txt -b 401,403,404,500 -o $PORT_$SUBDIR.log
gobuster vhost -u http://$DOMAIN -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain
reg save hklm\sam sam
reg save hklm\system system
impacket-secretsdump LOCAL -system system -sam sam
impacket-secretsdump domain/username[:password]@$IP
impacket-GetNPUsers $DOMAIN -no-pass -usersfile /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt |grep -v "Client not found"
kerbrute_linux_amd64 userenum -d $DOMAIN --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
sudo responder -I eth1 -Pdv
impacket-smbserver -smb2support kali /opt/SharpHound
impacket-smbserver -smb2support kali .
pkexec x-terminal-emulator -e 'neo4j console' &; disown
pkexec x-terminal-emulator -e 'openvpn ~/release_arena_ilikeyop.ovpn' &; disown
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
import-Module ActiveDirectory
Set-ADAccountPassword -Identity 'account_name' -NewPassword (ConvertTo-SecureString 'Pass1234!' -AsPlainText -Force)
pywhisker -d 'domian' -u 'user' -p 'pass' --target 'target user' --action "add"
gettgtpkinit.py domain/user -cert-pfx pfxfile -pfx-pass pfxpass targetuser.ccache
ssh-keygen -c -f id_rsa(二)建立与tmux终端交互的脚本
dmenu选择的命令,输入当前激活的tmux的分屏中,只上屏不运行,用户根据需要修改后回车再运行。
~ $cat /opt/drun.sh
l_num=$(wc -l /opt/dmenu_commands.txt|awk '{print $1}')
pane_id=$(tmux display-message -p '#{pane_index}')
commands=$(cat /opt/dmenu_commands.txt)
choice=$(echo "$commands" | dmenu -i -fn "WenQuanYi Zen Hei:size=10" -l $l_num -p "Choose a command" )
if [ -n "$choice" ]; then
tmux send-keys -t "$pane_id" "$choice"
fi(三)设定运行该脚本的系统快捷键
四、kali下wine运行出错
错误代码为wine: could not load kernel32.dll, status c0000135。
解决方法:
mkdir -p ~/myapp/prefix
export WINEPREFIX=$HOME/myapp/prefix
export WINEARCH=win32
export WINEPATH=$HOME/myapp
wineboot --init
winetricks五、解决与靶机的时间同步问题
windows下渗透测试时,涉及Kerberos验证时要求时间同步。可采取如下步骤:
(一)停止VirtualBox对虚拟机的时间同步
cd "C:\Program Files\Oracle\VirtualBox"
.\VBoxManage.exe setextradata "虚拟机名" "VBoxInternal/Devices/VMMDev/0/Config/GetHostTimeDisabled" 1(二)kali系统关闭时间同步服务
sudo systemctl disable systemd-timesyncd
sudo systemctl status systemd-timesyncd
systemd-timesyncd.service - Network Time Synchronization
Loaded: loaded (/usr/lib/systemd/system/systemd-timesyncd.service; disabled; pre>
Active: inactive (dead)
Docs: man:systemd-timesyncd.service(8)(三)与靶机同步时间
sudo ntpdate -u $IP六、auto_nmap.sh
一个调用nmap进行端口扫描的小脚本,首先快速扫描开放端口(不含UDP),再对这些端口进行细致扫描,避免一上来就对所有端口进行全面扫描造成等待时间过长,扫描结果保存到port.log。UDP端口另外单独扫描。
[ -z "$1" ] && { echo "Usage: $0 <target IP>"; exit 1; }
IP=$1
nmap -Pn -p- -T4 -v $IP | tee /dev/tty | awk '/PORT[[:space:]]+STATE[[:space:]]+SERVICE/,/^$/' | grep open | awk '{print $1}' |cut -d / -f1 |tr '\n' ',' | sed 's/,$//' |xargs -I {} nmap -Pn -sC -sV -p {} -v -oN port.log $IP #合并扫描指令七、uniq_attr.sh
这是借助AI生成的一个小脚本,用于检索LDAP中的特别属性,以便查找敏感信息,在打windows AD靶机时很有用。
#!/bin/bash
# 功能:检测LDAP中每个用户的特别属性,以便查找敏感信息
# 用法提示
usage() {
echo "Usage: $0 -s <LDAP_SERVER> -b <BASE_DN> [-u <USERNAME> -p <PASSWORD>]"
echo " -s <LDAP_SERVER> LDAP server address (e.g., ldap://example.com)"
echo " -b <BASE_DN> Base DN for the LDAP search (e.g., dc=example,dc=com)"
echo " -u <USERNAME> Username for LDAP authentication,for example:user@domain.com"
echo " -p <PASSWORD> Password for LDAP authentication"
exit 1
}
# 初始化参数
LDAP_SERVER=""
BASE_DN=""
USERNAME=""
PASSWORD=""
# 解析命令行参数
while getopts "s:b:u:p:" opt; do
case ${opt} in
s)
LDAP_SERVER=${OPTARG}
;;
b)
BASE_DN=${OPTARG}
;;
u)
USERNAME=${OPTARG}
;;
p)
PASSWORD=${OPTARG}
;;
*)
usage
;;
esac
done
# 检查必需的参数是否已提供
if [ -z "${LDAP_SERVER}" ] || [ -z "${BASE_DN}" ]; then
usage
fi
# 检查 -u 和 -p 参数是否同时提供或同时省略
if [[ -n "${USERNAME}" && -z "${PASSWORD}" ]] || [[ -z "${USERNAME}" && -n "${PASSWORD}" ]]; then
echo "Error: -u and -p must be provided together or omitted together."
usage
fi
# 输出读取到的参数(仅供调试使用,可以移除)
echo "LDAP Server: ${LDAP_SERVER}"
echo "Base DN: ${BASE_DN}"
if [[ -n "${USERNAME}" ]]; then
echo "Using authentication with username: ${USERNAME}"
else
echo "Using anonymous bind"
fi
FILTER="(objectClass=person)" # 过滤条件,提取所有用户
# 构造 ldapsearch 命令
if [[ -n "${USERNAME}" ]]; then
# 使用用户名和密码进行认证
ldapsearch -H "${LDAP_SERVER}" -b "${BASE_DN}" -D "${USERNAME}" -w "${PASSWORD}" "$FILTER" > ldap_users_raw.txt
else
# 使用匿名绑定
ldapsearch -x -H "${LDAP_SERVER}" -b "${BASE_DN}" "$FILTER" > ldap_users_raw.txt
fi
# 处理 ldapsearch 输出,提取用户和属性信息
awk '/^dn: / {user=$0; next} /^[^:]+: / {print user"|"$1"|"$2}' ldap_users_raw.txt > user_attributes.txt
# 统计每个属性的出现次数
awk -F '|' '
{
user=$1 # 提取用户标识
attr=$2 # 提取属性名
value=$3 # 提取属性值
user_attrs[user, attr] = value # 记录用户、属性与对应的值
attr_count[attr]++ # 统计属性出现的总次数
}
END {
print "特别属性:"
for (key in user_attrs) {
split(key, arr, SUBSEP) # 拆分组合键
user=arr[1]
attr=arr[2]
if (attr_count[attr] == 1) { # 如果属性只出现一次
print user, "独有属性:", attr, "值:", user_attrs[key]
}
}
}' user_attributes.txt
# 清理临时文件
rm -f ldap_users_raw.txt
rm -f user_attributes.txt